PCI Compliance Scans
-
I have a client running 2.4.4-RELEASE-p2 on a Netgate SG-3100. They are getting flagged during their PCI scans because the IPsec VPN tunnel they have supports 3DES. They are not using the algorithm, but the port scan shows that the VPN server will accept it.
Is there a way to disable depreciated algorithms in IPsec so they no longer show they are available?
Thx in advance!
-
@tim-mcmanus: Check phase 1 AND phase two settings on ipsec
pages, and also the pfs group selected.
And consider upgrading to 2.4.5p1. Many security fixes are involved since 2.4.4p2 -
@netblues Thanks for the reply. Sorry for the belated reply.
I only have AES256 selected in phase 1 and only one other selected in phase 2.
These are the errors on the PCI Compliance scan:


I am not sure why the VPN is responding like that when I am not using any of those types of encryption. There is also no way to remove them or make them unavailable.
I also upgraded to the latest release prior to posting this.
Any additional suggestions are appreciated.
-
You sure they are scanning your pfsense - and not something else? Its unlikely it would provide des in its handshake, if it wasn't actually enabled.
-
@johnpoz said in PCI Compliance Scans:
You sure they are scanning your pfsense - and not something else? Its unlikely it would provide des in its handshake, if it wasn't actually enabled.
Thanks for the quick reply. I just checked and port 500 is the pfSense IPSec service.
-
Not saying its not... But are you actually seeing the traffic hit pfsense? Can you sniff on pfsense when they are doing the scan? Do you see their scan in your logs?
-
@johnpoz said in PCI Compliance Scans:
Not saying its not... But are you actually seeing the traffic hit pfsense? Can you sniff on pfsense when they are doing the scan? Do you see their scan in your logs?
I need to see if I can schedule a scan and see it work. I know it is finding other open ports that forward to other devices (QNAP server for instance) that is very unique, so it does seem like they're scanning the right device.
Here is a snapshot of some of the Phase 1/2 settings.
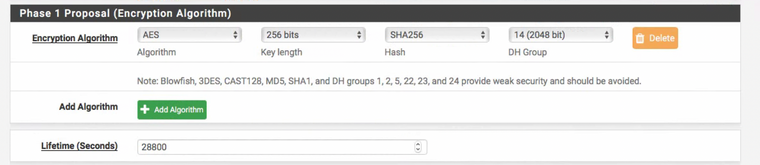

I'm not sure why they think those protocols are enabled.
-
@tim-mcmanus said in PCI Compliance Scans:
I'm not sure why they think those protocols are enabled.
exactly.. So you should see something like this in your log
charon: 14[CFG] received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 charon: 14[CFG] configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 charon: 14[IKE] no proposal found charon: 14[ENC] generating INFORMATIONAL_V1 request 3851683074 [ N(NO_PROP) ]You should see what they ask for, and what you return as options.
You could use a tool like ike-scan to test it on your own.
-
@johnpoz said in PCI Compliance Scans:
@tim-mcmanus said in PCI Compliance Scans:
I'm not sure why they think those protocols are enabled.
exactly.. So you should see something like this in your log
charon: 14[CFG] received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 charon: 14[CFG] configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 charon: 14[IKE] no proposal found charon: 14[ENC] generating INFORMATIONAL_V1 request 3851683074 [ N(NO_PROP) ]You should see what they ask for, and what you return as options.
You could use a tool like ipsec-scan to test it on your own.
Cool beans! I'll do that and see if I can schedule an ad hoc scan.
Thx!
-
Typo on my part ike-scan, not ipsec-scan ;)
-
Ok I see what might be going on... Hmmm
I just fired up a ipsec, and ran ike-scan on it.. And yeah so you can see where asking for des. and what gets returned
Oct 3 21:11:46 charon 10[CFG] <1> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Oct 3 21:11:46 charon 10[CFG] <1> received proposals: IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_768All of the options are returned, even though not possible to use it... Hmmm That should be simple enough to fix, but don't think you can do it in the gui.
I don't really ever do ipsec with pfsense...
-
@johnpoz said in PCI Compliance Scans:
Ok I see what might be going on... Hmmm
I just fired up a ipsec, and ran ike-scan on it.. And yeah so you can see where asking for des. and what gets returned
Oct 3 21:11:46 charon 10[CFG] <1> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Oct 3 21:11:46 charon 10[CFG] <1> received proposals: IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_768All of the options are returned, even though not possible to use it... Hmmm That should be simple enough to fix, but don't think you can do it in the gui.
I don't really ever do ipsec with pfsense...
I don't either, but my client has a vendor that needs to occasionally access some internal systems. The only thing they could get working on their end was IPSec. SMH.