Pfsense with AP dhcp server settings
-
I have a pfsense router and a cambium AP. Everything works.
I want the AP to issue ip-address according to ssid. SSID1 100-120 and SSID2 150-200.
SSID1 should go through vpn and SSID2 should just go to internet connection.
pfsense should see every device with ip-address, so I can create rules.I tried 2 methods:
Method1:
I have subnet .128 (/25) on pfsense and on ap.
Pfsense gives ip addresses up to 100 and 150-200 is done by AP.
AP has 2 ssid, one uses the dhcp from the router. The other is issued by AP (at the end 150-200).
Problem is that ip-addresses issued by ap don't get noticed in pfsense. pfsense just sees the ip from ap is doing all the trafic.Method2:
I have subnet .0(/24) on pfsense and on ap I have 2x .128.
AP issues ip's.
Problem is that ip-addresses issued by ap don't get noticed in pfsense. pfsense just sees the ip from ap is doing all the trafic.What am I missing?
-
Normally, when you have multiple SSIDs, you use VLANs and different subnets. I just set up a guest WiFi the other day. My home network is on 172.16.0.0 /24 and guests on 172.16.3.0 /24. I then set up the rules so that the guest can only access the Internet. You need to do something similar, but forwarding out the VPN. While you could do something within the same subnet, it will get messy, as you're discovering.
-
@JKnott Ok, I will try that. But does pfsense see the ip addresses from different range?
So if pfsense is on 192.168.0.1 and ap(different device) is on 192.168.0.5.
Ssid1 on ap just uses the dhcp leases from pfsense, so pfsense detects those devices individually.
Ssid2 on ap uses different range, 192.168.1.xxxIf configured this way, does pfsense also see the devices individually or does it show everything under ap ip address(192.168.0.5)?
-
You would typically have one SSID on your main subnet, though you could use another. You'd then have a different subnet for the other SSID. What you do with it after that depends on your rules and routing. As I mentioned, my guests only have access to the Internet. They cannot access anything on my local LAN or pfSense, other than pinging the guest interface address (172.16.3.1). Does your AP support VLANs?
-
@JKnott ok. My ap supports vlan. That's how I setup the dual ssid(in your example one is home and one is guest, with home through vpn and guest direct internet). Problem was when I set it up, pfsense router would not see individual guests.
What I could see was trafic to/from ap, but not individual guests.
Or do I have to setup same vlan on ap and router? -
@SlayrNeo Yep, you have to setup VLAN on both the AP and on pfsense.
If you create a VLAN for just the AP, something like VLAN10 as an example, and make the parent interface the LAN port on pfsense, all traffic for both trusted and untrusted (guest) networks will flow over the same physical cable. Very easy to setup and configure.
Then, on your AP, make the SSID for your trusted machines (LAN) the SSID1 you talked about above. And make the SSID for the guests the one with the VAN10 tag on it.
Give both networks a DHCP server, in different subnets, then all you need to do is configure rules on the LAN and on the GUEST networks to make it all work.
Do you have a smart/managed switch that all this stuff plugs into? That's kinda important too.
Jeff
-
@akuma1x I think I misunderstand. If I use 1 vlan only for ap, doesn't pfsense still thinks/sees all trafic on the ap ip? I need the trafic to show per device, so pfsense should see all devices.
With setting up both vlan, is this correct:
Vlan1 on pfsense for wired trafic. Vlan2 on pfsense for the ap.
Vlan1 on ap for home ssid. Vlan2 with own dhcp range for guest network. -
@akuma1x
Router: firebox m500 with upgraded i3 cpu with aes-ni
Ap: cambium e400
Switch: avaya 5500(managed poe)Do I also need to do some settings in switch?
-
@SlayrNeo said in Pfsense with AP dhcp server settings:
Vlan1 on pfsense for wired trafic. Vlan2 on pfsense for the ap.
Vlan1 on ap for home ssid. Vlan2 with own dhcp range for guest network.You don't necessarily need to add 2 separate VLANs, 1 for normal LAN traffic and 1 for GUEST traffic. You technically only need to add 1, for the GUEST network.
Jeff
-
@SlayrNeo said in Pfsense with AP dhcp server settings:
@akuma1x
Router: firebox m500 with upgraded i3 cpu with aes-ni
Ap: cambium e400
Switch: avaya 5500(managed poe)Do I also need to do some settings in switch?
Yep, you need to add a VLAN tag on the port plugged from pfsense to the switch, and the same tag on the port plugged into the access point.
This way, every single port on the switch will be on the LAN network, and only the 2 ports with tags will carry the GUEST VLAN traffic to/from the access point. Since every port on the switch is LAN, the access point can serve 2 purposes - LAN traffic and GUEST traffic, at the same time.
Make sense?
Jeff
-
About all you have to identify the guests would be the IP & MAC addresses. Those would be in the DHCP logs.
What exactly is it you're trying to do?
-
In reference to the switch, when I set up my guest WiFi, I had the guest VLAN 3 configured on pfSense and AP. I also had to configure my managed switch to pass VLAN 3, in addition to the native LAN on the ports connected to pfSense and the AP. If you don't have a managed switch, then just enabling the VLAN on pfSense and AP will work. Some people don't like the idea of having the VLAN available where it's not needed, but it does work.
-
@JKnott I want 2 ssid, my idea was: 1 with ip up to 100 and 1 with ip 150-200. Then i configure in pfsense that all ip in 150-200 should not go through vpn(I already made that rule and that works). Problem is when I configure ap to use ip 150-200 for ssid2, pfsense doesn'tsee those ip. Pfsense just shows the ap ip is using all the data, and doesn't show the 150-200 ip. Because the normal ssid usebundled as ap ip.dhcp from pfsense, those wifi devices do show up. But 150-200 uses ap dhcp, those just show up as
-
@JKnott ok, pfsense configured and I can confirm that works. my laptop receives vlan2 ip address when directly connected to port 3 from router(dedicated port for vlan2). but when connected to switch, the assigned vlan2 ports don't give ip.
I have an Avaya 5500 or Nortel 5520/48pwr.
I have configured vlan2 on the switch. I have assigned ports to it(pfsense router has dedicated port to 47 on switch). The port from ap is in "tagall(trunk)" mode. All other ports in "untagall(access)" mode. vlan1 works, assigns ip and has internet(also wifi). vlan2 works in router, but when plugged in switch and I plug laptop in assigned vlan2 port: nothing(no ip-address, even when I manually set ip: no internet or connection to router/switch).Switch does see which vlanids are active on the ports, those are all correct.
Do you guys have any ideas or can tell me which settings you had to do in switch?
-
@SlayrNeo Did you add the proper VLAN tag to the port that runs back to the pfsense box? It needs to be there, too.
From the post above, it looks like that's port 47, like you say.
Jeff
-
@akuma1x port 3 in pfsense is assigned vlan2 and gives ip to laptop with vlanid=2 when directly connected to port 3.
Avaya switch port 47:
index = 1/47
Vlanids = 2
Discarduntagged frames = false
filterunregisteredframes = true
defaultvlanid = 2
port priority = 0
tagging = untagall(access)In general:
Vlan 1 ports:
index = 1/xx
Vlanids = 1
Discarduntagged frames = false
filterunregisteredframes = true
defaultvlanid = 1
port priority = 0
tagging = untagall(access)Vlan 2 ports:
index = 1/xx
Vlanids = 2
Discarduntagged frames = false
filterunregisteredframes = true
defaultvlanid = 2
port priority = 0
tagging = untagall(access)Only Port 11(Cambium AP):
index = 1/11
Vlanids = 1,2
Discarduntagged frames = false
filterunregisteredframes = true
defaultvlanid = 1
port priority = 0
tagging = tagall(trunk)Cable from pfsense port3 to switch port 47. Then cable from vlan2 assigned port on switch to laptop: nothing(even when I manually add vlan2 id and/or ip address in vlan2 group).
-
@SlayrNeo To me, after reading all the steps you've tried, looks like something isn't cooperating in the switch. I don't know what else to tell you. I'm not familiar with that switch, so I can't help you troubleshoot it.
Can you reset the switch back to factory defaults, or is that not possible? It's a long shot, but maybe there's a setting in there somewhere that you're unaware of, that's keeping this all from working properly.
Jeff
-
Ok, maybe this helps.
When I try to ping lan connected devices(wired or wireless), I can ping everything on lan.
When I try to ping the managed switch on ip in lan, I get response.
When I try to ping the managed switch on ip in vlan2 with vlan2 interface I don't receive response.
When I try to ping the managed switch on ip from lan with vlan2 interface I receive response.Is this correct or should the outcomes from the last 2 be reversed? Otherwise this might be another symptom of my problem ;)
-
@SlayrNeo said in Pfsense with AP dhcp server settings:
Ok, maybe this helps.
When I try to ping lan connected devices(wired or wireless), I can ping everything on lan.That's normal, because devices on the SAME subnet never go thru the firewall. Therefore, no matter what your pfsense LAN rules look like, a ping from one machine to another machine, say thru a switch, on the same subnet, will most likely ALWAYS work.
When I try to ping the managed switch on ip in lan, I get response.
Same as above, same subnet traffic.
When I try to ping the managed switch on ip in vlan2 with vlan2 interface I don't receive response.
You probably don't have an appropriate firewall rule on your VLAN2 to allow/pass ping traffic to anywhere else. Attaching a screenshot of your VLAN2 firewall rules would help here.
When I try to ping the managed switch on ip from lan with vlan2 interface I receive response.
This is most likely because you have an ALLOW any LAN traffic to any destination, the default rule, on your pfsense LAN firewall rule tab.
Jeff
-
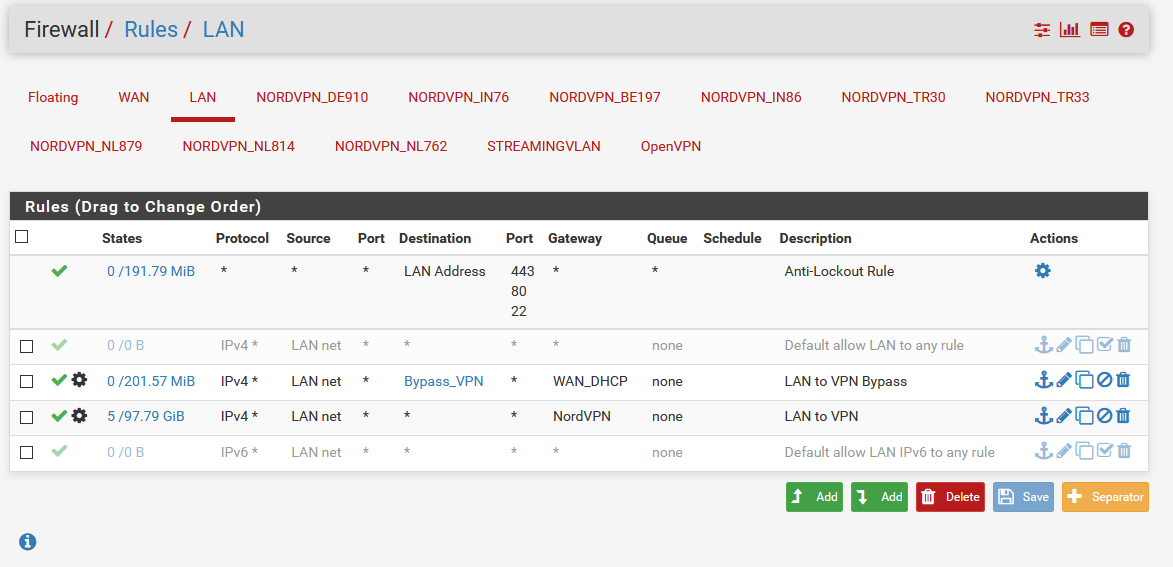
The rules on vlan:
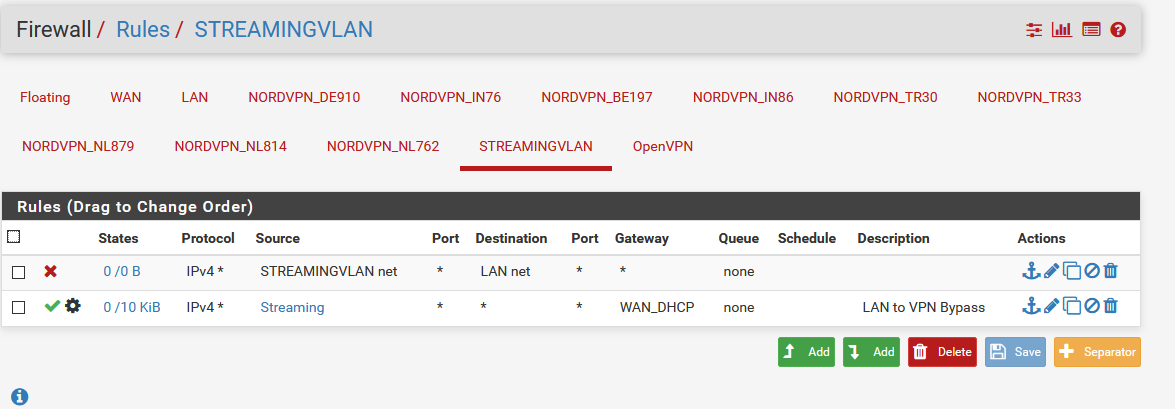
the rules on lan: