Move to Netgate XG-7100 ...
-
Hello, I'm working on a move from some old hardware (pfSense 2.3.4) to an XG-7100 (pfSense 2.4.5) and running into issues.
The old hardware (a HP server) has three NICs installed. One NIC for WAN. One NIC for management (MGMT). One NIC for several protected networks on different VLANs.
When I move to the XG-7100 I can get the WAN (Port 1) and MGMT (Port 2) NICs working fine. The problem is when I try to communicate with the protected networks (Port 3) I get no communication. I've tried several configurations including configuring the ETH1-3 ports as individual network interfaces but still can't get traffic on the protected VLANs to ping or communicate at all.
The biggest differences are the switch in the XG-7100 vs the three distinct NICs in the HP server and the pfSense version. I've tried to uncheck the default setting of "Enable 802.1q VLAN mode" thinking that Port VLAN mode may be a solution. Unfortunately I only have access to the MGMT interface and console at this time (thanks COVID). I've tried to configure the MGMT NIC over the console but can't get access to the MGMT NIC so I've had to roll back the config to get access to the web GUI again.
My questions:
-
Am I on the right track that moving from 802.1q VLAN mode to Port VLAN mode would resolve my issues of accessing multiple VLANs on a single switch port?
-
Is there a guide or document on switching to Port VLAN mode using the console? I've looked and didn't see anything.
-
Are there any other suggestions of things to try to get the protected networks accessible?
Thank you for your guidance.
Ben
-
-
how is port3( ETH3) configured on Switch part?
port 3 should be configured as (ex: vlan tag 50)
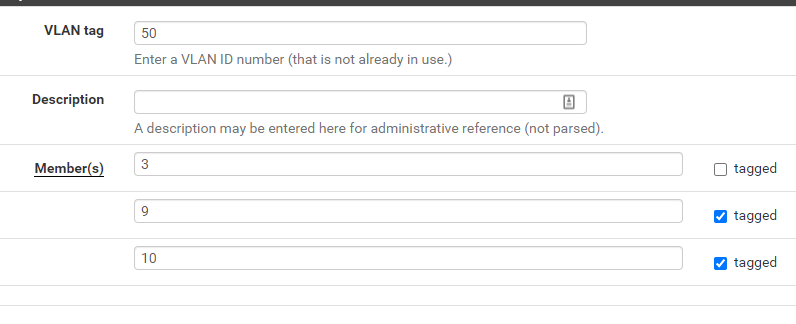
This video will help:
https://www.youtube.com/watch?v=NgRy14rYhV8 -
Thanks for the video. I did watch that one earlier this week and made a couple changes but they didn't help. That video is what made me realize I needed to re-configure the switch after turning off 802.1q VLAN mode. I think what the video was missing for me was how to add multiple VLANs to a single switch port.
Here's what the top part of my VLAN table looks like:
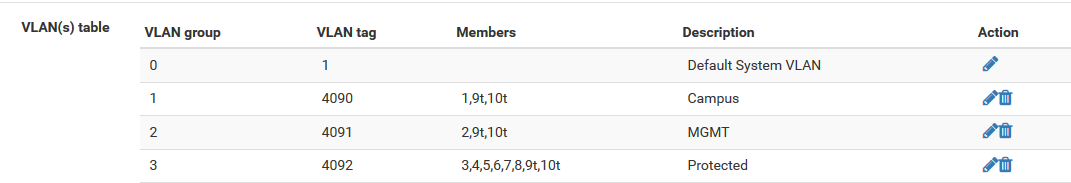
I also created additional VLAN groups for the protected networks I've tagged (e.g. HIPAA, PCI, etc.) and set the tag to what I have in the pfSense VLAN config. I assigned the same Members to those VLAN groups as I did to VLAN group 3.
-
Did you get this resolved?
You should be using 802.1Q mode and passing the tagged VLAN through the switch. So that means each of the VLAN you need should be setup on the switch with ports 3, 9 and 10 all tagged:
3t, 9t, 10t.Using port mode will pass your tagged traffic to the other ports which you don't want.
Steve
-
@stephenw10 I just checked the tagged box on the switch interfaces for the VLANs and that does appear to have resolved the issue. Thank you very much.
I have to do a little more testing and then I'll know but it looks like I'm back on track.
-
I just finished the cutover and indeed everything worked when I checked the tagged box for the VLANs in the switch.
Thank you everyone for your help. It feels good to have this done.