pfsense internal network on 'public' range
-
pf is setup with our internal network on a private range (LAN) and another internal private network via the OPT1 and everything is working great.
I have now added an additional private network but it is on a 'public' range. say 172.99.0.0/24. This is added as a static route using the OPT1 gateway. We are able to communicate via the existing internal networks and the new 'public' internal network without issue.
The problem is that the new 'public' internal network can't access the internet. I have noticed that the "Automatic outbound NAT rule generation" will not add the 172.99.0.0/24 network as a source in the automatic rules. I have created a manual rule to compensate however I still can't get internet access on that network. (trace stops at pf, dns works)
What am i missing?
-
@w4436 bump
-
@w4436 Did you create a firewall rule allowing 172.99.0.0/24 to go out to the internet through OPT1 interface?
Only NAT is not enough. -
I assume the gateway here is some other router in the OPT1 subnet and not the OPT1 interface IP?
You shouldn't need any NAT in or out for a public subnet as long as the upstream provider is correctly routing it to you.
Steve
-
@mcury OPT1 has the rule: PASS ANY * to *
-
This post is deleted! -
Facepalm. I forgot to set Outbound NAT mode to Hybrid to take advantage of the manual rule I created. It works, now. Thanks!
-
Really shouldn't need outbound NAT there if the provider is routing it to you.
If you do need NAT they are not routing it to your WAN IP, you should address that rather than NATing it to some other public IP.
Steve
-
@stephenw10 There is a misunderstanding here. I am trying to use the public range as a private range, not as an actual public range accessible from the internet.
-
Oh, OK. You shouldn't really do that since it will block access to real addresses inside that subnet if any hosts there ever need to access them.
Why not just use a private subnet there?Steve
-
@stephenw10 I totally understand this is not best practice but we are testing a product configuration for a customer who has run out of RFC 1918 subnets to use for their network so they have started to use similar public ranges. In production this product will not be connected to the internet, but for us testing it in house having internet access helps. I know I could use NAT between this test network and our pf box but it is unlikely that anybody needs to access any websites on this range.
Thanks!
-
Ah OK. Gotta play the hand you're dealt.

-
@w4436 said in pfsense internal network on 'public' range:
I forgot to set Outbound NAT mode to Hybrid to take advantage of the manual rule I created. It works, now. Thanks!
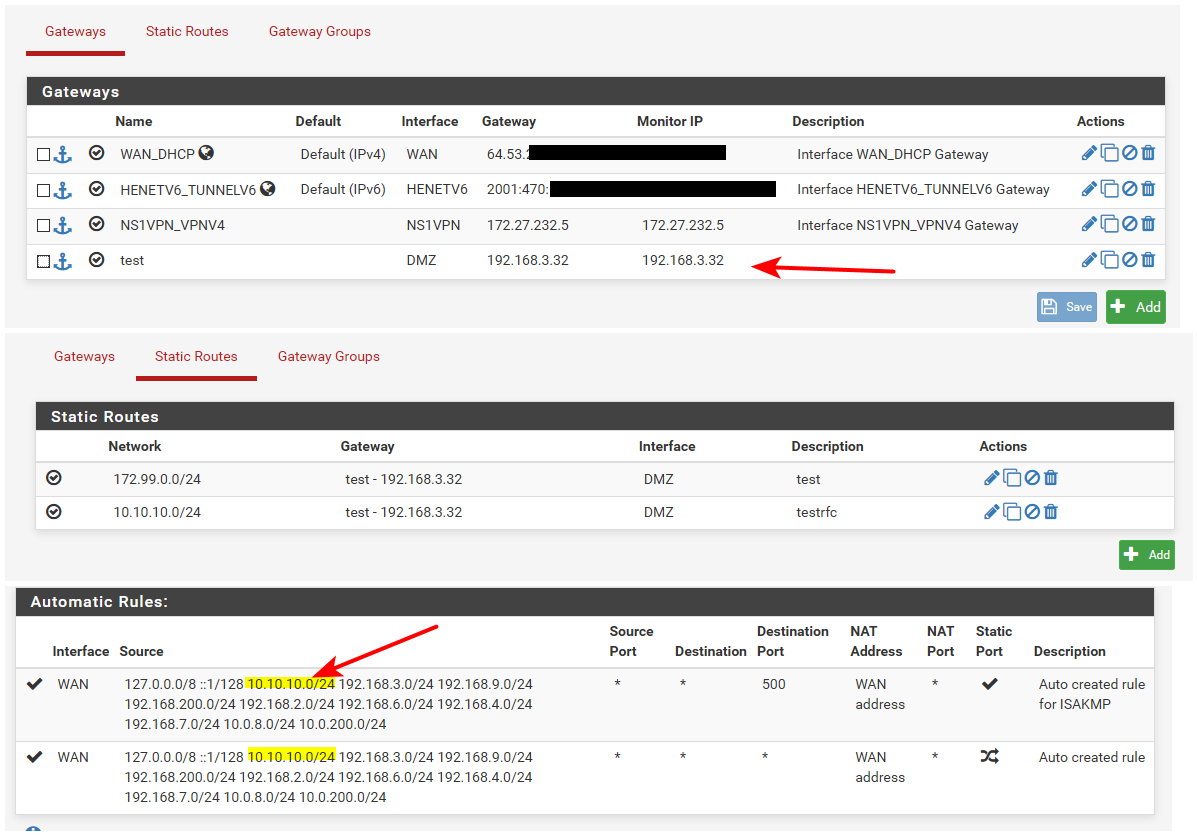
When you do this, route to a downstream network. Pfsense would automatically add an outbound nat for that network.. Be it rfc1918..
Example I duplicated your downstream network.. And if I add a route for rfc1918, its auto added to the auto outbound nat.
But yeah @stephenw10 is right - this is not good idea to just use public IP space internally that is not yours, or that is not actually routed to where your using it.
Lets just hope whoever this is - you don't need to get to any of their stuff ;)
NetRange: 172.99.0.0 - 172.99.3.255 CIDR: 172.99.0.0/22 NetName: SOUNDVIEW Organization: Soundview Broadcasting, LLC (SBL-72);; QUESTION SECTION: ;www.soundviewbroadcasting.com. IN A ;; ANSWER SECTION: www.soundviewbroadcasting.com. 3573 IN CNAME soundviewbroadcasting.com. soundviewbroadcasting.com. 3573 IN A 172.99.1.34for a customer who has run out of RFC 1918 subnets
Really?? the 10 space alone is 16 Million addresses.. Now with 192.168 another 65,000 then another million with 17.16/12..
I find it very hard to believe they have used this up.. Unless horrible IP management like using a /16 for every site out of the 10 space..
There is also the whole 100.64/10 space they could use which is cgnat space.. Which is another 4 million. There is is also the practice of using like the documentation networks.. 192.0.2.0/24
Or say the 198.18.0.0/15, which is used for benchmarking - that again doesn't step on some other companies public space.. That is another 130K address.
That someone could use all of this space up really just screams horrible IP planning and management.. And vs just fixing that they start grabbing public space that is not there's normally its the dod space like 6.x, 7.x, 11.x some of the common ones used...
If they using like 20Million devices on their network - they really really should be working on deployment of IPv6 vs just snagging public..
I know this on not on you specifically - Unless you planned out their misuse of rfc1918.. Yeah just use the /16 for the finance department vlan - with 3 people in it.. We will never use up this space ;) hehehe
Horrible misuse of network size is one of those things just bugs me - sorry ;) You do have to quite often work with what your given..
You see it here all the time where users using 10/8 on their lan or 192.168/16 -- you would think ah its just their 1 home - who cares if they use up all of rfc1918 with their 3 networks.. But such practice leads to nonsense in the work networks as well.. Just because space seem so large you will never use it up - doesn't mean your network shouldn't be appropriately sized.. Companies that do this shit rub me the wrong way is all.. ;)
Had a customer a few years back that used a /16 for their printer vlan.. Was like WTF??? you have 20 printers.. Tops!!