Private address not being blocked out bound
-
Hi,
I'm running PFSENSE with multiple WAN IP's and the NAT mode is set to Hybrid with several 1 to 1 nats. While most things seem to work just fine, what I have noticed is that private address space is not being dropped but passed on out into the internet. for example if I traceroute to 192.168.9.250 it hits the pfsense box and continues on out into the internet.
C:\WINDOWS\system32>tracert 192.168.9.1
Tracing route to 192.168.9.250 over a maximum of 30 hops
1 <1 ms <1 ms <1 ms gtwy-pfsense [10.10.10.1]
2 8 ms 8 ms 7 ms isprouter1.net [xxx.xxx.xxx.xxx]
3 8 ms 8 ms 8 ms isprouter2.net [xxx.xxx.xxx.xxx]
4 8 ms 9 ms 8 ms isprouter3.net [xxx.xxx.xxx.xxx]
5 * * * Request timed out.
6 * * * Request timed out.
7 * * * Request timed out.
8 * * * Request timed out.
9 * * * Request timed out.
Reply from xx.xxx.xxx.x: Destination net unreachable.
Reply from xx.xxx.xxx.x: Destination net unreachable.
Reply from xx.xxx.xxx.x: Destination net unreachable.This is true for all private address space.
This should not happen, or should be stoppable anyway. Does anyone have any suggestions ?
-
@dlewis_nepean
That“s the usual behavior of a router. If there is no matching network assigned to any of its interfaces it directs the packets to the default gateway.What“a the problem with that?
If you don’t want that you may block it. -
@viragomann said in Private address not being blocked out bound:
matching network assigned to any of its interfaces it directs the packets to the default gateway.
While I agree that routers are designed to do that in general, the wording in RFC for private address space also states that it should not be routed on inter-enterprise links.
Either way you are correct, I should be able to block them, but so far it doesn't seem to matter what rules I put into place they still flow. Would you have any suggestions ?
I created an alias of private networks and tried a floating rule on the wan/pppoe interface, I've tried moving it from floating to the actual interface.
I welcome suggestions.
Tks.
-
@dlewis_nepean said in Private address not being blocked out bound:
While I agree that routers are designed to do that in general, the wording in RFC for private address space also states that it should not be routed on inter-enterprise links.
It's not possible for pfSense to determine an internet gateway. Though it's not recommended, you can use non-RFC1918 adresses on internal devices. On the other hand may a WAN gateway have an private IP as well it it's behind another router.
The only one who knows is the ISP and usually RFC1918 is not routed in the internet. So the packets won't get far.So I cannot see any need to block it at all.
However, you should be able to block it by a floating rule. Select the WAN interface, check "Quick", direction any or out and enter the RFC1918 alias at destination.
That does not work? -
@viragomann said in Private address not being blocked out bound:
WAN gateway have an private IP
Just for reference I've seen ISPs that use RFC1918 addresses internally, for their routers (outside of the client's office). So a traceroute did actually show 10.x.x.x router addresses until the traffic left the ISP.
-
If you want to prevent rfc1918 from leaking out your wan... You can just put a outbound nat rule on your wan side interface(s)
-
@johnpoz said in Private address not being blocked out bound:
If you want to prevent rfc1918 from leaking out your wan... You can just put a outbound nat rule on your wan side interface(s)
You're probably talking about another issue.
Steve doesn't want, that packets destined to an RFC1918 address which has not route on pfSense is passed out to WAN.
Outbound NAT only tranlates the source IP, but the packets will still go out to the default gateway. -
Typo, brain fart ;) I meant to say outbound block rule in the floating tab... Not nat no..
Like this
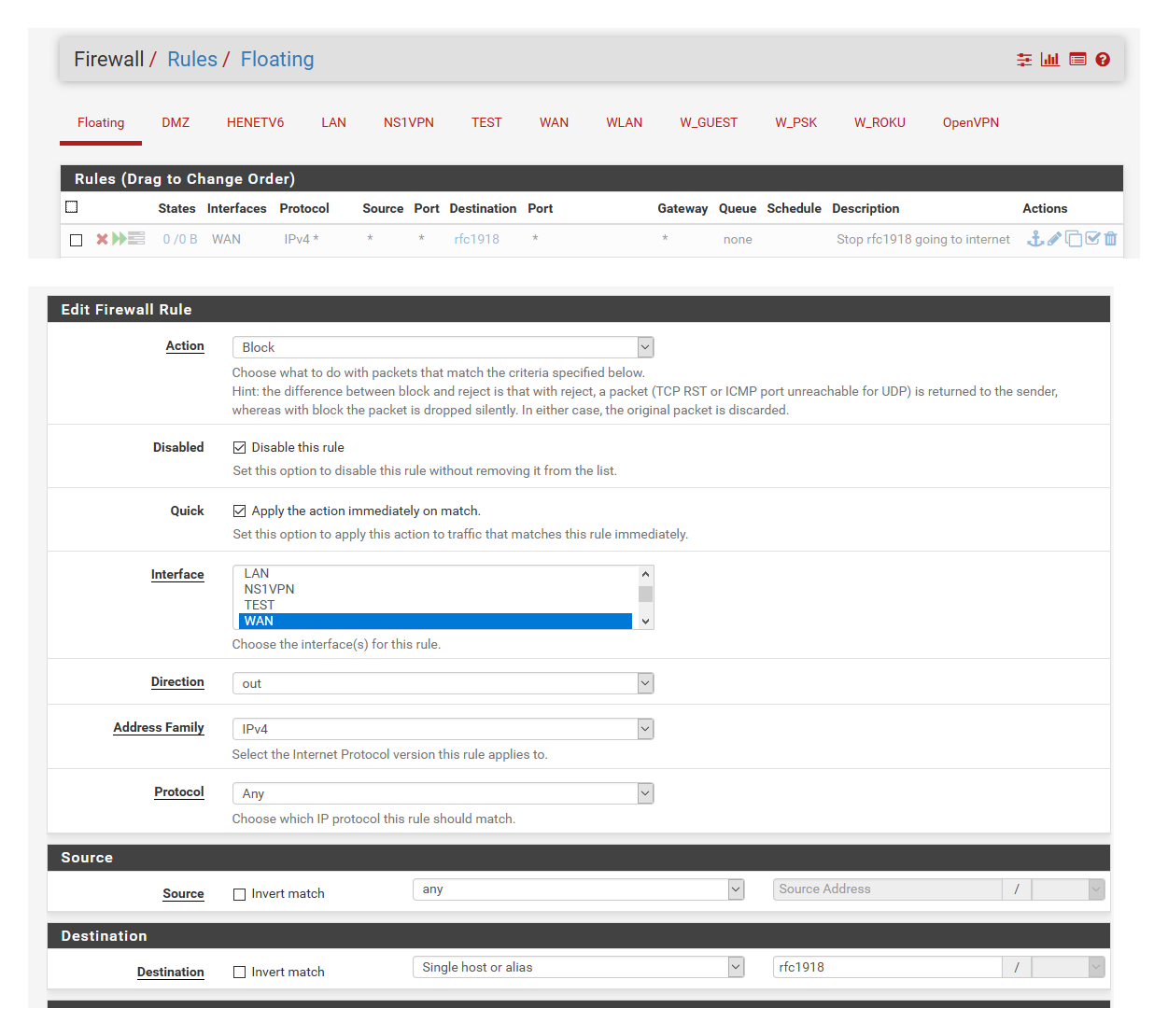
I have it disabled currently, was playing with my modem which uses a 192.168.100.1 address...
But yeah what the OP is seeing is normal - if router doesn't know where said network is, just send it to default that is how they work.. So if you don't want unknown rfc1918 to get sent do your default you either have to block it or blackhole or null route it.
-
I believe I have the firewall rule working now. Not sure why it wasn't accepting it previously but it seems to be ok now.
I guess I just found it odd that there is mention of blocking incoming but nothing for outgoing, when I would expect that it is pretty normal to not want private addresses to leave the private lan.
I appreciate everyone's replies and comments, and thanks for the help!
Tks,
-
@dlewis_nepean Private addresses on the LAN would never leave the LAN because they wouldn't be routed externally....A PC wouldn't forward those packets to the router. We're talking about private IPs that aren't in your LAN subnet, in which case the PC doesn't know what to do so sends them to the router, and the router forwards them along. You could make an argument the ISP should drop them...
-
^ exactly... Even if you put in the wrong address and does get routed to your isp.. it wouldn't go anywhere.
Sure your isp might use rfc1918 internally themselves - but if they route said traffic from their customers to their devices - they really shouldn't be in the ISP business if you ask me.. Or they need to fire their networking guys and security people..
From a security standpoint its not an issues from your point of view.. And if rfc1918 was blocked outbound out of the box, it would be very confusing for many new users that put pfsense behind their existing network and wouldn't figure out why they couldn't talk to some box they have sitting behind their isp router and in front of pfsense. Especially their isp router so pfsense could actually get to the internet.
So now you need some logic that would figure ok let pfsense talk outbound to its wan, but not to any other rfc1918 address, etc.. It just not really something that makes any difference from a security point of view. Worse case a few packets of noise leak out to the isp network.
There are many posts here were such users can not figure out why it doesn't work when they have 192.168.1 in front of pfsense and 192.168.1 behind pfsense..
The default rules on the wan block rfc1918 inbound, so even any noise from ISP did happen to hit pfsense wan it would be dropped, even if you had port forwards setup to allow the actual internet in, etc.
But if you are concerned - it takes only a few minutes to put in a rule to block whatever it is you want from leaving your network. To be honest the only rule I have rule I showed at all was some other post here or maybe on reddit where someone asking the same sort of question.
-
https://docs.netgate.com/pfsense/en/latest/recipes/rfc1918-egress.html