Inquiry about multiple ip setup
-
hello guys, i was given block of ip by my ISP, 5 total, which i want to use( forward )or some LAN Pcs, so my question is shoud i use port forwarding or 1:1 NAT, ips are for example:
gateway 173.198.47.111
range of ip 112-116
mask 255.255.255.252
i have one pfsense SG-3100, two routers and one switch, i want to separate the 3 computers on the Lan network with the ips ranges 111-113 and have the rest with dhcp server on. OR should i just use one segment and just port forwarding those ip to the devices (lan pc), your thoughts.
thank you in advanced for the help. -
It depends what you're using those internal hosts for. If they are externally addressable servers you might only need port forwards there. If you need those hosts to use the new public IPs for outgoing connections 1:1 NAT will do that for you but you could add outbound NAT rules instead.
If your ISP is routing the new subnet to you you could use it dircetly on a new intercace/subnet internally.Steve
-
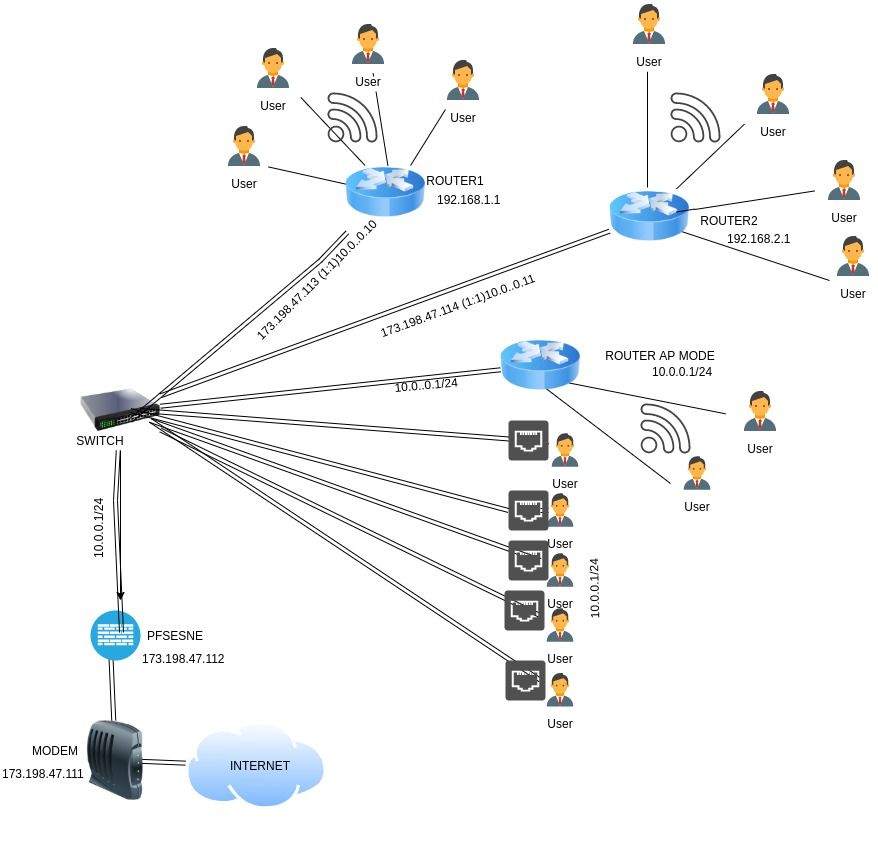
More details, i have 3 routers total, i want to forward two wan ip to those routers so whoever connects to those routers via wireless get a different external ip, i added the 2 virtual ips for the routers to use (Router 1-2) and i did 1:1 Nat to then with the ips with the respective rule. i use the third router as a AP wifi for the office Lan network. I believe there is a better way to do this (VLANS), so i am open to suggestions (noob here)
See the diagram i did, so you can get an idea.
thanks in advanced for help.
-
@ITECHNIFY
????
What's the point of sending 4 addresses to 4 users, only to NAT them? Why not give them public addresses? Also, why waste a public address on the other 4, when all you're doing is connecting a NAT subnet? Also, how are you getting the public addresses to the switch, when I only see 10.0.0.0/24 between pfSense and the switch.
-
Yes, you can do that. Yes, I would use 1:1 NAT for that.
It's quite common to see that in a shared provider situation, say 3 companies in the same building.
It would be better to separate them completely using VLANs from pfSense to the downstream routers though. As it is users behind Router1 would be able to connect to the other routers or users dircetly on the switch and pfSense cannot filter that.
Steve
-
@JKnott is a a special request, they wanted like that, i am forwarding the public ip to a internal router 1 and 2 ip, so whoever connects to those routers they get a different wan ip for the outside world. Now tell me what do you suggest and how will you do it, open to suggestions. thanks for the reply.
-
@ITECHNIFY
You have to be careful when you get those special requests. Often the person who's making the request doesn't really understand. I had one like that at work last year. This was on a large transit project and they had a couple of GPS receivers for NTP. They said to get the NTP from one company and then switch over to their own server when the other company's server failed. That is not the way NTP works. You use multiple sources and rely on redundancy. I have heard many other requests over the years that reflect ignorance of the tech. In those cases I try to find out why and often it's just a matter of they didn't know any better. There is nothing NAT can do for security that a properly configured firewall can't. So, now we wonder why they want NAT. This is one major area where people really don't understand that the reason for NAT was the IPv4 address shortage. If it wasn't for that shortage, there would be no need for NAT, but people are so used to using it, they think it's normal. It's not normal. It's a hack that also breaks things, requiring other hacks, etc..
So, what is their reason for using 1:1 NAT, when you could just route those 4 public addresses to the customer. Why waste a public address just to get to another router, when NAT is then used? An RFC1918 address is entirely suitable for that.
-
Thsoe IPs are in the WAN subnet (assuming they are real or representative) they can't be used directly internally.
A WAN VIP and 1:1 NAT is the correct way to this if they need to have those downstream routers. They might insist on it if those are separate clients for example.
Otherwise you could just have separate VLANs weth pfSense handling the subnets and the clients there directly. Just use a different outbound NAT rule for each to get different public IPs.
Steve