How to pass VLANs from two seperate interfaces to main Switch?
-
Hi,
Couldn't think of any better title (feel free to edit) but this what I'm dealing with atm. First off, this is a simplistic view of my home network:
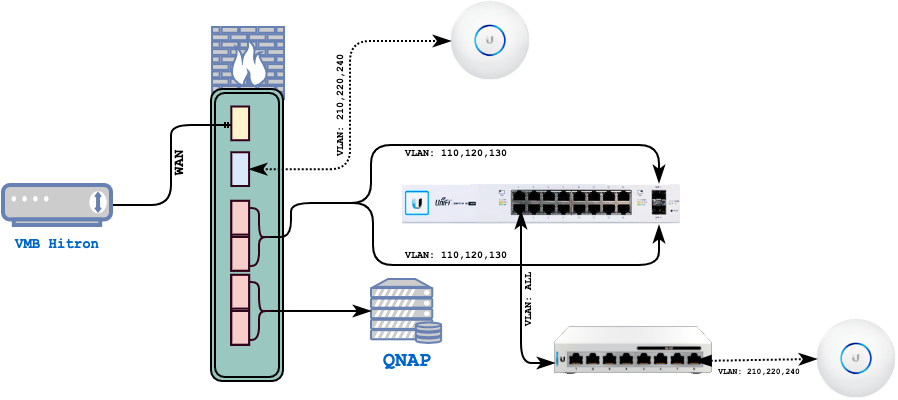
Main Area:
pfSense running with 6 ports:- Port 1
Connected to WAN - Port 2
Connects to main AP (uap1) + carries 3 VLANs, only used by the WiFi clients - Port 3+4
Forms LAGG1, carries another 3 VLANs used by different LAN clients, connected to the main SWITCH (usw1) as UPLink - Port 5+6
Forms LAGG2, directly connected to the STORAGE (qnap) facility
Secondary Switch Area:
P1of the main switch, carrying all the tags, connected toP1of the 2nd SWITCH (usw2) as the UPLinkP8of USW2 connected to 2nd AP (uap2), supposed to carry all of the WiFi VLANs
IP Address:
- SW1, SW2 and AP2 are configured with the interface IP of
LGGA1(10.0.11.xx)main - AP1 is configured with the Interface IP of
PORT-1(10.0.12.xx)
Every thing okay apart from AP2, which doesn't seem to see the VLANs (210,220 & 240) that I'm expecting. Is it b'cuz of the SW1 is connected to LGGA1, where as
22xVLANs are created on a different physical interface? Is there a way pfSense can also make those VLANs available to SW1, so that it can be passed on to SW2? - Port 1
-
How should pfSense know to send out packets destined to the 22x VLANs to SW1?
You will need additional VLAN interfaces on the LAGG1 and bridge them with the others if you realy want them to be within the same subnets. -
Not sure why you would want to bridge anything?
But if your going to have downstream switch with vlans on it, then those vlans have to be on your trunk that connects to your upstream switch to pfsense.
So on lagg1 create your vlans for your downstream switch..
Why can you top AP not just connect to sw1? Or put another switch where pfsense is, and use that for all your vlan connections.. You could then connect AP there, then run them also down to sw1, and your other downstream switch.
I would never recommend bridging interfaces on pfsense for such a setup. But if you want it setup like you have drawn, then you have to bridge that interface that connects to your top AP and also add your other vlans to that lagg for the downstream switch.
-
@johnpoz said in How to pass VLNAs from two seperate interfaces to main Switch?:
But if your going to have downstream switch with vlans on it, then those vlans have to be on your trunk that connects to your upstream switch to pfsense.
So on lagg1 create your vlans for your downstream switch..
Why can you top AP not just connect to sw1? Or put another switch where pfsense is, and use that for all your vlan connections.. You could then connect AP there, then run them also down to sw1, and your other downstream switch.
The reason AP1 is not connected to the main switch, so that two networks can run side-by-side independently (as long as pfSense is running okay) and don't get yelled by family for taking the Internet down (unintentionally) because I rebooted the switch
 It gives great flexibility- I can play with the Switches taking it up and down whilst rest of the members still can use the Internet.
It gives great flexibility- I can play with the Switches taking it up and down whilst rest of the members still can use the Internet.Anyway, so bridging interfaces is the only way to achieve what I want for the AP2 if I keep the setup like that? And doing so, can I still keep off the dependency between the switch and the
AP1?-San
-
Not sure why you would ever take a switch down, other than the 2 minutes it takes to upgrade its firmware.. But ok ;)
Or maybe you were moving it to a new location? You can play with configs all you want on a switch, doesn't take anything down other than say the ports your messing with, etc.
But how you have it drawn the only way to get that AP to have the vlans on it that are the same as the switch connected to the lagg would be to yes bridge that interface with your other ports. Which is just a horrible idea if you ask me.
If what you wan to do is play with switch 1 and up and down it all the time, etc. Then I would get another switch upstream of it to connect your AP and to run your lagg through - so your not "bridging" The only time I would ever bridge anything on a router is I needed a to put say a fiber connection on the same L2 as some ethernet port.. And my switch didn't have a fiber connection and the router did.. And even then it would just be done long enough until I could get a switch with a fiber connection on it ;)
I take it the only reason you can not just use your little downstream switch for both your APs is location?
I take it that little downstream is a poe switch - so wouldn't it make more sense to just use it for your APs?
If you haven't guessed - not a fan of bridging on a router ;) While there are specific use cases where you would have to do it.. For me it would always be the last possible, hold a gun to my head sort of reason.. I would do everything I could to work out a better way ;)
For example get another switch that you "don't" take down to play with and connect interfaces to that before you run the connects to your switch you do want to play with ;)
BTW - what exact hardware are you using for pfsense? A 3100 or 5100 for example have switch ports on it.. So you wouldn't have to "bridge"
-
I don't like bridging either but my one of the main objectives is keep the primary WiFi network independent of anything as much as possible. I have had a situation where the Switch went down and that took WiFi out as well even though the Internet from ISP was fine and then I had to deal with two things at the same time - move the AP out of the switch and then deal with the switch itself. Just wanna see history being repeated itself. But I agree that it does bring some other challenges.
The point above is the main reason for not connecting the both AP to SW2. Another reason is doing the cabling - next to impossible to lay the cable from SW2 to AP1 now. The both of the switches are PoE but AP1 cannot make use of that b'cuz of the point above/one again.
The pfSense box is a Dell R220 with 2x on-board Broadcom NIC + 4-port Intel I350-T4. Anything else better can I do with it?
-S
-
With your limitations - the only thing to do how you have it drawn, is bridge..
-
What if I put a switch (got a small un-managed one in hand) in between PF and AP1 and then run another cable between the un-managed and SW1? Then the SW1 will have all the VLANs, right? Would that work? I suspect in that case switch got to handle 2x UPLinks, I suppose?
-S
-
Yeah I already suggested you could add a switch upstream of sw1 between pfsense and it, and use it vs having to bridge.. But I wouldn't get a dumb one.. Get something smart..
You seem to like unifi so - but its a bit pricy to be honest at $100
https://www.ui.com/unifi-switching/unifi-switch-flex/The mini would be perfect and only $30. But couldn't power your AP. And I don't think it can do lagg.
https://store.ui.com/collections/unifi-network-routing-switching/products/usw-flex-miniOr you can pick up any smart switch for like $40 (non poe).. While sure a dumb switch could prob pass the tags.. It would be able to do lagg.. I show the DGS-1100-05 on amazon (can do 1 lagg group) for $38
-
finally started working, following @johnpoz 's route. I This is what it looks like now:
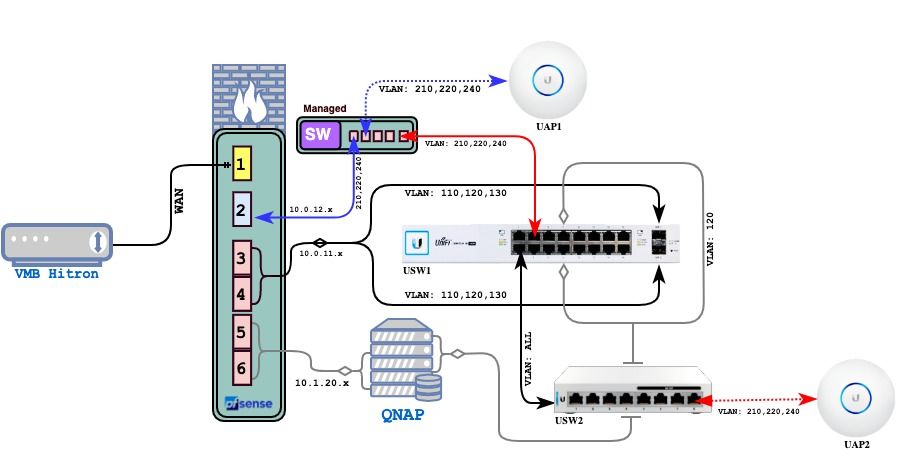
I was using a cheaper TP-Link managed switch (tlsg108e) before, which wasn't working as expected, for the reason I couldn't figure out. Then I remember I had a Linksys LGS318P collecting dusts somewhere and using that all started working. This way, now I can take the WiFi VLANs all the way to AP2 through the downstream switch and also the primary WiFi and the Unifi Controller can run independently of the main switch.
LGS318P is a bit overkill for my purpose but it worked in the end and it PoE (so that AP1 is directly connected to it) and I didn't have to pay a dime for it.
-S
-
@MacUsers said in How to pass VLNAs from two seperate interfaces to main Switch?:
I was using a cheaper TP-Link managed switch (tlsg108e) before, which wasn't working as expected,
Not surprising. Some TP-Link gear has problems with VLANs.
-
@MacUsers said in How to pass VLNAs from two seperate interfaces to main Switch?:
I was using a cheaper TP-Link managed switch (tlsg108e) before
Yeah as @JKnott mentions some of those tplink switches don't do vlans correctly.. What hardware version, what firmware were you running.
The problem was they would not allow removal of vlan 1 from ports.. they corrected it (finally after over a year of complaining about it on their forums) But they only released it for v3 of hardware. But there is a thread around here where you could put the v3 firmware on the v2 hardware (they made no mention of this in their release notes) From my testing did work.
So if you want to try and use your tplink device again.. See what version your on, and if you can remove vlan 1.. If you can not remove vlan 1 then the device is really no better than a dumb switch with an IP address on it ;)
-
@johnpoz said in How to pass VLNAs from two seperate interfaces to main Switch?:
Yeah as @JKnott mentions some of those tplink switches don't do vlans correctly.
Not just switches, my AP too. You may recall my recent discussion about my guest WiFi. I made no mention of IPv6, because I had to disable it on that interface, so that the guest WiFi would work properly. Even now, IPv6 capable devices get an IPv6 address. They just can't do anything with it. When I get a better AP, I'll enable IPv6.
-
re. TP-Link, I actually never understood their VLAN configuration page. Every time I think
I got it nowuntil the time I realize it's still not working. So I sort of stopped using their kit.The Linksys one a bit overkill but sits nicely in the rack and this is what it's looks like now (if anyone interested....)


-
@johnpoz said in How to pass VLNAs from two seperate interfaces to main Switch?:
But how you have it drawn the only way to get that AP to have the vlans on it that are the same as the switch connected to the lagg would be to yes bridge that interface with your other ports. Which is just a horrible idea if you ask me.
If you haven't guessed - not a fan of bridging on a router ;) While there are specific use cases where you would have to do it.. For me it would always be the last possible, hold a gun to my head sort of reason.. I would do everything I could to work out a better way ;)
As I mentioned I didn't like interface bridging as well, looking at just how inconvenient it becomes in my case but will be able to explain why it's a bad idea in general - purely from technical (and from security, if any) stand-point pls? I tried to google it a bit but nothing coming out that inconveniencing. Any pointers?
-S
-
@MacUsers said in How to pass VLNAs from two seperate interfaces to main Switch?:
in my case but will be able to explain why it's a bad idea in general
Performance for one - there is no way your going to be able to bridge in software as fast as you can with doing it on in hardware on a switch.
2nd just complexity of configuration. Users can barely understand firewall rules on an interface, let alone on a bridge.. Are you doing the rules on the interface, or the bridge, etc.
3nd would be misuse of a router port.. A discrete interface is way more valuable as actual interface to do routing with, than to try and use it a sub optimal switch port. When switch ports are cheap!!!
There are cases when bridge on your firewall makes sense - but to be honest it is almost always would be the last choice if can do it cheaper, simpler and easier config.