Can't connect to IPsec VPN
-
I built a IPsec VPN server according to the official tutorial(https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ikev2-with-eap-tls.html), But it has something wrong with certificate authentication.
Here is the settings of Phase 1
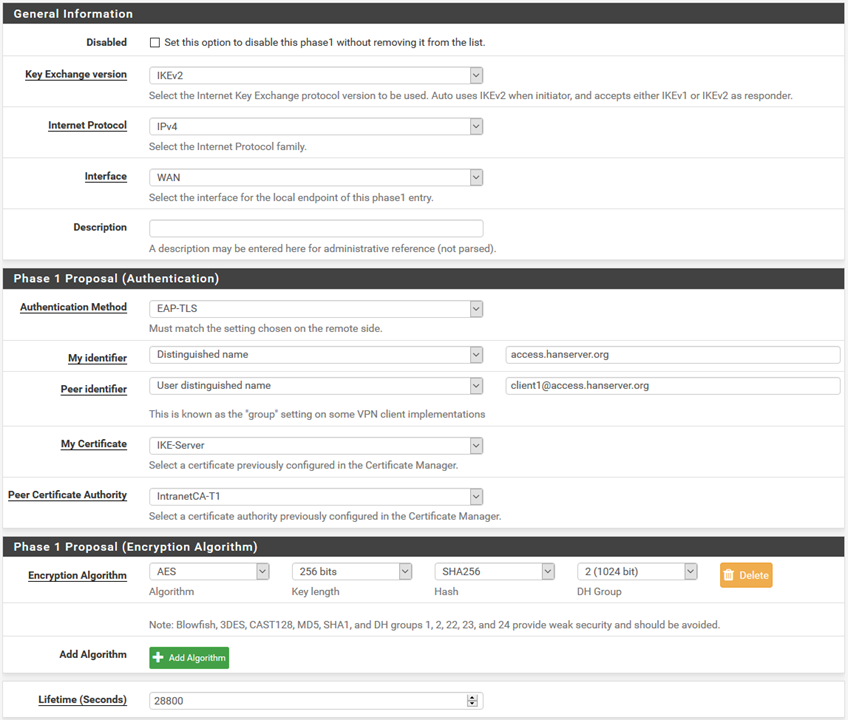
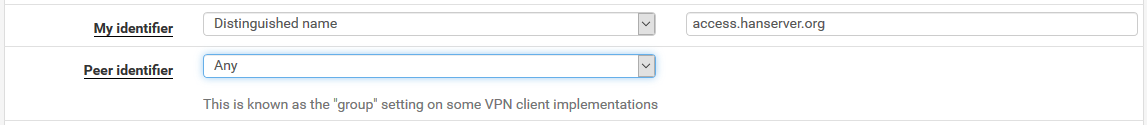
IPsec logs:Jun 20 21:30:48 pfSense charon: 09[NET] <1> received packet: from 172.20.10.131[761] to 124.116.232.99[500] (616 bytes) Jun 20 21:30:48 pfSense charon: 09[ENC] <1> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) V V V V ] Jun 20 21:30:48 pfSense charon: 09[CFG] <1> looking for an IKEv2 config for 124.116.232.99...172.20.10.131 Jun 20 21:30:48 pfSense charon: 09[CFG] <1> candidate: %any...%any, prio 24 Jun 20 21:30:48 pfSense charon: 09[CFG] <1> candidate: 124.116.232.99...%any, prio 1052 Jun 20 21:30:48 pfSense charon: 09[CFG] <1> found matching ike config: 124.116.232.99...%any with prio 1052 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received MS NT5 ISAKMPOAKLEY v9 vendor ID Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received MS-Negotiation Discovery Capable vendor ID Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received Vid-Initial-Contact vendor ID Jun 20 21:30:48 pfSense charon: 09[ENC] <1> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> 172.20.10.131 is initiating an IKE_SA Jun 20 21:30:48 pfSense charon: 09[IKE] <1> IKE_SA (unnamed)[1] state change: CREATED => CONNECTING Jun 20 21:30:48 pfSense charon: 09[CFG] <1> selecting proposal: Jun 20 21:30:48 pfSense charon: 09[CFG] <1> no acceptable ENCRYPTION_ALGORITHM found Jun 20 21:30:48 pfSense charon: 09[CFG] <1> selecting proposal: Jun 20 21:30:48 pfSense charon: 09[CFG] <1> no acceptable INTEGRITY_ALGORITHM found Jun 20 21:30:48 pfSense charon: 09[CFG] <1> selecting proposal: Jun 20 21:30:48 pfSense charon: 09[CFG] <1> no acceptable ENCRYPTION_ALGORITHM found Jun 20 21:30:48 pfSense charon: 09[CFG] <1> selecting proposal: Jun 20 21:30:48 pfSense charon: 09[CFG] <1> proposal matches Jun 20 21:30:48 pfSense charon: 09[CFG] <1> received proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:3DES_CBC/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024 Jun 20 21:30:48 pfSense charon: 09[CFG] <1> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024 Jun 20 21:30:48 pfSense charon: 09[CFG] <1> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> remote host is behind NAT Jun 20 21:30:48 pfSense charon: 09[IKE] <1> sending cert request for "CN=IntranetCA-T1, C=CN, ST=A, L=B, O=C, OU=D" Jun 20 21:30:48 pfSense charon: 09[ENC] <1> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(CHDLESS_SUP) N(MULT_AUTH) ] Jun 20 21:30:48 pfSense charon: 09[NET] <1> sending packet: from 124.116.232.99[500] to 172.20.10.131[761] (345 bytes) Jun 20 21:30:48 pfSense charon: 09[NET] <1> received packet: from 172.20.10.131[63062] to 124.116.232.99[4500] (768 bytes) Jun 20 21:30:48 pfSense charon: 09[ENC] <1> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 2c:75:d9:70:0b:c5:a3:a4:52:e6:69:35:6a:13:60:2f:36:c6:82:23 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for "CN=IntranetCA-T1, C=CN, ST=A, L=B, O=C, OU=D" Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 0e:ac:82:60:40:56:27:97:e5:25:13:fc:2a:e1:0a:53:95:59:e4:a4 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid dd:bc:bd:86:9c:3f:07:ed:40:e3:1b:08:ef:ce:c4:d1:88:cd:3b:15 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 6a:47:a2:67:c9:2e:2f:19:68:8b:9b:86:61:66:95:ed:c1:2c:13:00 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 01:f0:33:4c:1a:a1:d9:ee:5b:7b:a9:de:43:bc:02:7d:57:09:33:fb Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 7d:78:68:af:8d:0c:5d:b5:e2:46:b4:1b:3e:19:62:0e:35:4f:e9:53 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 88:a9:5a:ef:c0:84:fc:13:74:41:6b:b1:63:32:c2:cf:92:59:bb:3b Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 34:4f:30:2d:25:69:31:91:ea:f7:73:5c:ab:f5:86:8d:37:82:40:ec Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 3e:df:29:0c:c1:f5:cc:73:2c:eb:3d:24:e1:7e:52:da:bd:27:e2:f0 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 87:db:d4:5f:b0:92:8d:4e:1d:f8:15:67:e7:f2:ab:af:d6:2b:67:75 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 6c:ca:bd:7d:b4:7e:94:a5:75:99:01:b6:a7:df:d4:5d:1c:09:1c:cc Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid e2:7f:7b:d8:77:d5:df:9e:0a:3f:9e:b4:cb:0e:2e:a9:ef:db:69:77 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid b1:81:08:1a:19:a4:c0:94:1f:fa:e8:95:28:c1:24:c9:9b:34:ac:c7 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid bb:c2:3e:29:0b:b3:28:77:1d:ad:3e:a2:4d:bd:f4:23:bd:06:b0:3d Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Jun 20 21:30:48 pfSense charon: 09[IKE] <1> received 20 cert requests for an unknown ca Jun 20 21:30:48 pfSense charon: 09[CFG] <1> looking for peer configs matching 124.116.232.99[%any]...172.20.10.131[10.0.2.102] Jun 20 21:30:48 pfSense charon: 09[CFG] <1> candidate "bypasslan", match: 1/1/24 (me/other/ike) Jun 20 21:30:48 pfSense charon: 09[CFG] <1> ignore candidate 'bypasslan' without matching IKE proposal Jun 20 21:30:48 pfSense charon: 09[CFG] <1> no matching peer config found Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP4_ADDRESS attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP4_DNS attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP4_NBNS attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP4_SERVER attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP6_ADDRESS attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP6_DNS attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> processing INTERNAL_IP6_SERVER attribute Jun 20 21:30:48 pfSense charon: 09[IKE] <1> peer supports MOBIKE Jun 20 21:30:48 pfSense charon: 09[ENC] <1> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Jun 20 21:30:48 pfSense charon: 09[NET] <1> sending packet: from 124.116.232.99[4500] to 172.20.10.131[63062] (80 bytes) Jun 20 21:30:48 pfSense charon: 09[IKE] <1> IKE_SA (unnamed)[1] state change: CONNECTING => DESTROYINGWhen I change Peer identifier to Any, it worked. I use a Intermediate CA to issue all the client certificate and different clients can access different subnet. I'm worried that this will cause security problems.
So I want to know:
Is the setting of "My identifier" and "Peer identifier" correct?
How to solve the problems.
I set "Peer identifier" to "Any", Whether will it cause security problems?Here is Part of the log:
Jun 20 21:35:21 pfSense charon: 09[IKE] <2> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Jun 20 21:35:21 pfSense charon: 09[IKE] <2> received 20 cert requests for an unknown ca Jun 20 21:35:21 pfSense charon: 09[CFG] <2> looking for peer configs matching 124.116.232.99[%any]...172.20.10.131[10.0.2.102] Jun 20 21:35:21 pfSense charon: 09[CFG] <2> candidate "bypasslan", match: 1/1/24 (me/other/ike) Jun 20 21:35:21 pfSense charon: 09[CFG] <2> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Jun 20 21:35:21 pfSense charon: 09[CFG] <2> ignore candidate 'bypasslan' without matching IKE proposal Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> selected peer config 'con-mobile' Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> initiating EAP_IDENTITY method (id 0x00) Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP4_ADDRESS attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP4_DNS attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP4_NBNS attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP4_SERVER attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP6_ADDRESS attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP6_DNS attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> processing INTERNAL_IP6_SERVER attribute Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> peer supports MOBIKE, but disabled in config Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> authentication of 'access.hanserver.org' (myself) with RSA signature successful Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> sending end entity cert "CN=access.hanserver.org, C=CN, ST=A, L=B, O=C, OU=D" Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (1792 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (96 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 2 [ EAP/RES/ID ] Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> received EAP identity 'client1' Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> initiating EAP_TLS method (id 0x83) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 2 [ EAP/REQ/TLS ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (80 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (256 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 3 [ EAP/RES/TLS ] Jun 20 21:35:21 pfSense charon: 09[TLS] <con-mobile|2> negotiated TLS 1.2 using suite TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA Jun 20 21:35:21 pfSense charon: 09[TLS] <con-mobile|2> sending TLS server certificate 'CN=access.hanserver.org, C=CN, ST=A, L=B, O=C, OU=D' Jun 20 21:35:21 pfSense charon: 09[TLS] <con-mobile|2> sending TLS cert request for 'CN=IntranetCA-T1, C=CN, ST=A, L=B, O=C, OU=D' Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 3 [ EAP/REQ/TLS ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (1104 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (80 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 4 [ EAP/RES/TLS ] Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 4 [ EAP/REQ/TLS ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (1008 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (1376 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 5 [ EAP/RES/TLS ] Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 5 [ EAP/REQ/TLS ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (80 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (560 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 6 [ EAP/RES/TLS ] Jun 20 21:35:21 pfSense charon: 09[TLS] <con-mobile|2> received TLS peer certificate 'CN=client1, C=CN, ST=A, L=B, O=C, OU=D' Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> using certificate "CN=client1, C=CN, ST=A, L=B, O=C, OU=D" Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> certificate "CN=client1, C=CN, ST=A, L=B, O=C, OU=D" key: 2048 bit RSA Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> using trusted ca certificate "CN=IntranetCA-T1, C=CN, ST=A, L=B, O=C, OU=D" Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> checking certificate status of "CN=client1, C=CN, ST=A, L=B, O=C, OU=D" Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> ocsp check skipped, no ocsp found Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> certificate status is not available Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> certificate "CN=IntranetCA-T1, C=CN, ST=A, L=B, O=C, OU=D" key: 4096 bit RSA Jun 20 21:35:21 pfSense charon: 09[CFG] <con-mobile|2> reached self-signed root ca with a path length of 0 Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 6 [ EAP/REQ/TLS ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (160 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (80 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 7 [ EAP/RES/TLS ] Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> EAP method EAP_TLS succeeded, MSK established Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> generating IKE_AUTH response 7 [ EAP/SUCC ] Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> sending packet: from 124.116.232.99[4500] to 172.20.10.131[50242] (80 bytes) Jun 20 21:35:21 pfSense charon: 09[NET] <con-mobile|2> received packet: from 172.20.10.131[50242] to 124.116.232.99[4500] (112 bytes) Jun 20 21:35:21 pfSense charon: 09[ENC] <con-mobile|2> parsed IKE_AUTH request 8 [ AUTH ] Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> authentication of '10.0.2.102' with EAP successful Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> authentication of 'access.hanserver.org' (myself) with EAP Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> IKE_SA con-mobile[2] established between 124.116.232.99[access.hanserver.org]...172.20.10.131[10.0.2.102] Jun 20 21:35:21 pfSense charon: 09[IKE] <con-mobile|2> IKE_SA con-mobile[2] state change: CONNECTING => ESTABLISHED -
@SuperHans
The purpose of my identifier/peer identifier is that they match. What I do is choose IP address, then use one of my ip’s for my identifier, one of my peers for the peer and ensure the peer is configured with its pertinent info. -
@SuperHans
If this is for mobile, you pretty much have to choose any, unless you have something it can match. If using like radius and nps, it can’t determine user distinguished name by default. By setting to any, it just means all of the other auth requirements must be met, ie: cert, username and password, etc.