Port forward through site-to-site VPN
-
Hi!
I'm trying to solve a problem on my setup, and kindly ask your help.
This is the scenario.
Site 1
- Internet connection via 4G/LTE provider, with natted connection
- pfSense firewall
- 172.20.0.0/25 LAN subnet
- NAS server (172.20.0.10)
Site 2
- Internet connection via fiber provider, with static and public IP address
- pfSense firewall downstream to providers router (172.16.0.2 WAN IP and 172.16.0.1 WAN gateway)
- 172.30.0.0/25 LAN subnet
IPsec VPN
I've an IPsec tunnel between the two sites, initiated always by Site 1 (because of the dynamic and natted IP).
The tunnel uses vti mode and a static route on both sides.
172.19.250.1 tunnel IP for Site 1
172.19.250.2 tunnel IP for Site 2With this setup I'm able access correctly resources on both sites from either sites, and also via OpenVPN connection (I connect from internet to Site 2, and I'm able to reach also Site 1).
Now I need to access directly a resource on Site 1 (a port of the NAS) from the internet, using the public IP of Site 2.
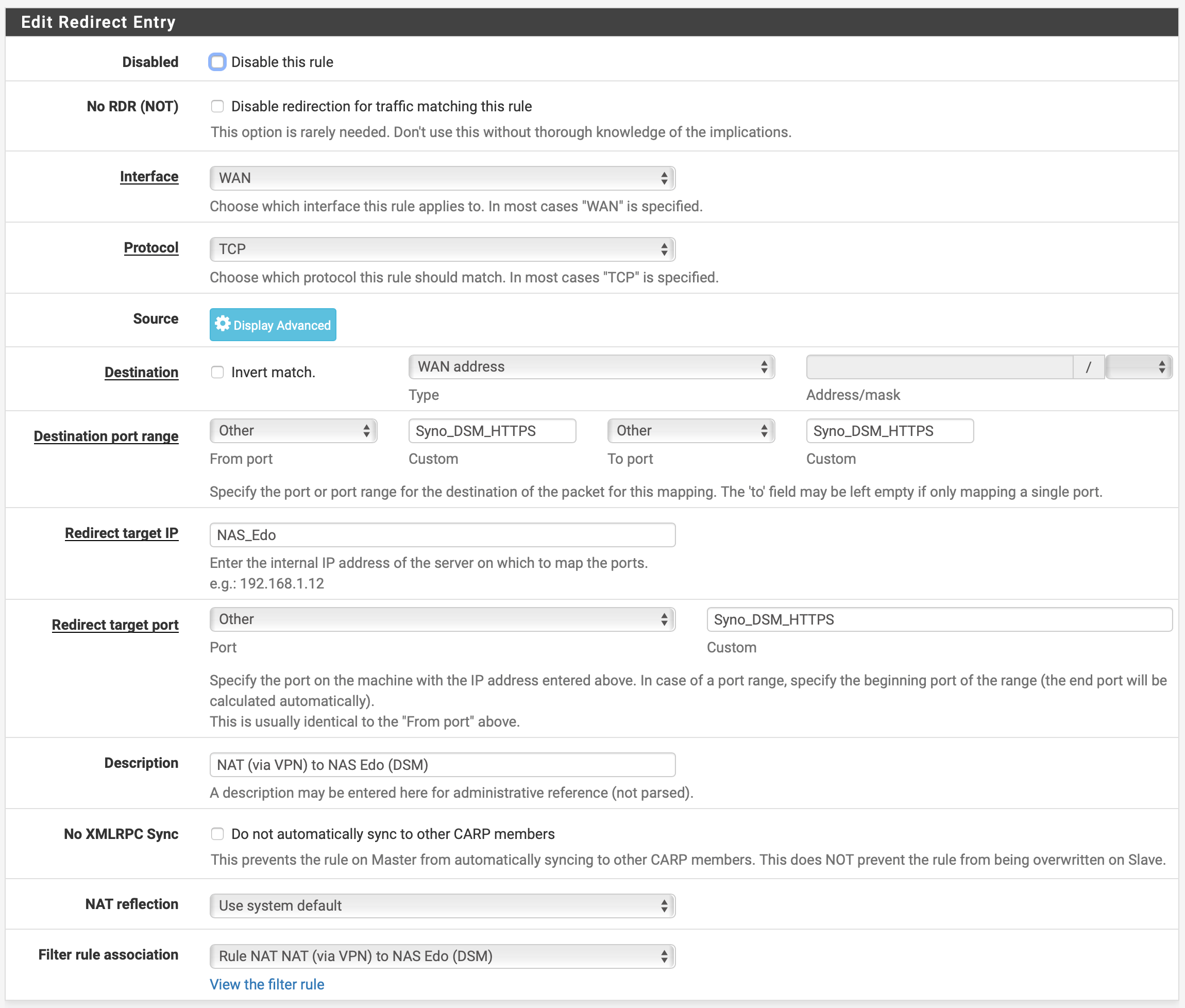
So, I've created a NAT rule on Site 2 to forward the needed port to the private IP of the NAS on Site 1.
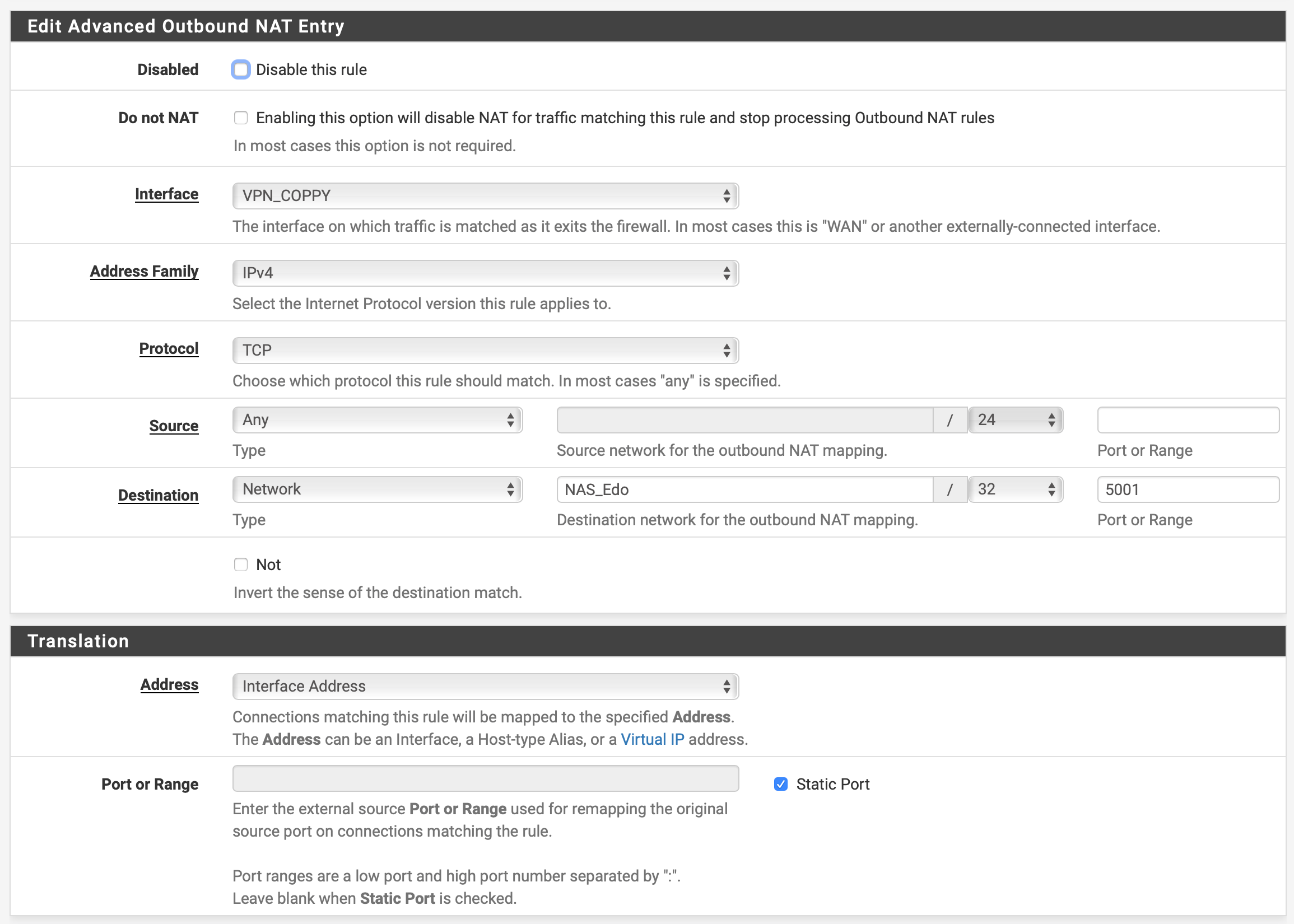
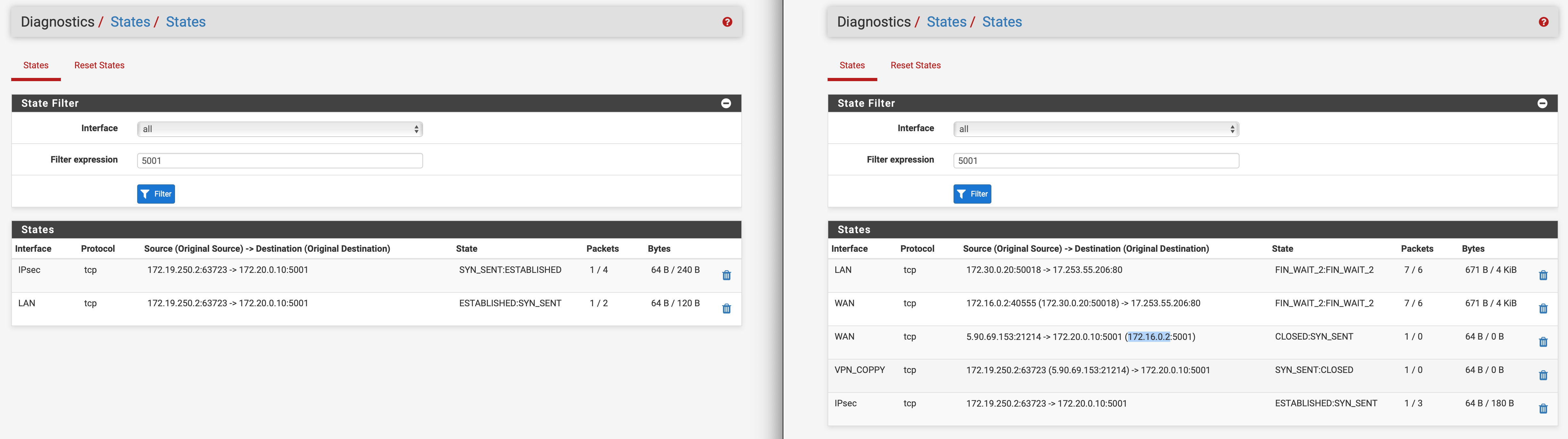
I've also created an Outbound NAT to masquerade the public IP of the source from the internet, to prevent that Site 1 replies directly via internet, instead from the VPN tunnel and Site 2 IP.The setup seems to work and the NAS in Site 1 receives the connection (from the right IP), but the response did not leave the firewall on Site 1.
No blocked connection are listed in the firewall logs, and this is the States view from both sides (Site 1 on left and Site 2 on right).
This is the port forward rule:
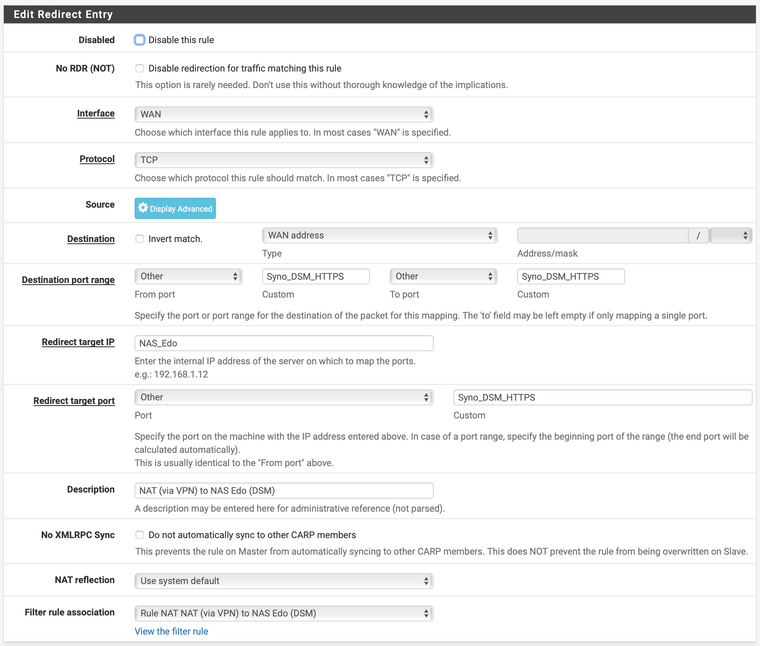
And this is the outbound NAT rule:
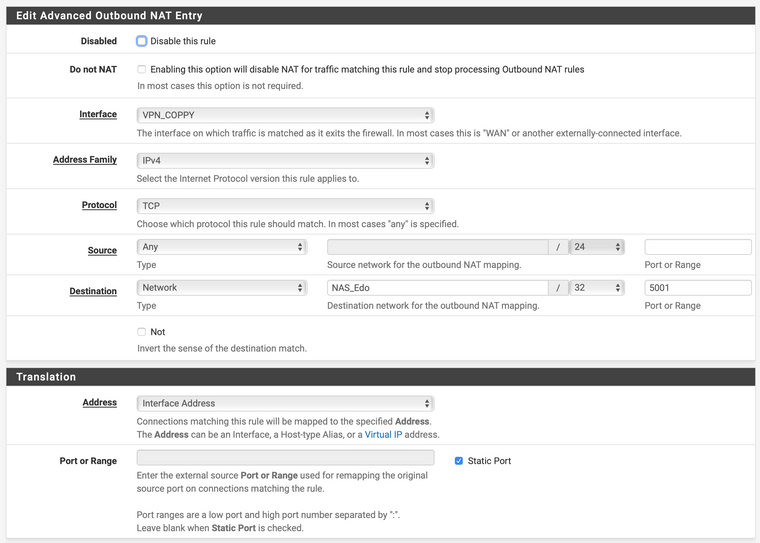
Do you have any suggestions?
I've missed something?Thanks in advance!
Edoardo
-
After many many tries, readings, etc....I've solved by switching to an OpenVPN Site-to-site tunnel

-
I have the same issue on my setup but in my case Site 2 does receive the return traffic, it just doesn't translate the destination IP of the return traffic back to the original source IP (the public IP) so the return traffic stops at the Site 2 IPsec interface. I switched from OpenVPN to IPsec because I needed the speed bump so OpenVPN is not a solution for me. Any workarounds to this?
-
@kevindd992002 I've switched to OpenVPN because it seems to be no solution other than routing all the traffic through the VPN tunnel :(
-
@edofede Exactly. They said this is a workaround: https://forum.netgate.com/post/935884 but it's also not working for me. It even further broke the tunnel in terms of routing from either end.
-
@edofede how did you solve this problem exactly?
-
@dennis-westhuis said in Port forward through site-to-site VPN:
@edofede how did you solve this problem exactly?
He solved it like how he said he did, by using OpenVPN. With OpenVPN, all these IPsec issues are non-existent. I should know because I came from using OpenVPN to trying out IPsec.