Issues connecting to doxy.me with pfsense
-
Hi - we are a clinic that has been using doxy.me for tele-medicine visits. We recently upgraded our connection to accommodate this and also went to an SG-3100 from an edgerouter. The issue we are having is clients are connecting to our providers using doxy, and the clients cant see or hear the providers - however the providers can see and hear the clients. This is a new issue that didn't happen with the edgerouter.
I think something is being blocked someplace, but I do not see anything obvious in the firewall logs. We have pure NAT enabled, and also set up a static outbound port for these connections. Doxy's website for configuring this is here: https://help.doxy.me/en/articles/95887-network-security-port-and-firewall-configuration - according to this our config should work fine.
We do not block anything outbound, and UPNP is even enabled for troubleshooting this issue and it still doesn't work. Any other video conferencing sevice (teams, zoom, etc) all work fine.
Is anyone else having a similar issue? I am not sure what to check next at this point.
-
Can we assume the 'providers' are behind pfSense here and clients are external?
It should be falling back to port 443 is other ports cannot be used but maybe that is failing. I would guess it's because pfSense randomises outbound source ports and there are still some applications that cannot cope with that.
Try adding an outbound NAT rule with static source ports set for a test device behind the firewall and see if that allows it.Steve
-
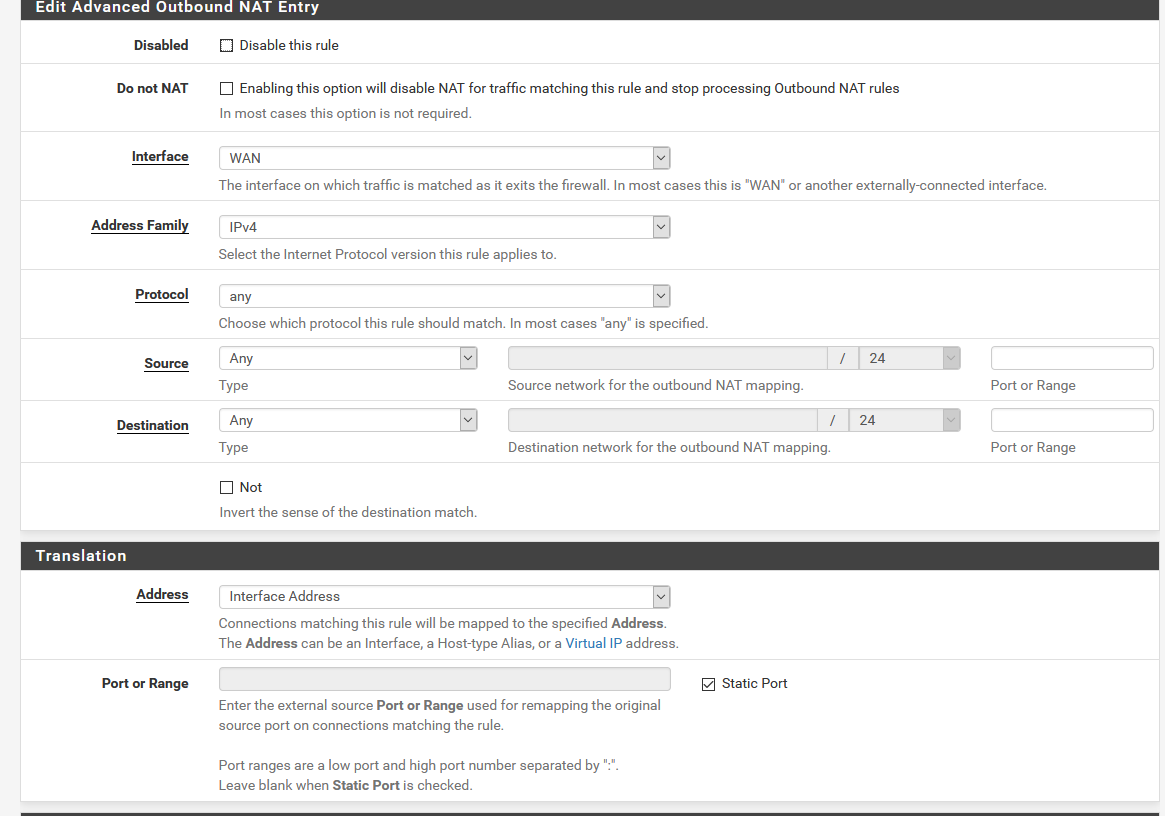 This is the NAT rule - that should do static port for the whole LAN correct? Even with that in place it does not seem to be working. Yes - the providers are behind the firewall and the clients are out in the community.
This is the NAT rule - that should do static port for the whole LAN correct? Even with that in place it does not seem to be working. Yes - the providers are behind the firewall and the clients are out in the community. -
You should never use an outbound NAT rule with source set to 'any' as it will catch all traffic including traffic from the firewall itself which can break things like VPNs.
That would catch traffic from the internal devices though.
Unless you're filtering outbound traffic there shouldn't be anything more required.
Steve
-
Ok - I edited the rule to remove the any, and instead did the subnet the devices are on, however that still didn't work even after rebooting the firewall and the devices behind it. I removed the rule completely though and remake it exactly the same, and now it seems to be working fine.
From what I can tell - pfense still seemed to be stuck randomizing ports until I completely remade the rule, it wasn't respecting that static port selection. Either way, its working now - thanks for the help!
-
There were probably states open already carrying the traffic. Adding the new rule would not have removed those but they would have eventually timed out and been replaced by states with static ports when re-opened.
Be aware that static source ports can occasionally be a problem if set for everything like that. If you have two clients behind the firewall trying to connect to the same external IP with the same source and destination ports one will fail.Steve