Firewall rules to create a guest network
-
@akuma1x That is some advanced ruling.
I like it.
Although, if you have a cable-modem, it will probably not blocked by this. -
@Bob-Dig said in Firewall rules to create a guest network:
Although, if you have a cable-modem, it will probably not blocked by this.
I don't understand what you mean here... And, I've got a DSL internet connection.
Jeff
-
@akuma1x I just thought about the block of WAN net and why someone would want that, but my "explanation" for that was wrong.
-
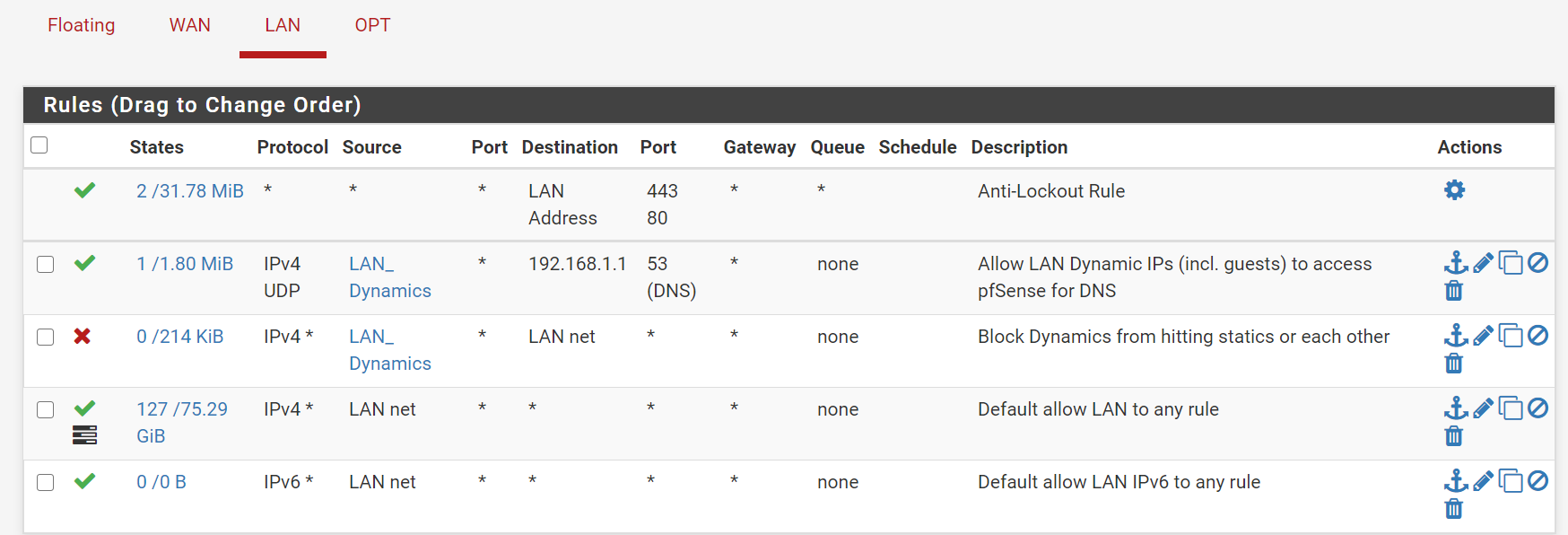
You would usually block the WAN subnet because it includes the WAN address and any VIPs you have on it which would otherwise allow GUEST hosts to access the firewall services listening on those. You can also use the system alias 'This firewall' for that and that also includes all other firewall IPs. For exmaple:
In that case I have to allow DNS access to the firewall because it would otherwise be passed by the policy routing load-balance rule which would send it out of the WAN uselessly.
The LOCAL alias contains all my local subnets.
Steve
-
I highly recommend implement VLANs to isolate your guest and office traffic since pfsense (installed on netgate hardware or desktop) is very much capable of doing that.
from the guest vlan you can simply block access to office vlan + pfsense, etc. And to allow access to Internet create another allow rule and put it below the block rule.
refer to the links below to help get your idea about vlans
https://www.youtube.com/watch?v=CDUyMpBC8bw -
@akuma1x said in Firewall rules to create a guest network:
and keeps my kids game boxes off the guest wifi network.
This won't happen with a rule on the guest network./
You have to filter them on the interface they are connected.
-
@DrPhil
Both SSID you see are on the same network. Your router supports dual band. One SSID is 2.4 GHz and the other is 5GHz. Your laptop or smart-phone is probably seeing both bands ... older devices can see 2.4 GHz only ... I don't understand if there is really an option in your router that can isolate the traffic being grey out -
@DrPhil
You can try create another alias for static IPs and name it LAN_Statics and populate it with a list of static ips. Then in the block rule you've already created set the source to LAN_Statics. Also make this rule as the second (below the default Anti-Lockout Rule). -
@wintok said in Firewall rules to create a guest network:
@DrPhil
You can try create another alias for static IPs and name it LAN_Statics and populate it with a list of static ips. Then in the block rule you've already created set the destination to LAN_Statics. Also make this rule as the second (below the default Anti-Lockout Rule). -
@netblues said in Firewall rules to create a guest network:
@akuma1x said in Firewall rules to create a guest network:
and keeps my kids game boxes off the guest wifi network.
This won't happen with a rule on the guest network./
You have to filter them on the interface they are connected.
Um, yes it does. If they happen to join the guest wifi network ('cuz the password is hanging on a bulletin board in the kitchen for guests to see) with their game boxes, they get assigned an IP address. It is with this IP address that I can then set NO ACCESS and block them from getting to any other destination. Essentially, it's a dead end. I don't know if this is the best way to accomplish my goal, but it works and is pretty simple to implement.
On the interface they are connected to 99.9% of the time, the LAN network, there is filtering there for the game boxes, like throttling and scheduling. Works perfectly.
Jeff
-
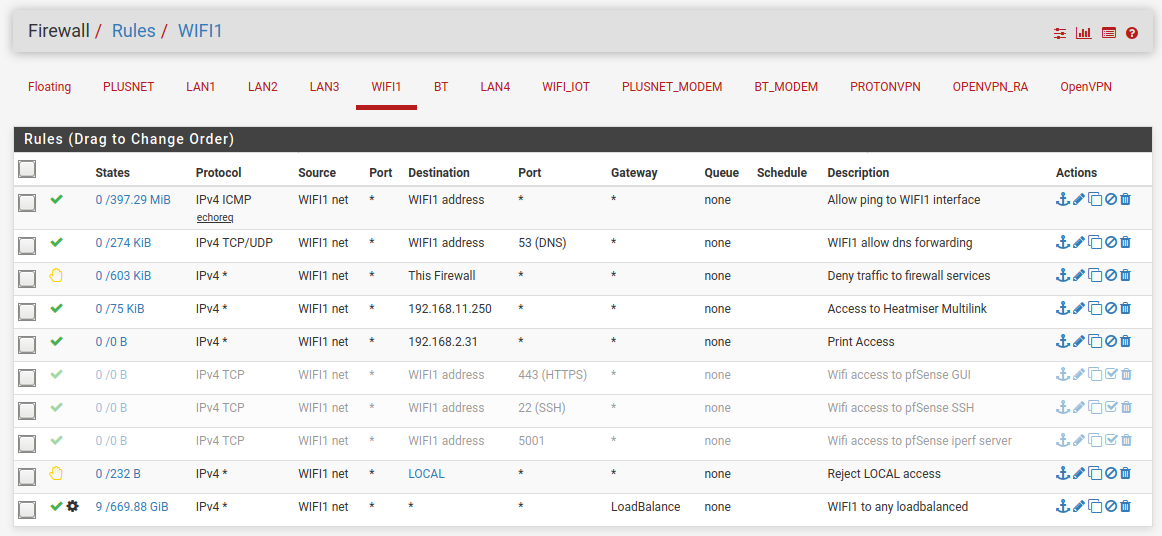
As requested I will post screenshots, but I think this is still a WIP as some of these rules are set automatically internally, so I could cleanup, and I notice also that I have ALTQ queues defined when ALTQ is off now, but hopefully gives you an idea what I meant.
Managementports alias points to ports 80,443,22 to block ssh, and webui access to firewall.
guest_ntp_dns points to ports 53,123,853 to allow dns/ntp access on firewall.
The nolog rule near bottom is to disable logging for some extra packets that get blocked from the walled garden setup, and were been logged because I decided to log the blocked packets, so that was to disable logging for those packets.
Guest_ports is allowed ports on walled garden, its an expansive list as I include ports for some android and social media apps as well as email. Will attach pic for it also.
Also as has been pointed out, you need to have the ability to have an isolated WAP setup that uses the guest VLAN. Unless you ok with all wifi clients been on the main LAN.