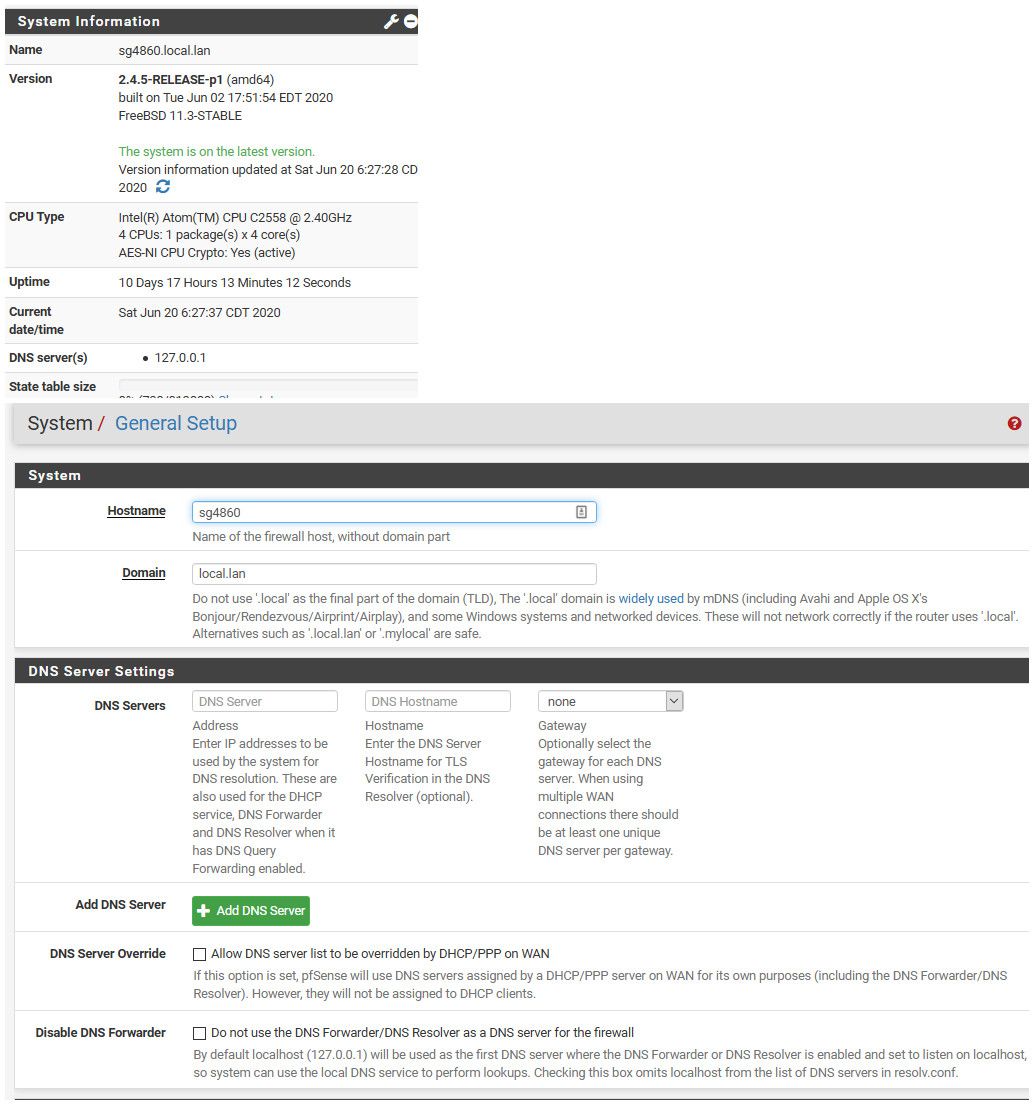
DNS server in "general settings" when using unbound as resolver
-
Background/context:
I am using a local DNS server (pihole) for DNS resolution for all devices on my network. This DNS is assigned by pfsense through DHCP. Pihole is configured to use pfsense as its only upstream resolver. I am not running pfsense unbound in forwarding mode, it is querying root servers directly.Now my questions for you are:
- What DNS server I should put in pfsense->general settings? I've tried my local pihole's IP, an external DNS like 8.8.8.8, and even left it blank, regardless of what I use, things work normally. Which, I guess, is what should happen when unbound is querying root servers directly. But I'd still like to understand what's the ideal setting here.
- I have a NAT rule set up to block DNS queries for hardcoded DNS servers and route them all to my pihole. This works well for queries for any machine on my network EXCEPT the pfsense box. Can I have DNS queries made by the pfsense box also route through pihole? I assumed that the NAT rule + firewall rule would take care of this but apparently not.
Needless to say, I've managed to thoroughly confuse myself. Any helpful hints are appreciated so that I can sleep in peace :)
-
1 What DNS server I should put in pfsense->general settings? > my local pihole's IP
2 NAT rule + firewall rules, there is no need for the box, only for device on the lan
-
@kiokoman Thanks for the insights in regards to #2. Good to know!
When I use my pihole's IP in pfsense->general settings, executing
dig pfsense.orgon the pfsense box does not cause for that lookup to go to pihole. Instead, pfsense will resolve it locally (and properly) despite the fact that I have the settingDo not use the DNS Forwarder/DNS Resolver as a DNS server for the firewallchecked. Another pfsense local box nuance? -
The only thing pfsense should point to is itself, loopback.. Why would you think it needs to know about or point to pihole in any way?
The only reason pfsense would need to go ask pihole something, is if pihole knew something it needed... What would that be in your scenario? I can't think of anything.
And if it did, that would be a domain override..
I use pihole in my network, clients point to pihole for dns.. It forwards to pfsense, pfsense resolves..
-
@johnpoz yep, makes total sense. I guess I just needed to have this hammered into my head. Thanks!
-
Users seem to have a hard time grasping what a resolver is and how it works.. They think that there has to be a dns server you point to..
-
@johnpoz what i don't understand is, if we do the way you recommend (which i had for a long time) the dnsleak test shows my ISP.
so now i had to go back to using the DNS Resolver to forward to 1.1.1.1 so i don't fail the leak test
-
@gwaitsi said in DNS server in "general settings" when using unbound as resolver:
so i don't fail the leak test
Yeah because its so much better to hand everywhere you go to 1.1.1.1.. I mean who would be tracking that.. vs talking directly to the authoritative ns across the globe directly..
What do you think is easier to track?
If your tinfoil hat is that tight, then just route your dns queries through a vpn.
-
@johnpoz my dnsleak test IS being conducted over a VPN.
I route everything over expressvpn (except for a few IPs like this forum which don't VPNs).
So what use is the VPN if the dnsleak test then gives my local IP address when using the root servers? that seems to defeat the who point of having the VPN.
the problem is, unbound does not respect the outgoing interfaces. i tell the firewall to use 1.1.1.1 and not use the unbound/forwarder - resolution from the firewall correctly goes to 1.1.1.1.
if i select unbound to use only the vpn interfaces, it does not. it goes via WAN -
Well clearly you not routing your dns queries over a vpn, if the dns test is showing your actual IP vs your vpn ip..
Bringing up unbound on a vpn interface to be used as outbound can be problematic depending on when the vpn comes up, if goes down, how you actually have your routing setup, etc.
Unbound should be set to only use the localhost for outbound traffic if you want to ensure vpn traffic is used if your doing a default route then via your vpn service.
Or if you going to be doing policy routing of your vpn connection, its best to move your dns off of pfsense and have something on your network doing the dns queries so you can be sure you policy route that traffic, and use any sort of kill switches for when the vpn might go down that your tinfoil hat calls for.
-
@johnpoz dnsleaktest.com shows the IP address of my vpn provider.
whether you select standard or extended, it then shows results in the IP of my ISP connection.my config is as follows
System DNS Servers
DNS Servers 1.1.1.1 firewall WAN
DNS Server Override unchecked
Disable DNS Forwarder checkedDNS Resolver
enable checked
Network Interfaces LAN / VLAN
Outgoing Interfaces Localhost
system transparent
DNSSEC checked
Use SSL/TLS outgoing checked
DHCP Register checked
Static DHCP checkedAdvanced Privacy
Hide ID checked
Hide Version checked
Query Name checked
Prefetch Support checked
prefetch DNS key checked
harden DNSSEC checked
Experimental Bit 0x20 checkedRouting
WAN Default RouteRules
TCP/UDP * * LAN Address DNS allow
TCP/UDP * * !Firewall DNS blockTCP/UDP * * VPNBYPASS * WAN none
TCP/UDP * * !LAN * ExpressVPN noneNAT
LAN TCP/UDP * * !LAN Address DNS LAN Addr (i found using 127.0.0.1 didn't work, but it did with LAN addr)** PS it is not a tin foil hat, when you live in a country where big law firms criminally intimidate and extort (for 3yrs relentlessly) exorbitant amounts of money because you play 50sec of a movie - consider yourself lucky your lawyers haven't woken up to that scam **