PfSense SG-5100 setup with Netgear XS708T, Ruckus AP R510U and GL.iNet GL-X750
-
Hi all
New to networking and was hoping for some guidance with improving an existing network:
- Firewall: PfSense SG-5100
- WAN1 PPOE: HFC Modem (with VLAN tag)
- WAN2 DHCP: GL.iNet GL-X750 (4G failover router with SIM)
- LAN Managed Switch: Netgear XS708T
- AP: 2 x Ruckus AP R510 Unleashed
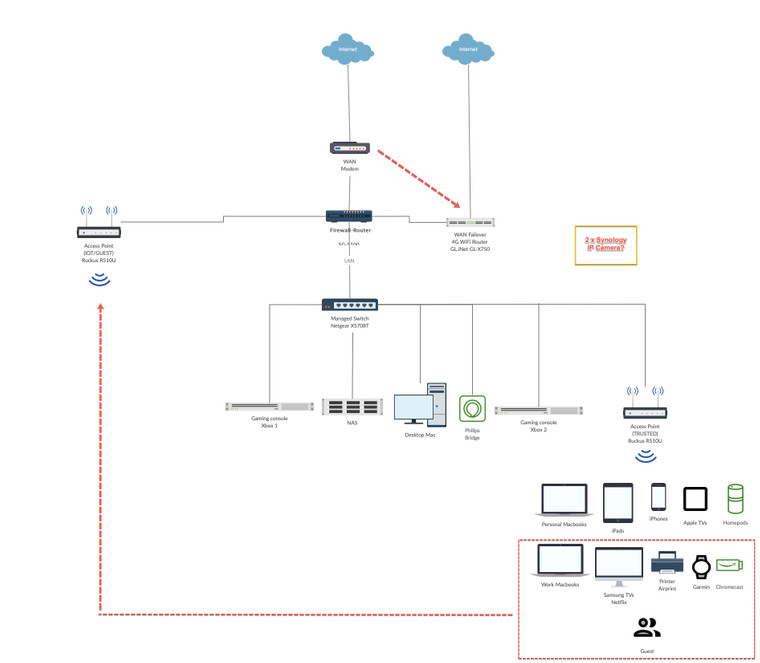
My aim is to keep things simple based on what I been reading on this forum:
- PfSense taking care of routing and the firewall
- Using the managed switch for QoS control
- keeping more sensitive parts of the network physically sectioned off from the less trustworthy parts of the network
- Treating some wireless clients exactly the same as wired clients (thus I have connected the trusted AP to the managed switch that's connected to PfSense)
- Applying different firewall rules to some wireless clients (hence I connected a new IoT/guest AP to the pfSense NIC to allow these to access the internet but not all wired clients)
- Setting clients on the same VLAN as the servers they depend upon
Much appreciated if you guys could help / provide feedback on below items I am not sure about:
- Failover: The GL-X750 in router mode is working and I am able to connect to the WiFi. However, how do I setup a failover in pfSense so that if WAN1 PPOE is down pfSense automatically switches to WAN2 DHCP for internet access?
- Should the IPv4 be static instead of DHCP?
- The gateway status in widget is showing as 'Unknown'
- IoT/Guest AP: This is physically connected to pfSense at the moment however unclear how to properly connect this to internet:
- IPv4 config type: Should this be a static address with an IP different (e.g. XXX.XXX.0.4) to what's assigned to the LAN interface (XXX.XXX.0.1) which has the trusted AP (XXX.XXX.0.3) or same (e.g. XXX.XXX.0.1)?
- IPv6 config type: Should this be set to 'Track Interface' WAN1 PPOE?
- Those familiar with Ruckus unleashed APs, currently the IoT/Guest AP is broadcasting an unique IP address (unleashed.ruckuswireless.com) and the wizard is treating this as a new master AP needing setup. However, I already have the master / trusted AP up and running (XXX.XXX.0.3) which isn't detecting this pfSense NIC connected AP as an additional unit in the Ruckus web interface yet
- Can the IoT/Guest (located at the middle of the house) still act as a mesh network for the wireless clients connected to trusted AP?
- VLANs: Once the IoT/Guest AP has been setup I would like to connect some wireless clients to it as per the diagram. However, I am not sure how some of the trusted clients (such as mobile phone / PC) would then talk to Garmin device / AirPrint / Chromecast etc. Currently everything is on the trusted AP with no issues. Would I need VLANs set up for the communications to continue working? What would you recommend in terms of a simple setup?
- Interfaces: Wondering whether to keep some of the items connected to the switch (1 free port) or pfSense (2 free ports):
- Philips Hue Bridge: It's on the switch at the moment but should it be on the pfSense NIC instead? If so, how would the wireless iOS devices connected to trusted AP be able to talk to it?
- XBOX: Additionally, not clear if the two XBOXs should be on SG-5100 given nothing else needs to communicate to it and it would potentially reduce lag while gaming if connected directly to pfSense?
- IP Camera: Considering to purchase 2 x Synology compatible IP cameras soon. Should these be on the managed switch in order to communicate with the NAS?
- QoS / traffic shaping / bandwidth priority: How do I provide highest bandwidth priority to XBOX over other clients connected to the IoT/Guest AP such as Samsung TVs or other trusted AP clients specially when they are streaming videos / Netflix (in order to reduce lag while gaming)?
Thanks so much in advance!
-
WAN failover is described here:
https://docs.netgate.com/pfsense/en/latest/book/multiwan/index.html
In addition to using policy routing you can now also set the system default gateway to a failover group which will also route traffic from the firewall itself.
You can, and probably should, have both WANs set as DHCP. It may be showing as unknown if the service is not started or there is a subnet conflict perhaps. More likely the latter.You IoT/Guest AP should be in a different subnet to the LAN. That interface should be separate. The pfSense interface IP would commonly be .1 and the AP IP should be either statically set outside the dhcp range on that interface or set via a static dhcp mapping so you always know where to access it.
IPv6 should probably be set to track PPPoE unless you have a static IPv6 address.
To be able to have guest and regular users connected to either AP you want to set them up with multiple SSIDs on different VLANs and separate the traffic that way. Both APs should connect back to pfSense on the same port carrying all VLANs.VLANs have nothing to do with connecting between subnets, each VLAN would be a separate subnet. Traffic from the IoT/Guest subnet will be able to reach resources on LAN as long as there are firewall rules allowing it. Conversely you should have firewall rules blocking access to the LAN for most guest clients.
Multicast/broadcast services, like Chromecast, are a different matter. They are not intended to be used across subnets and additional measures are required (igmpproxy/pimd).Anything that should be in the same subnet should be on the switch. Interfaces on the SG-5100 are not switch ports and though they can be bridged to act like switch ports moving traffic between them requires valuable CPU cycles they could be used elsewhere.
The lag introduced going through a switch is negligible.
IP cameras would normally be considered an IoT device. Commonly found with known firmware vulnerabilities and no updates from the manufacturer. That would denote they are put on a separate subnet with very limited access to anything else. However they also generally generate a lot of traffic which will all have to be routed by pfSense if they are separated from the NAS like that. The decision is yours!
You can apply a basic priority based shaper to prioritise traffic from the xbox IP. It will need a static dhcp mapping to do so. However I would not do that unless you are actually seeing latency issues. Adding traffic shaping often introduces more problems that is solves.
Steve