How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver
-
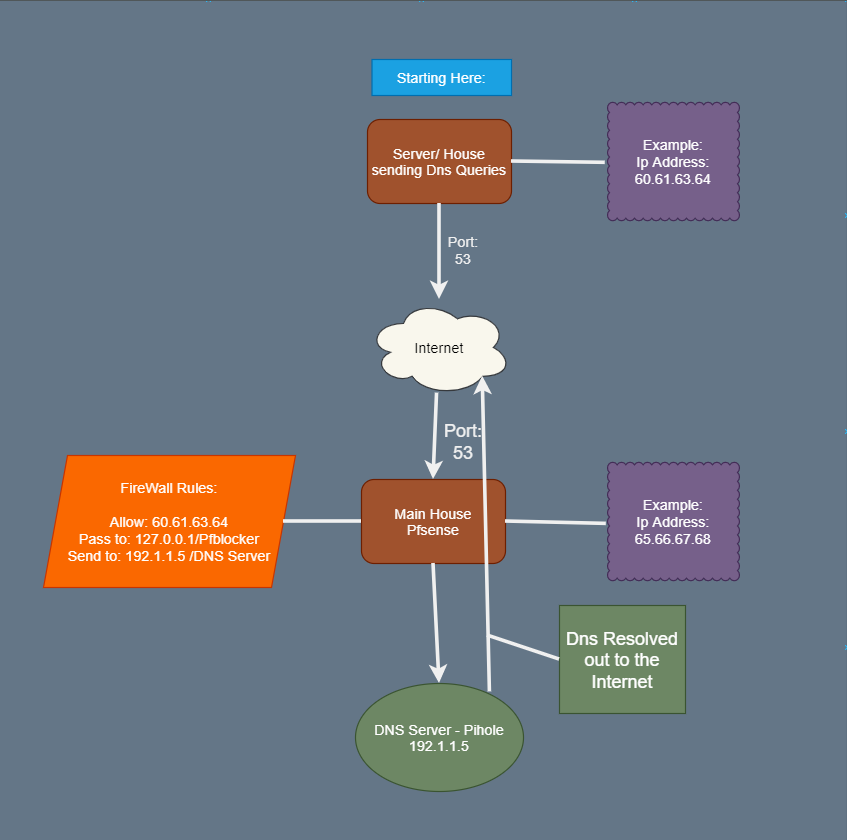
I have a House/ Server that is sending Dns Queries to my second house.
I need the Dns Queries to be resolved and sent to my pfsense 127.0.0.1 locally (192.1.1.1/24) then passed to my pfblocker. Lastly, pasted down to Pi-Hole that's 192.1.1.5. then it goes back to pfsense to be sent on DOH - Dns over https to cloudflare.Why its not working?
I have no clue except that somehow the dns isn't getting to my pfblocker and I don't why that is. If it is doing that.
Or
After it gets to the pfblocker it gets sent to 192.1.1.5 the dns server - Pihole it just doesn't make it.
(This is unlikely because I have tried cloud flare after it gets to pfblocker and still doesn't work. + When I am using 192.1.1.5 everything goes through when I am using the firewall for browsing websites Normally.)Reasons Why?
It isn't possible to have the dns queries to have the first house to have there own custom pfsense &/or pi hole. I don't any blocking capability on the network what so ever. This is my only option. I have a google cloud that's a Dns Server only allowing to accept Dns from specific
Ip Addresses on the list. Yes it is: Pi Hole on the google cloud platform.Settings:
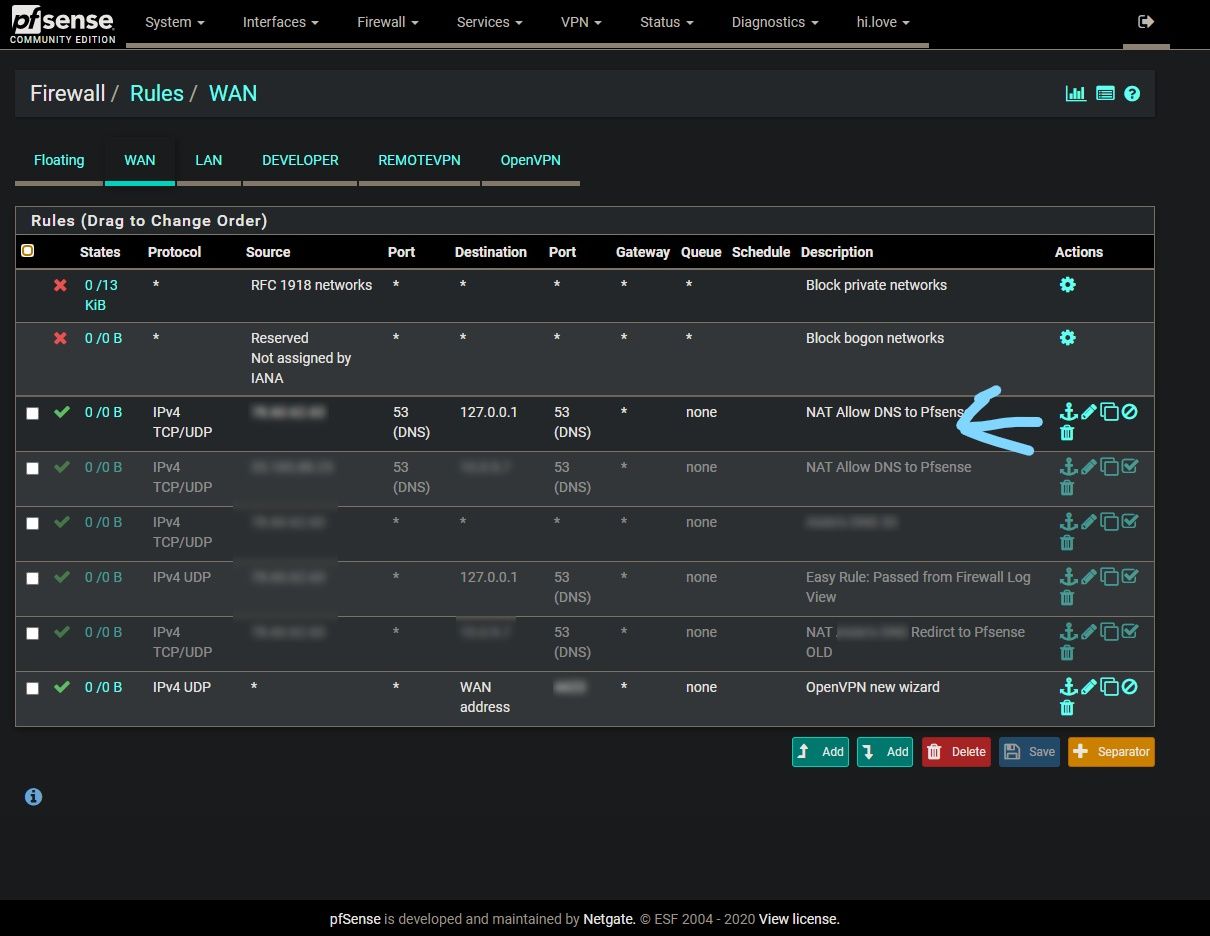
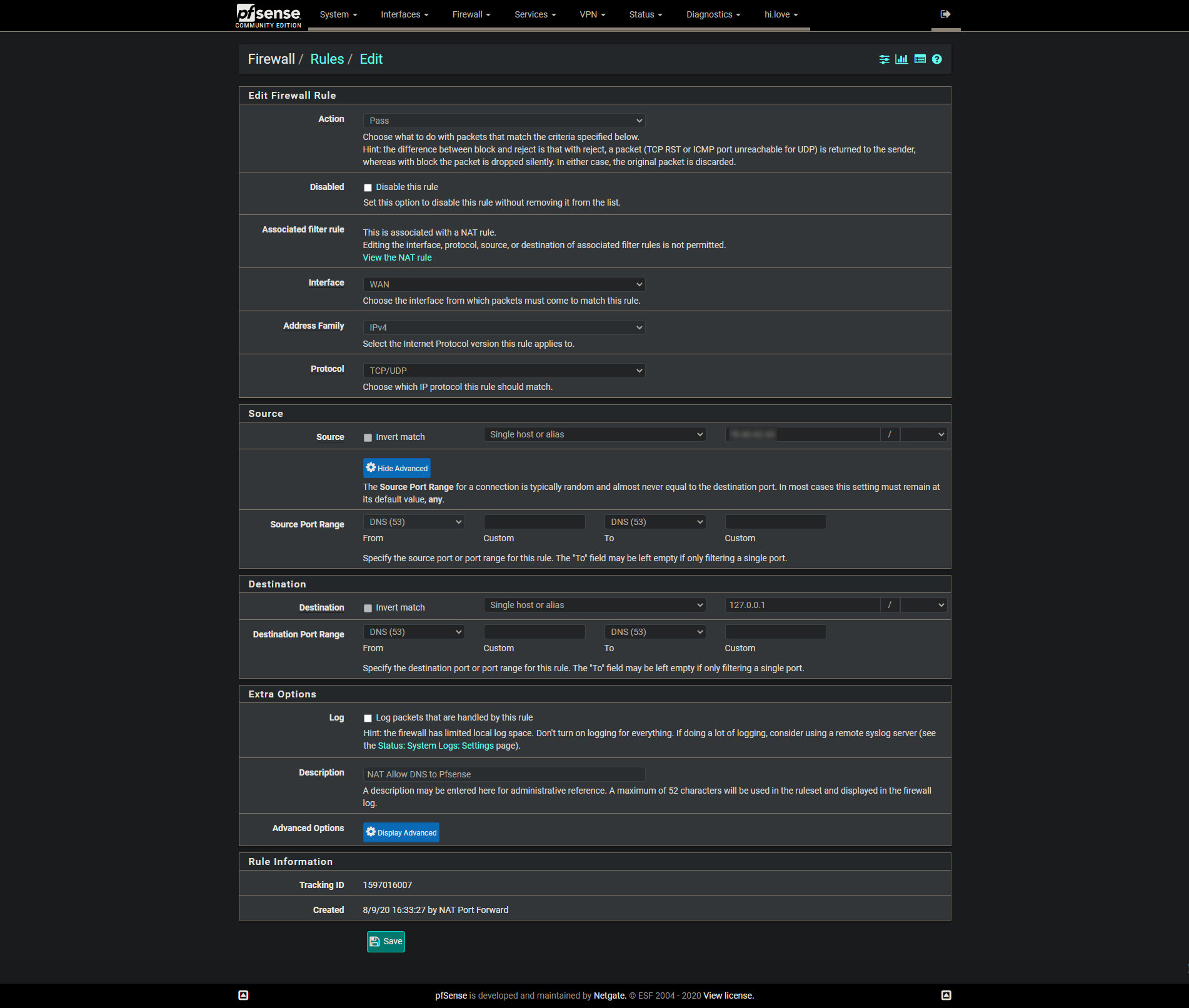
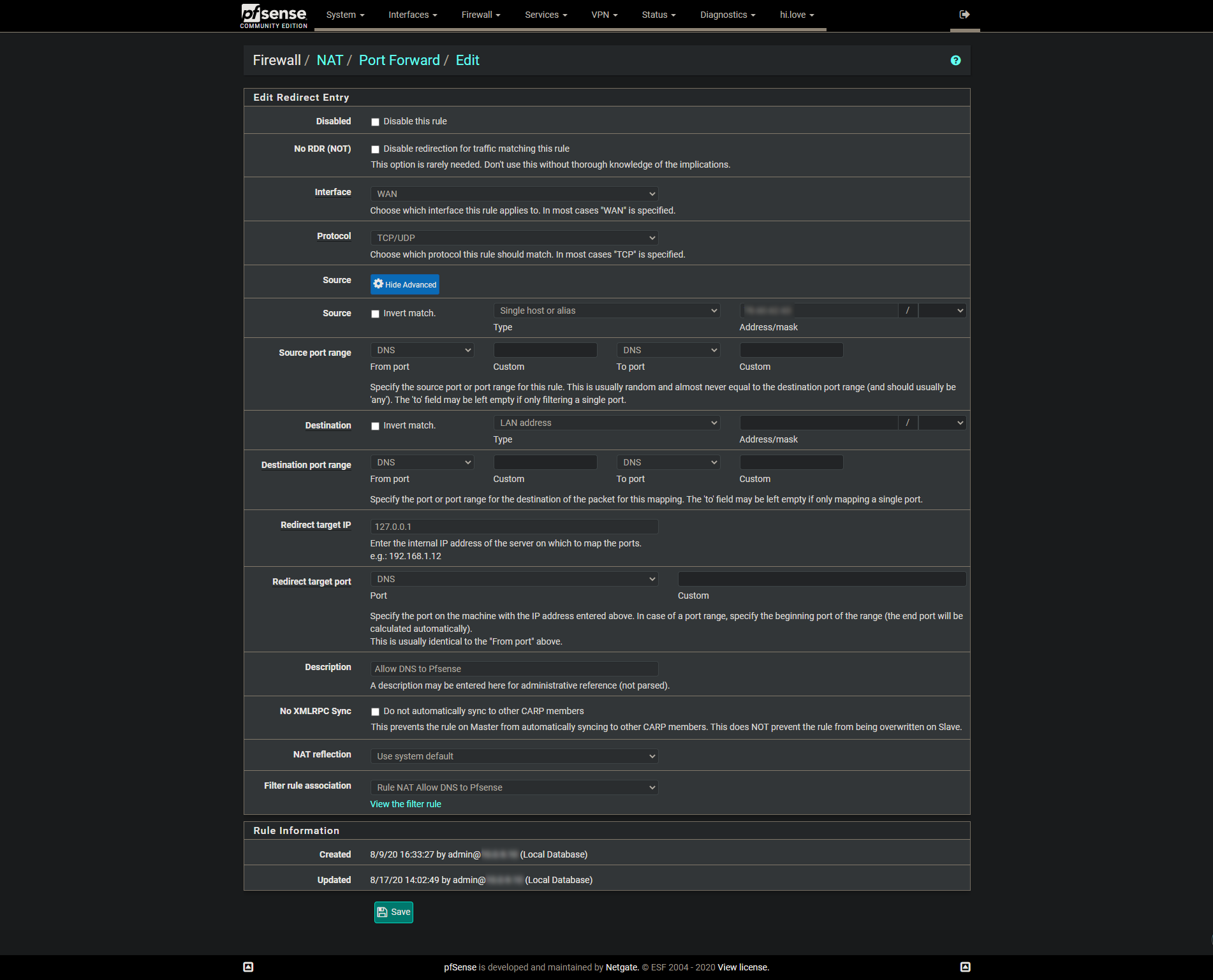
-
DNS requests may come from any port. So you have to set the source port to any in the rule.
Since you've set the destination to 127.0.0.1 you need to forward DNS requests to localhost. Better to use "This firewall" here.BTW: 192.1.1.0/24 is a public network and you shouldn't use it.
-
This can't exist :
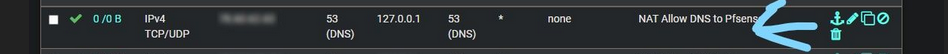
A "127.0.0.1" address as a destination address couldn't exist in an Ethernet packet., the ones that are send out using a NIC.
So, your WAN will never receive such a packet.
Which means that this part :
will stay a 0/0B forever => this rules has never been used/matched/applied.@viragomann said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
Better to use "This firewall" here.
Exact. Because it includes all the NIC IP addresses. The WAN IP will be included.
(that is, I'm pretty sure it does) -
@Gertjan said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
A "127.0.0.1" address as a destination address couldn't exist in an Ethernet packet., the ones that are send out using a NIC.
So, your WAN will never receive such a packet.No, that want be the problem here. The "NAT" in the description indicates that this rule was added by a NAT rule. I didn't see it earlier.
You get the "127.0.0.1" destination when you forward traffic to the localhost.I have similiar firewall rules in place as well and they works fine.
-
Why is your nat using a source port of 53.. That is almost never going to be the case, unless it was a zone xfer.. And even now that is not always done.
Thats fine if you want to port forward to loopback, but your source port is wrong. You can clearly see you have no hits on that rule.
First thing I would do is actually validate your remote site is actually sending dns to you, and that you actually get it via a simple sniff on your wan.
Also your port forward is wrong.. The destination would be your wan address, not your lan... How is some remote server ever going to hit your lan?
edit: here just set this up as example, so that one of my vps could resolve.. Lets pretend that is your remote server..
So I setup a port forward to loopback (unbound is set to listen on localhost as well).
Let the port forward create the firewall rule. (notice hits on it after did query)
Made sure I edited the unbound ACLs so that remote could actually query it.
And there you go my remote vps doing queries to unbound running on pfsense, as you can see it resolved my local pfsense IP via its name.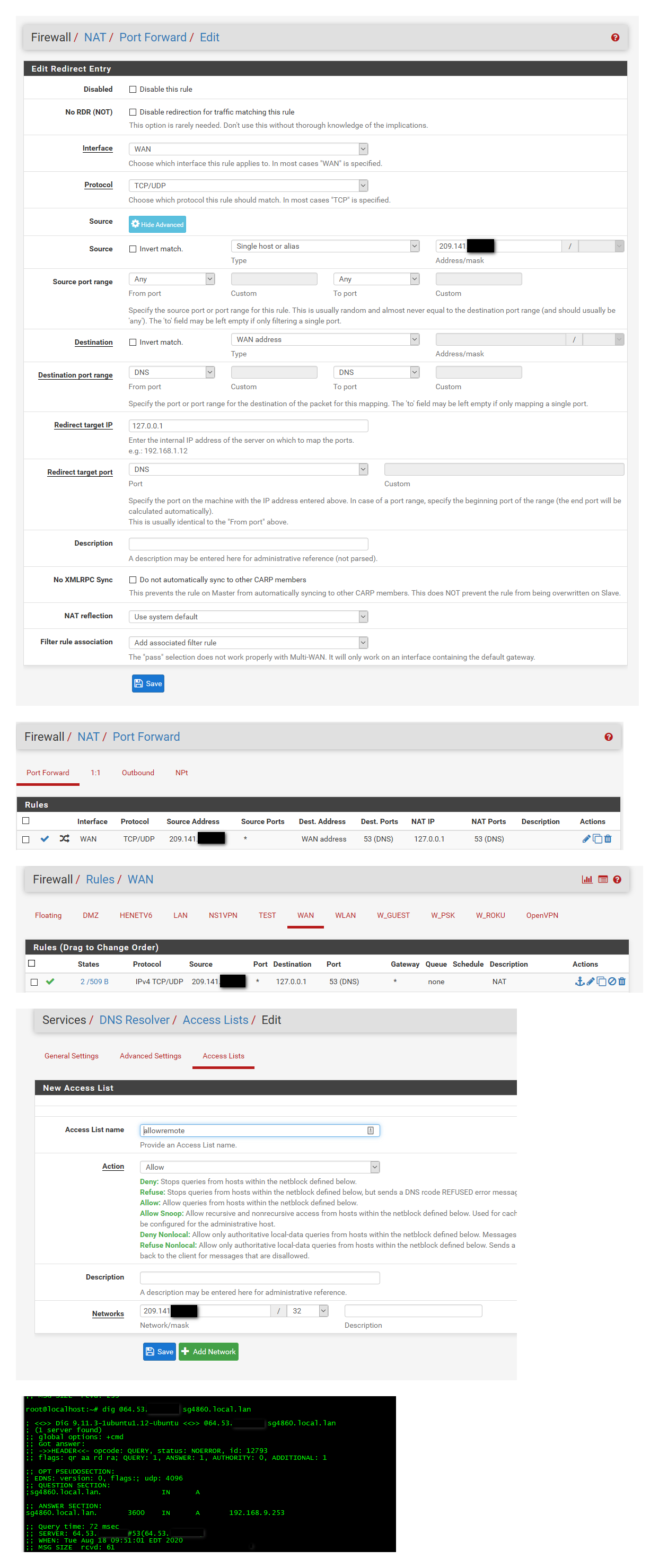
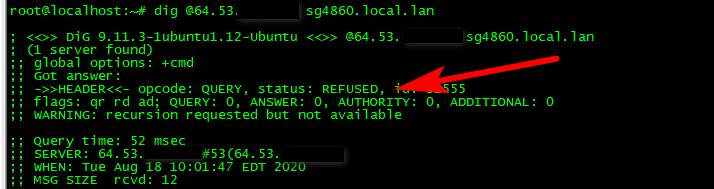
edit2: You need the ACL on unbound as well.. It will auto allow networks directly attached to query unbound.. But if your going to allow remote access you need to create a ACL that allows that.. Here I deleted the acl, and now you see get refused back
-
@viragomann said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
I didn't see it earlier.
-
It Worked, Thank you so much!! Now I know how to do this on my own.
-
@johnpoz it works great. I would to expand a bit more on the setup. I'm Adding on to it exactly how it is now.
The only change is that I have a different interface/ Vlan 21 for the dns Server. (Different Subnets) I don't know how to forward the DNS packets from the user = Pfsense itself to the DNS server on a different Vlan. Pfsense can see the other network, both have normal internet from each firewalls Wan address and have Lan Address (Pfsenses). I have been playing around with all the rules and can't seem to figure it out.
I tried the firewall rules + forwarding/ passing it the DNS to the server.
The DNS gets to the server sometimes not all however, the DNS won't go through this interface to get out to the internet either through both firewalls or coming hitting where it came from.I really need some help, I have been tried to figure this out for months.
Thanks for your Help!
-
Can you draw up how this is connected... You have some other DNS.. Why do you want to forward to this DNS? Is it authoritative for some domain? If so just setup a domain override.
Is this client trying to use something other than dns for pfsense, and you want to redirect say their query to 8.8.8.8 to this other NS elsewhere on your network?
I am not getting what your trying to do exactly.
-
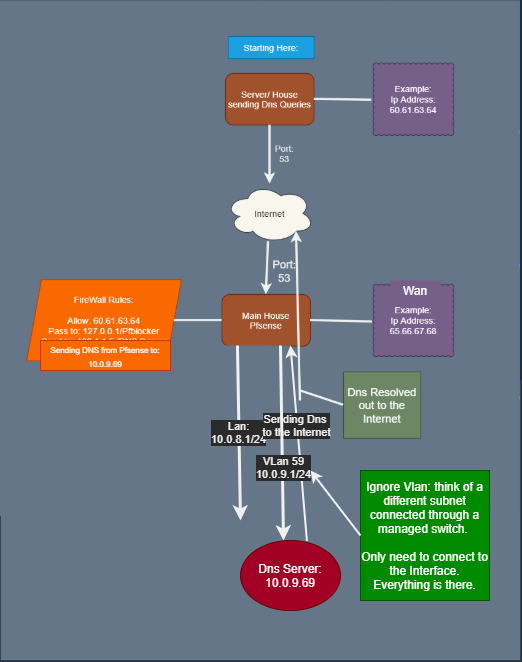
@johnpoz Here you go, hope this helps
Its Internet Dns to Pfsense to PiHole to Internet.
Thank You so MUCH!
-
Didn't we already go over this.. This server at 10.0.9.69 is different than you previous pihole?
How is that any different than your pihole 192.1.1.5?
Do you want to send your query to 10.x or 192., btw is that a typo - why and the hell would you pihole be on a non rfc1918 address? You sure don't own 192.1.1 (BBN Communications (BBNP))
You can not send traffic hitting pfsense wan on port 53 to both.. of these NS on your network.
Who do you want to send to this 10.x server? And who do you want to send to this 192 (pihole) box? What are they looking for, just internet stuff - local domains? what?
You have 1 dns server, pihole? Doesn't really matter what its running.
And you want other vlans on your network to use it? Or what? You can for sure port forward on your lan something that might be trying to query for example 8.8.8.8 and send it to pfsense, which forwards to this other dns..
Maybe I'm tired - but not understanding what exactly you want to happen... Who do you want to query this server? Why do you not just point them directly to what you want them to use for dns?
-
I have normal DNS queries coming from a house or small business that needs to be sent respond of a website page or loading YouTube videos. - (Normal Everyday DNS)
I want Pfsense to use Pfblocker then forward the next query to Pi Hole to do more filtering. Pi Hole is on a different network then on Normal Lan Side. Add another Interface on Pfsense, Example. I want to make a rule to allow and pass the DNS to the other network while giving a response back. Pihole can go through the Normal Lan side of the other network or just go right threw the internet from the WAN of the Pfsense.I don't know how to use a rule and pass the DNS to the other network while ONLY letting that device have access to port 53 on the other network. - (From the Pfsense's Rules)
Does this make any sense? or not explaining it enough.
Thank You for your Help
-
@Mr-Waste said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
Pi Hole is on a different network then on Normal Lan Side
Doesn't matter what network your pihole is on.. be it lan or your 100th vlan.. Pfsense can still talk it right? No port forwarded needed on your lan side networks.
So you want wan side client to use unbound on pfsense (with pfblocker).. Then for that to go to pihole..
But you want lan side clients to just use unbound of pfsense, but not get forwarded to pihole??
So you only have the 1 dns on your local lan side network.. You changed the pihole IP from the 192 address to the 10 address? Or you have 2 different nameservers? The pihole and this other one on the 10 address?
Or do you want wan to use unbound, forward to pihole? And then lan side clients to use unbound but get forwarded to some other name server? Which is not pihole? Or not use unbound at all and just get forwarded to this other NS?
-
@Mr-Waste said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
I want Pfsense to use Pfblocker then forward the next query to Pi Hole to do more filtering
Just keep in mind :when you use pfBlockerNg-devel, it will need unbound to work as a resolver (== not forwarder).
It's stated up front in the settings when you activate the DNSBL part.I can't say that you can't forward unbound, the 'resolver' but it will influence 'DNS' behaviour.
What about keeping things simpler ? -
@Gertjan said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
it will need unbound to work as a resolver (== not forwarder).
Ummm - no, why would you think that? You can use pfblocker while unbound forwards..
It states.. "To Utilize, Unbound DNS Resolver must be enabled." be it unbound is set to resolve or forward has nothing to with it..
I can see how the wording could be confusing.. But unbound is meant to be a resolver, that is its default state. But how unbound finds out something this is not local record, be it resolves or forwards has nothing to do with the workings of pfblocker.
Unbound is the resolver for pfsense, pfblocker doesn't work with dnsmasq (the forwarder) in pfsense. But you can for sure use unbound in forwarder mode, and still use pfblocker.
-
@johnpoz said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
why would you think that?
I was reading :
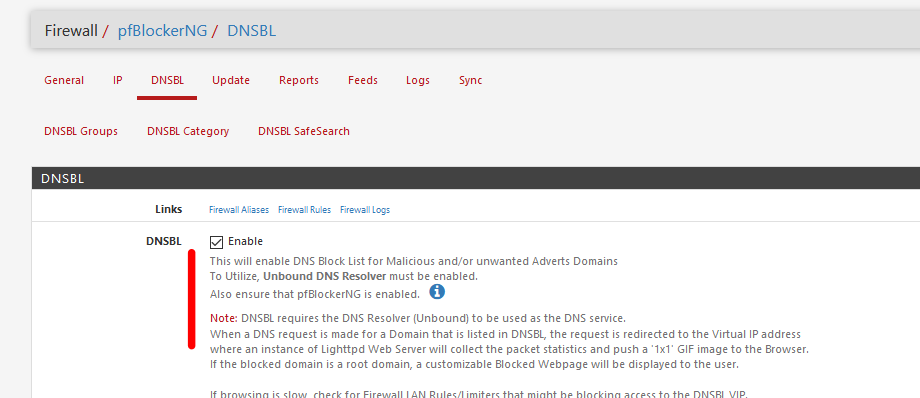
and agree (now) : the forwarding or resolver mode could be used.
I guess I mixed up resolver, Resolver and resolving. -
Yeah.. to be honest the wording should take out the resolver part of the unbound name.. Yes unbound is a "resolver" but you can set it to forward. While the forwarder (dnsmasq) can not resolve - only forward.
-
@johnpoz said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
do you want wan to use unbound, forward to pihole? And then lan side clients to use unbound but get forwarded to some other name server?
"So you only have the 1 dns on your local lan side network.. You changed the pihole IP from the 192 address to the 10 address?"
To be clear the 10 addresses are ONLY local on that subnet range. I decide to use the 10 network then 192 or others. Easier to remember. - Local ONLY
"Or you have 2 different nameservers? The pihole and this other one on the 10 address?"
Both network will only be using the 1 Pi Hole for Dns.
I need to know how to get a response back from the Pfsense being on a different network.Example network for Pi Hole ONLY:
Pfsense Extra Interface Lan2: IP:10.0.9.2 (Getting a IP address from the other Router on this network)
Pi Hole: 10.0.9.69Remember we have this too, but don't confuse your self here.
Pfsense Lan Interface: 10.0.8.1/24Pfsense is being the Unbound Resolver for the 10.0.8.1/24 (Lan) network. (Samething-Pfblocker for block lists) Then, Passing the Traffic to Lan2 network. Pi Hole gets the request and sends it out threw either Network. I would think the network 10.0.9.1/24 (Lan2) because the 10.0.8.1/24 (Lan) it doesn't know there is a Gateway for the Internet traffic to get out. + thinking of normal device just requesting Normal DNS queries.
"Or do you want wan to use unbound, forward to pihole? And then lan side clients to use unbound but get forwarded to some other name server?"
Talking about Pfsense ONLY: 10.0.8.1/24 LAN
I will explain more, I want every device either threw the WAN of Pfsense itself or threw the Lan to send the requests to Pfsense Resolver then forward them to the other network Lan2 Pi Hole.Lan2 10.0.9.1/24:
This other network will use Pi Hole for their requests of DNS. -
@Mr-Waste said in How to get Pfsense to resolve a DNS Queries from a Home on the Wan interface to pfsense DNS Resolver:
I need to know how to get a response back from the Pfsense being on a different network
Huh?? Doesn't even make sense.. Pfsense is connected to both networks or all networks question right?? Do you have drawings of some other downstream routers in your network??
Lets say you have this...
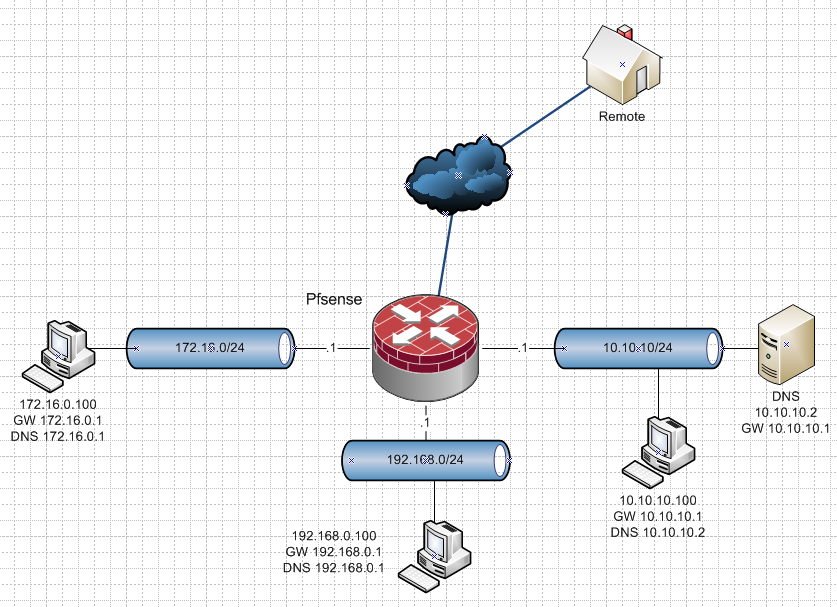
Forget the network IPs - there could be 3 there could be 3000 of them... Doesn't matter..
Your devices on each network.. Would point to pfsense IP on that network, in my drawing .1 on each network for DNS. Unless you want to point them direct to DNS like on the 10.10.10 I show..
The only thing that has to be allowed for is that 172.16.0 interface that network can talk 53 udp/tcp on that pfsense interface.. Whatever that vlan is called would be listed as vlanX address, on other network it would be vlanY address.
Now all you devices ask pfsense for DNS.. To the respective IPs of pfsense on that network - this is default what is handed out via dhcp..
Pfsense forwards this to your DNS..
To be honest all you have to do for your remote is allow that remote IP to your wan IP on 53 udp/tcp as well.. Unbound listening on your wan address.. Will also forward this traffic to your dns..
The only time you ever have to do any sort of port forwarding is if say a client on vlan X 192.168.0 in my drawing is trying to talk to 8.8.8.8 for dns.. This is when you would do a redirect (port forward).. Anything going to anything other than pfsense IP for dns, port forward it to loopback so unbound will see it and pretend its googledns..
I have no idea what you got into your head... But unless your wanting to intercept dns not set to talk to pfsense (default dhcp settings) then this works out of the box.. Nothing to do for any of it.. Other than set unbound to forward to your pihole/dns..
Do you have more routers in your network other than pfsense? Or is my drawing a representation of what you have? Forget what IP ranges I have on networks, or how many they are even... You could have 2, or 2000 - doesn't matter all works the same!!