DNS leak
-
That site does not respond for me. Which I'm finding quite ironic!
Any DNS leak test simply shows you where your clients queries are being resolved. You have to device for yourself if those are correct.
There is no reason to have a block rule for DNS on WAN. All inbound traffic is blocked on WAN by default anyway.
Steve
-
@stephenw10 said in DNS leak:
That site does not respond for me. Which I'm finding quite ironic!
Any DNS leak test simply shows you where your clients queries are being resolved. You have to device for yourself if those are correct.
There is no reason to have a block rule for DNS on WAN. All inbound traffic is blocked on WAN by default anyway.
Steve
Good morning Steve, theoretically the default configs is blocked on Wan, but for some odd reason Pfsense responds differently with different hardware ;)
Also the second rule (pass 53), you need to assign to all interfaces (opt1,opt2,..) and place it above all others rules.Then test again for DNS leak https://ipleak.net
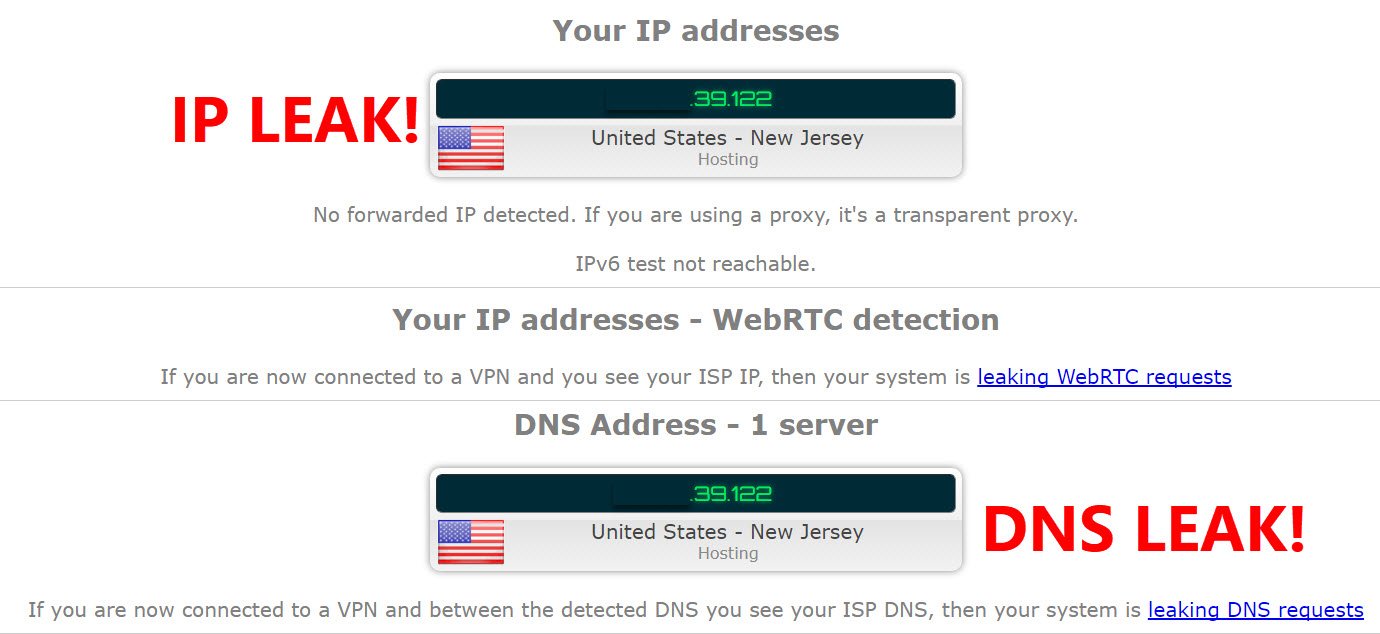
-
@AKEGEC : your second rule : include TCP.
Your first rule : WAN is blocking everything, even for these devices :
but for some odd reason Pfsense responds differently with different hardware
so the default block all rule will do it's job. If for some "odd reasons" devices could penetrate the firewall I recommend changing the firewall and/or the person that admin's it.