pfSense - DNS redirect to local DNS server
-
My goal is to redirect all outbound DNS requests to my internal DNS servers (PiHole) while allowing my DNS servers to query outside.
I found 2 links that helped, but 1 was incomplete and the other was long, old and had too many posts off point. I only intend on posting what I have working to help the next person.Links included to give credit to where credit is due, without these two I would not have figured it out.
https://docs.netgate.com/pfsense/en/latest/dns/redirecting-all-dns-requests-to-pfsense.html
https://forum.netgate.com/topic/139457/transparently-intercept-and-redirect-dns-traffic-to-an-internal-dnsThe Setup:
2 VLANs: 42 and 128
All DNS is on 42
The test host moves between 42 and 128 and uses a bogus DNS server
Alias PiHole contains all DNS servers
(I would recommend using an alias even with 1 DNS server, adding and removing DNS servers requires 1 update, not 6)The rules:
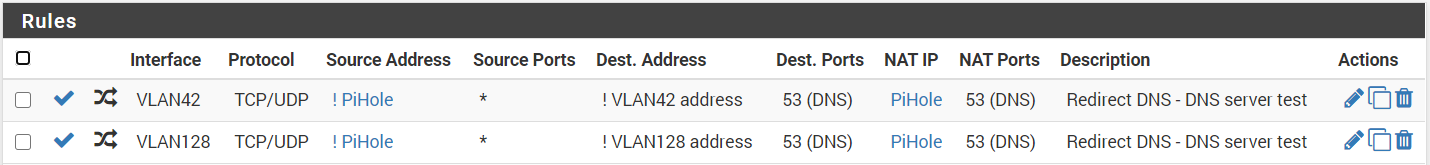
NAT / Port Forward - These send the requests to your DNS
-- Rule for VLAN42 --
Interface: VLAN42
Protocol: TCP/UDP
Source: Invert match Alias PiHole
Destination: Invert match VLAN42.address
Destination port: DNS
Redirect target IP: PiHole
Redirect target port: 53
NAT reflection: Disable-- Rule for VLAN128 --
Interface: VLAN128
Protocol: TCP/UDP
Source: Invert match Alias PiHole
Destination: Invert match VLAN128.address
Destination port: DNS
Redirect target IP: PiHole
Redirect target port: 53
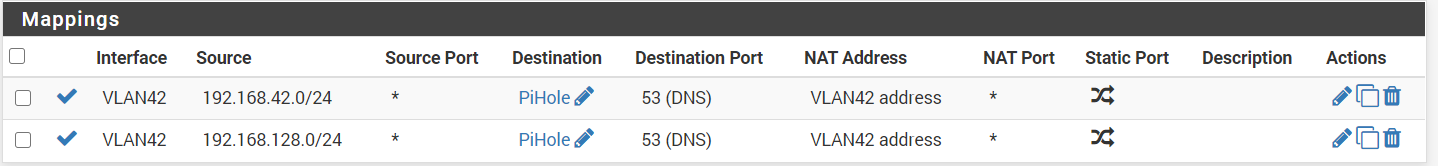
NAT reflection: DisableNAT / Outbound - These masquerade the IP address to make the client happy.
-- Rule for VLAN42 --
Interface: VLAN42
Protocol: any
Source: Network 192.168.42.0/24
Destination: Network Pihole port 53
Address: Interface Address-- Rule for VLAN128 --
Interface: VLAN42 (yes 42)
Protocol: any
Source: Network 192.168.128.0/24
Destination: Network Pihole port 53
Address: Interface AddressThe pictures:
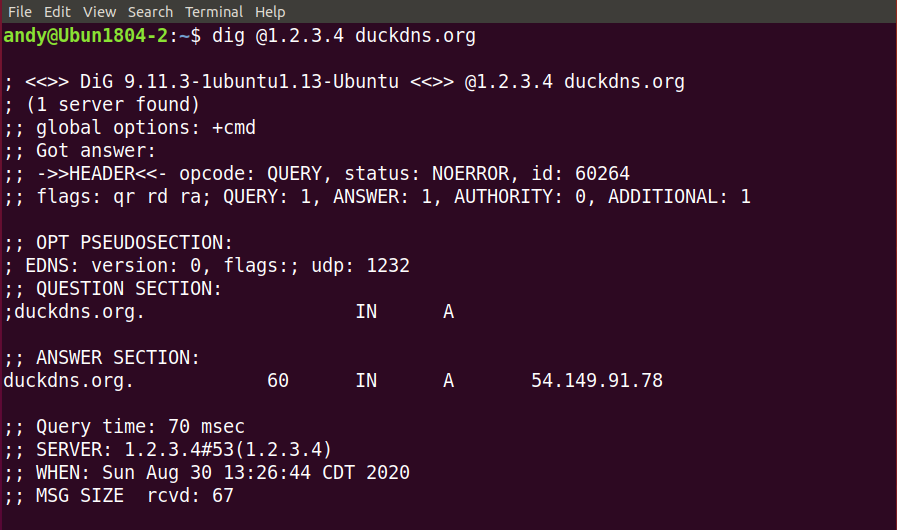
You can see that dig @ a server that is not a DNS server returns correct results.
I hope this is useful.
-
@AndyRH Your NATing to redirect all dns queries to Piehole isn't working because you get no error from dig saying "reply from unexpected source: <insert_your_piehole_server_ip_here>, expected 1.2.3.4#53" which you would get if PfSense would truly NAT properly. Something else is replying to dig, but its not piehole.
I redirect all DNS queries from my LAN3 and WIFI segments to Piehole like this:
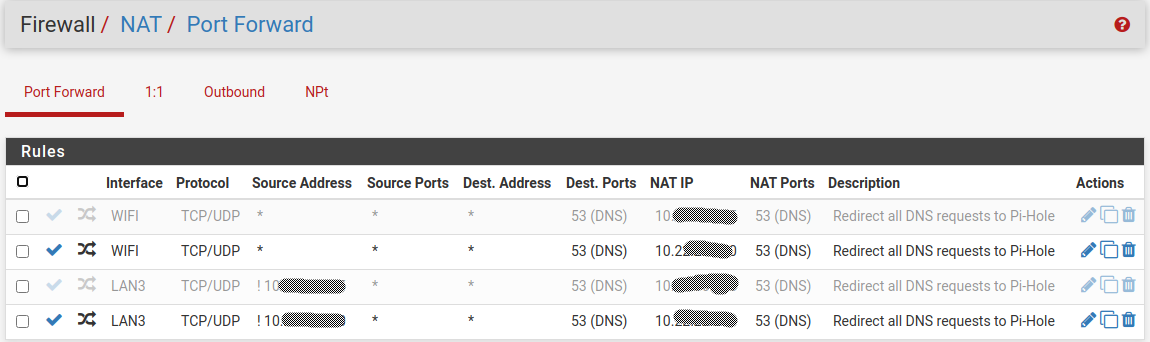
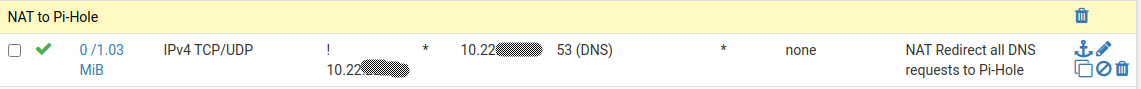
As you can see, all WIFI DNS requests from any source (segment 10.40.x.x/24) are NATed to my Piehole server on segment (10.22.x.x/24). Then you can see on the Piehole segment itself I redirect all DNS requests (segment 10.22.x.x/24) to the Piehole server EXCEPT for the Piehole server itself.
Then here are the rules for the WIFI segment that goes with the NATing of WIFI DNS's request:
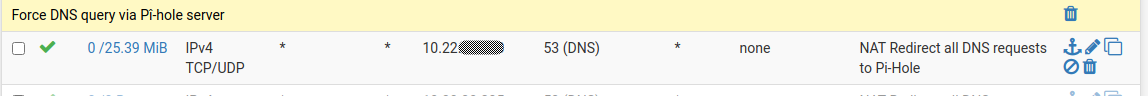
And the rule for LAN3 segment (where the source isn't piehole itself):
And this is the output from Dig with a proper DNS redirection :
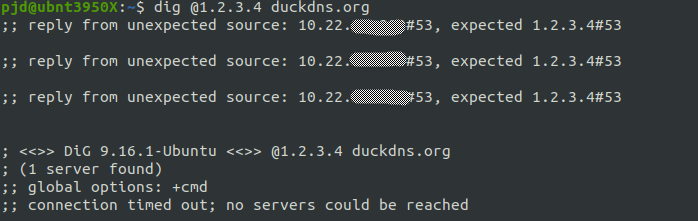
You can see the DNS request comes back from the Piehole server but Dig is waiting a reply from 1.2.3.4.
And in piehole, you can see the request being redirected, resolved and returned to dig:

-
You are correct if the goal is to prevent resolution if a wrong DNS server is used. In that case a simple block of the port will work just fine.
It is working as I intended. The goal is to get a proper response to the client. Without the "masquerade" of the wrong DNS server the client is not able to resolve the requested address.
I do not want to stop the clients from resolving addresses, I do want to stop clients from resolving addresses on servers that are not mine.
Roku's are notorious for using 8.8.8.8 if they fail to connect to the usage reporting servers. I have also found Amcrest cameras try hard coded DNS servers when they fail to connect home. -
@AndyRH Oh I understand what you wanted to do. You are anonymizing your piehole so your client's think their reply comes from the legitimate DNS they wanted to use. That's clever!
-
I know this post is pretty old, but I just want to thank you for providing an elegant solution of forwarding all DNS queries to the Pihole. I am running Pfsense 2.5.2 and this solution is working for me.
-
Excellent, tyvm! ;)
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
@AndyRH Thank you for this post ! I have a question, with this solution pi-hole see only one IP "VLAN42 address" and not client IP ? It's correct ?
-
@fjmp24 No, a client on VLAN100 will be seen with its correct address. Any redirected (rouge) queries come from pfSense (42.1). I know it works because VLAN100 does not have ad filtering because 192.168.100.0/24 is in a group on PiHole to not do ad filtering.
-
Even though I have experimented a lot with PiHole a few years ago, and add filtering from many top firewall brands, the best thing to remove ads is Ad Blocker Ultimate plugin for Chrome.
Nothing passes through and free YouTube is possible. So it is worth to get and pay a little to help development as I did because it is simply outstanding. -
@AndyRH VLAN100 ?
-
@fjmp24 An example, one of my VLANs is VLAN100. VLAN42 (the meaning of Life, the Universe and Everything) is my primary VLAN and where the PiHoles reside.
-
@P-J said in pfSense - DNS redirect to local DNS server:
is Ad Blocker Ultimate plugin for Chrome.
And those browser plugs are a bit hard to run on say your roku stick.. Or some app your playing on your phone.. I use a browser plug for sure in my browser but dns filtering can be very helpful on stuff your network is doing that is not browser based, or even on browsers that do not allow for addons, etc..
-
@AndyRH Sorry but it doesn't work with me :-(
When I use the command :
- dig @1.2.3.4 google.fr, adguard display firewall address
- dig @adguard google.fr, adguard display client address
What is wrong ?
-
@fjmp24 no idea what your trying to do.. Have you setup redirection? @1.2.3.4 is not going to answer anything unless your redirecting or your dns is being redirected
And @aguard sure an the hell would never work.. Its not an IP address or a fqdn that could be resolved by anything.
-
@johnpoz Sorry I wrote my message quickly
I want to redirect all DNS requests to my internal DNS server Adguard Home.
I configured Adguard Home as DNS server in my DHCP servers so by default my devices use Adguard Home as DNS server.
Now I want to redirect DNS request that do not have Adguard Home as destination to Adguard Home.
I followed the procedure of @AndyRH but I have a name revolving problem. Adguard Home does not display names all the time. When I executes theses commands from a client device I have:- dig @1.2.3.4 google.fr, adguard displays firewall address
- dig @<Adguard home ip> google.fr, adguard displays client address
I think the problem is with the mappings rules but I don't know how to fix it. Ideas ? Thanks
-
@fjmp24 said in pfSense - DNS redirect to local DNS server:
adguard displays firewall address
What does this mean? You are seeing this error?

Would be helpful if you showed how you setup redirection, and the actual output of your dig command.
-
@johnpoz No I have not an error.
Dig response:

Adguard home log:

IP is my pfsense address.
My configuration:



The alias MAIN_Host_Shepheherd represents Adgaurd Home host.
-
@fjmp24 what do you think it would show? your doing an outbound nat that nats it to your main address..
-
@johnpoz Client IP

-
@fjmp24 not sure what that has to do with you... Your doing you have a outbound nat on man, that says any traffic to that main host, on dns ports to nat it to your main address..
Here I setup a quick port forward to my pihole... You can see it lists my client as who asked for it.
