pfSense-on-a-Stick | Adding VLAN for VPN only
-
Hi everyone,
I am currently running a pfSense-on-a-stick into a Cisco switch with 3 VLANs configured:
VLAN 10: Wireless
VLAN 20: Servers
VLAN 30: IoTI would like to add VLAN 40 with one port for isolated virtual machine hosting. As of now, I have set up the new VLAN 40 in pfSense and on the switch and also set up DHCP on that interface. The machine is able to get an IP from the DHCP server, but cannot access any other VLAN, the LAN, or the internet. I have added a temporary allow all rule as shown in the screenshot, but that still does not help.
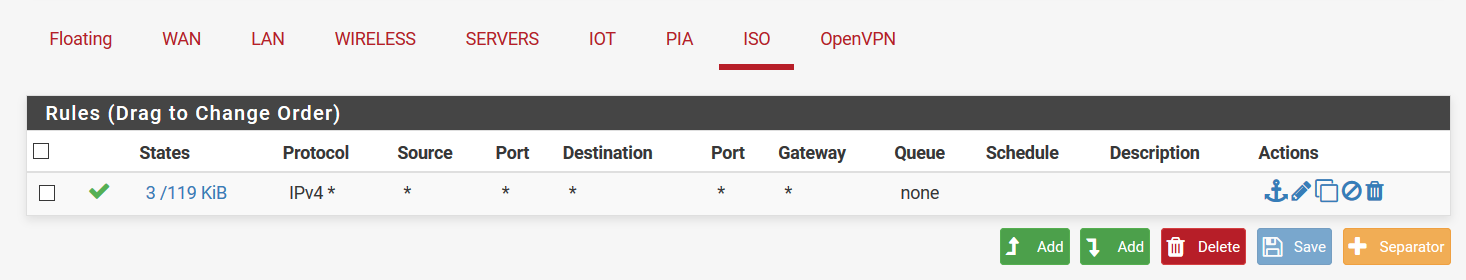
Eventually I would like the VLAN to only be accessible through a VPN server on the pfSense box. I set up the OpenVPN server to access the VLAN 40 network, but no traffic routing from VLAN 40 network as mentioned above.
Any help is appreciated.
-
Floating block rule?
Routing conflict?
Bad subnet mask?
Can the client in VLAN40 ping the pfSense interface in VLAN40? Can it ping any of the other pfSense interfaces? Can it resolve addresses against unbound in pfSense?
Steve
-
I'm going to try to change the addressing scheme that I used. Perhaps it is a routing conflict, but I am not sure. The client can ping the all pfSense interface from VLAN 40, but cannot ping beyond that. It stops at the router for some reason.
-
No go... Its super flaky. Sometimes I am able to ping to other VLANs, but now I have no communication with any device besides pfSense. No idea as to what is going on. The new addressing scheme is 192.168.40.0/24, but even that does the same thing.
-
Start a continuous ping from a client on VLAN 40.
Run packet captures on each interface to see where the pings are going and what's coming back.It's almost certainly a conflict of some sort with symptoms like that though.
Steve