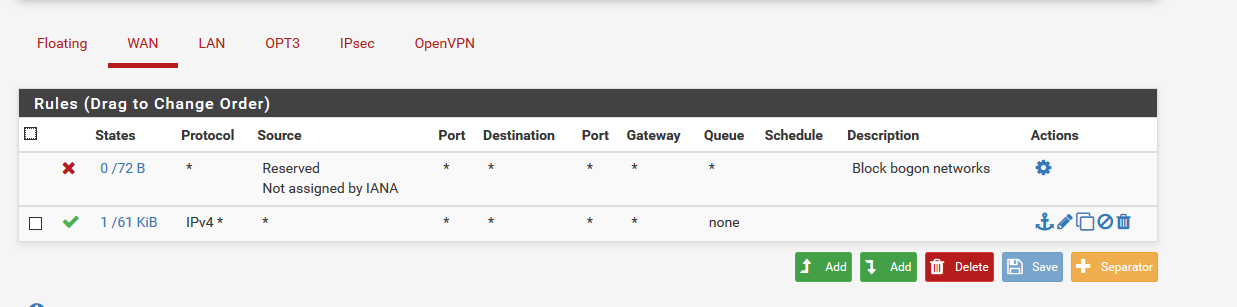
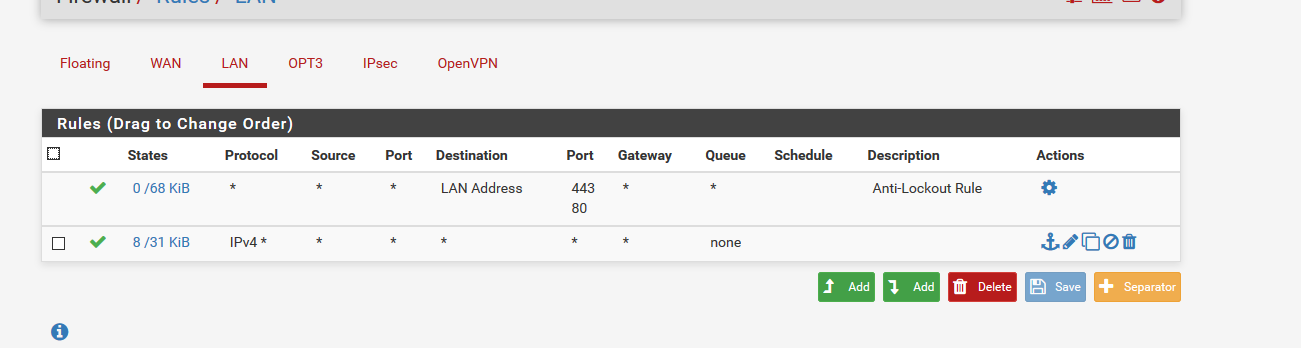
Cannot Ping WAN Interface
-
@teamits Thank you for your answer...I have a any-any rule under WAN...do I still need to create another rule?
-
@andy10 said in Cannot Ping WAN Interface:
Thoughts?
Your "any to any rule on WAN" is just temporary to make ICMP work, right ? What about, at least, limiting this "IPv4*" protocols to "ICMP" ?
DO NOT keep it rule.
Or change pfSense for a switch to have close to identical results, and zero admin efforts. -
@Gertjan yes it’s a temp rule...i need to figure out first why i cannot ping my WAN IP...
-
Using what ? From where ? Through which other upstream devices - the ones between you and pfSense ?
@andy10 said in Cannot Ping WAN Interface:
I can ping the LAN interface but I cannot ping the WAN IP
From where ?
You have already a pass all rule - that's ok for testing purposes.
You know now that ant traffic coming into WAN will be 'seen' by the network stack. At that level, ICMP is handled.
You should fire up tcpdump (packet capture), select WAN as the interface and ICMP for the type of protocol.
Now you ping from where ever you ping.
Stop the capturing : if it's empty, the traffic never reached pfSense.Most often this is explained easily : right after you discover that the ISP router is also a router (...) it becomes clear that router should a) also reply to ICMP (because this router has the actual WAN IP, not pfSense, which uses a RFC1819 type IP), or b) pass the ICMP requests through.
Are you trying to ping from pfSense's LAN the WAN IP ? What are your LAN rule(s) ?
Your WAN IP is a RFC1918 type ? -
@andy10 I was assuming you were pinging from LAN. If no block is logged by the default block rule then it's not being blocked, meaning it's generally a routing or some other issue.
-
I am pinging from another server on the LAN network.
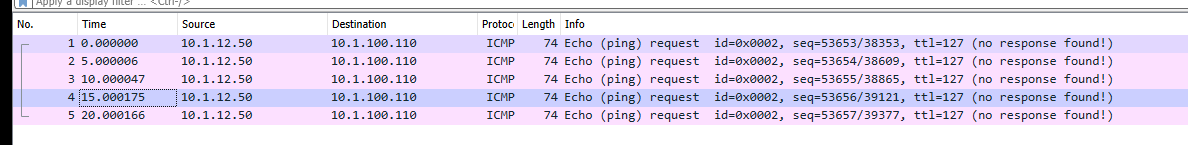
-
@Gertjan
From where ?You have already a pass all rule - that's ok for testing purposes.
You know now that ant traffic coming into WAN will be 'seen' by the network stack. At that level, ICMP is handled.
You should fire up tcpdump (packet capture), select WAN as the interface and ICMP for the type of protocol.
Now you ping from where ever you ping.
Stop the capturing : if it's empty, the traffic never reached pfSense. colored text please see screenshot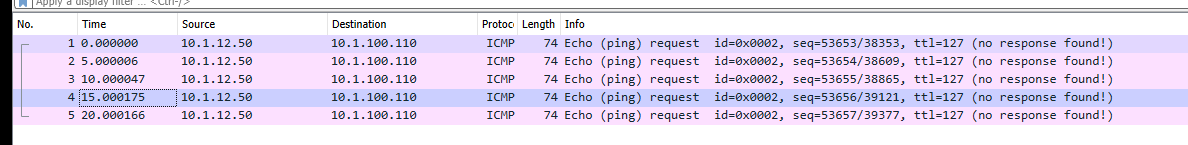
Most often this is explained easily : right after you discover that the ISP router is also a router (...) it becomes clear that router should a) also reply to ICMP (because this router has the actual WAN IP, not pfSense, which uses a RFC1819 type IP), or b) pass the ICMP requests through.
ISP is not involved here...it's installed on a VM which is behind a Palo Alto firewall...
Are you trying to ping from pfSense's LAN the WAN IP ? What are your LAN rule(s) ? trying to ping from 2 servers on the LAN and WAN networks...both fail
Your WAN IP is a RFC1918 type ?colored text 10.1.100.110/24 -
@andy10 Does the server you're pinging from have a firewall rule that is blocking the replies?
If you're pinging from LAN the WAN rule shouldn't be used. -
@teamits no..the windows firewall is off....the weird thing is that when i reboot pfsense...and run a continuous ping to the WAN interface...i get responses right before it shuts down ...could it be a bug ?
-
I reinstalled pfsense on another VM and i can ping the interfaces now...could be a bug! Issue resolved. Thanks!
-
Bug ?
Setup !pfSense handles ICMP as per user settings.
If not, this forum would be swamped by angry user posts ^^