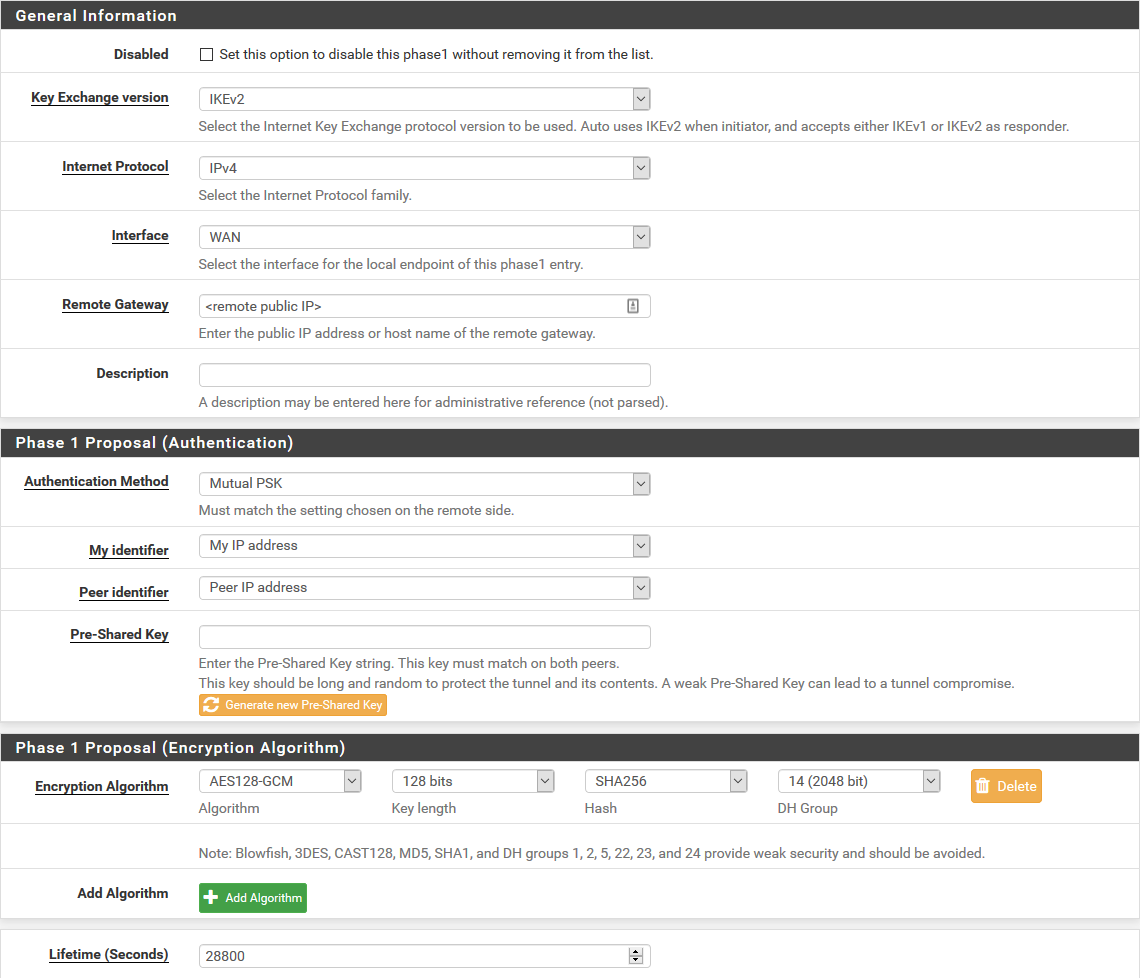
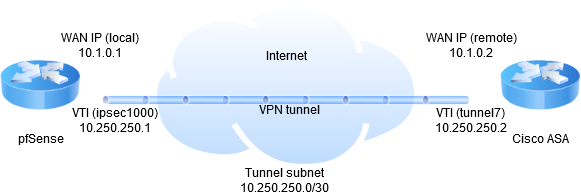
One-way traffic over VTI IPsec tunnel between pfSense and Cisco ASA
-
did you check this: https://forum.netgate.com/topic/60633/pfsense-2-1-and-cisco-asa5520-one-way-traffic-solved?_=1598350584376
-
As this is a connection between two virtual tunnel interfaces, there is no NAT involved - while it is certainly possible for NAT rules to interfere with traffic outside the tunnel, the two VTI endpoints should be able to reach each other.
I have run the Cisco packet tracer on both this connection, and another VTI-based tunnel to AWS, and the results are identical - in both cases, it identifies the correct VTI to use based on source IP, does not apply NAT, checks that there are no rules or policies blocking the outgoing traffic, and concludes that the packet is allowed and should be sent over the VPN.
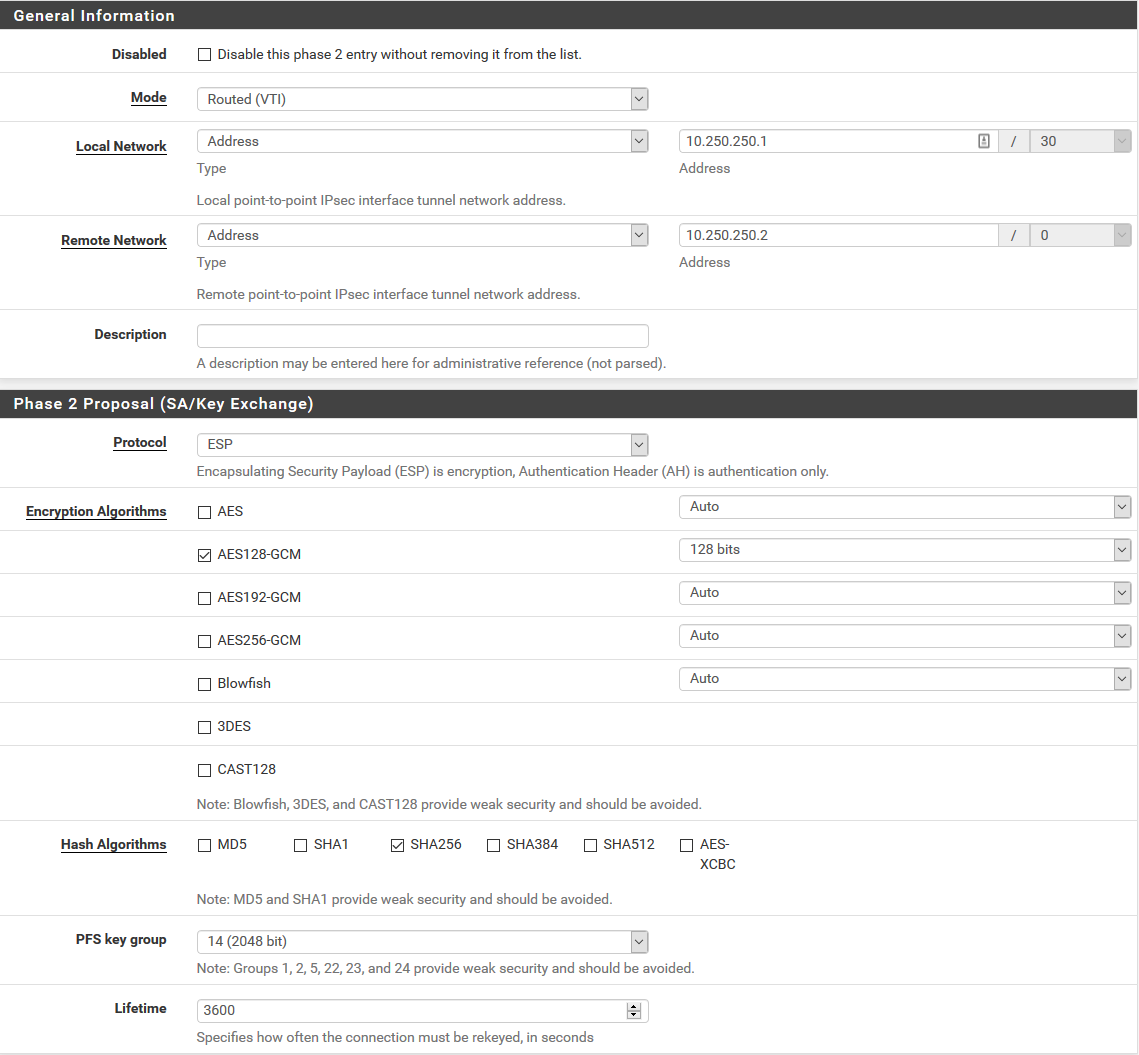
The config in both cases is identical except for addresses, names and PSKs, but the connection to AWS works (can ping the remote VTI address), and the one to pfSense does not.
-
Hmm.... did you reboot the pfsense ? Sometimes it helps ....
-
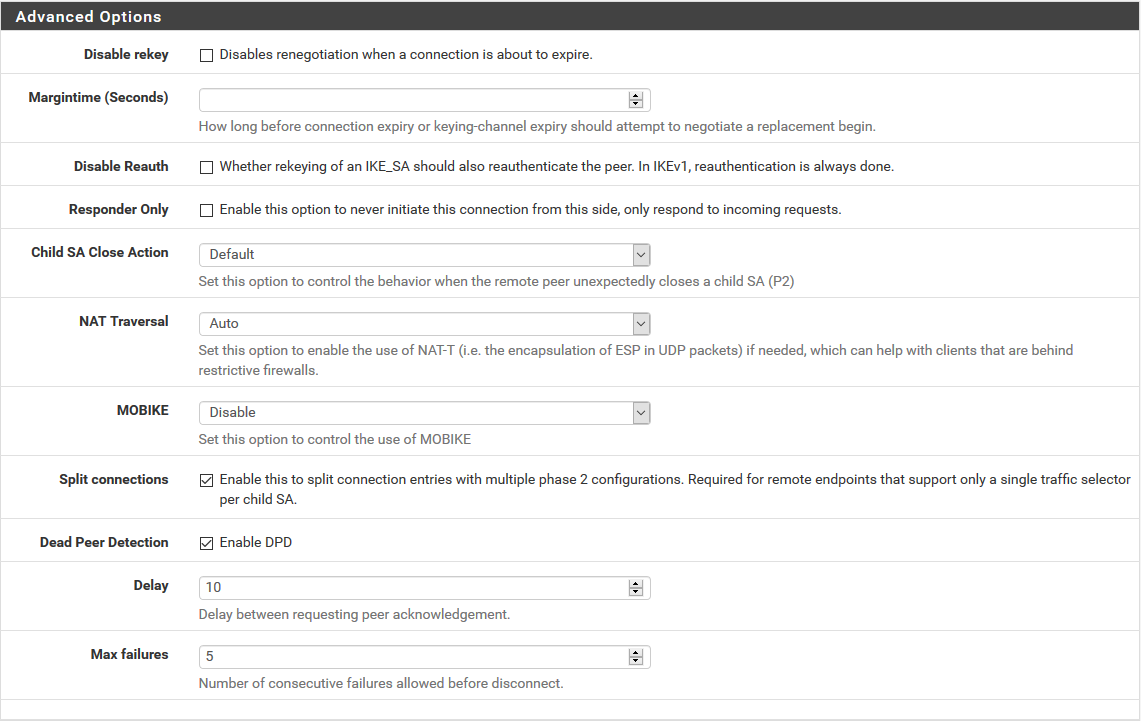
Which version of Pfsense do you use, pls update to 2.4.5 p1. Mobike is gone on the latest GUI.
-
I have rebooted pfSense many times over the course of troubleshooting, I don't think turning it off and on again is going to be the solution in this case.
And I am already running the latest stable release:
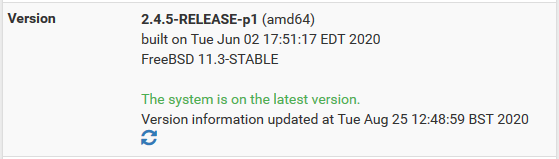
-
ok, im out of ideas now ...
-
Have you done packet captures on the outside interface to be sure the ESP being sent by the ASA side is actually being received on the pfSense side?
-
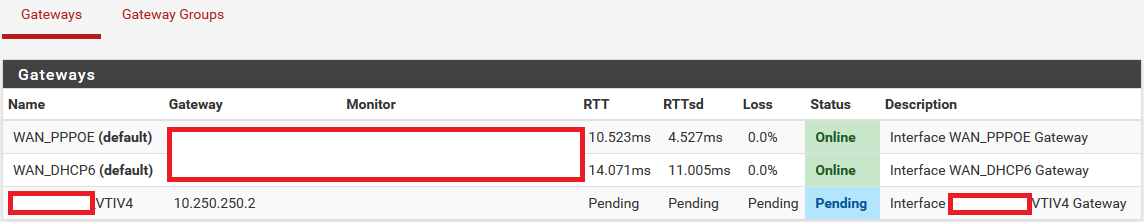
Hmm, i had this problem before with pfsense ipsec vti tunnels. You may try to disable and enable the vti gateway, to bring it up from "pending".
-
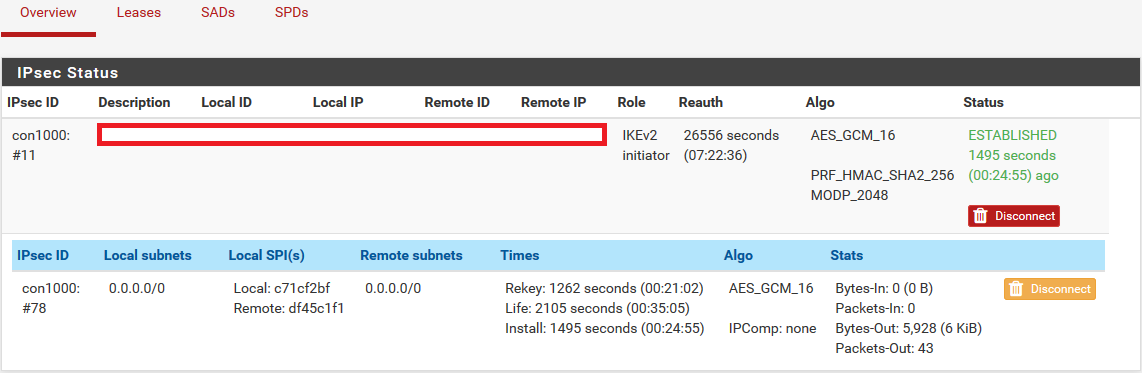
@Derelict - I just logged into the pfSense and set up a packet capture on the WAN interface, as suggested, and saw that ESP packets were being received when I sent out test pings.
And, as it turns out, so were the ICMP replies on the tunnel interface. I changed nothing locally, but other configuration changes were being made on the ASA, so presumably, there was a conflict in some other part of the configuration that I had not noticed.
Thanks everyone for your suggestions.
-
Maybe it helps...
You can find a running Cisco pfSense VPN configuration here:Unfortunately in German but the screenshot and config is pretty self explaining.