AWS multiple EIPs; NAT and VPN
-
Hello,
I'm trying to sort this out for over a week now with no success, so I'm asking for a bit of help :)
I have 3 pfsense instances in aws:
- each in different public subnet (different AZ)
- each have two interfaces, ena0 (WAN) and ena1 (VPN) in the same subnet
- each ena0 has EIP attached
- only one ena1 has EIP attached
Idea is to have 3 nat instances, each for different AZ that also acts as HA for VPN (both mobile and site to site). Each instance constantly does netcat VPN_EIP to check if VPN IP is responsive - if not it attaches VPN_EIP to its own VPN interface. That way whenever I shut down instance that currently is handeling VPN connections, VPN_EIP is moved to other instance and VPN connections are re-established.
Thing is that I cannot setup traffic for VPN_EIP on 2nd interface. Pfsense cannot even netcat VPN_EIP if it's attached to it's own ena1 and obviously I can't netcat from remote machine. Only way that I succeed was setting up virtual ip with VPN_EIP, but then I have response either if VPN_EIP is actual attached to instances eip1 or not, so netcat tests are false positive.
AWS part is rather ok, It's not fault of misconfigured security groups, source/dest check is also disabled. I'm quite sure that I'm missing something in routing/nat part as setting 2nd IP on EC2 always required route table edits, but I can't find any guides on how to do it on pfsense. EIP is provided by doing NAT by AWS, so pfsense has private ips on interfaces which makes things even harder for me.
Any guidance would be much appreciated!
-
OK, I got this finally. I've spend ridicules amount of time on this one and it seems to be some kind of bug.
So I'm starting with a clean installation. At the beginning instance has only ena0 configured and ena1 is disabled. Changing ena1 to enabled makes
Anti-Lockout Ruletravel to ena1 (1st thing that shouldn't happen if you ask me) and I can not access 443 using EIP on ena1, just private ip. Then I'm addingallow allrule to both interfaces so all traffic should be accepted and I still can not access 443.
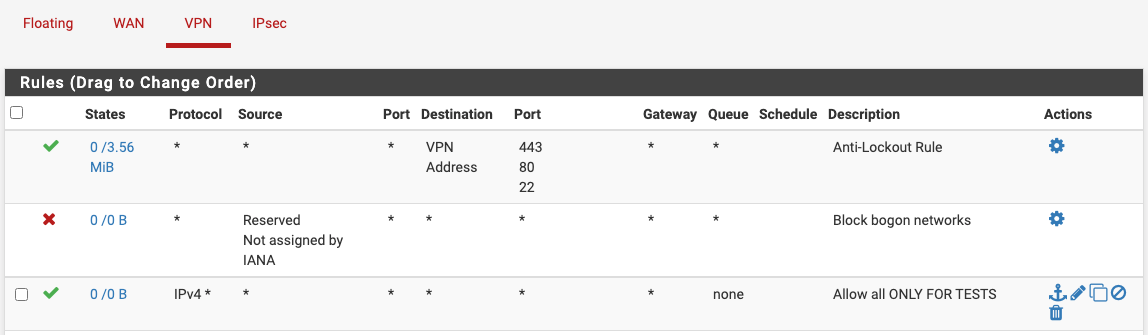
nc -zv $EIP 443does not work either from pfsense or remote computer. It works using private ip.Only after removing
Anti-Lockout Rulethings are getting back to normal.