OpenVPN client subnet is not routed to IPSec tunnel
-
Hi,
There're two pfSense routers with IPSec tunnel setup in between. It's working fine with a single Phase2 entry which routes LAN traffic to the tunnel:
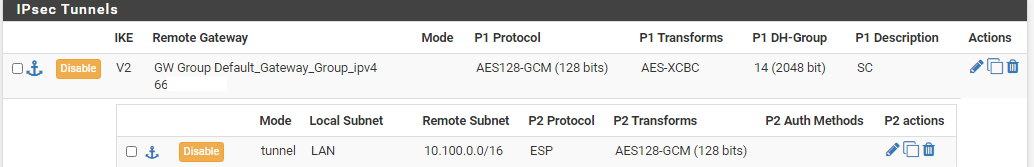
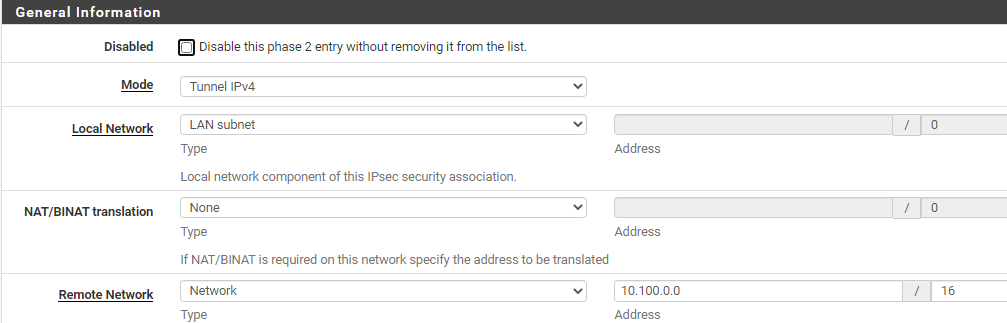
Now I added OpenVPN client subnet (well, for testing purposes just a single client IP at the moment) as a 2nd Phase2 entry:
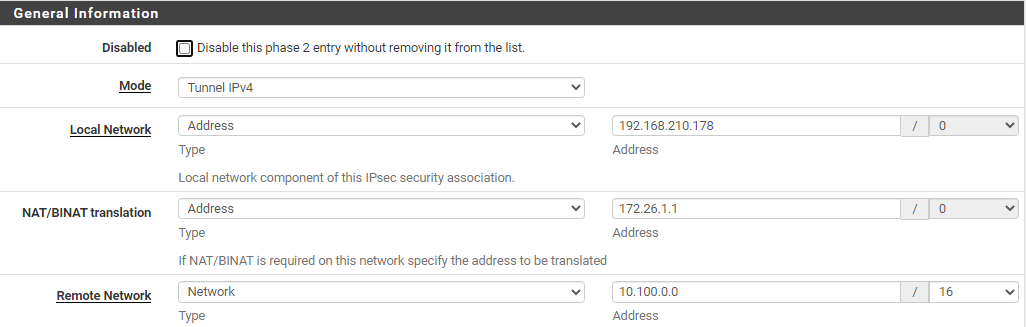
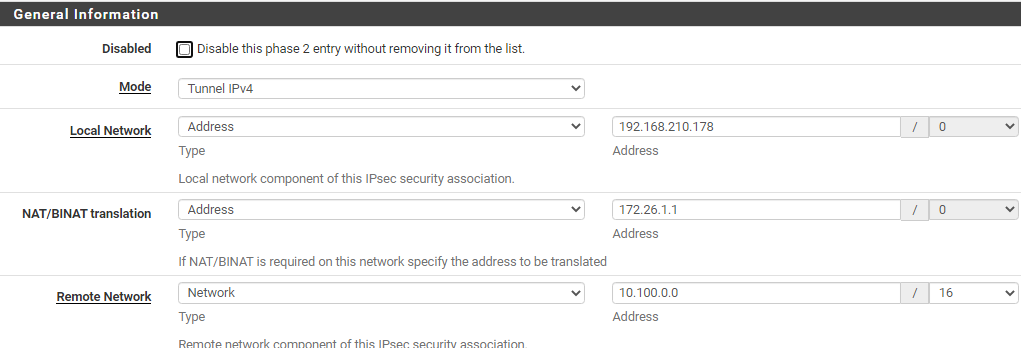
172.26.1.1 is local pfSense; I'm able to ping remote side from this IP:
# ping -S 172.26.1.1 10.100.10.114 PING 10.100.10.114 (10.100.10.114) from 172.26.1.1: 56 data bytes 64 bytes from 10.100.10.114: icmp_seq=0 ttl=63 time=143.874 msWhen pinging from openvpn client, I see the traffic coming into pfsense, but no traffic goes to the tunnel:
# tcpdump -nn -i ovpns3 host 10.100.10.114 and icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ovpns3, link-type NULL (BSD loopback), capture size 262144 bytes 15:45:08.440499 IP 192.168.210.178 > 10.100.10.114: ICMP echo request, id 1, seq 242, length 40 ^C 1 packet captured 3968 packets received by filter 0 packets dropped by kernel # tcpdump -nn -i enc0 host 10.100.10.114 and icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on enc0, link-type ENC (OpenBSD encapsulated IP), capture size 262144 bytes ^C 0 packets captured 50 packets received by filter 0 packets dropped by kernelThere're no blocking rules on in the firewall:
# cat /usr/local/etc/ipsec.conf config setup uniqueids = yes conn con2000 fragmentation = yes keyexchange = ikev2 reauth = yes forceencaps = no mobike = no rekey = yes installpolicy = yes type = tunnel dpdaction = restart dpddelay = 10s dpdtimeout = 60s auto = route left = 95.x.x.x right = 66.x.x.x leftid = fqdn:axxxxxxxx ikelifetime = 3600s lifetime = 3600s ike = aes128gcm128-aesxcbc-modp2048! esp = aes128gcm128-modp1024,aes128gcm128-modp2048,aes128gcm128-modp2048,aes128gcm128-modp2048,aes128gcm128-modp2048! leftauth = psk rightauth = psk rightid = 66.x.x.x rightsubnet = 10.100.0.0/16 leftsubnet = 172.26.0.0/16,172.26.1.1|192.168.210.178Please, help me figure out why the packets do not reach the ipsec tunnel.
-
Why are you doing BiNAT on your VPN Subnet (192.168.x.x) in the first place and not simply using it like your 10.100.0.0/16 in the first P2 phase?
Also did you configure your OpenVPN tunnel to actually route 10.100.0.0/16 via your VPN? Otherwise it won't reach pfsense in the first place.
-
It's b/c I don't want to make the other side aware of another subnet - it might be in use.
Also did you configure your OpenVPN tunnel to actually route 10.100.0.0/16 via your VPN? Otherwise it won't reach pfsense in the first place.
Where should I set this up?
As I mentioned, I do see the openvpn client traffic coming into pfsense thru the openvpn connection (seetcpdump -i ovnps3output in my 1st message) -
@jazzl0ver said in OpenVPN client subnet is not routed to IPSec tunnel:
Where should I set this up?
in your OpenVPN Server - where you define the "local" networks. There you can add further networks by adding them comma separated.
-
Yes, the route is in place. Otherwise I wouldn't see incoming packets in pfsense from my openvpn client.
-
OK if it is seen inbound on the ovpns interface, the route is there. :)
If it's not outbound via the IPsec tunnel (enc0) then the route from your OVPN RAS network isn't defined in a P2 of your tunnel so it isn't picked up by the ipsec service.
What is your OVPN tunnel network? The network your client gets assigned an address after dialing in?
Also if you want to hide it, I'd use a simpler BiNAT to an address that is not used on your firewall or the other sides network. -
Looks like you didn't read my 1st message completely :( I specifically showed my ipsec config. Check this part:
rightsubnet = 10.100.0.0/16 leftsubnet = 172.26.0.0/16,172.26.1.1|192.168.210.178So, I guess, this defines the P2 route.
My OVPN network is 192.168.210.128/26.
What do you mean by "simpler BiNAT"? I'm trying to use the ipsec functionality that is well-documented in pfSense docs (https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/nat-with-ipsec-phase-2-networks.html).
-
No, I didn't ignore it, but as I wrote you map your OVPN network to an IP probably in use in another phase or on the LAN? That's why I was mentioning, you should use another network or IP that isn't used on either side if you want to BiNAT or outbound NAT your 192.168.210.x/26 network
Also you were only NATting the specific IP .178 so if you didn't do some magic in OpenVPN you could get another random IP from your /26 subnet that won't get routed through the tunnel.
So you should setup your additional phase 2 to something like
- local net: 192.168.210.126/26
- BiNAT: <some IP NOT from your LAN or any network on the remote side>
- remote: 10.100.0.0/16
Sorry if you think I overlooked some details but you e.g. didn't tell us what the LAN(s) on pfSense or remote side are so I can only guess which IP ranges are in play and why your address of 172.26.1.1 didn't work. Is 172.26.1.0/24 the pfSense LAN side? Or is 172.26.x.y in use there?
How is the other side configured? Both P2s there? How is the additional P2 setup on the remote side? -
The point is that I want to use just a single P2 entry:
left right 172.26.0.0/16 -- ipsec tunnel -- 10.100.0.0/16and NAT any other possible subnets from the left side to the existing P2 left subnet or address (from 172.26.0.0/16 range).
Are you saying it's not possible?
PS Yes, I made that magic and openvpn always gives me a certain IP.
PPS left LAN is 172.26.0.0 /16
PPPS The other side has a single P2 entry (why are you saying both P2s?) with the same subnets (just swapped). As I said, ipsec tunnel works well, I can ping the other side from pfSense's IP (172.26.1.1) as well as from other left LAN PCs. -
Are you saying it's not possible?
Actually I'm not sure. Never even thought of using it that way but it could make problems as the 172.26.1.1 is on your LAN side and NATting ovpns0 to enc0 with that could screw with some routing logic as perhaps the IPsec deamon only picks it up coming from LAN. Could be that the rewriting done by NAT comes too late for that. But just a guess here.
PS Yes, I made that magic and openvpn always gives me a certain IP.
Alright, just wanted to check :)
The other side has a single P2 entry (why are you saying both P2s?)
Because the way I'd have it set up would have been like NATting the OVPN network to some IP not in use, say 172.27.1.1 and add another P2 entry to both sides with the corresponding network.
-
Addendum:
AH now I understand (after your edit with the "I want to use a single P2 entry"
Could you post your IPsec P2 again please?
I think I know why (and that) it won't work? -
Sure.
# cat /var/etc/ipsec/ipsec.conf # This file is automatically generated. Do not edit config setup uniqueids = yes conn con2000 fragmentation = yes keyexchange = ikev2 reauth = yes forceencaps = no mobike = no rekey = yes installpolicy = yes type = tunnel dpdaction = restart dpddelay = 10s dpdtimeout = 60s auto = route left = 95.x.x.x right = 66.x.x.x leftid = fqdn:axxxxxxx ikelifetime = 3600s lifetime = 3600s ike = aes128gcm128-aesxcbc-modp2048! esp = aes128gcm128-modp1024,aes128gcm128-modp2048! leftauth = psk rightauth = psk rightid = 66.x.x.x rightsubnet = 10.100.0.0/16 leftsubnet = 172.26.0.0/16,172.26.1.1|192.168.210.178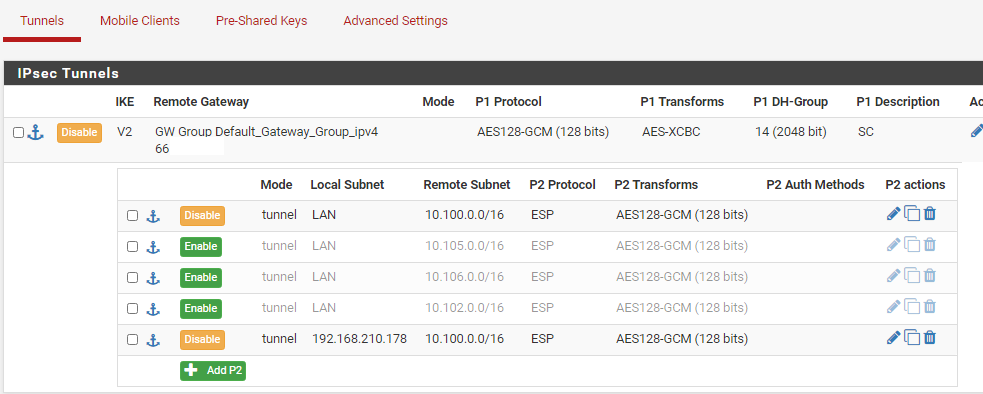
(And, yes, I tried to disconnect ipsec tunnel and restart ipsec daemon to make the changes applied for sure)
-
So you have two phase 2 entries, not just one. Do you have that on the other side, too? As you wrote:
The point is that I want to use just a single P2 entry:
I thought you only had one? If you define 2 P2s on one side, that has to match the other side. There's no way you can run "just one" on the other side. The Phases have to match.
Greets
\jens -
That makes sense! I indeed missed that point. Thanks for the explanation!
Is there a way to NAT a local subnet/address into pfsense's address, so it would travel thru the ipsec tunnel?
I just tried to add 192.168.210.178 to outbound nat but that didn't work:
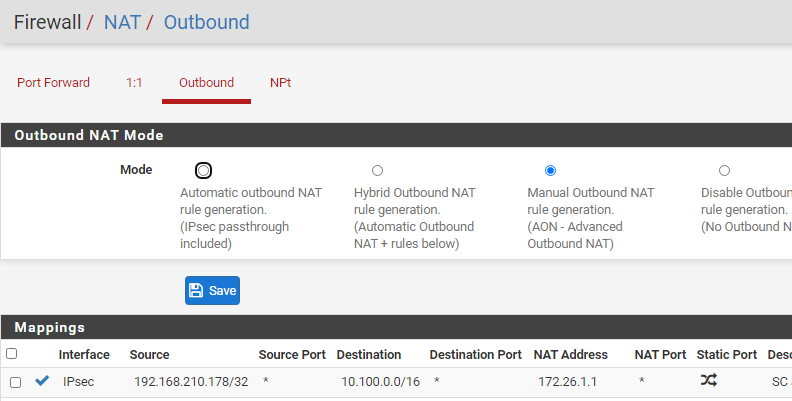
(Also tried to specify "Interface address" in NAT Address field) -
Hmm, I don't think that outbound NAT will work on IPsec with a NAT address from LAN but I'm unsure.
But as you told us in the OP, that both ends are pfSense? You could change the tunnel to an VTI style tunnel, then you can simply route your networks via the transfer net you define on the VTI phase and as there's a pseudo interface like in OVPN, it should also be possible to NAT traffic to your hearts content ;) as your tunnel has a fixed IP on one and the other side (the tunnel transfer net/gws) that you can NAT on.
-
Yeah, I'm aware of VTI, but this is not always possible. Anyway, thank you for your valuable help!
-
Glad I could be helping you :)