pfsense on Netgate SG-1100: IKEv2 VPN with EAP-TLS Authentication Failed
-
Hi everyone! I am trying to set up IPSec IKEv2 VPN with EAP-TLS Authentication using these instructions.
Although, I tried to do my best in terms of following the instructions, created the CA, Server Cert and Client Cert, I still cannot make the authentication work, so posting it here in order to beg the community for help, lol, as my inability to solve this issue freaks me out.
Attaching the log from my StrongSwan Android client. For relative anonymity purposes, I have masked the following data in the log:
<IPSEC_SERVER_IP> - my firewall's static public IP
<MY_ORG> - the stupid name I made up for my self-signed CA and certificates.Strongswan Android client log:
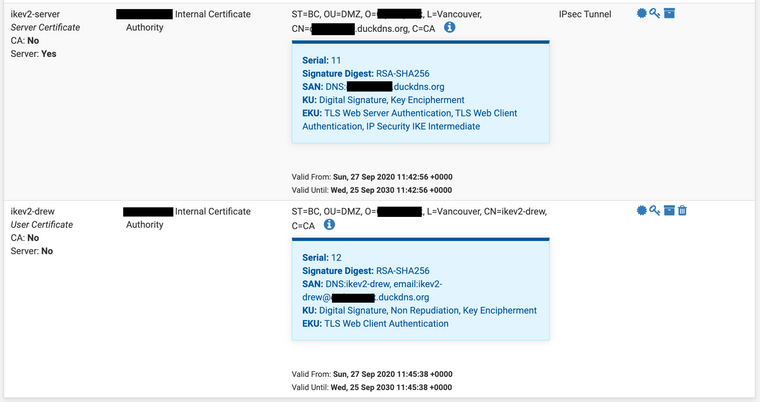
Sep 26 20:26:00 00[DMN] +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Sep 26 20:26:00 00[DMN] Starting IKE service (strongSwan 5.8.4, Android 10 - QQ3A.200705.002/2020-07-05, Pixel 2 XL - google/taimen/Google, Linux 4.4.210-gff8bddbea588, aarch64) Sep 26 20:26:00 00[LIB] loaded plugins: androidbridge charon android-log openssl fips-prf random nonce pubkey chapoly curve25519 pkcs1 pkcs8 pem xcbc hmac socket-default revocation eap-identity eap-mschapv2 eap-md5 eap-gtc eap-tls x509 Sep 26 20:26:00 00[JOB] spawning 16 worker threads Sep 26 20:26:00 06[CFG] loaded user certificate 'CN=drew, C=CA, ST=BC, L=Vancouver, O=<MY_ORG>, OU=DMZ' and private key Sep 26 20:26:00 06[CFG] loaded CA certificate 'CN=<MY_ORG>-internal-ca, C=CA, ST=BC, L=Vancouver, O=<MY_ORG>, OU=DMZ' Sep 26 20:26:01 06[IKE] initiating IKE_SA android[33] to <IPSEC_SERVER_IP> Sep 26 20:26:01 06[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Sep 26 20:26:01 06[NET] sending packet: from 10.198.87.82[49354] to <IPSEC_SERVER_IP>[500] (716 bytes) Sep 26 20:26:01 09[NET] received packet: from <IPSEC_SERVER_IP>[500] to 10.198.87.82[49354] (305 bytes) Sep 26 20:26:01 09[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ] Sep 26 20:26:01 09[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256 Sep 26 20:26:01 09[IKE] local host is behind NAT, sending keep alives Sep 26 20:26:01 09[IKE] received cert request for "CN=<MY_ORG>-internal-ca, C=CA, ST=BC, L=Vancouver, O=<MY_ORG>, OU=DMZ" Sep 26 20:26:01 09[IKE] sending cert request for "CN=<MY_ORG>-internal-ca, C=CA, ST=BC, L=Vancouver, O=<MY_ORG>, OU=DMZ" Sep 26 20:26:01 09[IKE] establishing CHILD_SA android{33} Sep 26 20:26:01 09[ENC] generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Sep 26 20:26:01 09[NET] sending packet: from 10.198.87.82[37865] to <IPSEC_SERVER_IP>[4500] (560 bytes) Sep 26 20:26:01 10[NET] received packet: from <IPSEC_SERVER_IP>[4500] to 10.198.87.82[37865] (80 bytes) Sep 26 20:26:01 10[ENC] parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ] Sep 26 20:26:01 10[IKE] received AUTHENTICATION_FAILED notify errorMy Certificates have the following CNs and SANs:
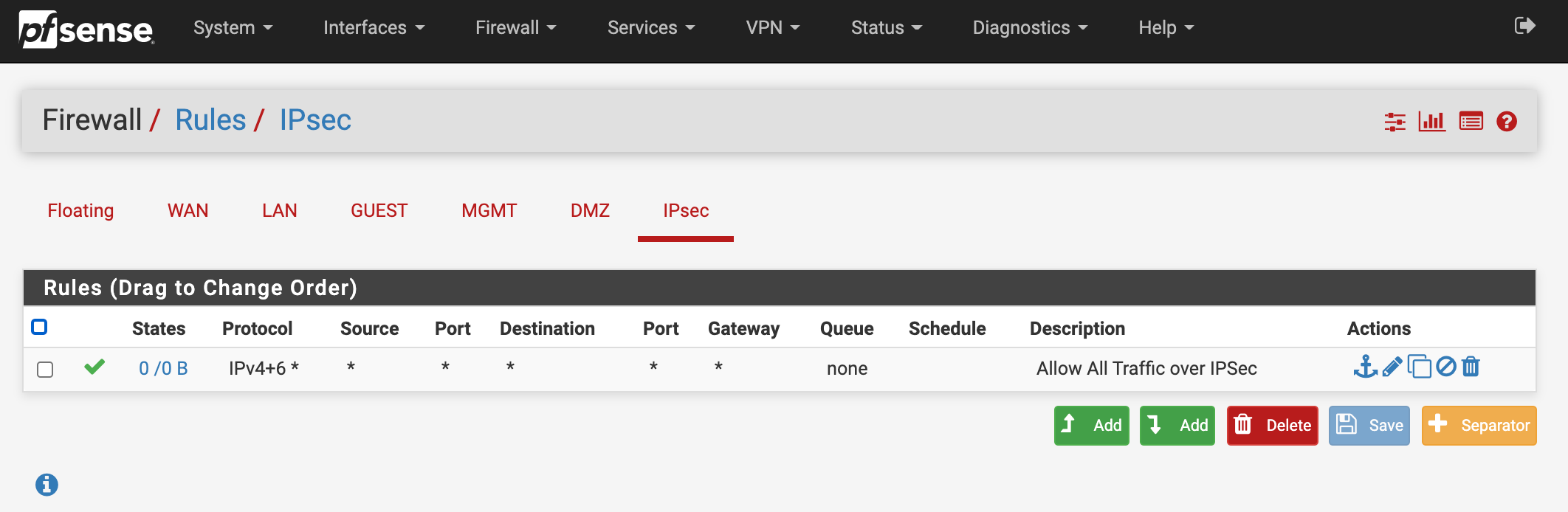
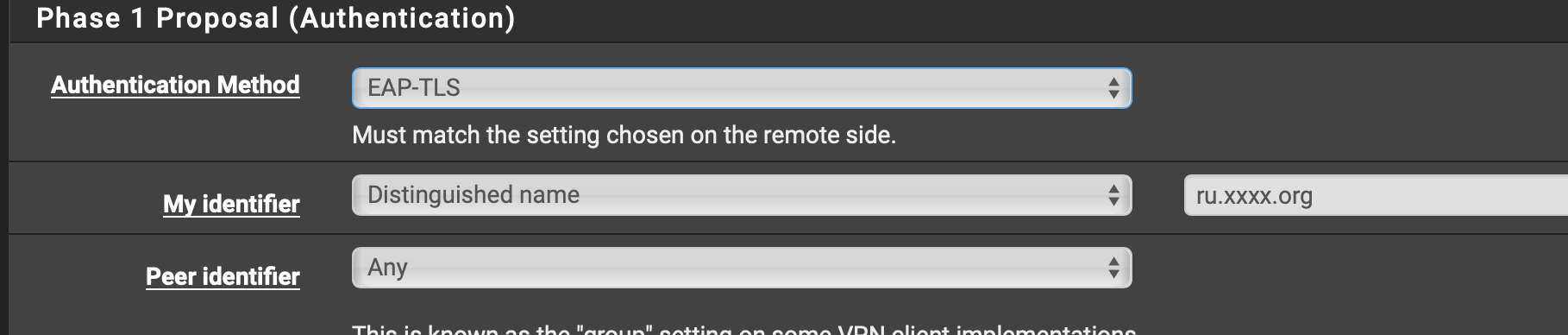
My IPSec Configuration:
VPN / IPSec / Tunnels

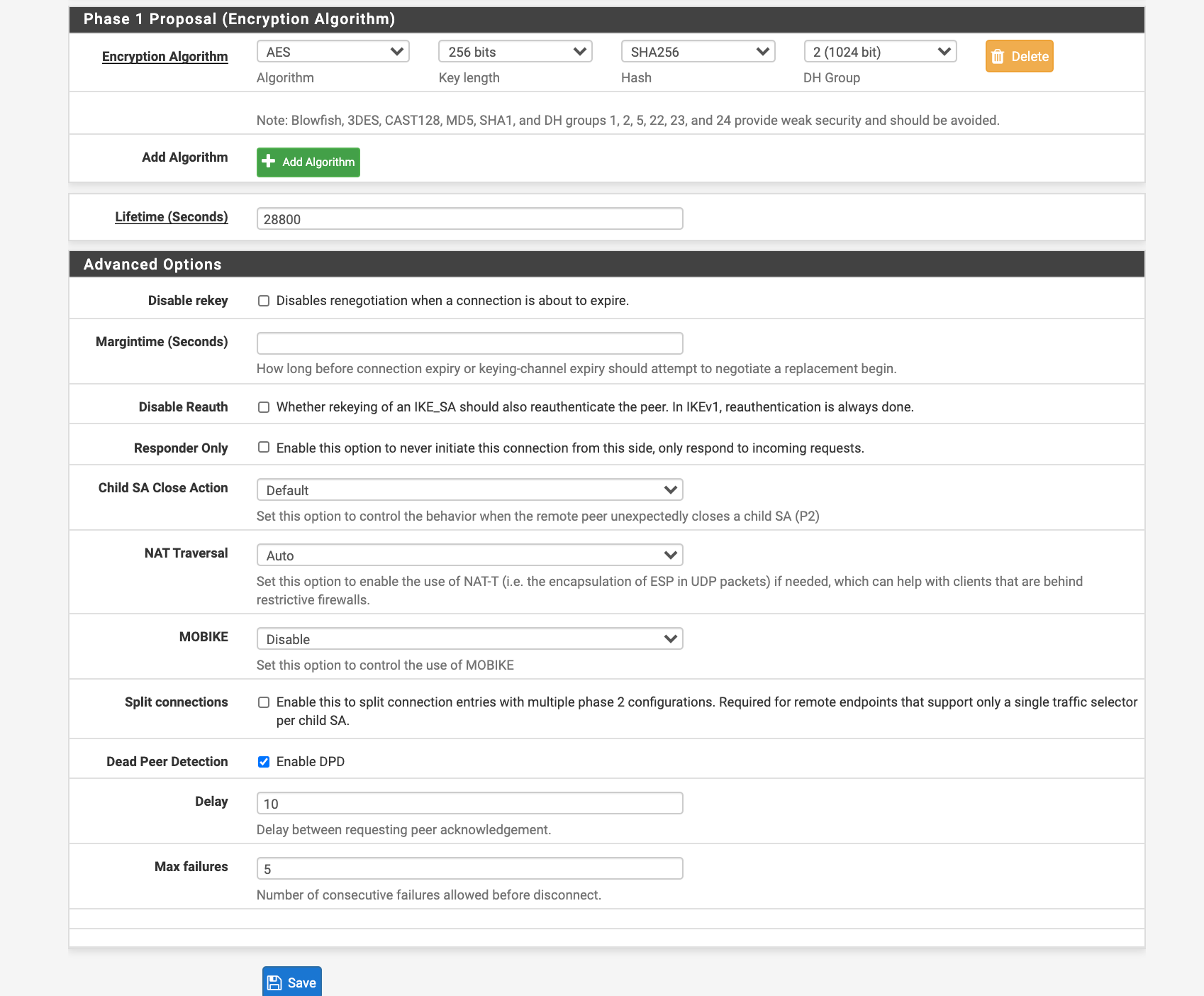
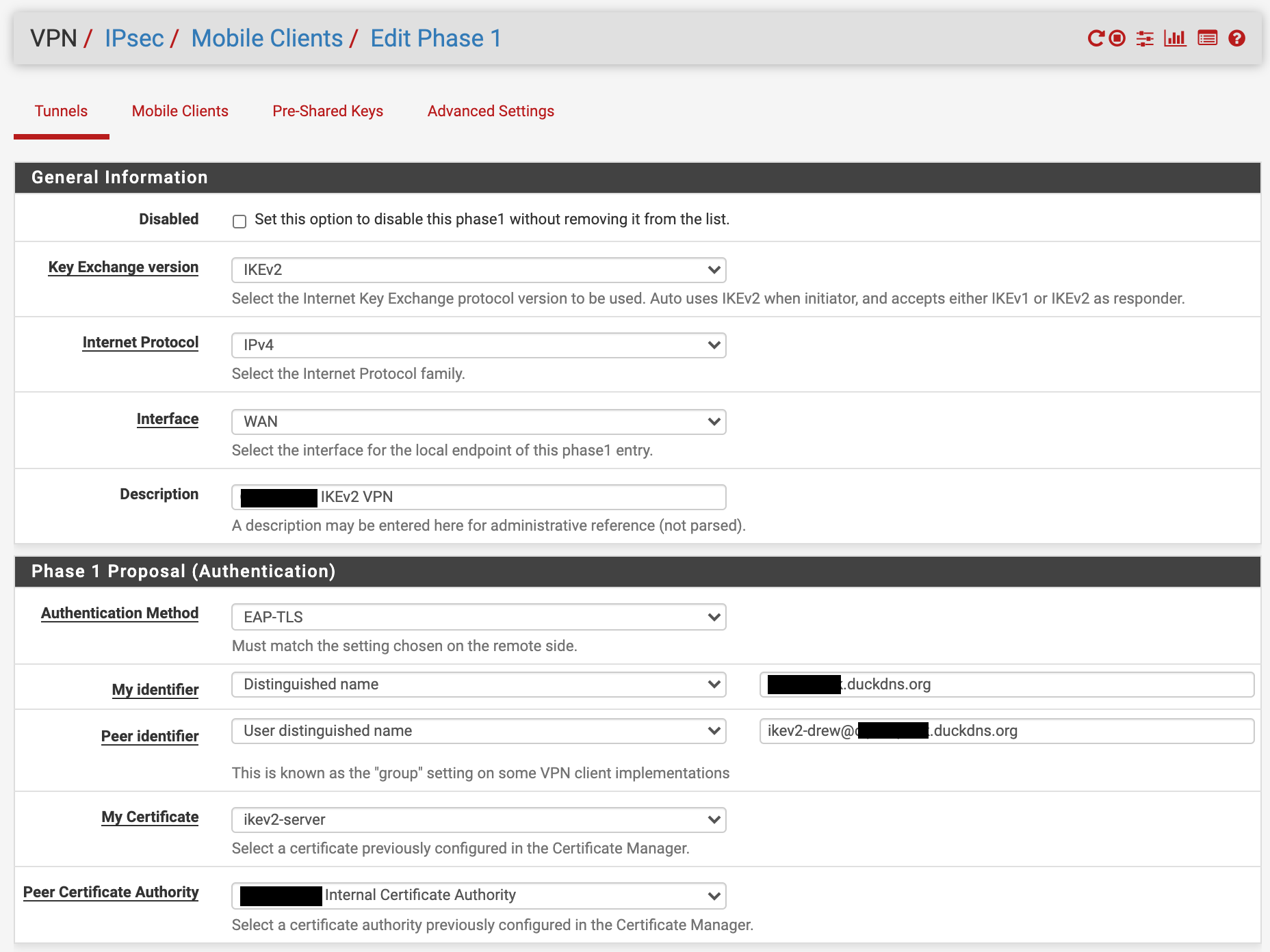
Phase 1
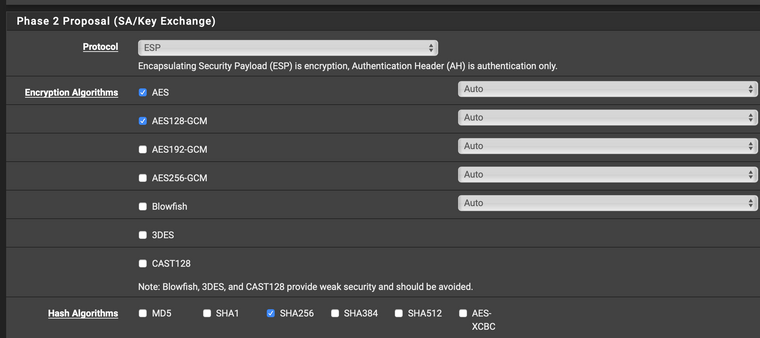
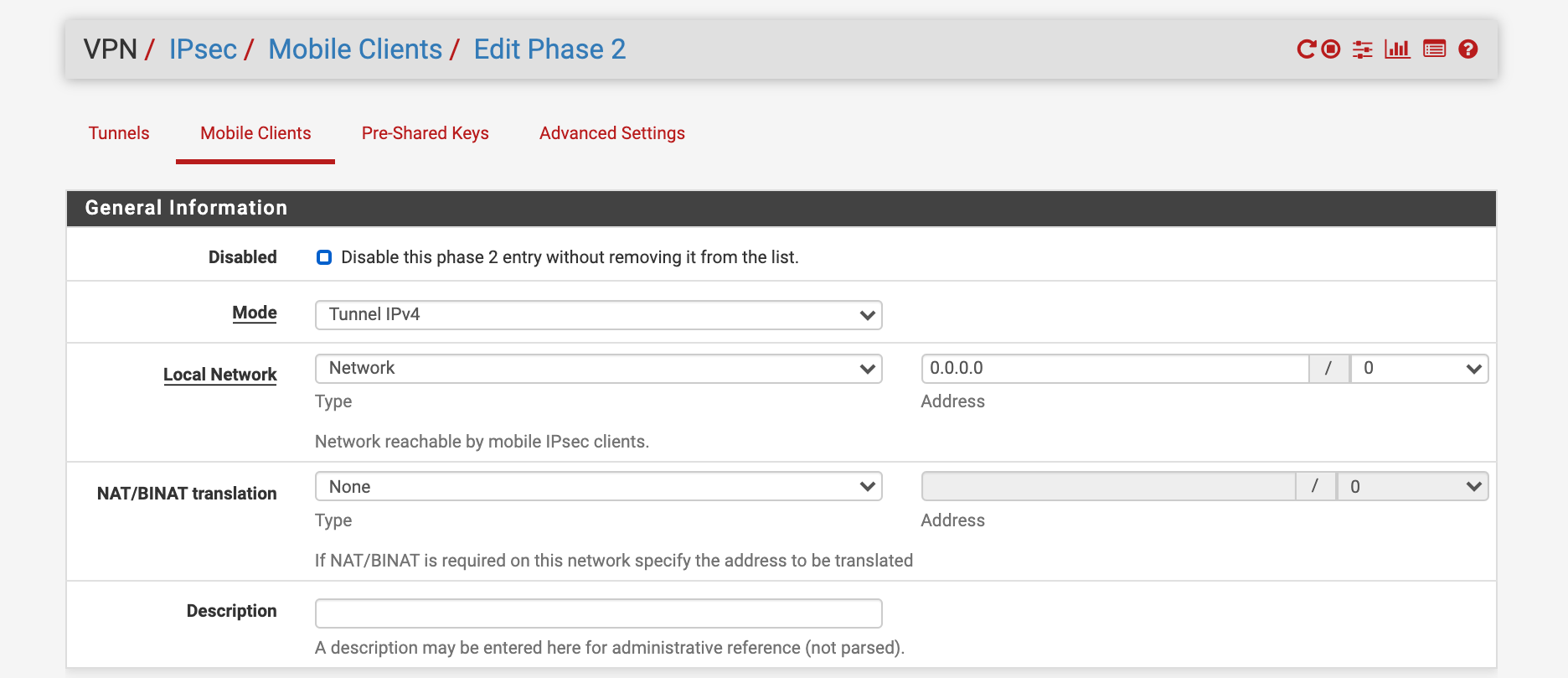
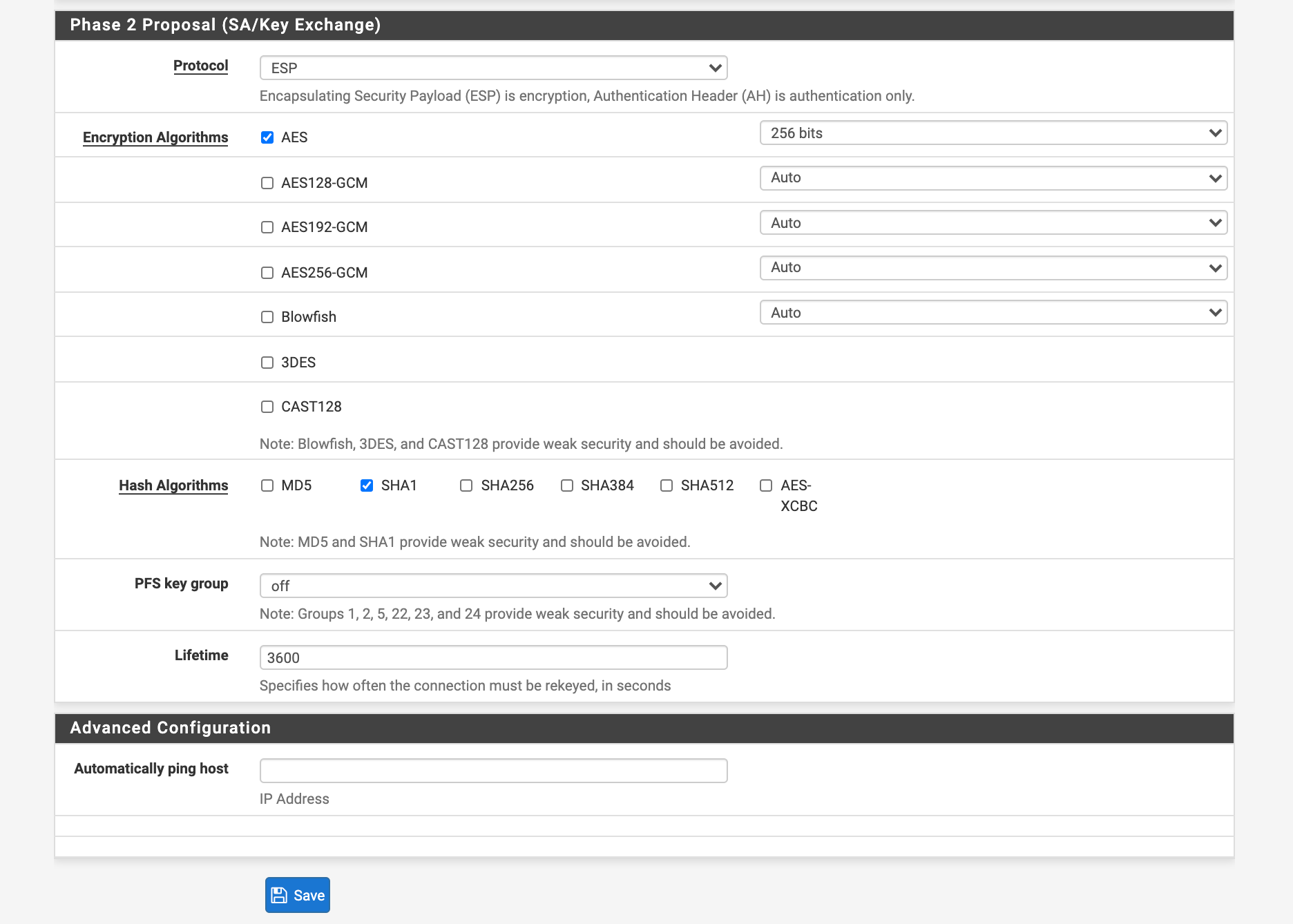
Phase 2
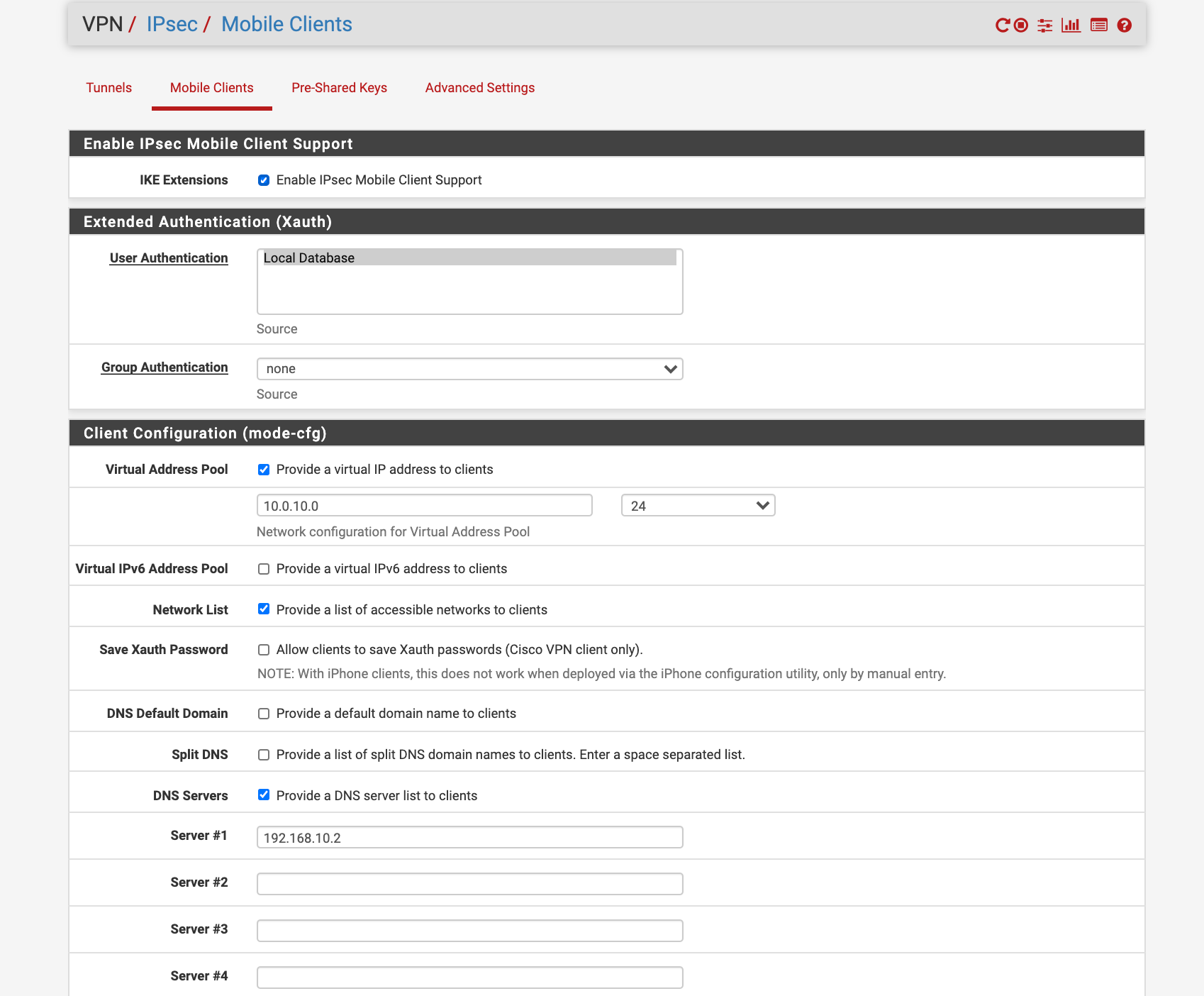
VPN / IPSEC / Mobile Clients:
Firewall:

With this config using StrongSwan Android app I receive the 'Authentication Failed'message (see the charn.log for StrongSwan android app).
Similarly, the MacOS built-in IPsec vpn client simply returns this:

Please let me know if you have any ideas, what do I do wrong and how could I fix it. Please feel free to ask for any other files I could provide in order to troubleshoot this.
-
Here are also logs from the firewall side:
Sep 28 11:48:42 pfSense charon: 14[NET] <73> received packet: from <IPSEC_CLIENT_IP>[29281] to <IPSEC_SERVER_IP>[500] (716 bytes) Sep 28 11:48:42 pfSense charon: 14[ENC] <73> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Sep 28 11:48:42 pfSense charon: 14[CFG] <73> looking for an IKEv2 config for <IPSEC_SERVER_IP>...<IPSEC_CLIENT_IP> Sep 28 11:48:42 pfSense charon: 14[CFG] <73> candidate: %any...%any, prio 24 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> candidate: <IPSEC_SERVER_IP>...%any, prio 1052 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> found matching ike config: <IPSEC_SERVER_IP>...%any with prio 1052 Sep 28 11:48:42 pfSense charon: 14[IKE] <73> <IPSEC_CLIENT_IP> is initiating an IKE_SA Sep 28 11:48:42 pfSense charon: 14[IKE] <73> IKE_SA (unnamed)[73] state change: CREATED => CONNECTING Sep 28 11:48:42 pfSense charon: 14[CFG] <73> selecting proposal: Sep 28 11:48:42 pfSense charon: 14[CFG] <73> no acceptable DIFFIE_HELLMAN_GROUP found Sep 28 11:48:42 pfSense charon: 14[CFG] <73> selecting proposal: Sep 28 11:48:42 pfSense charon: 14[CFG] <73> no acceptable ENCRYPTION_ALGORITHM found Sep 28 11:48:42 pfSense charon: 14[CFG] <73> received proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> looking for IKEv2 configs for <IPSEC_SERVER_IP>...<IPSEC_CLIENT_IP> Sep 28 11:48:42 pfSense charon: 14[CFG] <73> candidate: %any...%any, prio 24 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> candidate: <IPSEC_SERVER_IP>...%any, prio 1052 Sep 28 11:48:42 pfSense charon: 14[IKE] <73> no matching proposal found, trying alternative config Sep 28 11:48:42 pfSense charon: 14[CFG] <73> selecting proposal: Sep 28 11:48:42 pfSense charon: 14[CFG] <73> proposal matches Sep 28 11:48:42 pfSense charon: 14[CFG] <73> received proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256 Sep 28 11:48:42 pfSense charon: 14[CFG] <73> received supported signature hash algorithms: sha256 sha384 sha512 identity Sep 28 11:48:42 pfSense charon: 14[IKE] <73> remote host is behind NAT Sep 28 11:48:42 pfSense charon: 14[CFG] <73> sending supported signature hash algorithms: sha256 sha384 sha512 identity Sep 28 11:48:42 pfSense charon: 14[IKE] <73> sending cert request for "CN=<MY_ORG>-internal-ca, C=CA, ST=BC, L=Vancouver, O=<MY_ORG>, OU=DMZ" Sep 28 11:48:42 pfSense charon: 14[ENC] <73> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ] Sep 28 11:48:42 pfSense charon: 14[NET] <73> sending packet: from <IPSEC_SERVER_IP>[500] to <IPSEC_CLIENT_IP>[29281] (305 bytes) Sep 28 11:48:42 pfSense charon: 14[NET] <73> received packet: from <IPSEC_CLIENT_IP>[29923] to <IPSEC_SERVER_IP>[4500] (496 bytes) Sep 28 11:48:42 pfSense charon: 14[ENC] <73> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ IDr CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Sep 28 11:48:42 pfSense charon: 14[IKE] <73> received cert request for "CN=<MY_ORG>-internal-ca, C=CA, ST=BC, L=Vancouver, O=<MY_ORG>, OU=DMZ" Sep 28 11:48:42 pfSense charon: 14[CFG] <73> looking for peer configs matching <IPSEC_SERVER_IP>[<MY_ORG>.duckdns.org]...<IPSEC_CLIENT_IP>[ikev2-drew] Sep 28 11:48:42 pfSense charon: 14[CFG] <73> candidate "bypasslan", match: 1/1/24 (me/other/ike) Sep 28 11:48:42 pfSense charon: 14[CFG] <bypasslan|73> selected peer config 'bypasslan' Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> peer requested EAP, config unacceptable Sep 28 11:48:42 pfSense charon: 14[CFG] <bypasslan|73> no alternative config found Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> processing INTERNAL_IP4_ADDRESS attribute Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> processing INTERNAL_IP6_ADDRESS attribute Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> processing INTERNAL_IP4_DNS attribute Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> processing INTERNAL_IP6_DNS attribute Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> peer supports MOBIKE Sep 28 11:48:42 pfSense charon: 14[ENC] <bypasslan|73> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Sep 28 11:48:42 pfSense charon: 14[NET] <bypasslan|73> sending packet: from <IPSEC_SERVER_IP>[4500] to <IPSEC_CLIENT_IP>[29923] (80 bytes) Sep 28 11:48:42 pfSense charon: 14[IKE] <bypasslan|73> IKE_SA bypasslan[73] state change: CONNECTING => DESTROYINGI have found some kinda clues here that it may be an issue with mobile clients being behind the NAT. But again, I am using User distiguished name so it should not be an issue... probably..
and here it says that "If it selects bypasslan that typically means it did not match any other configured Phase 1. So the main thing to check is that the local and remote identifiers match and that the peers are connecting using the addresses expected by each end."
Can anyone please suggest me something about it.
-
-
@Konstanti Thank you very much for your help! Could you please show your pfsense Phase 2 Proposal. What exactly do you select for Encryption Algorithms and Hash algorithms?
-
-
Well, I finally made it work thanks to @Konstanti .
I want to leave it here in case it may help someone else, struggling with the finicky ipsec settings...
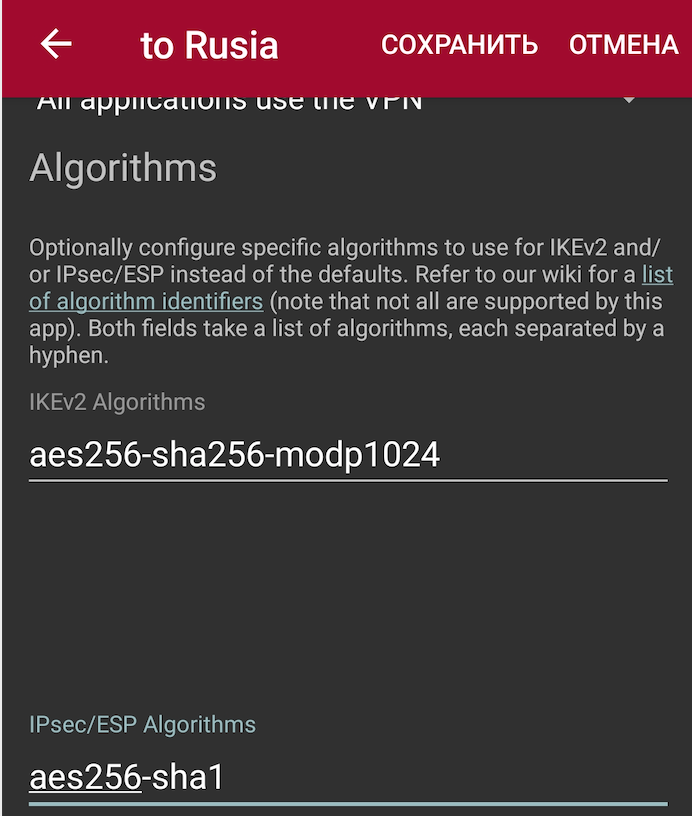
In my case the key point seems to be setting
IKEv2 Algorithmsasaes256-sha256-modp1024in the StrongSwan Android Client.The
IPsec/ESP Algorithmsmay be left empty. I am just not sure what the benefits of specifying it ( @Konstanti , please correct me).There is still another part that seems equally contibutes into the successful establishment of the IPSec tunnel - I also had to specify in StrongSwan Android Client:
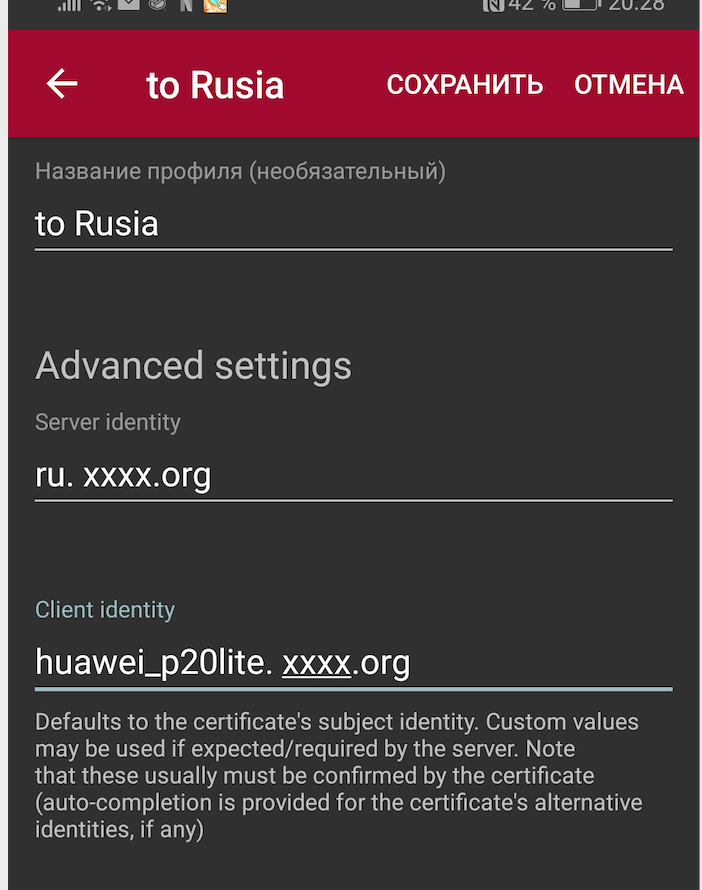
Server identity: <MY_ORG>.duckdns.orgClient identity: ikev2-drew@<MY_ORG>.duckdns.orgNote, that setting client identity (at least in my case) MUST be specified in this email style:
client1@<SERVER_IDENTITY>. For some reason, changing it to justclient1(ikev2-drewin my case) breaks everything, even though I canged theUser distinguished namefromikev2-drew@<MY_ORG>.duckdns.orgtoAnyin pfsense ipsec settings (phase1) in GUI.Again, thank you very much, @Konstanti for your time and help!