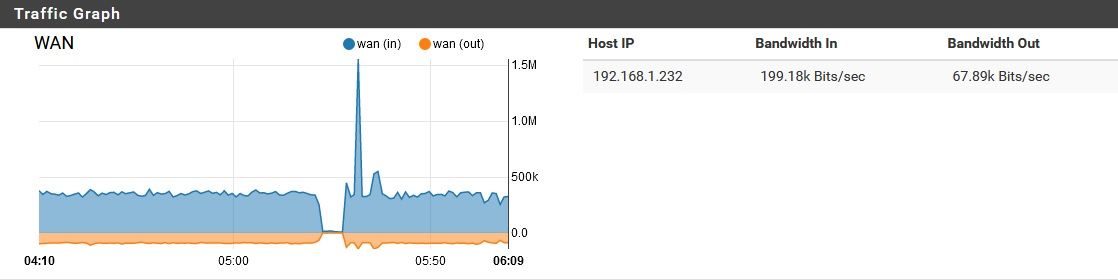
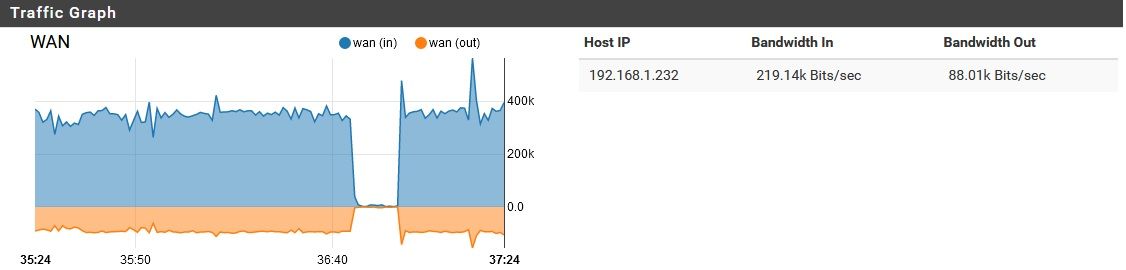
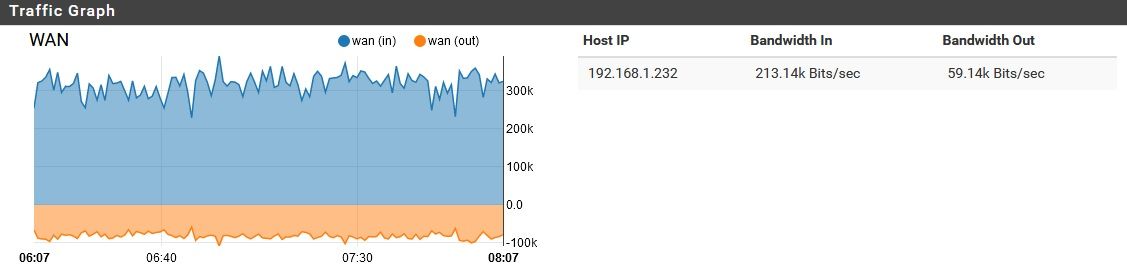
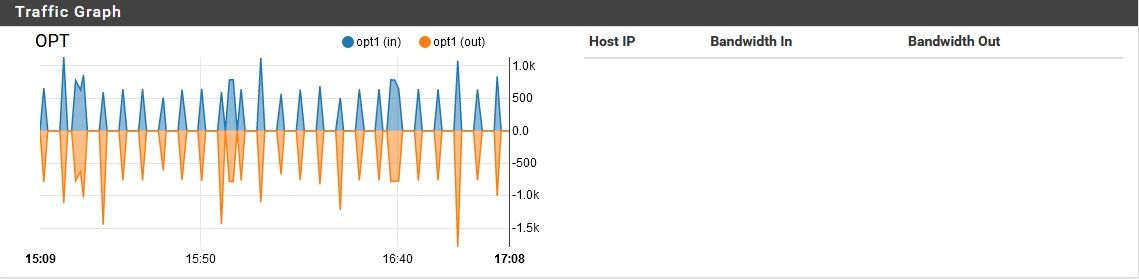
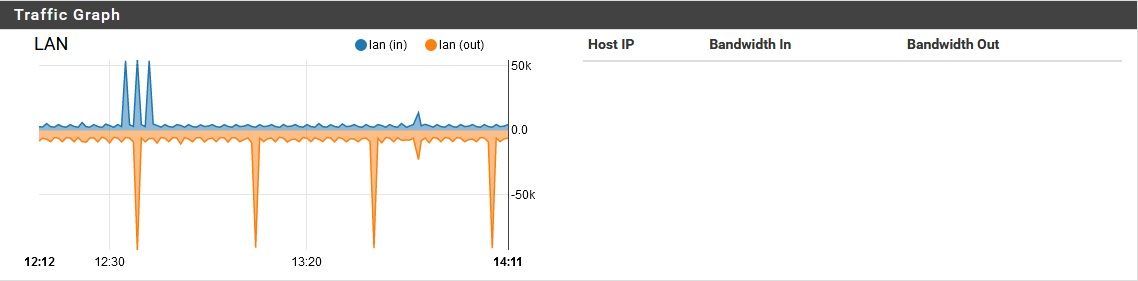
pfSense using unreasonable amount of bandwidth while idle
-
@johnpoz said in pfSense using unreasonable amount of bandwidth while idle:
well this one
https://www.spamhaus.org/drop/asndrop.txtis a bunch of AS numbers - those would have to be resolved to IP ranges or CIDR blocks..
Oh..that's interesting. It used to have the IP blocks themselves on that list. I'll remove that one. I should check through all of my lists...it has been almost two years since those were added.
Why are you loading all these lists? You don't even have any port forwards setup? I just don't get the reason for trying to filter shit when you don't even have anything exposed?
I don't have any ports forwarded right now although I did in the past. That is partially because I wasn't sure what was wrong on this network. If I regain confidence that nothing is vulnerable or compromised, I will probably open ports again. To be clear, I want to have open ports, but I'd prefer to make sure everything is shipshape before doing that again. It looks like this is probably a benign issue (although I still need to fix it), but I want to get it working properly first, just the same.
-
Vs trying to block the planet, if you are going to open up ports - its better to just limit what can talk to your ports. Example - I have plex open for friends and family. They are all in the US.. So I only allow US Ips to talk to that.. I don't load every possible bad guy list and block them - that is just insane to try and do that..
When I had someone outside the US, I added that country..
Sure in a perfect setup would only allow their specific IPs.. But then again they are users - asking them for their IP is like asking a monkey to explain theory of relativity.. And many of them use phones and travel, etc.
I would really if your not going to just nuke this thing from orbit and start over - which is what I would do.. Is turn off all this list shit..
You use bad guy lists, when that is the smaller list. Ie you want to serve up stuff to the globe - that is when you filter bad guy lists. Since that is smaller list ;)
-
@johnpoz said in pfSense using unreasonable amount of bandwidth while idle:
Vs trying to block the planet, if you are going to open up ports - its better to just limit what can talk to your ports.
You use bad guy lists, when that is the smaller list. Ie you want to serve up stuff to the globe - that is when you filter bad guy lists. Since that is smaller list ;)At the risk of continuing down the age-old "block the planet" vs whitelist dispute, the problem is, I plan to have incoming connections from six continents. Whitelist management is going to be a much bigger headache than some low-maintenance blacklists.
I would really if your not going to just nuke this thing from orbit and start over - which is what I would do.. Is turn off all this list shit..
Yeah, I'm leaning that way. I reverted this unit to a backup from December 2019. After fixing a few small things, it seems to be humming along without issues so far. It does still have the aforementioned fragments of the Suricata package, but hopefully that's irrelevant. After about 4 days, I have yet to notice these garbage DNS queries, although I may have missed some.
-
@CyberMinion said in pfSense using unreasonable amount of bandwidth while idle:
I have yet to notice these garbage DNS queries, although I may have missed some.
You should have ZERO of those - there is NOTHING that should create dns queries like that.. They can not resolve - they are garbage..
-
I hate to bump this to the top, but I just wanted to let you know that I have not seen any of this bad behavior from the firewall since restoring from backup. Whatever it was, it seems to be fixed. I just wish I knew the root cause.
Thank you for your help, everyone!
-
Mmm, weird. Thanks for following up though. Yeah it would be good to know what it was but that's probably not possible at this point.
Steve