Some devices on IoT vlan can access internet and others do not
-
Hi!
New to PfSense and I am learning alot over the past week. Today for some odd reason any new devices like an ipad or phone that connects to IoT vlan cannot access internet. Any existing devices, like a smart thermostat or Google Home can. No changes were made today so not sure why this is happening. DHCP is assigning IP's, DNS is auto configured on new devices. I even reloaded a back config from a couple of days ago and rebooted. BTW I am using NetGate SG1100.
At a loss right now.

-
Hi,
@the_object said in Some devices on IoT vlan can access internet and others do not:
an ipad
It's using DHCP ? So you can see the IP it got from the pfSense DHCP server for that pfSense interface ? Can you see, in the pfSens DHCP log, your iPad issuing the DHCP requests ?
It also received a gateway and DNS - both are ok (== interface IP used by pfSense) ?
What are the firewall rules for this interface ?edit :
How did you set up the IOT interface ?
How did you set up the DHCP server for this IOT interface ? -
Yes, the ipad gets the proper IP address/DNS/gateway from IOT DHCP. I see the device in DHCP leases. One thing I tried is to add the DNS server manually on the ipad and I had internet activity. What I can't understand is why some devices, Google Home, Ecobee thermostat which are on the the same vlan and on DHCP have no issues with internet. Everything connecting to same wireless AP.
It's a plain vanilla config for DHCP
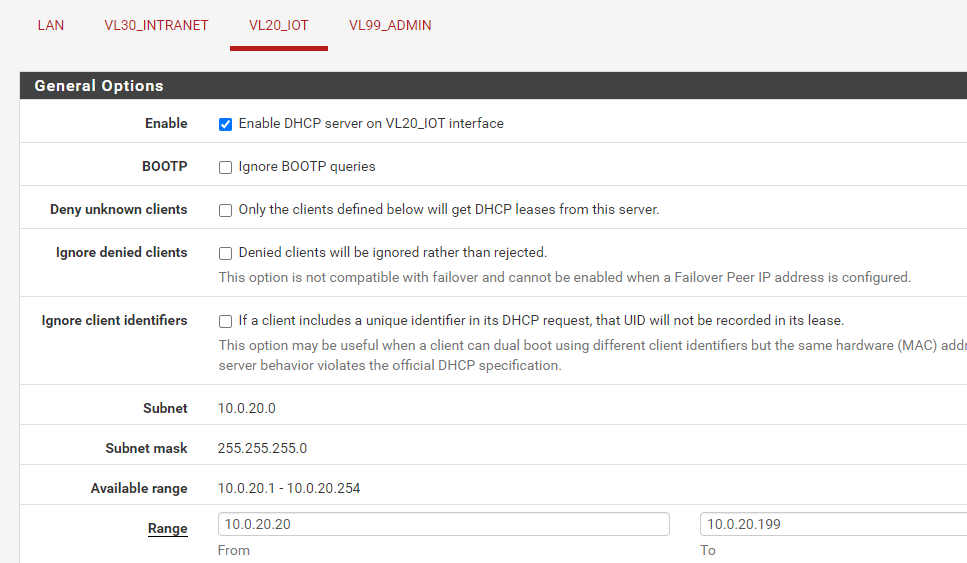
Here are the rules
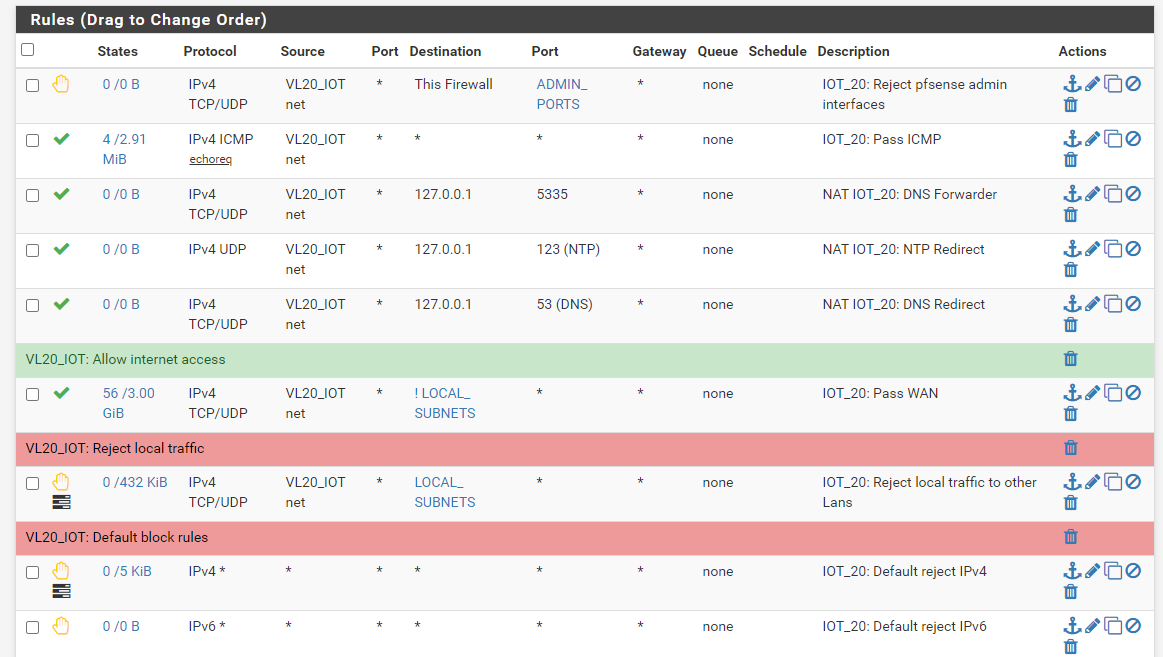
-
This traffic :
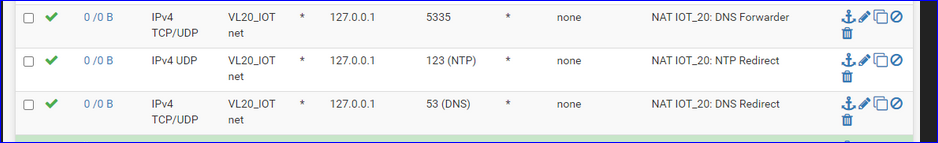
will never circulate on your network.
Traffic with destination 127.0.0.1 will always stays in the device where it was emitted. It's the device itself (sender == receiver).
In stead of 127.0.0.1 consider using the Alias 'this firewall' or "VL20_IOT_address".
So these 3 rules will never get hit by any traffic.This rule :

will get used by any traffic as long as the destination isn't "LOCAL_SUBNETS". (Dono what LOCAL_SUBNETS actually is)
I advise you to change "TCP/UDP" for "All" which includes, among others, ICMP.
Your iPad should be able to go 'outside'.To test, disable your first rule and check if you can reach the pfSEnse IP base VL20_IOT_address - if you can see the pfSense GUI, using your iPad and a browser.
-
No, that did not seem to help. I disabled all 4 of the first set of rules.
LOCAL_SUBNETS is the 3 other networks I have,
10.0.10.x which is the device LAN
10.0.30.x which is internal device LAN
10.0.99.x Admin LAN
The rule is meant to stop the IOT devices from talking to the other networks but allow traffic to the internet. Which is working for some and not others. -
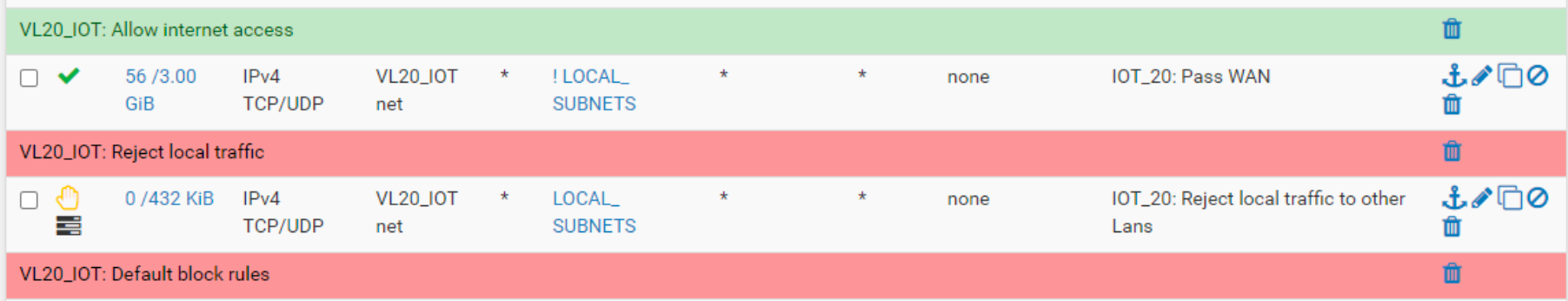
I would not craft rules like this.
I would reject to destination LOCAL_SUBNETS then pass to destination any.
You should probably packet capture the host that can't get out and see what it is doing and what is failing.
-
I got it figured out. IOT interface was not set in Network Interfaces in DNS Resolver. Although it doesn't explain why some devices on IOT could still access internet. Maybe they had cached info.
I can redo the Reject rule to go before Allow.
Many thanks to all for helping out!