Default outbound interface
-
Is there a way to change the "default outbound" interface? For example, the "LAN" is always what it chooses as the source interface for functions like AD lookup, internal DNS lookups, etc. In my case I set the LAN up as a local only /30 mgmt interface. I could always move things around, but would be nice to know if you could change this.
-
huh? The source interface would be the interface in the network trying to talk to.. If the dest IP is in your lan /30 then yes it would use that interface as source.
How about you draw up your network, and the point out what exactly your wanting to accomplish. Or what you feel it should be doing but isn't
example: Here is a basic network, I assume you have something more than just lan, since you state your using that as management interface (only?) So you have at least 1 other network
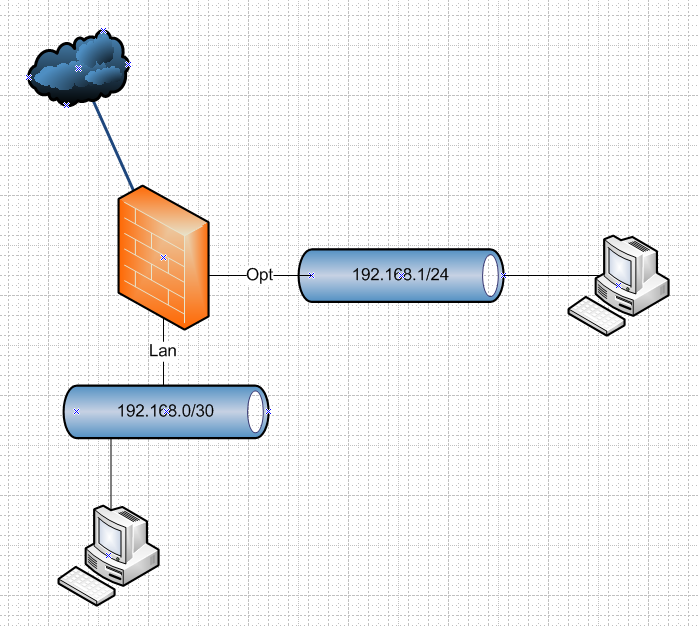
What do you feel is not working as it should, or what exactly are you trying to accomplish. in this sort of setup, lan and opt would not be natted when talking to each other. And only when either lan or opt network talking to internet/wan would traffic be natted to your wan IP..
So for example if device on opt network 192.168.1.X wanted to talk to device on lan network 192.168.0.X then the source interface talking to your lan /30 would be yes the lan interface. But the source IP for the traffic would still be 192.168.1.X no nat should be happening between these networks - unless you setup a gateway on them so pfsense thinks they are wan interfaces. Which you would never really do..
-
In my case I am very multi LAN. There are features that tie in to the idea of LAN and only apply there, like the "bypasslan" option in strong swan that only applies to the factory defined "lan", which I get and I know there are fixes waiting to test. Was just curious if I could define an alternate interface, with out that being the "factory lan". If not, I get it, but most other platforms have a way to define the source interface it uses for various tasks. My thought was, since the LAN has these unique attributes, peg an interface that will rarely be used to this, so no one interface has these chosen features applied to them, except the one that I will only use in a worst case scenario situation.
-
Also, my authentication servers and DNS servers live on the other side of a VPN tunnel, and that local management interface I'd rather not have routes to/for it, as it's a last bastion of hope in a bad situation.
-
@jgraham5481 said in Default outbound interface:
but most other platforms have a way to define the source interface it uses for various tasks
You mean what IP a service binds too - not sure what that has to do with router or firewall? What specific service are you talking about?
So you have some stuff are accessed via a site to site vpn? Well yeah there is going to be route to what network(s) are on the other side of the vpn.. Not sure what that has to do with interface or IP a service binds too..
I have read over your 2 post multiple times, and still no clue to what your actually trying to accomplish or what you feel is an issue.
-
OK Here's what I have:
WAN:
50.x.x.xLANs
172.16.120.1/30
10.0.13.254/24
10.0.60.0/24
10.0.61.0/24
10.0.62.0/24VPN
172.16.120.13/30So if I need to contact my auth server at 10.0.6.159 (on the other side of the VPN), it will always originate from 172.16.120.1, I would prefer it originate from 10.0.13.254. I do not have routes on the other side of the VPN for 172.16.120.1/30, nor do I want their to be any.
-
@jgraham5481 said in Default outbound interface:
it will always originate from 172.16.120
When what contacts it? Pfsense? You have this server setup as authentication server in pfsense.
-
It gets weirder, made the factory LAN 10.0.13.254/24 and made the 172.16.120.1 another interface (basically flipped the drop downs, and adjusted the IP's and DHCP, etc). Now when attempting to reach 10.0.6.159, it originates from the VPN /30 IP, so weird.