Setup DNS over TLS on pfSense 2.4.5
-
Hi,
The previous topic was locked because I suppose it is a guide or old topic ! So I post again here
I obviously followed the official guides to redirect DNS queries over TLS and it works fine
However, I wanted to go further and implement the redirect external client requests or block external client requests.My internal servers do properly use pfsense as a DNS server. I wanted to block clients that could have a custom DNS server setup (Firefox, chrome, windows 10 or Android custom settings) when they are connected to the LAN and force them to use DNS setup in pfsense
I started by the guide to port forwarding DNS traffic:
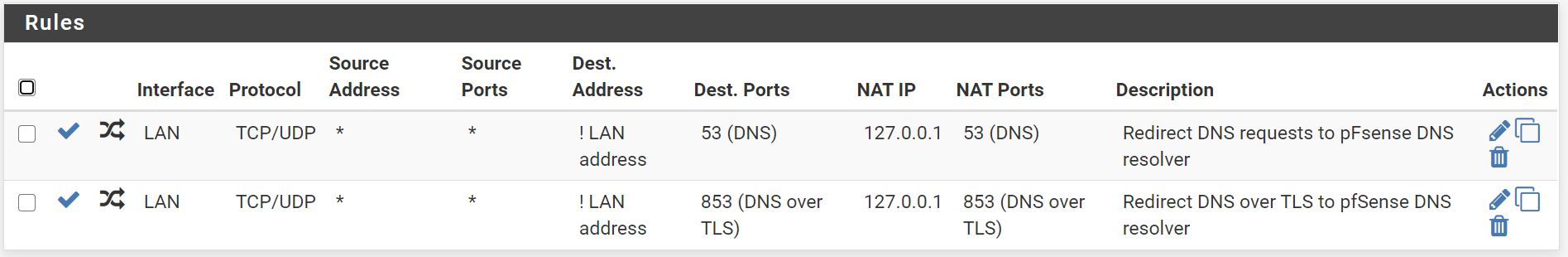
Creating the port forward rules, automatically created the allow rules in firewall in image below.
I also added the block rules (I guess now that they are not useful too) by following the official guide https://docs.netgate.com/pfsense/en/latest/recipes/dns-block-external.html
I also edited the Custom options in the DNS resolver to target the most common DOH servers, while I guess that it is far from perfect, it is ok for me to start with:
# Block DNS over HTTPS (DOH) client requests so that they are redirected to pfSense server: local-zone: "use-application-dns.net" always_nxdomain local-zone: "cloudflare-dns.com" always_nxdomain local-zone: "dns.google" always_nxdomain local-zone: "dns.quad9.net" always_nxdomain local-zone: "dns9.quad9.net" always_nxdomain local-zone: "dns10.quad9.net" always_nxdomain local-zone: "dns.adguard.com" always_nxdomain local-zone: "dns-family.adguard.com" always_nxdomainFrom the answer of @johnpoz here https://forum.netgate.com/topic/139771/setup-dns-over-tls-on-pfsense-2-4-4-p2-guide/66 I now understand that the rules in the firewall are not needed in my setup at all
When I tested by manually setting a fixed DNS in windows 10 network settings and a DOH DNS server in Firefox, my settings seem to work and all DNS traffic was properly redirected to the DNS servers setup in pfSense (DHCP specific to client or the General settings DNS depending on clients and DHCP server setup)
What are the issues to redirecting the DNS:53 and DOT queries with such a setup ? I did not get the issues I could have with certificates and if, based on my use case, I could face. I have a FreeBSD server setup with an apache server with Host Overrides setup in pfSense and that works properly. For my local domains, I use a private CA but not in pfSense, just on the windows machines and the FreeBSD server
Thank you for your help and best regards
-
@elodie80 said in Setup DNS over TLS on pfSense 2.4.5:
my settings seem to work and all DNS traffic was properly redirected to the DNS servers setup in pfSense
Yeah if doh or dot fail, it is suppose to failover to use normal dns - which then your redirect would work.. There is little reason to try and redirect dot or doh.. Unless whatever just insists on using them, and will not fallback to using normal dns.
While you might be able to trick something into using a specific doh/dot that it thinks is doh.domain.tld into using your local NS, but creating a cert for doh.domain.tld with your CA, and that device trusting your CA.
How would you get your NS to serve up doh and or dot with cert that device trusts for any fqdn that might be used?
-
I understand better now, I really did not think at it that way.
If the external client insists on being served by the DNS server it is asking for, it will reject the DNS query returned by pfsense configured DNS server since it is coming from another server, breaking TLS.Well, in my case it is ok as I just don't want some clients to bypass the OpenDNS filter that is assigned to them by the DHCP server. If they are misconfigured, they will fail, that is ok for me. I also do not need a huge complexity to block all possibilities for them in the firewall, that part is ok in my case.
By the way, in pfSense, when a client is assigned a static IP AND a specific DNS server through the DHCP server: if the client is setup to use a different DNS (windows 10, Firefox...), than the DNS address assigned by the DHCP server would be bypassed. I guess that is not a bug as the DHCP server is not supposed to be a firewall, right ? Sorry, but I am new to pfSense and only using it since a few months, but just loving it.
Edit: and a last one:
When port forwarding is activated, why does pfSense create those 2 allow rules ? Firewall rules are processed before the port forwarding maybe ? If it is the case, should I move the 4 bottom rules to the top, before the default pfSense allow rules for all the LAN ?
Note that I am using a fully managed switch that does the filtering using ACL rules before the router and that some devices are isolated at that level before hitting the router.Let's suppose I have custom rules for the LAN instead of the two bottom ones in my below picture.
Are the 4 DNS rules needed with the port forwarding ?
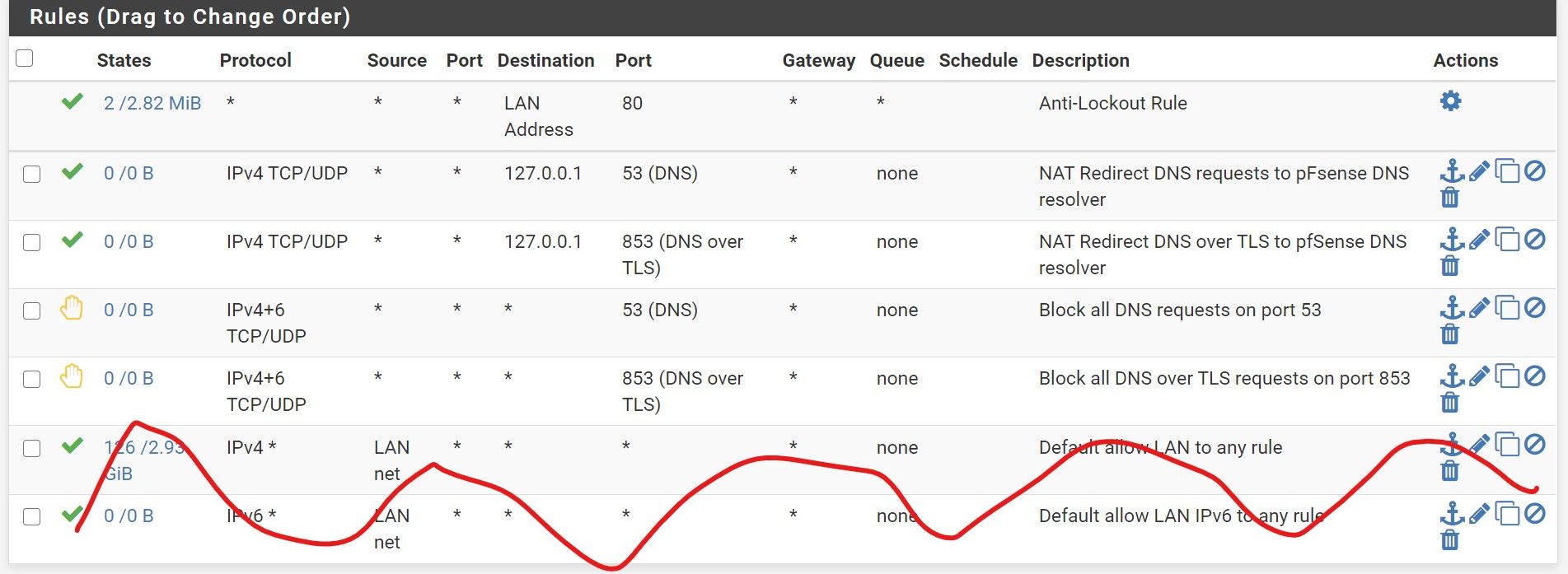
Thank you and best regards
-
Ok, I really need help
When I moved the rules like above, keeping the allow all rules at the end, all my DNS traffic is blocked and I have no more internet access
So, it seems like the DNS resolver is not working !Here's the setup in the DNS resolver:
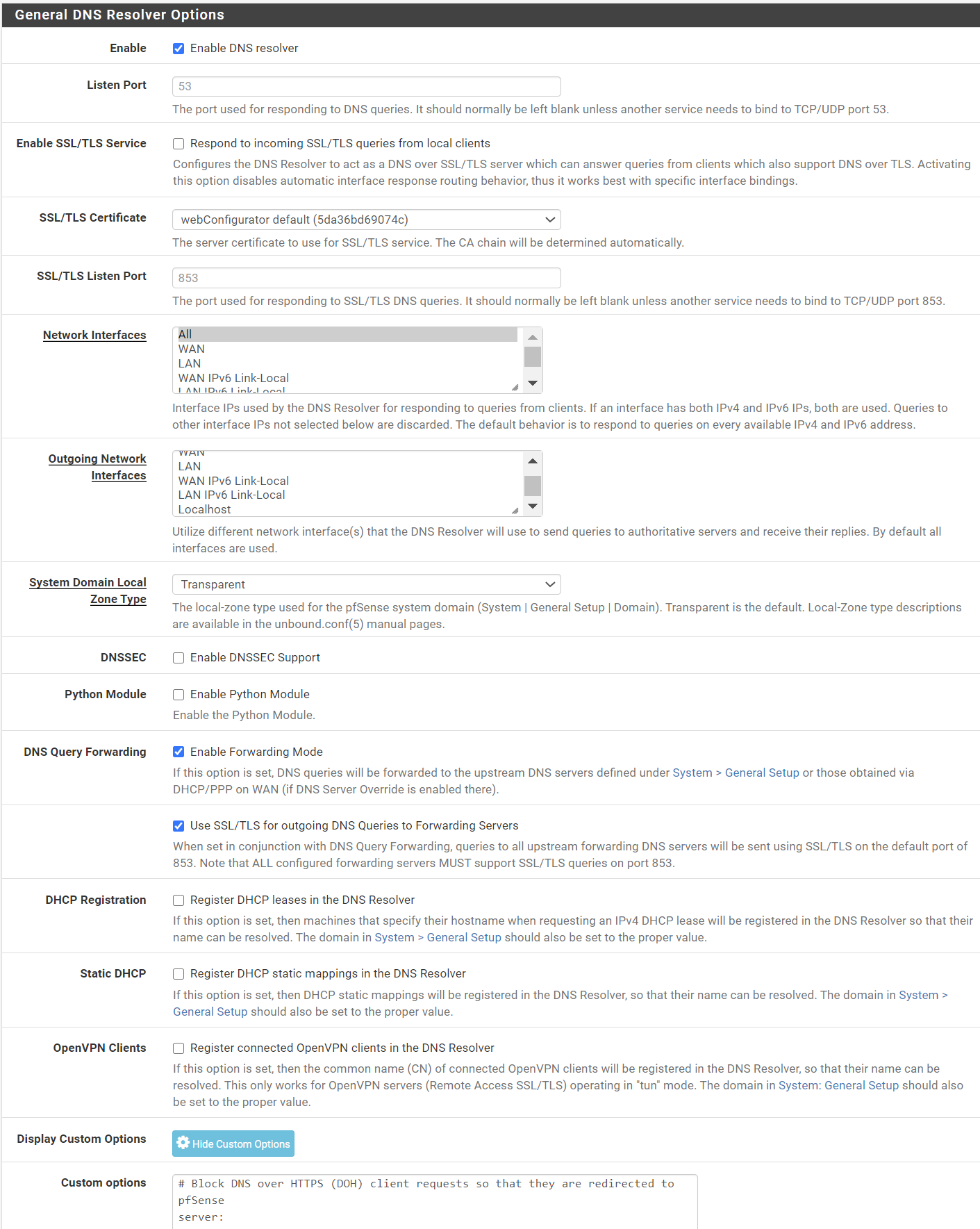
DNS in General tab are the google ones and the DNS override is unchecked there:
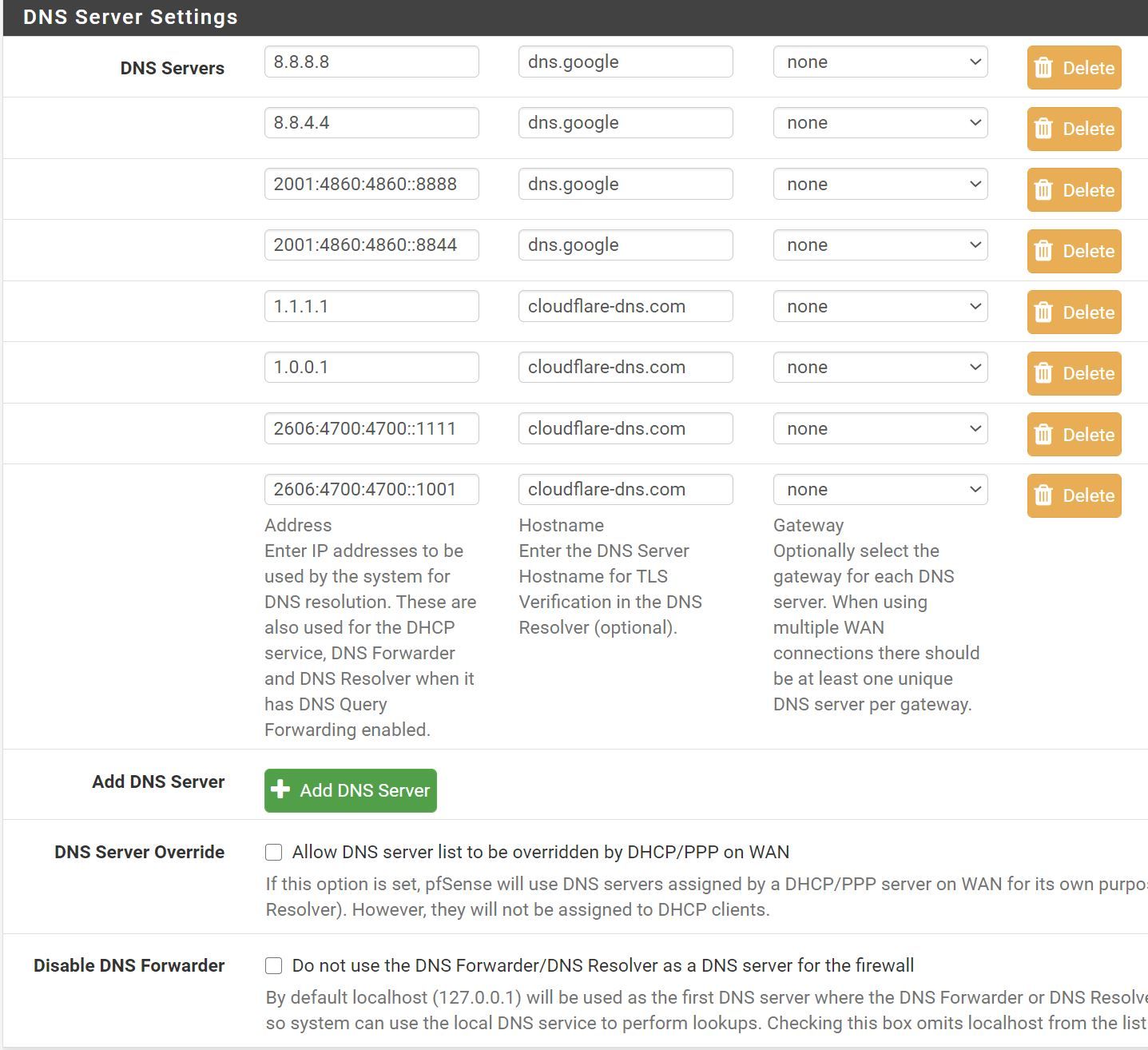
Firewall states:
WAN tcp xxxxxxx:60087 -> 8.8.4.4:853 FIN_WAIT_2:FIN_WAIT_2 13 / 10 1 KiB / 4 KiB WAN tcp xxxxxxx:46355 -> 8.8.8.8:853 FIN_WAIT_2:FIN_WAIT_2 13 / 10 1 KiB / 5 KiBThis is without a custom DNS setup in the client, just quering pfSense as a DHCP server with above rules in firewall
Why the allow rule for 127.0.0.1 is not working ? -
A final debug post: any help with the firewall rules please:
They are just for debugging, I understand some rules are not useful:
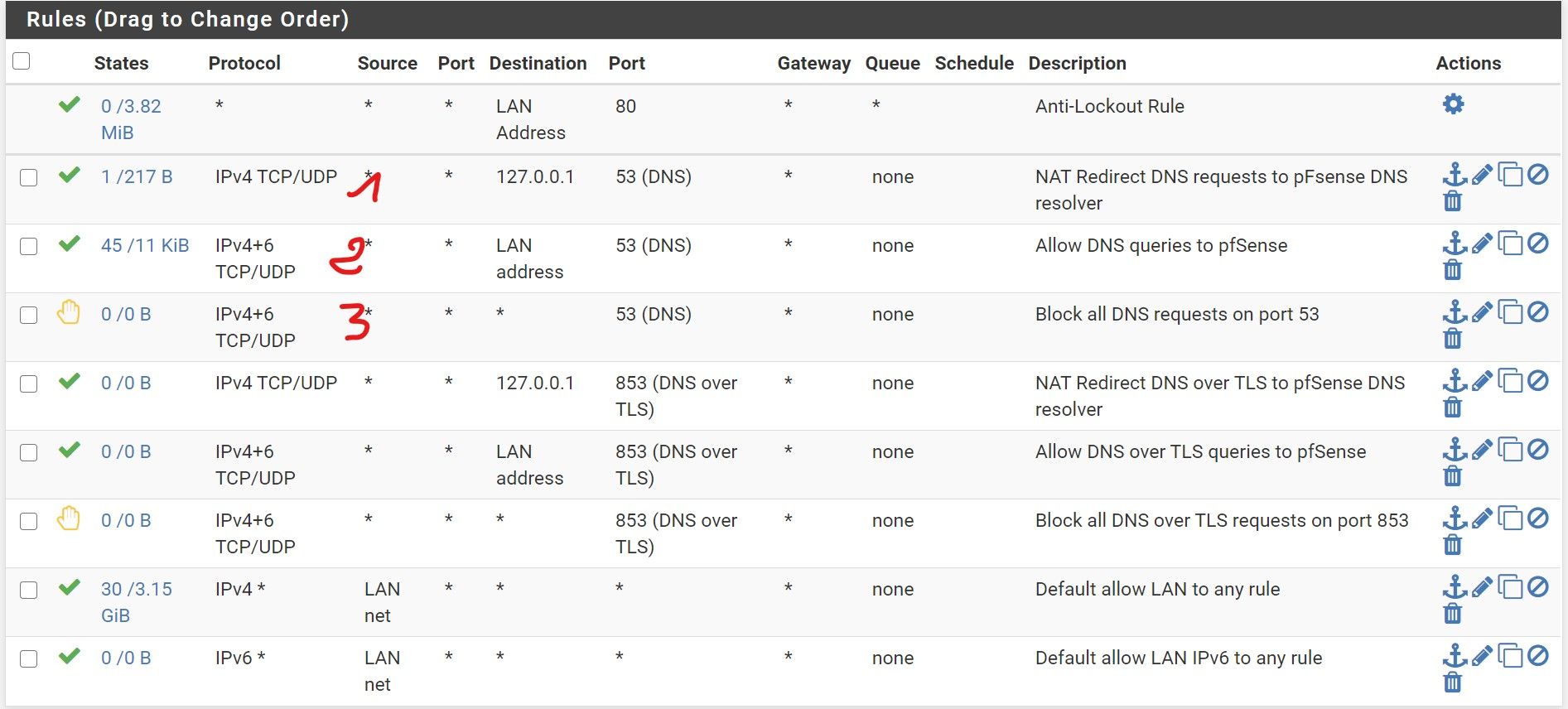
- rule 1 in red: doesn't work, doesn't seem to be used, DNS queries fail. It was created by the port forward rule
- rule 2: without it, all DNS queries fail. If I restrict rule 2 to LAN address as source, DNS queries fail also. That part is the most wired. Why DNS fails if I restrict source to the LAN ?
And why the redirect to 127.0.0.1 is not working ?
thank you
-
What do you have in your custom you have it cut off.
If what you want to do is forward traffic that hits pfsense on 53. to pfsense (unbound).. then have unbound use dot..
You have not shown your port forwards.. you can not redirect without port forwards.
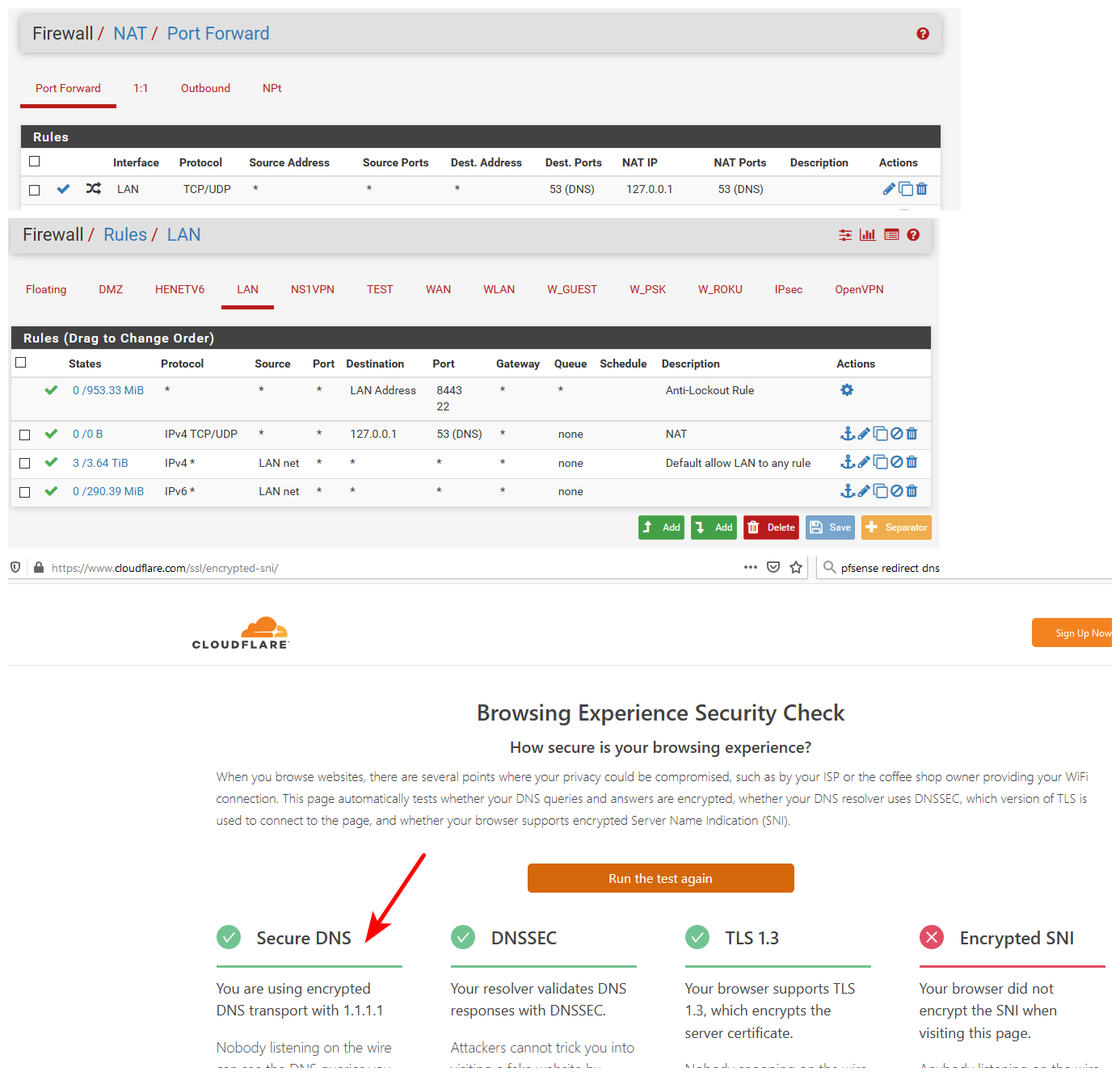
edit: here this took all of 30 seconds to setup.
Set 1.1.1.1 in general, setup unbound to forward and use tls. Created my port forward. my pc using pfsense for dns..
Tested that using encrypted dns to cloudflare..
-
Unbound custom options:
# Block DNS over HTTPS (DOH) client requests so that they are redirected to pfSense server: local-zone: "use-application-dns.net" always_nxdomain local-zone: "cloudflare-dns.com" always_nxdomain local-zone: "dns.google" always_nxdomain local-zone: "dns.quad9.net" always_nxdomain local-zone: "dns9.quad9.net" always_nxdomain local-zone: "dns10.quad9.net" always_nxdomain local-zone: "dns.adguard.com" always_nxdomain local-zone: "dns-family.adguard.com" always_nxdomainNot used in my case, only for Firefox or eventual third party clients
Port forward:
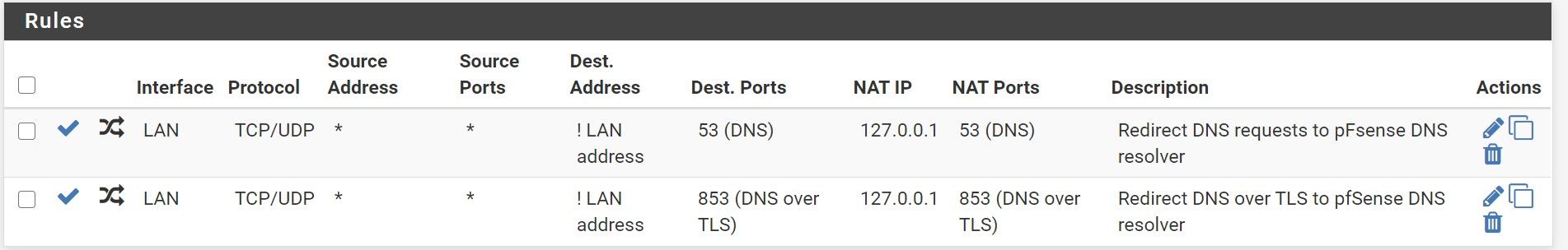
Firewall (same pic as in previous post):

I have it working, I just don't understand what's happening and that's my issue:
- mobile devices (Android): Firewall states shows DNS query from Local IP -> 127.0.0.1:53
- Windows machines (2): Firewall states show query from Local IP -> PfSense Local IP:53
- redirects to DNS:853 appear in the form of WAN IP -> DNS IP:853
-> So, rule 1 (red) created by port forward: not used by windows machine
-> rule 2 (red) must allow all interfaces include WAN for port 853 and maybe ? only Pfsense local IP for :53
Now, rule 3 (red) won't block DNS traffic calls (I added it to ensure my above rules are fine and understand how they work)Why the 127.0.0.1 is not enough always ? and why the firewall needs to allow all WAN and not only its self to query the DNS:853. I did not think that even the DNS resolver is subject to firewall rules
edit: maybe I am understanding: Android devices are trying a direct DNS call which is being redirected by pfSense. The windows machines have the router set as a DNS server
-
@elodie80 said in Setup DNS over TLS on pfSense 2.4.5:
Why the 127.0.0.1 is not enough always ?
127.0.0.1 is never going to be a destination that would be tried by lan to get to.. Its a rule that allows your redirect to work. That is all, if you have some other rule that allows it, like an any rule its not even needed.
What is the point of allowing clients to talk to pfsense on 853.. Are you wanting your clients to use dot to talk to unbound? WHY???
Again your redirection to 853 to unbound is NEVER GOING TO WORK!!! Never!! TLS has to use a cert, the cert fqdn has to match... Did you setup a cert that is valid for dns.google for example - that your clients browser is going to trust?
If your goal is to have clients use unbound, and for unbound to use tls to forward to X.. Just block anything trying to use doh or dot.. So they have to fall back to using local dns.. Because your never going to get a redirect on those to work.
-
Ok, thank you again
So I should just remove the 853 redirect port forwarding rules and add a rule to simply block all 853 from any to any like below ?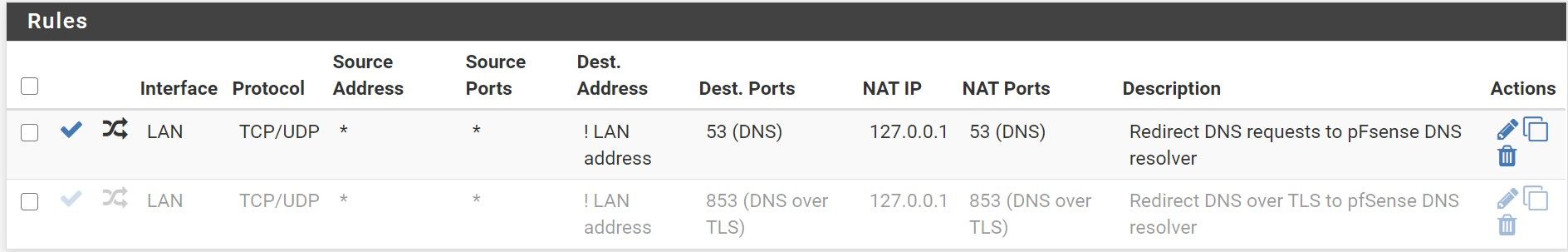
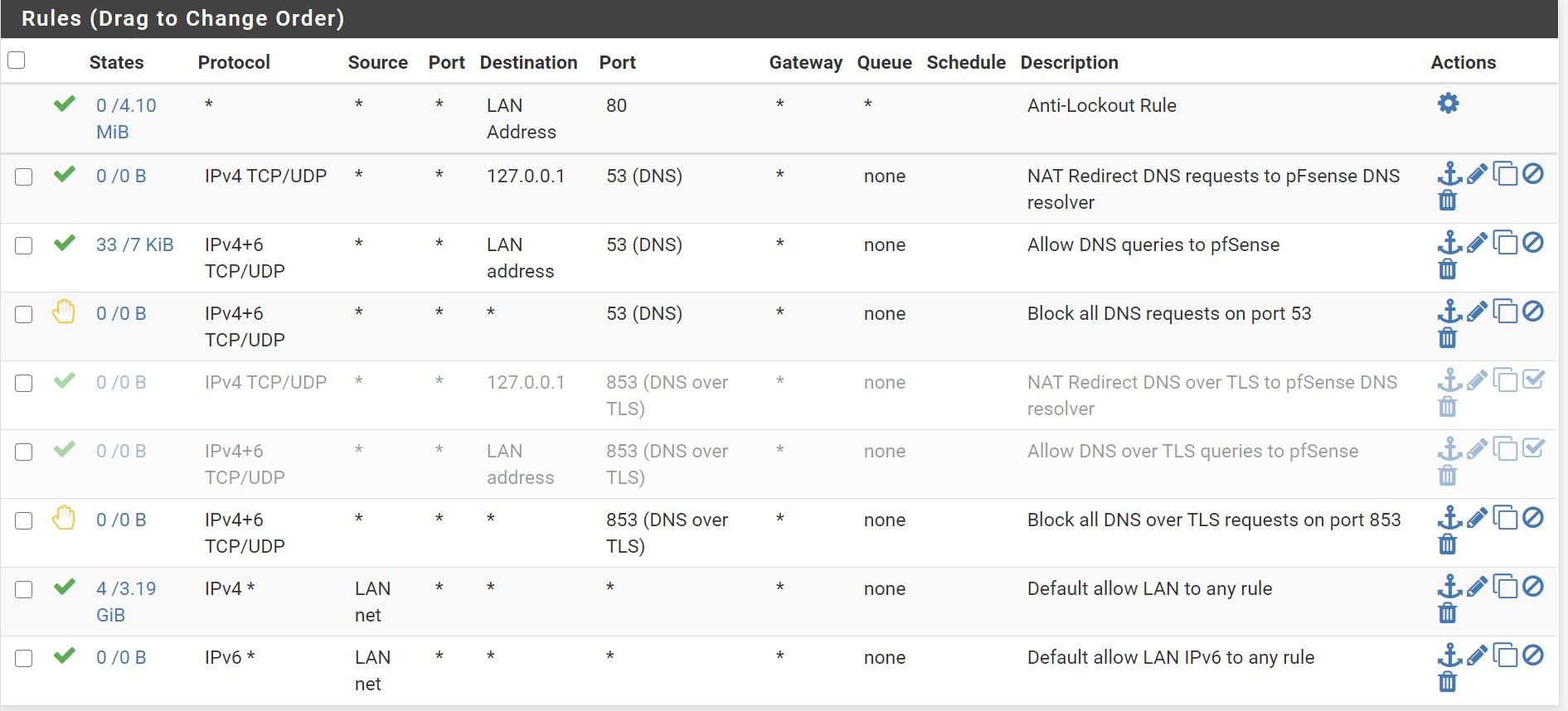
This setup in fact works, you are right :-)
Are there still things I should fix in the rules ?
Really thank you for the support as it is not so evident when someone doesn't have a lot of knowledge in the DNS thingsBy the way, from time to time, I get this state:
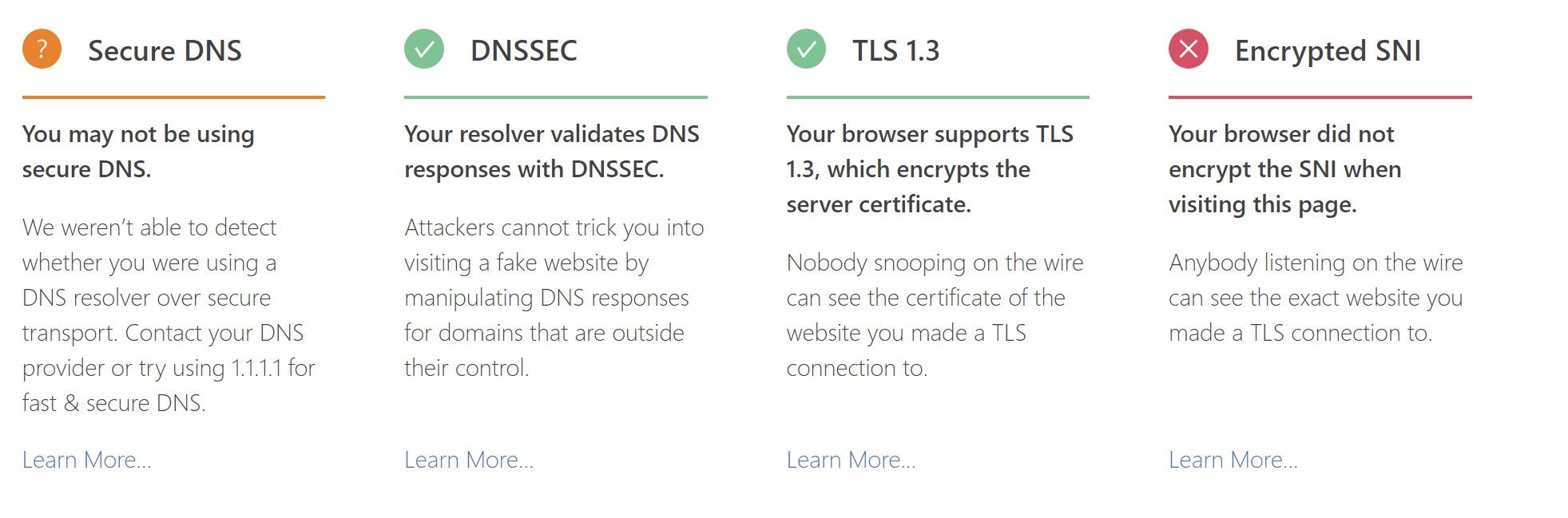
Is it because of the google DNS ? pfSense states show only DNS server IP:853 entries, and all DNS:53 are from Local -> PfSense IP:53
So that's normal ? -
I can confirm that using only google DNS makes that TLS assumption unknown despite it is properly using TLS over port 853
-
A last feedback please on the rules I setup if they seem better ?
Thank you -
That can only know your using dns over tls, if you directly ask them... So yes using multiple NS could account for why it doesn't show you secure some times.
Yeah those rules look sane.
-
thank you a lot again
-
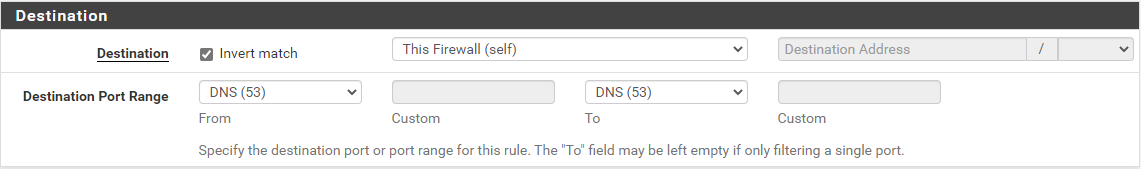
Just a note that you could simplify your 2 and 3 rules down to a single rule, if you wanted... use the Invert Match checkbox for the destination so pfSense will block all port 53 requests that are NOT to "LAN Address".
My example here is a floating rule, so it's using "This Firewall" to cover all interfaces it applies to, but works just as well.
-
While I agree that ! rules can help trim a rule list down to less actual rules. I would just make sure that rules are working as you expect them to, and fully validate it functions as you desire.
There are some weird little things that can happen with ! rules and especially if you have vips, etc.
So unless your fully familiar with how bang rules operate, and how to validate they are working as expected. Its normally cleaner and easier to tell from a glance of the rules what exactly will or will not pass by using explicit rules.. Allow this, Block that.. etc.
-
I better understand with this example the use of "invert match"
In my case, I just followed the doc guide to create the redirect rule.
I do prefer explicit rules since I am not used at all to the firewall modificationsThank you