Missing LAN Interface
-
@ta2oo said in Missing LAN Interface:
Thanks for nudge
You welcome

btw:
be careful with the VM environment, it can cause a lot of weirdness, if the NIC(s) pass-through is set incorrectly -
Hi.
I'm scouring the internet to understand how best to configure pfSense to isolate the lab from my home network but maintain internet access.
I'm investigating more along the lines of how to deploy the VMs onto a new VLAN to route through pfSense and then work out to route this traffic to the internet only.
If you know of any good resources on this subject I would be so grateful.
Thanks Phill.
-
@ta2oo said in Missing LAN Interface:
If you know of any good resources on this subject I would be so grateful.
You don't even need a tutorial...
The answer is simple:
Buy (eBay or other) a cheap, used 4-port Intel (genuine) NIC and segmented your network into a separate interfaces, like WLAN for WiFi / mobile, IoT, DMZ, LAN, VPN, GAME, etc.
(Intel I340-T4, I350-T4, I210, I211, PRO1000)
I prefer this solution over VLANs where this can be possible.
VLAN is also a good solution where there is no free interface, but remember VLANs consume bandwidth.I tend to solve VLANs question with an L3 capable switch

+++edit:
or...
https://netosec.com/protect-home-network/
https://docs.netgate.com/pfsense/en/latest/book/vlan/vlans-and-security.html
https://www.youtube.com/watch?v=b2w1Ywt081o -
Hi DaddyGo.
Thanks, I'll have a read and digest.
I do like Unifi, I have the 3 x AP AC Pro's distributing my home WiFi, but as I'm studying for my CCNA I've gone the Cisco route for equipment, C3750G, ASA5520 & ISR2901. The equipment started out as part of a separate hardware lab but I just could help myself and migrated my home network

I have the L3 infrastructure in place to manage VLAN routing once the network traffic leaves the various VMs, I have pfSense setup as a VM to manage traffic segregation so only traffic that requires internet access gets through, this is where I am at now. I am new to pfSense and Hyper V, bit of a learning curve but I love it.
I know this has all gone a little off topic from my initial post, I appreciate you giving me your time and continuing.
I've attached my current network topology below. My thinking is.
- Create a new VLAN in pfSense and tag the Hyper V virtual interfaces with this VLAN
- Create the same VLAN on my 3750 and change the desktop switch port from access to trunk and allow only the new VLAN and VLAN3 for my desktop
- Configure ACL's on the 3750 to allow this VLAN out over 192.168.10.101 only
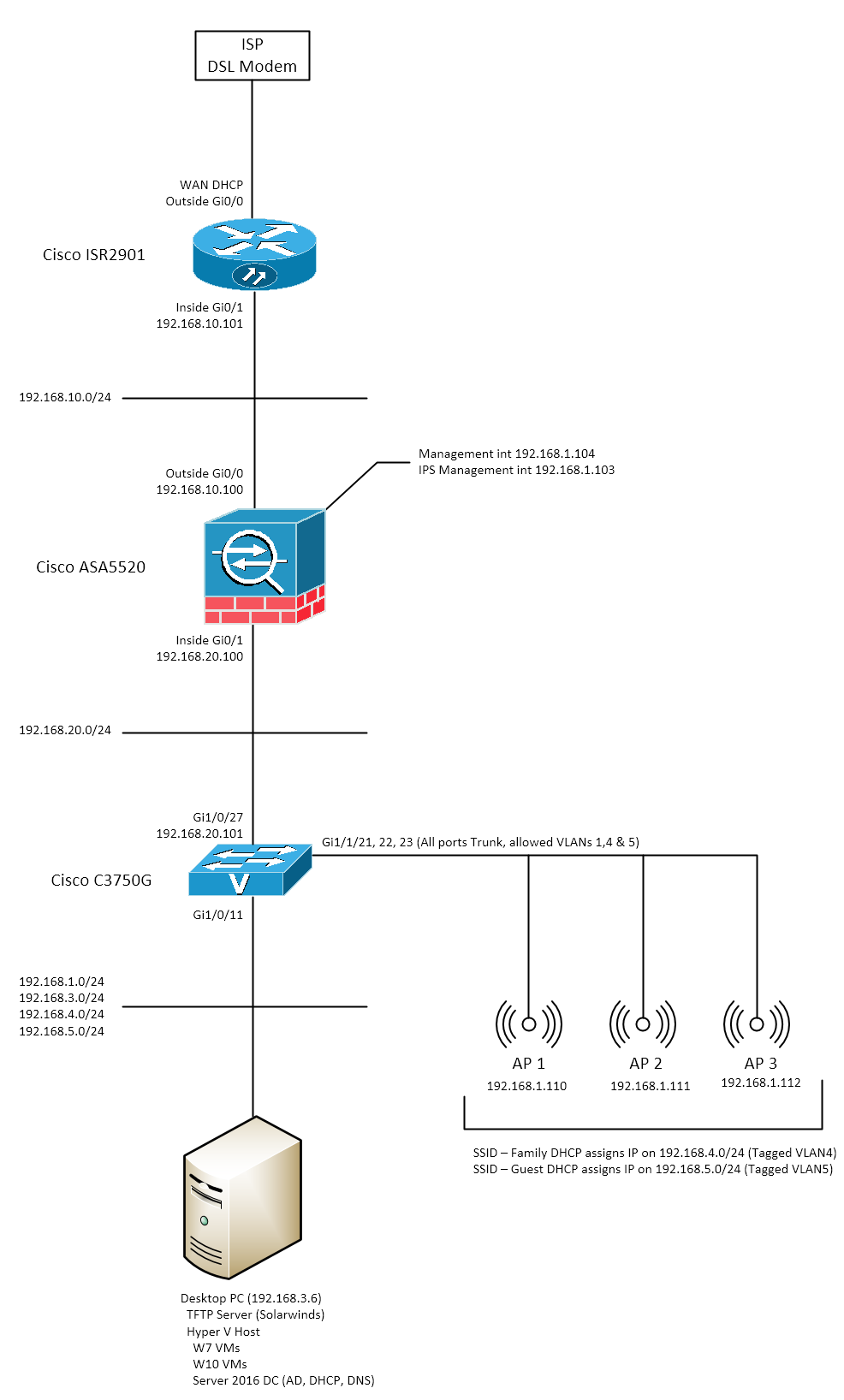
Thanks again.
Phill
-
@ta2oo said in Missing LAN Interface:
I do like Unifi, I have the 3 x AP AC Pro
I like it too, but we usually work with the Cisco WAP series and Ruckus
So about your drawing:
There is no problem with this solution and/or network topology.
What I would like to point out that you use Gig interfaces thus, each VLAN consumes your bandwidth (on trunk) the more of your VLANs, the further you slice the Gig bandwidth.
Think only of the way,......... f.e.: I currently have an ISP 1000/500 GPON, ergo Gig internet speed available to my desktop (wired Cat6A), if I load this internal interface even with VLANs I can't take advantage of the ISP Gig connection, because the bandwidth is shared between the VLANs.
Therefore, I have a Supermicro-based device with 8 ports (for pfSense), where each interface is a separate subnet and then I distribute the VLANs in a Cisco SG350X, which Cisco does very well.
So my network is fully segmented and I trunk forwarding VLANs on the Cisco SG350X 10Gig port to other swithes.
The 10Gig interface delivers nearly 7 to 8 VLANs as well
-
Sweet, gig internet to desktop. I'm way off with my 100Mb connection although Virgin Media do a 500Mb service.
Ok, I'm understanding that bandwidth will be affected for each and every VLAN on a trunked interface, effectively throttling my share of the bandwidth. Some of the hardware solutions for pfSense are nice but a little outside of my budget at the moment. Hardware is definitely the way to go and I think long term for my lab this is something I'd like to invest in.
For now I'm going to have to stick with the pfSense VM. So, if I can get my hands on a 4 port gig Ethernet card for the PC I have my VMs running on, I can create virtual network interfaces for each VLAN (up to 4), assign a single VLAN to each gig port and patch these direct to my Cisco 3570 ports, configured for access and set to the appropriate VLAN.
Many Thanks
Phill
-
@ta2oo said in Missing LAN Interface:
I think long term for my lab this is something I'd like to invest in.
This is a good idea as it can get more out of your system

-
Hi.
Going back to my original issue which was resolved by creating the virtual switches in Hyper V.
I have since created another 2 private virtual switches, LAN3 and Test1, which should identify as OPT2 and OPT3, these are not showing in the console interface assignments page.
I've rebooted pfSense and Hyper V a few times, I've removed the virtual switches and re-created them.
The original WAN & LAN assignments are still working fine.
I don't think that I am missing anything as the configuration options set are the same as the two interfaces I currently have working.
Sorry to keep going on, I though I had this cracked

Thanks Phill
-
Ok.......
so I've taken another look Hyper V and realised that although I had created the new virtual switch connections I had only applied to the interfaces to the client VMs.
I've applied the virtual switch connections to pfSense VM and voila, they now appear in the console ready for configuration.
The case of the missing LAN interfaces is now closed.
Thank you for your advise and support on this topic, I'm sure as I learn more about pfSense there will new posts

Phill
-
@ta2oo said in Missing LAN Interface:
I had only applied to the interfaces to the client VMs.
I'm so glad you successfully configured the interfaces.
Yesterday unfortunately I could not look into the forum we had a little Citrix problem.btw:
Reading this way, I thought you had an interface pass-through issue...
When we talk about hypervisor, we almost always make mistakes here this point....