how do you setup users with restricted access
-
hi i trying to figure out how to add a user with restricted access to the network
what i have already is my admin account with a openvpn server so i can access my network from remote location..
now id like to setup for my son when hes not home but to have limited access to some VMs i setup on Unraid..
i created a user and a Group but i tried looking under Fire wall rules like Group or so so when he logs in he would only get access to a certain set of IPS like say under Alias's and setup Alisas of 10 ip Address's and he would only be able to access those.. so rest of the network isnt compromised if he had someone else log in using openvpn clientis this possible if there is a link or a video i could watch be great too
-
I hope you understand that you should do as little as possible on a firewall. Everything else you do beyond that brings potential vulnerabilities.
-
ah ok so whats the best route then.. to let him log into network to access VM's to work on... i tried Teamviewer app but it didnt always work
so i figured with pfsnese make a user then restrict access to a couple IP address's and connect with the OpenVPN...
but isnt that what the users section is for to add users to be able to access the network? for business? as i wanted basiclly he get a login and he only gets access to 5 ip address's on the network rest is blocked..
its just idea to give access to 5 vms so i dont know how to do that or even if possible with pfsenseor if thats like a windows server account access thing.. jsut ideas i looking into
-
i did read under the user for privleges but they confused me
what i wanted was
user1 ---> access the network of 192.168.0.x (but only have access to 192.168.0.10-192.168.0.15) as the example the rest be blockedi was thinking like a different network 192.168.50.x but i dont have vlans and i dont think i can with my network switch or if i can as my unraid is 192.168.0.x and id have to set the ip address to like 192.168.50.x and not sure if that would work
-
Like this :
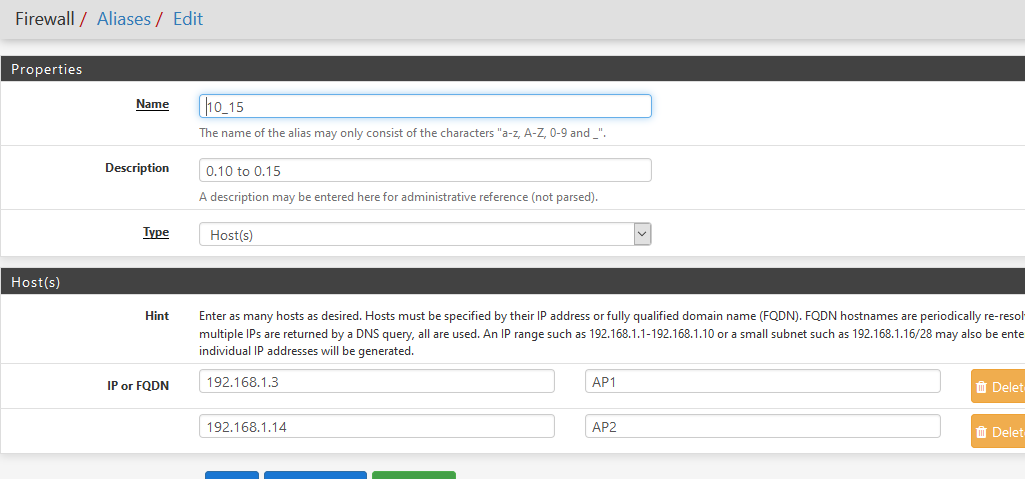
I have a default LAN network 192.168.1.0/24.
I have 2 access points using 192.168.1.3 and 192.168.1.14.I created an alias like :
These are my firewall rules :
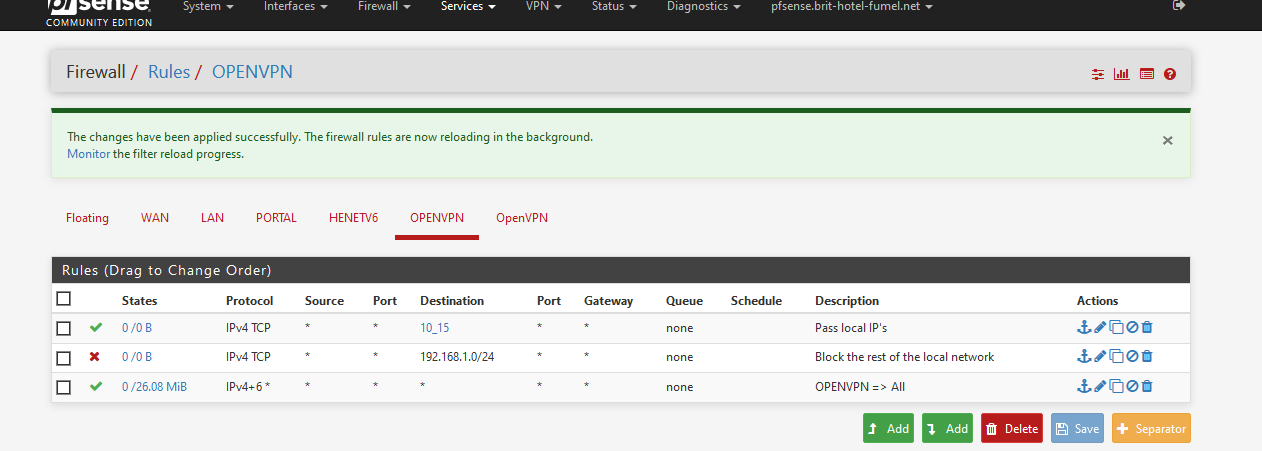
Note : this is just an example - I do have an issue because my pfSense OpenVPN remote access works with IPv4 and IPv6, so I could access my devices using IPv6.
I tested : in the 192.168.1.0/24 network I could only access my 2 AP's on .3 and .14 - and no other devices in that network.
I could use the other networks, like the entire Internet. -
@Gertjan
you say you have an issue with the ipv6 is that good or bad?
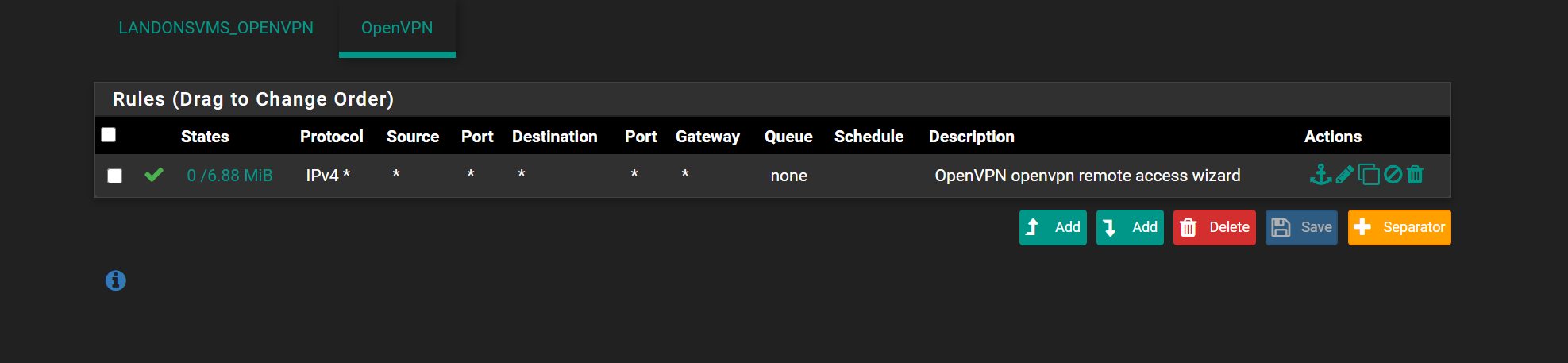
so your openvpn firewall rules
the first like Pass Local IPs what does mean it allows the 2 IPs right?
the 2nd line blocks the rest of the IP address's except the the 2 in 10_15
and then what doe it do for the 3rd line OpenVPN Alli not pro at this.. i just usually set it up and forget it so i dont tweak it every day lol
but ill give that a try -
@comet424 said in how do you setup users with restricted access:
you say you have an issue with the ipv6 is that good or bad?
My rules - alias based pass rule and block rule wirk with IPv4.
I could address these device and other devices using their IPv6, and them my two demo rules wouldn't have any effect.I shwoed you
@comet424 said in how do you setup users with restricted access:
the first like Pass Local IPs what does mean it allows the 2 IPs right?
Yep, the alias "10_15" is shown.
@comet424 said in how do you setup users with restricted access:
the 2nd line blocks the rest of the IP address's except the the 2 in 10_1
The second rules blocks the entire network 192.168.1.0/24 with no exception.
This include my AP1 192.168.1.3 and AP2 192.168.1.14
If I was talking to 192.168.1.3, the second rule would never be reached, as the first rules applies.@comet424 said in how do you setup users with restricted access:
and then what doe it do for the 3rd line OpenVPN All
If the traffic was for another network, like a some local 192.168.2.0/24 IP, the traffic would pass.
If I wanted to connect to www.netgate.com, the traffic would pass.
The third rule, if reached, says : pass all. -
ok i think i understand
i just set it up like yours basiclly and i added to my lan rules as i had no internet to setup ubuntubut ok
so If you didn have 10_1 then the 2nd rule blocks all access including 2 ipsso first one allows access to the 2 ips
the 2nd line blocks everything including the 2 ips but because You allowed 2 ip address in the first line it allows access to the 2 ips but blocks the restso the 3rd rule allows access to any subnets like 192.168.10.x 192.168.20.x www.netgate.com etc
if so how would you would set it not to access 10.x 20.x if i had that setup
would that be in the block and state block 192.168.20.0/24 like the 192.168.1.0/24 in your setupi think i got it confugred and ill have to go try it from a home depot as i dont have internet on my phone other then my home network or if i hit a home depot lol..
so will see if she works well...
i appreciate the help so far i very appreciated -
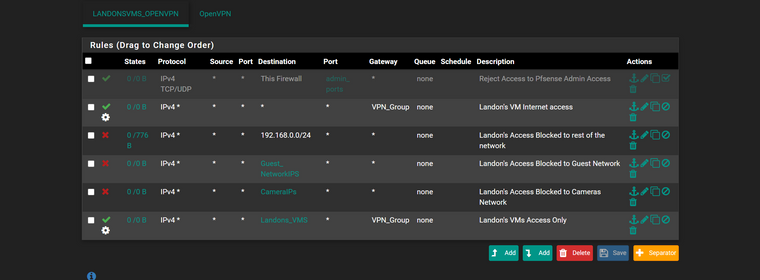
here is the rules i set
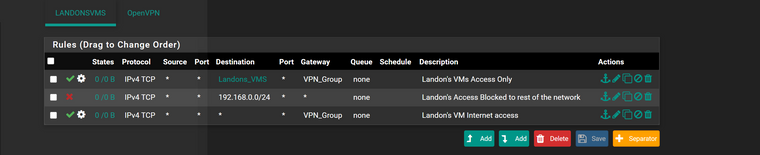
update..
here is i added blocks for the 10.x 20.x as i havent set them up yet dont have guests or cameras yet.. just future for over winter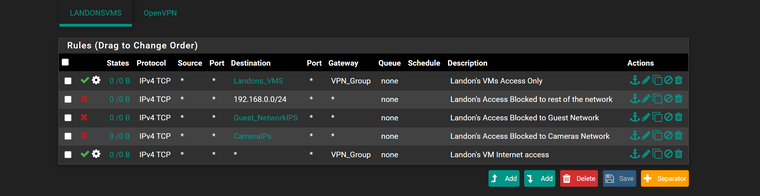
-
@comet424 The firewall rules in pfsense work from the top to the bottom on an interface, the first rule to match wins, no other rules are evaluated.
To setup your block rule for 10.x.20.x, you would simply create a new rule with that as the destination, and either an alias with your source IP addresses, or a specific IP address on that same subnet, or some other network on your pfsense box.
The rule @Gertjan used above blocks all other devices except the 0.10 - 0.15 hosts. Then, after you create this rule, drag it to an appropriate spot in your firewall list and do some testing.
Jeff
-
I initially thought I understoof your question :
You want your son, when he is connecting from 'some where', using the pfSense OpenVPN, having access to some devices on the LAN - and not to others.
Right?H'll be using the pfSense OpenVPN server, so the rules I showed should be placed on the OpenVPN interface firewall rule tab.
Because OpenVPN server traffic comes in by this interface.
Not the LAN interface : he isn't connected to the LAN interface.You put all the IP addresses he is allowed to connect to into an alias
Use this alias in a Pass rule.
Then create a second block rule, that forbids all access to the network (the IP addresses uses in the alias are part of this network).
Put in place a third - pass all rule if you allow that he can visit the Inter through the OpenVPN remote access. -
@akuma1x
ok is this correct then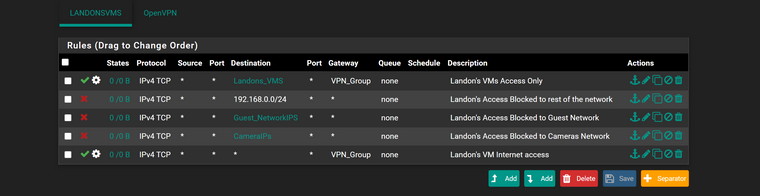
this is my LAN rules i think i have it set properly then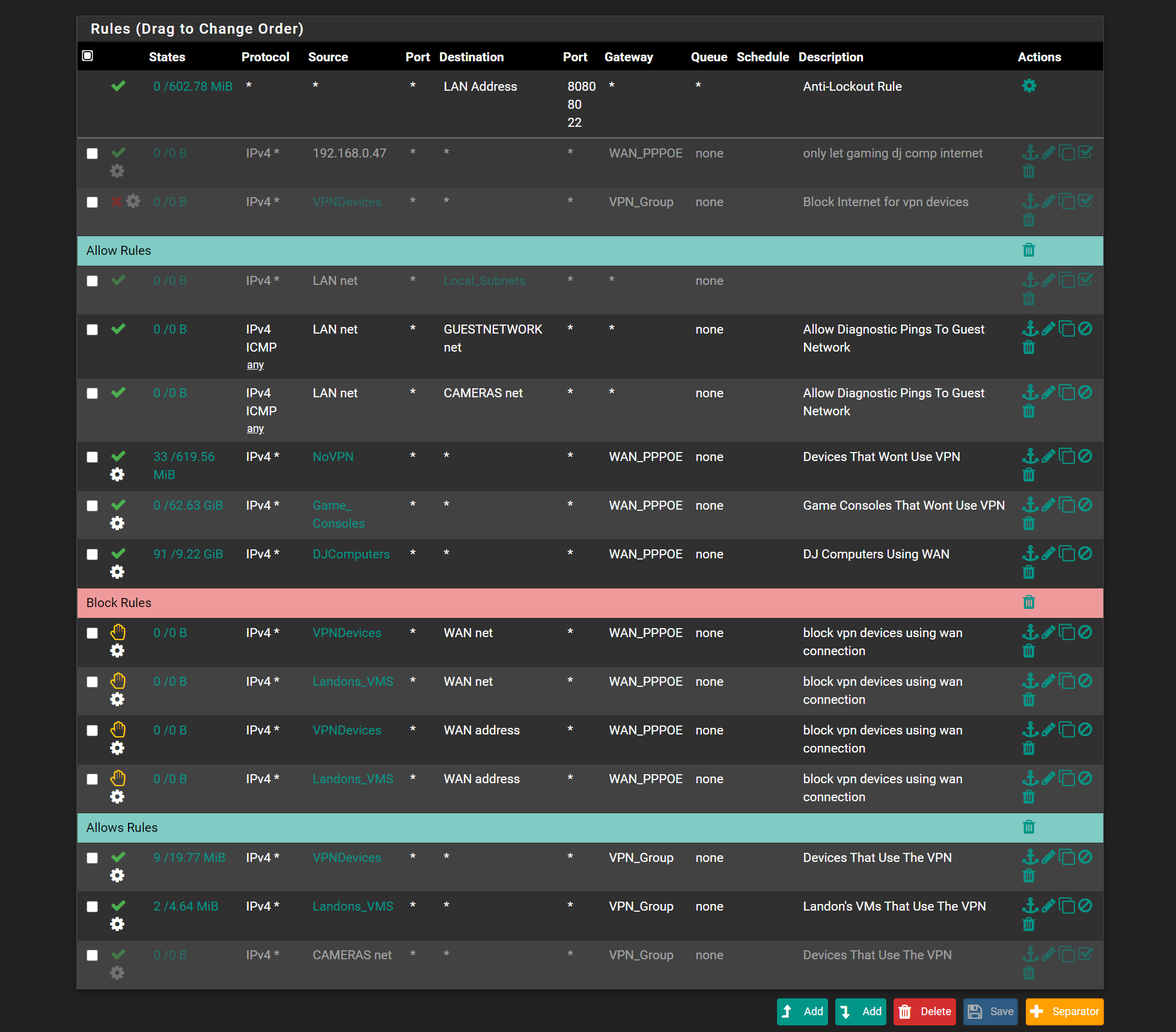
-
@Gertjan ok ill have to re read
what i did was setup 2 OPENVPNs
i already have 1 for myself to give full access
and the 2nd open i made for him and thats LandonsVMS thats linked to the 2nd openvpn thas what i thought you had setup in your example.. so i made 2 openvpn serversas there was no option in pfsense to allow a user to use the OpenVPN and under restrictions of user to access certain IPS
-
ok i renamed my interface so doesnt confuse
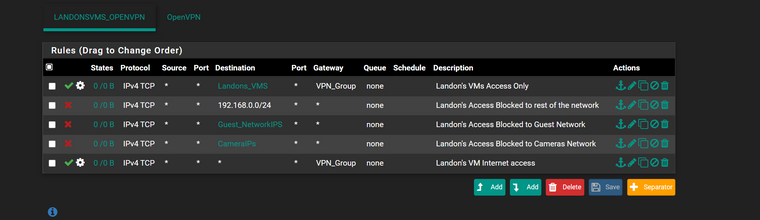
what i really wanted was
1 OpenVPN server running
user (me) has full admin access when loggin in
user (landon) has only access to the VMS (for now)but under users you can create Groups but i tried asking and i tried looking through the settings
to say User Group (LandonsVMS) has access to this range
but when you look under the access they can have its just the pfense pages access control.. not like restricted accessso now i made 2 Open VPNS 1 for my to log in full access and other for his access
if i knew how to make 1 server and then 2 user accounts 1 that has full access and 2nd has just access to the VM Ipsand sorry my dislexia confuses people too i dont explain things right.. yet sounds right to me
-
@comet424 said in how do you setup users with restricted access:
to say User Group (LandonsVMS) has access to this range
but when you look under the access they can have its just the pfense pages access control.. not like restricted accessThe pfSense user access :
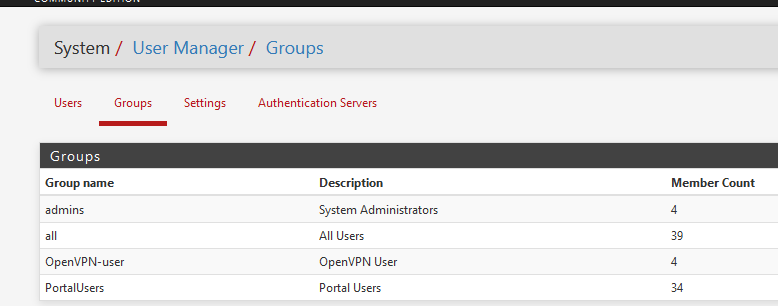
determines what users - can access the web GUI of pfSense, and what parts.
It doesn't handle network access.Your choice to have two OpenVPN servers with dedicated firewall rules seems a good solution to me.
-
@Gertjan ah ok to groups is just editing the pfsense.. figured you only want an admin to edit it
so that also means users can log in to either openvpn then with there login pass
i come across another issue with the openvpn to make that 2nd openvpn i did the wizard where you create a new cert new ca i did the 192.168.0.0/24 etc i chose the assignment and gave that openvpnvm link... but when i goto to Export the clients are not shown.. its there for the main one i have for full access
so i get "If a client is missing from the list it is likely due to a CA mismatch between the OpenVPN server instance and the client certificate, the client certificate does not exist on this firewall, or a user certificate is not associated with a user when local database authentication is enabled."
now today first time running 2 openvpn servers and its been a year since i even touched my openvpn server since i set it and forget it.. and dont work with this everyday..
i did the wizard but what could gone wrong.. where would i look what screen shots would you need
-
gonna try... delete cas certs openvpn server firewall settings it creates and do a reboot so its clean to see if it fixe's it
when in doubt do a reboot lol
-
well that didnt work
deleted all saved rebooted.
then ran wizard still says that issue on exportupdate..
figured it out had to choose user and the bottom the certs linked and had to link exisit cert... now i can test it at home depot lolhopefully it all works (:
-
@
@Gertjan
ok so i cant seem to connect,,, i was able to connect to my orginal openvpnthe 2nd one with my other account its stuck on connecting.. i was able to download the opvn file but when connecting its jus stuck connecting... is there something to check.. i checked that it was basiclly exactly same as the admin one i have setup and i did run the wizard.. but its stuck at connecting.... even if i make up a user using the client software it stays connecting.. if i make up a user on my orginal open vpn it tells me invalid
so its not getting to authenticating or what not
-
@Gertjan
so i got it to log in using the landon account i had to delete the user and re add it then create cert button instead of add cert and then add exisiting cert..but there is issue.. i was getting full access to the network.. so when i got home.. LandonsVM Open VPN didnt get really access.. but it went to the OPENVPN Firewall rules.. it didnt go to the correct firewall rule.. where do i look
also everytime i delete the openvpn server, certs,ca, and do the wizard again.. it always saves the rule under OPENVPN not the LandonsVMOpenVPN..
but interface is set for it so its going to the wrong firewall rule
what do i look for that its going to the wrong rules?interfaces
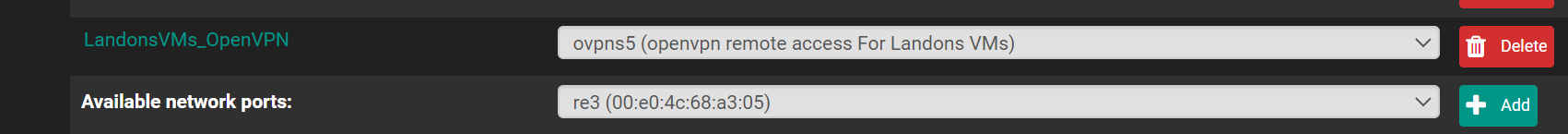
rules