wireguard gateway - how to remove need for double NAT
-
Hi there,
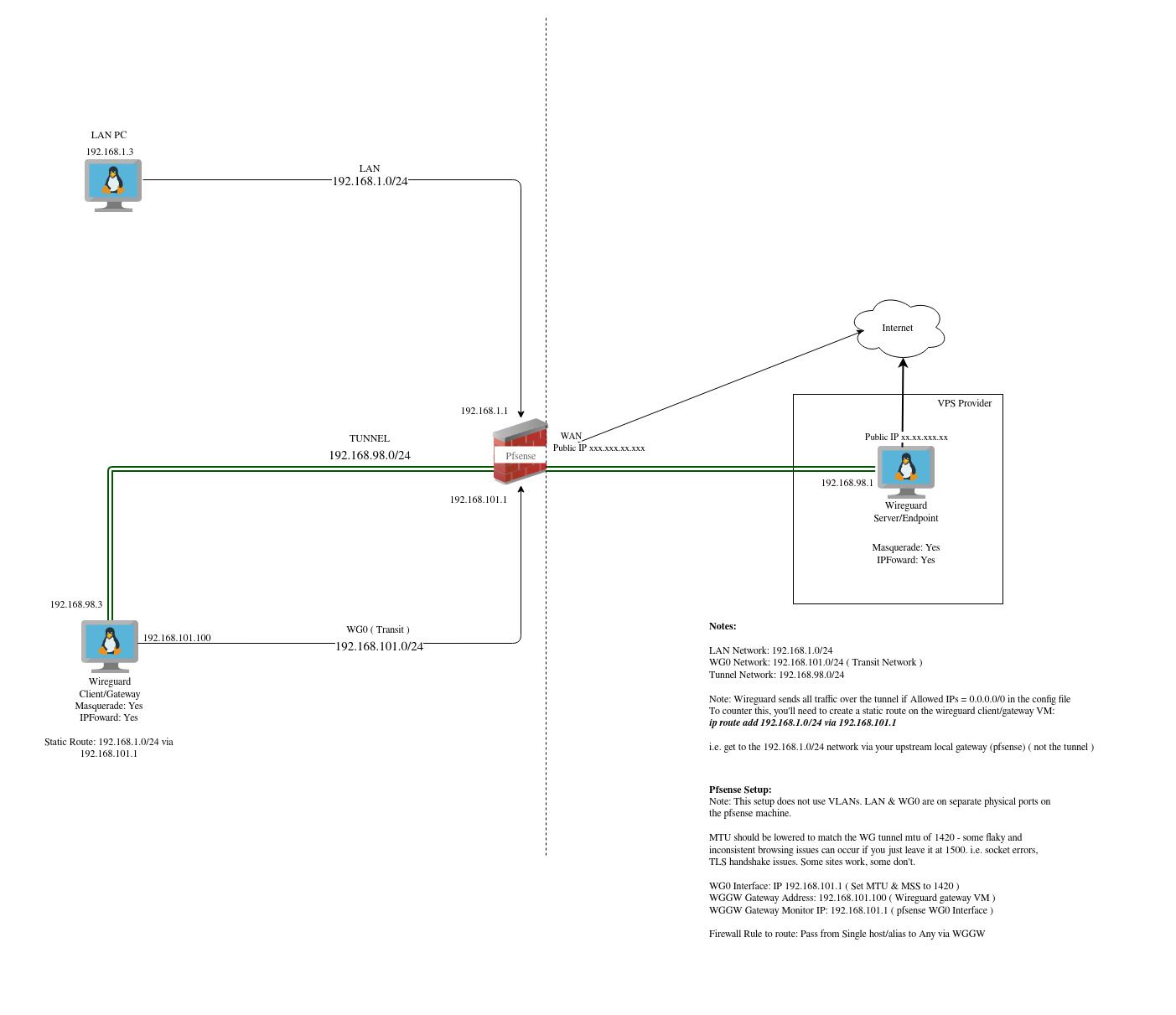
I've got a question about how I can achieve the setup i have now, without needing two lots of NAT.See the pic for detail, but essentially i have a VM on a separate subnet to my main LAN that i am using as a transit network ( to avoid issues with possible asymmetric routing ). This VM is essentially a gateway/client to allow traffic to enter a wireguard tunnel. It is connected to a VM in a VPS which is the wireguard endpoint.
both these VMs have IP Forwarding turned on + Masquerade.
I've setup a pfsense gateway and set it's IP to the VM that acts as the wireguard client/gateway, and then use LAN firewall rules to point certain LAN clients at that gateway. This then routes those LAN clients out the VPS endpoint to the internet.
It all works perfectly - however, I think it's not "right", I'd prefer not to have to need two lots of Masquerade. Effectively I'm Double NAT'd.
How can I get the same outcome as this, but not needing masquerade on either the local VM or the endpoint in the VPS? Static routes? I'm just not sure what or how ( i'm not a networking expert by any means! ).
Cheers
Seb
See pic for detail on the current setup:
-
@Sebastiaan76 said in wireguard gateway - how to remove need for double NAT:
's not "right", I'd prefer not to have to need two lots of Masquerade. Effectively I'm Double NAT'd.
How can I get the same outcome as this, but not needing masquerade on either the local VM or the endpoint in the VPS? Static routes? I'm just not sure what or how ( i'm not a networking expert by any means! ).
Cheers
Seb
See pic for detail on the current setup:@Sebastiaan76 did you every make any headway on this?
I am having a similar double NAT issue when using another server as a gateway (eg. like your Wireguard client/gateway).
-
Hi there,
Yes, I did resolve this in the end. The key for me was Static Routes on the Wireguard Gateway VM on my local network, I also set a static route on the Endpoint to send any traffic with my LAN IP addresses back over the wg interface.I didn't realise that if you set your wgx.conf to use AllowedIPs= 0.0.0.0/0 it forces ALL traffic over the wireguard interface, so returning traffic never gets back to the client that initiates the connection.
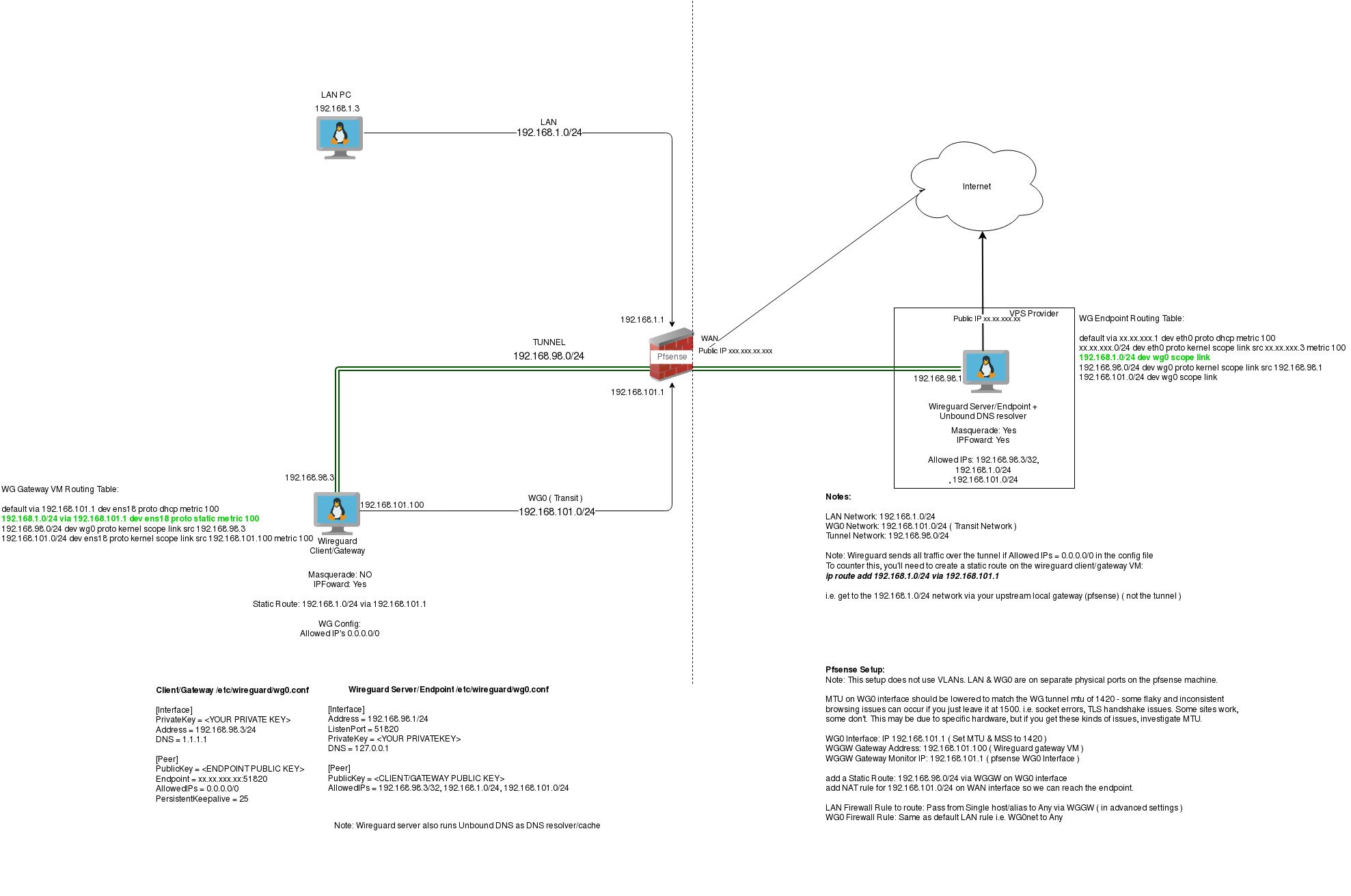
Anyway, a picture is worth a thousand words, and see my updated diagram here. Apologies to the Network Engineers out there. I'm not a pro, so I guess my diagram is pretty amateur! It serves it's purpose for me as documentation though :)
In the pic, you can see the routing table on the WG Gateway VM and the WG endpoint. The routes in Green are the ones I added manually, and it all works like a charm now. Also, note the MTU thing, that caused me no end of grief, so if you have issues with SSL handshakes failing and other random stuff....check your MTU.