How to access local services “Via the Front Door” !!??
-
Hello,
When accessing e.g. a web-server from the internet, the traffic is screened by the WAN-filter-rules. In case of IPV4 additional there is NAT. Those functions take care of the security.
However, if you want to access your own servers from your own network, then:- IPV4: The IPV4-address internally is different, so not at all reachable
- IPV4 & IPV6: The filter/security stack from the WAN is bypassed (do not like that!)
I know you can make the IPV4 reachable via Pure-NAT or double DNS and you can access the IPV6 ^without problems
 ”, but IMHO these are not good options.
”, but IMHO these are not good options.Part of the problem is that using pfSense, there is no ^front door towards the “server zone”^. You trust on the fact that other subnets and static routes block unwanted traffic for you. So to compare a street, you removed the front door, and the neighbors, have to check that nobody is going towards your home. Conceptually a bad idea IMHO! What ever you can build a front door using Floating rules, but it is complicated.
So, back to my issue ^How to access local services “Via the Front Door”^. In my opinion, the proper option to tackle the problem in a conceptual proper way, is to route the internal request towards one of your own servers back to ^the front door^ being the entry point of the WAN-gateway.
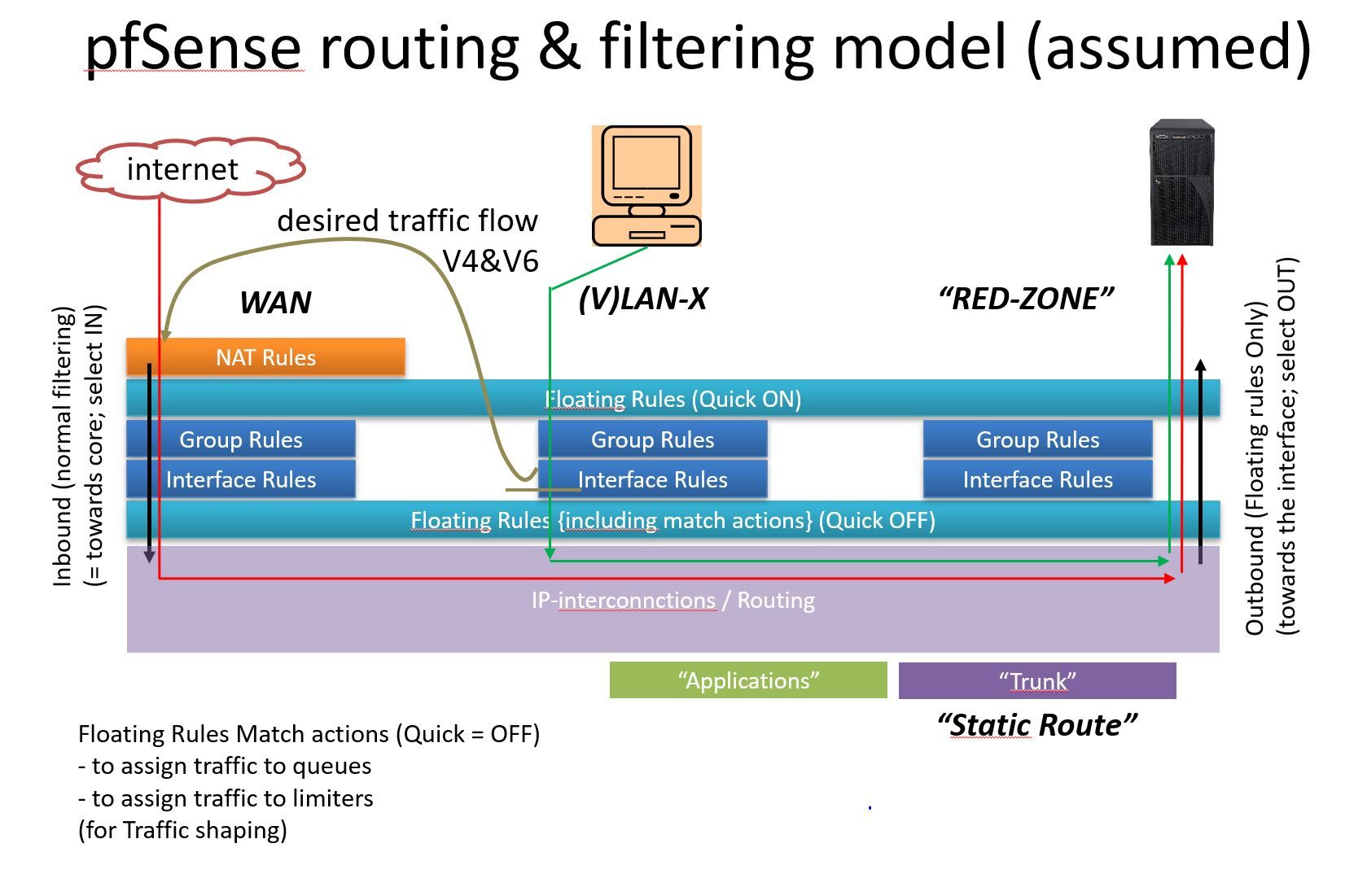
For that purpose there should be a “PCLAN-GW-rule” like if destination is “One of my Own Servers” then through back the traffic towards the start of the WAN-GW (see picture).[0_1592042366164_20200613 How to access local services “Via the Front Door”.docx](Uploading 100%)
Problem is that …. I have no idea how to do that ……
Sincerely,Louis
-
the only proper way is to use split dns. all the other crap is bullshit
-
I definitively do not agree with you for two reasons:
- The security is bypassed (unless you define and maintain a second rule set). Unacceptable IMHO
- You have to define and maintain a second DNS tree, not a good idea as well
Sincerely,
Louis
-
@louis2 said in How to access local services “Via the Front Door” !!??:
The security is bypassed (unless you define and maintain a second rule set). Unacceptable IMHO
You have to define and maintain a second DNS tree, not a good idea as well
Sincerely,Louis
A) your picture in the previous post seems to indicate a complicated ruleset with a bunch of floating rules.
A.1) try to simplify your setup. it's almost never a good idea to make simple stuff hard,just because you can
A.2) floating rules have their uses, but a lot of times they are used incorrectly or without warrant
B)what security are you talking about?
B.1)by maintaining a second ruleset you mean?- creating a single additional firewall-rule?
- that uses the same alias as your existing rule?
- and if changes are made to the alias, both rules are up to date ?
C) no need for a seperate dns tree, just use host or domain overrides
D) there might be better ways to accomplish whatever it is you need. But without explaining you setup in detail it will be hard for some of the experienced community members or devs to pitch in