DNS Resolver/Unbound is not resolving
-
Hi guys,
for some reason I can't get the DNS Resolver/Unbound to do it's job. It seems that over time I must have misconfigured something so that it stopped working in the default way: to resolve DNS locally via 127.0.0.1 without any external server. (Temporarily I've added a forwarding rule to 1.1.1.1 in the config just so that I can access the internet right now.)
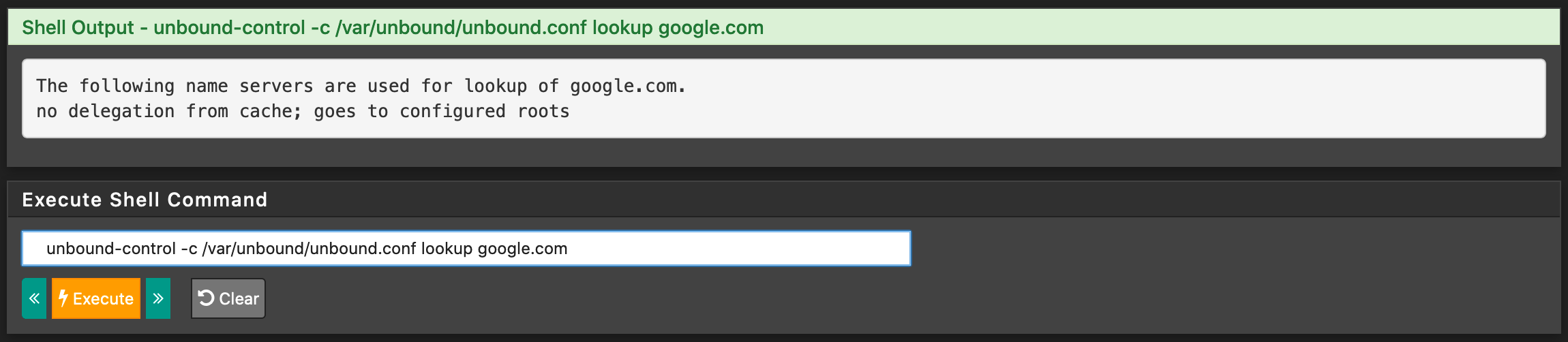
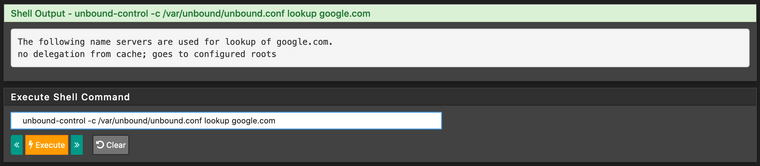
I've followed a lot of tipps and setting advices on this forum and reddit but nothing's working. So here I am, asking for help. I've disabled pfBlockerNG, removed every firewall rule that I temporarily tried to forward DNS traffic, removed the unbound_control and anbound_server files, restarted unbound and the system, tried to dig & trace the resolver. I'm lost. The system logs don't show anything suspicious to me (no errors), the DNS lookup just gives me a "Host "google.com" could not be resolved."
Running latest version 2.4.5-RELEASE-p1 (amd64)
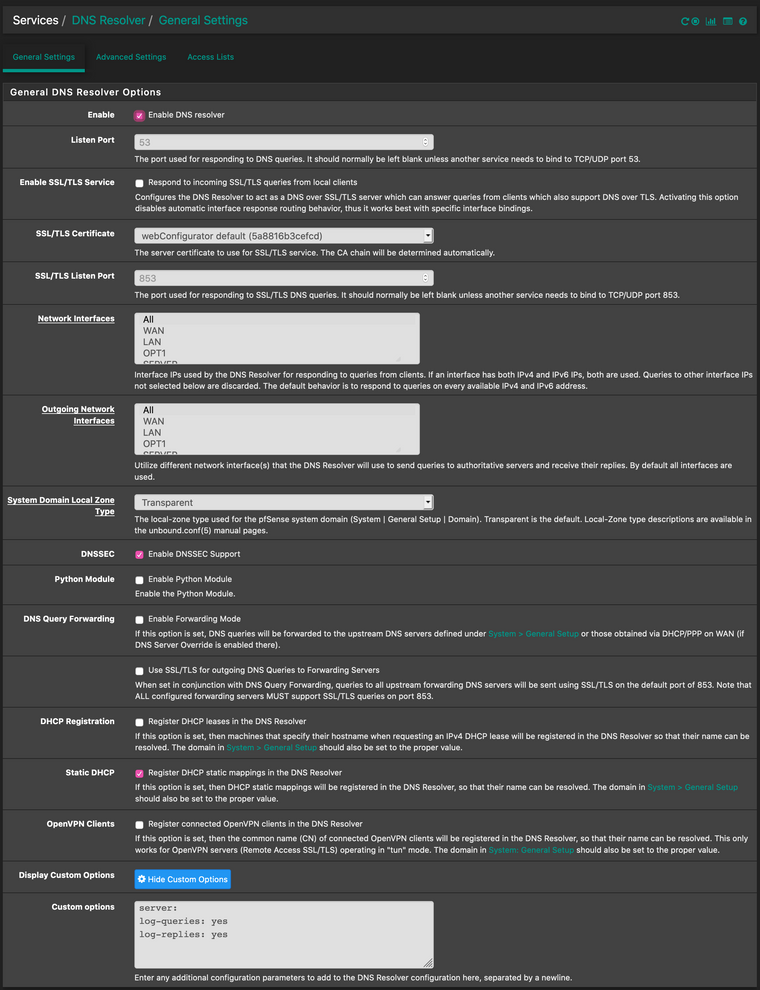
Here's my unbound.config:
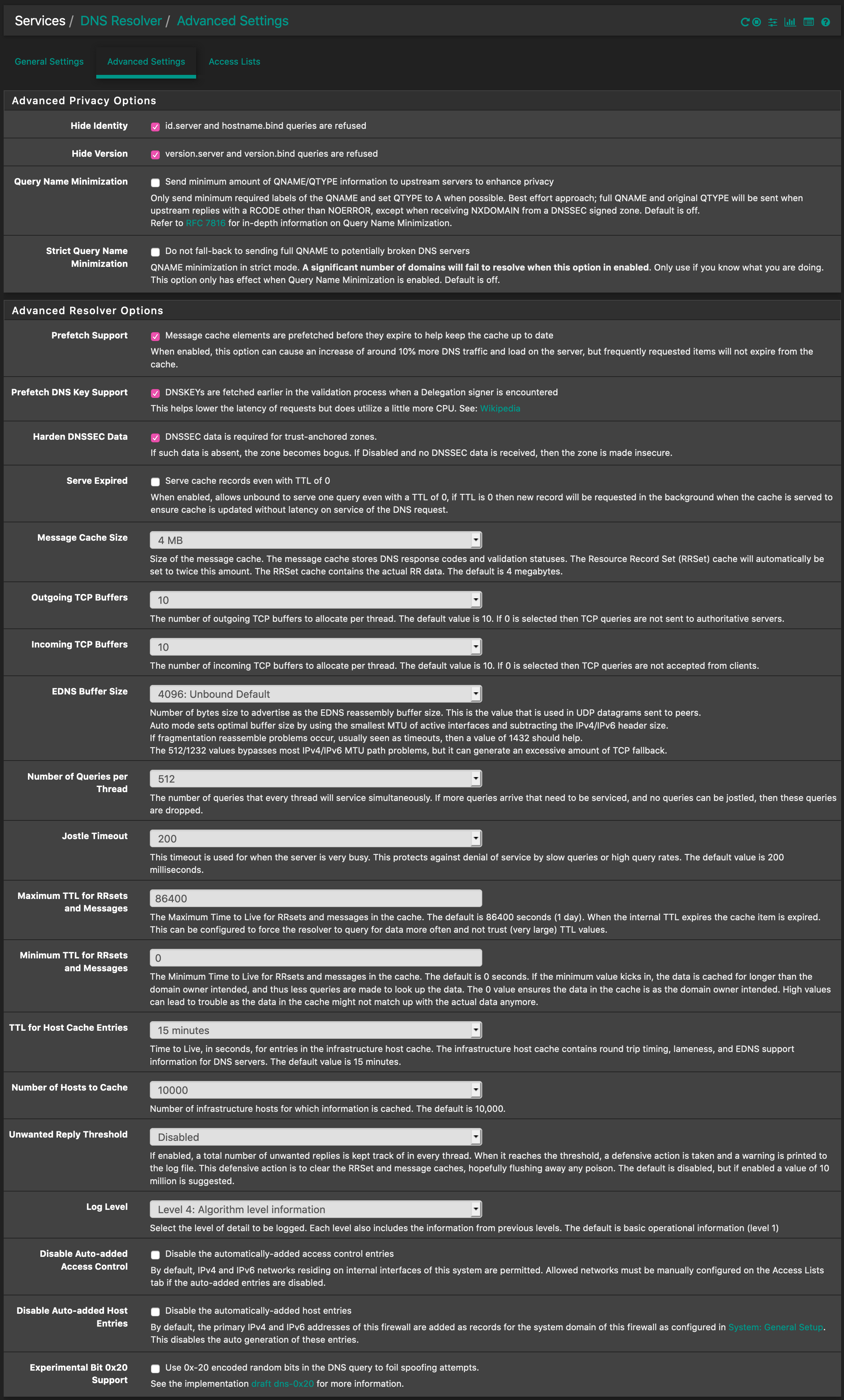
########################## # Unbound Configuration ########################## ## # Server configuration ## server: chroot: /var/unbound username: "unbound" directory: "/var/unbound" pidfile: "/var/run/unbound.pid" use-syslog: yes port: 53 verbosity: 4 hide-identity: yes hide-version: yes harden-glue: yes do-ip4: yes do-ip6: yes do-udp: yes do-tcp: yes do-daemonize: yes module-config: "validator iterator" unwanted-reply-threshold: 0 num-queries-per-thread: 512 jostle-timeout: 200 infra-host-ttl: 900 infra-cache-numhosts: 10000 outgoing-num-tcp: 10 incoming-num-tcp: 10 edns-buffer-size: 4096 cache-max-ttl: 86400 cache-min-ttl: 0 harden-dnssec-stripped: yes msg-cache-size: 4m rrset-cache-size: 8m num-threads: 4 msg-cache-slabs: 4 rrset-cache-slabs: 4 infra-cache-slabs: 4 key-cache-slabs: 4 outgoing-range: 4096 #so-rcvbuf: 4m auto-trust-anchor-file: /var/unbound/root.key prefetch: yes prefetch-key: yes use-caps-for-id: no serve-expired: no # Statistics # Unbound Statistics statistics-interval: 0 extended-statistics: yes statistics-cumulative: yes # TLS Configuration tls-cert-bundle: "/etc/ssl/cert.pem" # Interface IP(s) to bind to interface-automatic: yes interface: 0.0.0.0 interface: ::0 # Outgoing interfaces to be used # DNS Rebinding # For DNS Rebinding prevention private-address: 127.0.0.0/8 private-address: 10.0.0.0/8 private-address: ::ffff:a00:0/104 private-address: 172.16.0.0/12 private-address: ::ffff:ac10:0/108 private-address: 169.254.0.0/16 private-address: ::ffff:a9fe:0/112 private-address: 192.168.0.0/16 private-address: ::ffff:c0a8:0/112 private-address: fd00::/8 private-address: fe80::/10 # Set private domains in case authoritative name server returns a Private IP address # Access lists include: /var/unbound/access_lists.conf # Static host entries include: /var/unbound/host_entries.conf # dhcp lease entries include: /var/unbound/dhcpleases_entries.conf # Domain overrides include: /var/unbound/domainoverrides.conf # Unbound custom options server: log-queries: yes log-replies: yes forward-zone: name: "." forward-ssl-upstream: yes forward-addr: 1.1.1.1@853 forward-addr: 1.0.0.1@853 # ^^ I've added the forwarding part just temporarily to access the web right now. #### ### # Remote Control Config ### include: /var/unbound/remotecontrol.conf
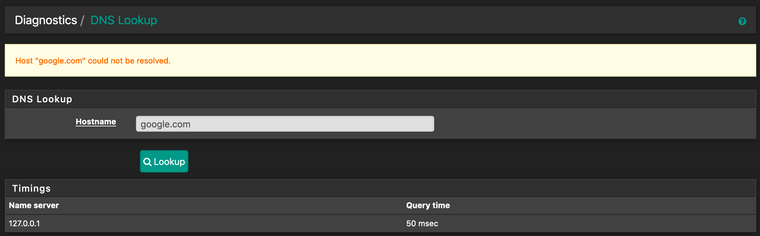
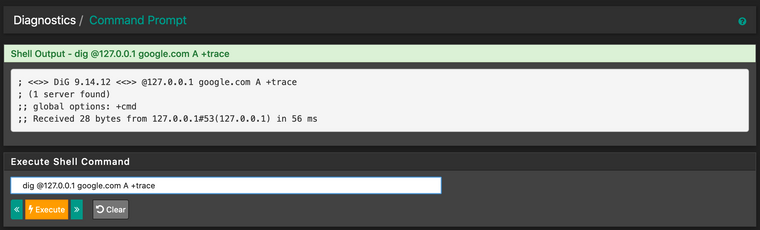
Thanks for your help in advance!!
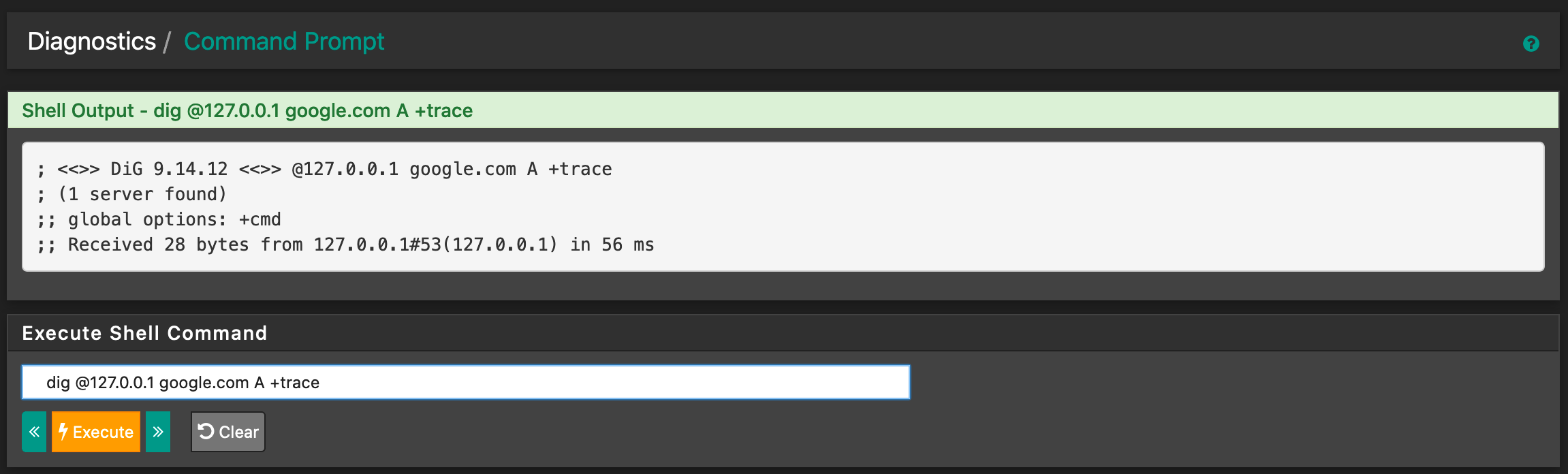
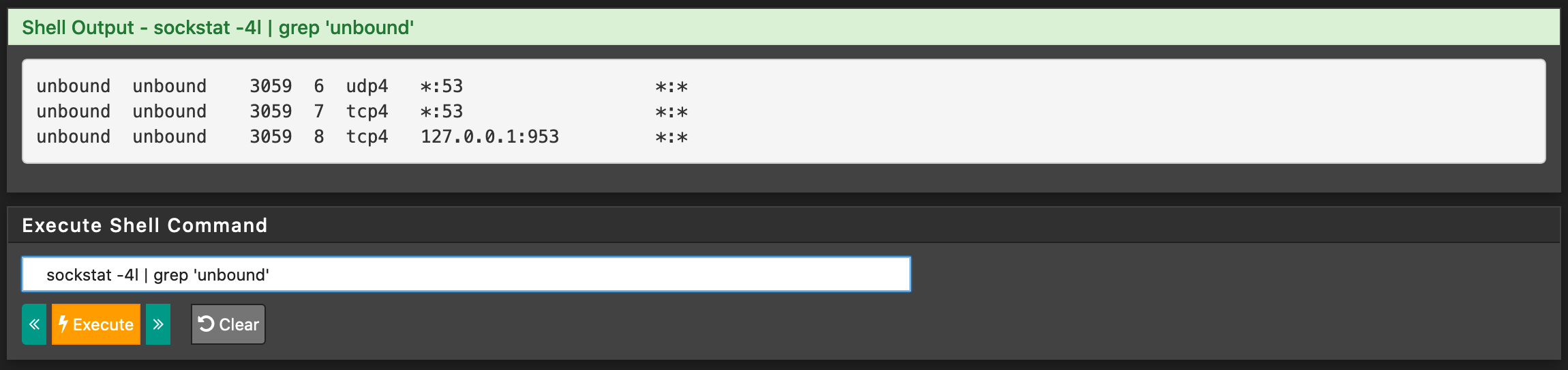
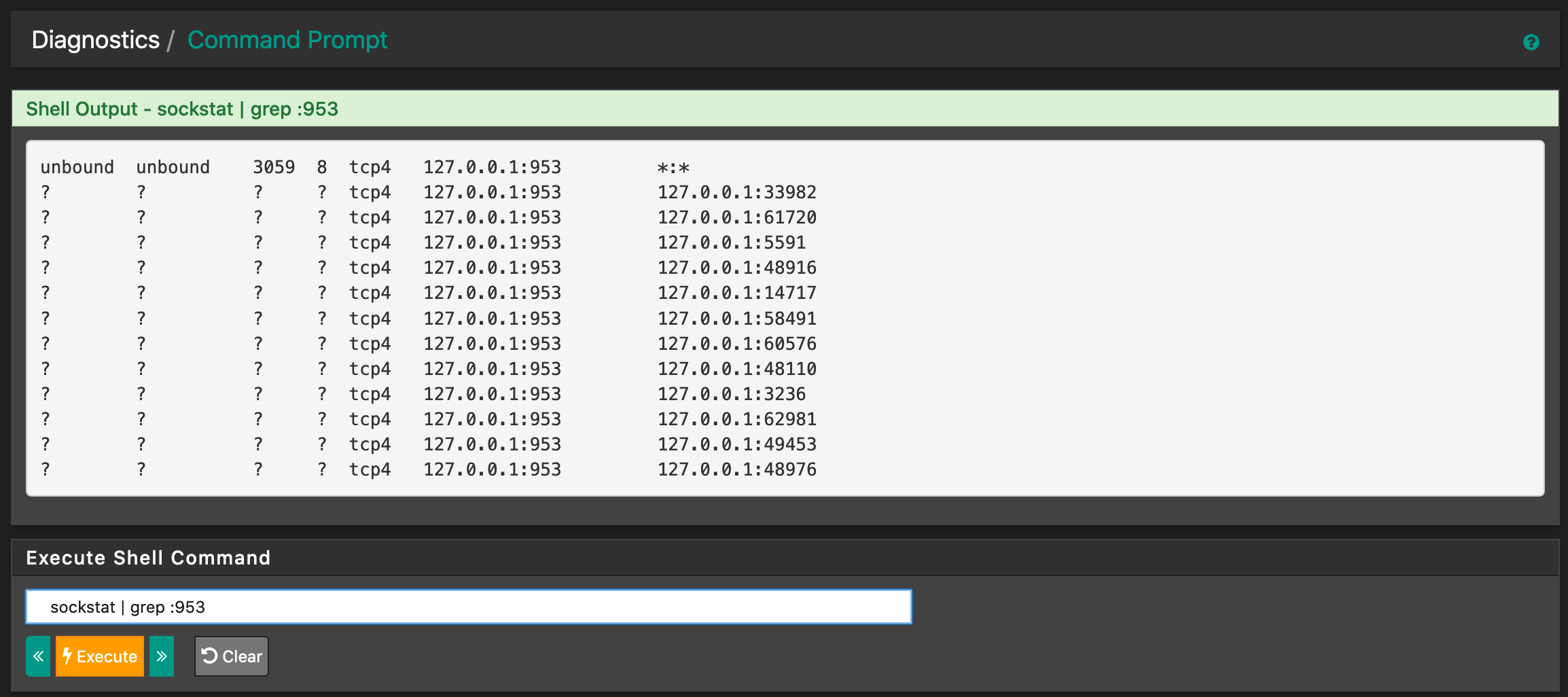
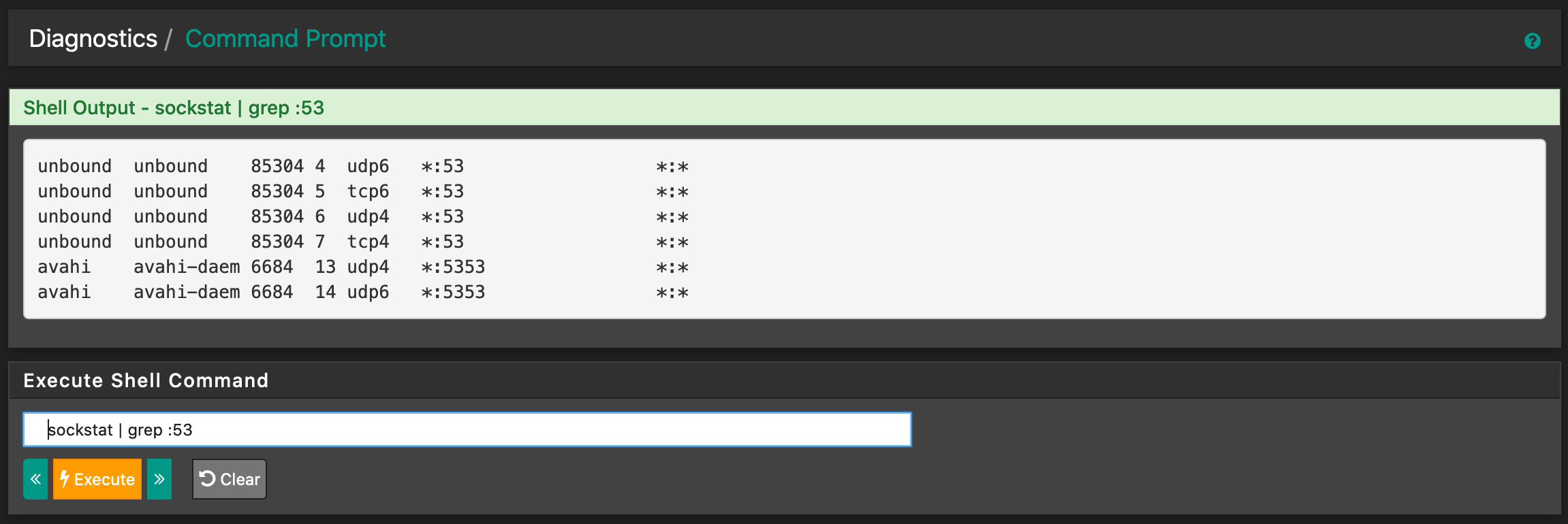
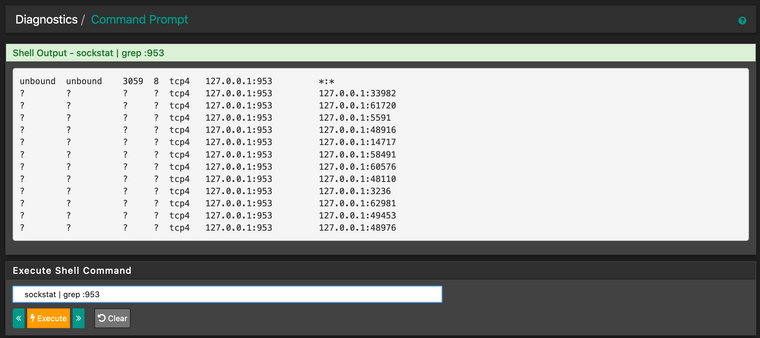
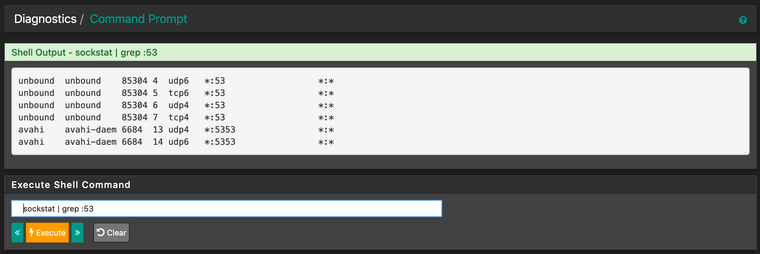
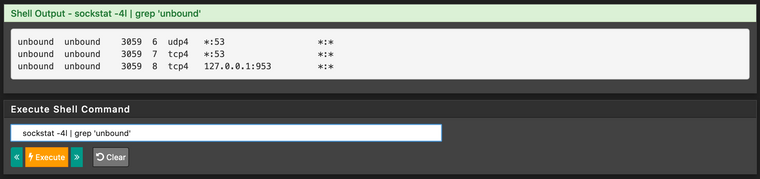
Edit: Added screenshots. I think that the output of sockstat | grep :953 is kind of suspicious as there seems to be something off? Multiple processes listening to the port?
-
So unfortunately no one has an idea on how to fix this or what I'm missing/overseeing in the configuration?
I'd really appreciate any thoughts on what to try to get rid of the DNS forwarding. :)
Thanks!
-
@2malH said in DNS Resolver/Unbound is not resolving:
So unfortunately no one has an idea on how to fix this or what I'm missing/overseeing in the configuration?
Can't really see why unbound refuses to work ....
For testes, use the SSH (or console) access, it far more easier to work with.
Like :dig @127.0.0.1 google.com ANYThis :
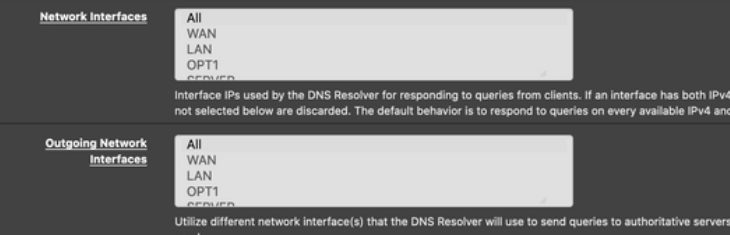
both are set to "All", right ?
Like
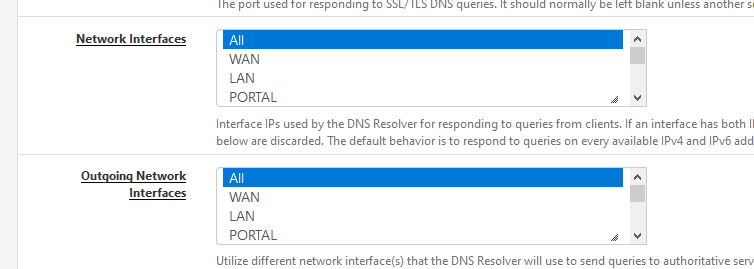
Your unbound.conf mentions that you included other lines, like
forward-zone: name: "." forward-ssl-upstream: yes forward-addr: 1.1.1.1@853 forward-addr: 1.0.0.1@853What happens if you back your settings, and reset your settings, make you WAN work (and do nothing more) : does unbound work now ?
If so, compare actual, resetted settings with your back up settings.Btw : you do not block TCP port 53 traffic with a floating firewall rule, right ? (DNS can also be TCP, not only UDP, especially if you ask DNSSEC info)
These :
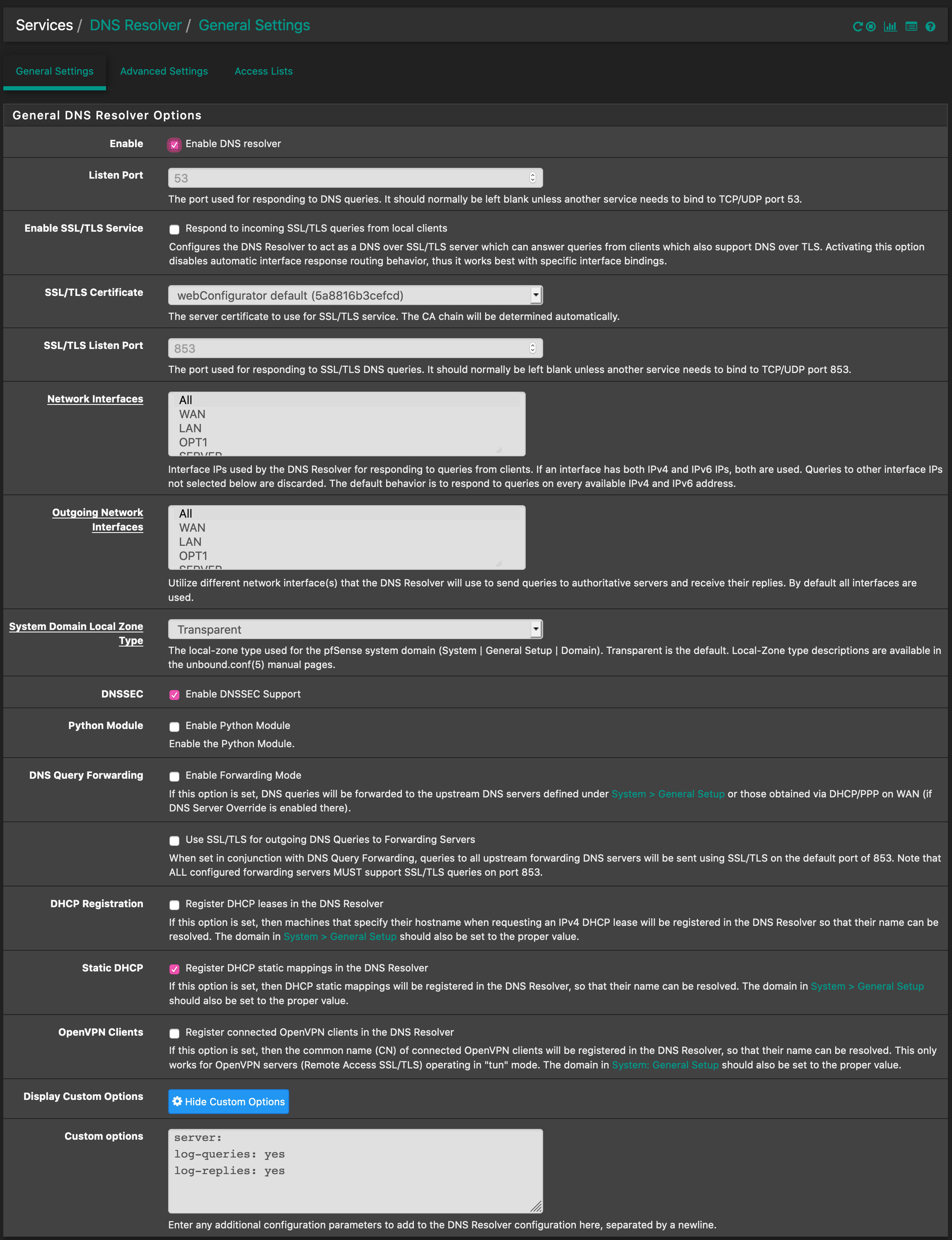
log-queries: yes log-replies: yeswill 'explode' your logs as there will be a huge number of log lines.
Remember : to much info kills the info.