Solved!! pfsense vlan untagged interfaces with vlans on same trunk
-
hey everyone, I am having issues with pfsense and an hp1910-16g. I am leaving vlan 1 untagged and then 10,99,100 tagged on my network card but its not passing vlan tagged traffic even using the switch itself. I need to keep vlan 1 untagged for my desktop to be able to manage it without needing to change network settings all the time. I can get it working if I use 2 interfaces on my network card but I would love to change it to just one trunk. https://pastebin.com/mjUzJWHh here is my switch configuration and https://pastebin.com/vSzUd3dp is my pfsense configuration. any ideas on how to make this work or do I just bit the bullet and install a second network card in my pc just for managing the switch and dealing with remote logging after?
Solution: suricata on inline mode was causing the vlans to mess up. After disabling it and adding ifconfig em0 -vlanhwtag then renabling it, it seems to have fixed the problem
-
You can for sure run 1 network untagged, or native and then tags on top of that..
I run one of my interfaces like this.
Not sure on actual setups on hp.. But here is my config on sg300 for the port connected to pfsense that has native network setup and then vlans on top of that
interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 3-4,6-7,19 switchport trunk native vlan 2vlan 2 on the switch is this untagged vlan
-
did you have to add any routes to make it work?
-
No any directly attached network doesn't need routes on pfsense.
-
@johnpoz on your switch side?
-
NO! Why do you have routes on your switch? Are you wanting to do routing on your switch? If so pfsense wouldn't have any vlan info on it.. Nor know about any vlan IDs
If your going to do routes on your L3 switch, then it just becomes a downstream router and only thing connection between pfsense and it is a transit network.
-
I had to add a static route to be able to access my switch management from my wifi side. is the routes on my switch causing the issue then maybe?
-
Well your doing it wrong from the get go then.
Are you wanting to do routing on your switch, or just layer 2 - or a combination?
-
pfsense is going to do all the routing. I just need to have one static route because otherwise my phone (192.168.1.20) cant access my switch management at (10.0.0.2)
-
Only route you would need on your switch is the default route, pointing to pfsense Ip in whatever vlan you put your management IP in.. Then you can get to it from any other network routed by pfsense.
As you can see on mine.
ip default-gateway 192.168.9.253That is the setup on my switch. Its management IP is 192.168.9.99
! interface vlan 9 name lan ip address 192.168.9.99 255.255.255.0 -
ok so i setup the route and the interface as it should be and but the ip address for the vlan interface which im using dhcp for is getting its address unless I put my pfsense vlan tags on another interface. Im using 2.4.5 and is that maybe the problem?
-
Using 2.4.5 not sure why you think that would be a problem..
You can use dhcp if you want, not sure why anyone would do that on a switch management IP - but sure you can do that.
If using dhcp it should prob get its gateway from dhcp I would think..
from your config for your trunk port I don't see anywhere you set which vlan is untagged.. Not sure how you would do that on a hp switch.. But in cisco setting it to native as you saw in my config tells the switch what vlan to put untagged traffic in, and what vlan to send egress from the port untagged. It sets the pvid on the port so any untagged traffic ingress is in that vlan.
-
so it tells me 1(default) 10, 99-100 as interfaces with a pvid of 1 and passing all vlans correctly.
-
Well yeah vlan 1 is default untagged vlan.. So that would work..
-
it doesnt work with another switch I have and its the exact same configuration. untagged on one and then tagged on 10,99,100. what version of pfsense are you using?
-
Its not rocket science traffic is either tagged or not tagged.. If just naked on the interface directly its untagged. If it's setup as a vlan then it will have whatever vlan ID tag you put on it..
So here is my interface where I put my vlans and native untagged traffic. so igb2 network is 192.168.2/24, vlan 4 and 6 are 192.168.4/24 and 192.168.6/24
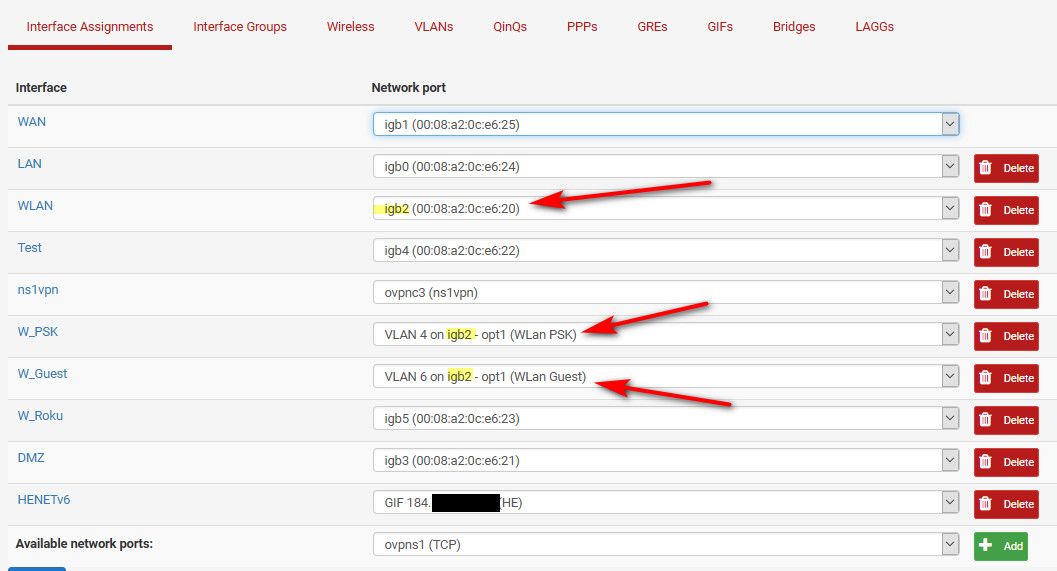
On the switch this untagged is vlan 2.. Makes it easy to know what vlan is what when the ID is just the 3rd octet of the network address space.
-
i checked that and made sure mine matched. what I did find out though is that my lan port (em0) if I change it to my 2nd interface (em2) that it works exactly how I expect it to. I wonder if its a bug and its already assigned that it causes that issue. it is the lowest mac address too so maybe that was my problem