Cannot ping pfSense from specific LAN host
-
My pfSense has Static IPv4 Configuration 192.168.0.1 with /24.
I have problems pinging it from specific LAN host 192.168.0.2
Packet capture confirms that pfSense receives ICMP echo requests but never sends echo replies back only to that IP - see below.
I could not reproduce such an issue from any other address on LAN.
I reviewed all possible settings and rules and could not find anything suspicious.
Any idea what can be wrong here?LAN Packet capture (ICMP only):
14:33:58.336847 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 230, length 64 14:33:58.827006 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33720, length 40 14:33:58.827028 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33720, length 40 14:33:58.829050 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33721, length 40 14:33:58.829063 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33721, length 40 14:33:58.831391 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33722, length 40 14:33:58.831404 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33722, length 40 14:33:58.834754 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33723, length 40 14:33:58.834767 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33723, length 40 14:33:58.836737 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33724, length 40 14:33:58.836750 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33724, length 40 14:33:59.338807 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 231, length 64 14:34:00.343811 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 232, length 64 14:34:01.012868 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.012919 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.019895 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.019909 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.021324 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.021337 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.022694 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.022708 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.024114 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.024127 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.026282 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.026296 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.027828 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.027841 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.029420 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.029433 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.030901 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.030914 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.032300 IP 192.168.0.58 > 192.168.0.1: ICMP echo request, id 575, seq 4833, length 64 14:34:01.032315 IP 192.168.0.1 > 192.168.0.58: ICMP echo reply, id 575, seq 4833, length 64 14:34:01.340041 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 233, length 64 14:34:02.342652 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 234, length 64 14:34:03.353589 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 235, length 64 14:34:04.358648 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 236, length 64 14:34:05.358840 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 237, length 64 14:34:06.354584 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 238, length 64 14:34:07.356502 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 239, length 64 14:34:08.331518 IP 192.168.0.116 > 54.186.148.131: ICMP echo request, id 44035, seq 59287, length 64 14:34:08.367303 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 240, length 64 14:34:08.375565 IP 54.186.148.131 > 192.168.0.116: ICMP echo reply, id 44035, seq 59287, length 64 14:34:09.369418 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 241, length 64 14:34:10.364026 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 242, length 64 14:34:11.364515 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 243, length 64 14:34:12.365247 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 244, length 64 14:34:12.672683 IP 192.168.0.116 > 34.222.218.144: ICMP echo request, id 6093, seq 6094, length 64 14:34:12.716892 IP 34.222.218.144 > 192.168.0.116: ICMP echo reply, id 6093, seq 6094, length 64 14:34:13.337325 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33725, length 40 14:34:13.337405 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33725, length 40 14:34:13.340313 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33726, length 40 14:34:13.340351 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33726, length 40 14:34:13.343151 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33727, length 40 14:34:13.343185 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33727, length 40 14:34:13.345398 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33728, length 40 14:34:13.345429 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33728, length 40 14:34:13.349648 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33729, length 40 14:34:13.349681 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33729, length 40 14:34:13.373406 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 245, length 64 14:34:14.377262 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 246, length 64 14:34:14.591258 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.591333 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.622597 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.622637 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.626600 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.626640 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.628543 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.628580 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.629805 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.629836 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.636247 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.636264 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.639397 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.639432 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.640885 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.640911 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.644563 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.644596 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:14.647289 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 58067, length 64 14:34:14.647330 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 58067, length 64 14:34:15.378139 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 247, length 64 14:34:16.375401 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 248, length 64 14:34:17.376440 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 249, length 64 14:34:18.377175 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 250, length 64 14:34:19.380159 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 251, length 64 14:34:20.382733 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 252, length 64 14:34:21.386503 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 253, length 64 14:34:22.396763 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 254, length 64 14:34:23.391258 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 255, length 64 14:34:24.399512 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 256, length 64 14:34:25.400894 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 257, length 64 14:34:26.334513 IP 192.168.0.27 > 192.168.0.1: ICMP echo request, id 0, seq 0, length 64 14:34:26.334558 IP 192.168.0.1 > 192.168.0.27: ICMP echo reply, id 0, seq 0, length 64 14:34:26.396355 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 258, length 64 14:34:27.405741 IP 192.168.0.2 > 192.168.0.1: ICMP echo request, id 20744, seq 259, length 64 14:34:27.847941 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33730, length 40 14:34:27.847960 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33730, length 40 14:34:27.850103 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 33731, length 40 14:34:27.850116 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 33731, length 40 -
Do you have static arp setup? Does pfsense know the mac address of 192.168.0.2? Look in the arp table under diagnostics, or from cmd line arp command
What are you firewall rules? on this lan interface?
When you try and ping 192.168.0.2 from pfsense what do you see in your sniff?
-
Static ARP is not enabled in DHCP settings.
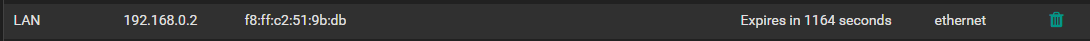
ARP Table shows mapping between 192.168.0.2 and the mac address of the host (this static assignment is configured in DHCP).
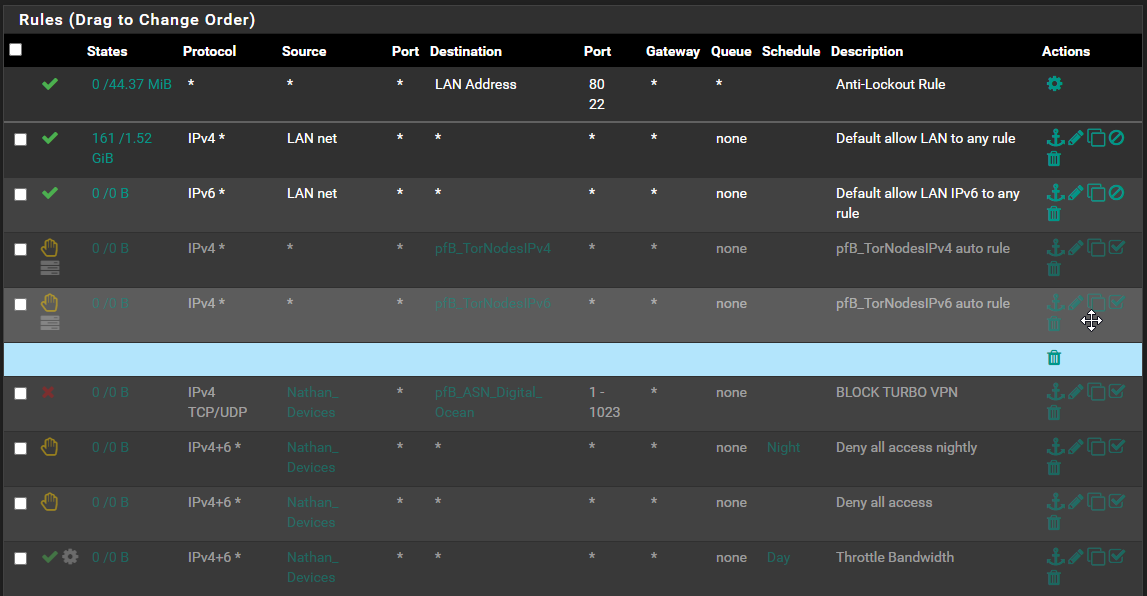
All my LAN firewall rules are set for TCP. Regardless, I disabled them all (except "Default allow LAN to any rule"), and the issue remains.
When I try to ping 192.168.0.2 from pfSense, I see no traces of ICMP echo requests from pfSense to that IP address. -
@shturm said in Cannot ping pfSense from specific LAN host:
All my LAN firewall rules are set for TCP.
Well ping is not tcp... How are you pinging from any IP if your firewall rules are only tcp?
Any any rule would allow.
How about you post up your rules on your lan interface.. And show us the arp table of pfsense showing this 192.168.0.2 address.. And the ifconfig from your device with this IP..
If your saying pfsense shows an arp entry for 192.168.0.2, and it has an interface on the 192.168.0/24 network and you try and ping 192.168.0.2 then it would send a request out that interface. Only reason it wouldn't would be it thinks it thinks is IP is 192.168.0.2? Do you have a vip setup? you would see that in an ifconfig on pfsense..
example.. Here I created a vip on my lan that is the same as a device on my network.
igb0: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=6500bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:08:a2:0c:e6:24 hwaddr 00:08:a2:0c:e6:24 inet6 fe80::208:a2ff:fe0c:e624%igb0 prefixlen 64 scopeid 0x1 inet6 2001:470:snipped prefixlen 64 inet 192.168.9.253 netmask 0xffffff00 broadcast 192.168.9.255 inet 192.168.9.101 netmask 0xffffff00 broadcast 192.168.9.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: activeYour saying that this client is getting IP via dhcp fromn pfsense? But when you try and ping it - you see not request leaving the lan interface via a sniff?
These are all physical devices? Or is VM involved? pfsense a vm, this device a VM? Your other devices?
What is the response on pfsense when you try and ping this 192.168.0.2, error, timeout? Response? what?
Lets see the route table? You don't have some specific route setup for this 192.168.0.2?
You don't have some vpn tunnel network using this 192.168.0 network?
You don't have any bridges setup in pfsense?
-
Here are my LAN firewall rules:
Record in the ARP table:
pfSense is not a VM, it runs on a dedicated box. ifconfig for LAN interface on pfSense:
em1: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=209b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,WOL_MAGIC> ether 00:42:43:ad:02:51 hwaddr 00:42:43:ad:02:51 inet6 fe80::242:43ff:fead:251%em1 prefixlen 64 scopeid 0x2 inet 192.168.0.1 netmask 0xffffff00 broadcast 192.168.0.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex>) status: active192.168.0.2 is a Mac laptop (not virtual either). Its ifconfig:
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500 options=400<CHANNEL_IO> ether f8:ff:c2:51:9b:db inet6 fe80::18dd:7bbb:ca26:6f32%en0 prefixlen 64 secured scopeid 0x6 inet 192.168.0.2 netmask 0xffffff00 broadcast 192.168.0.255 nd6 options=201<PERFORMNUD,DAD> media: autoselect status: activeYour saying that this client is getting IP via dhcp fromn pfsense? But when you try and ping it - you see not request leaving the lan interface via a sniff?
Correct
What is the response on pfsense when you try and ping this 192.168.0.2, error, timeout? Response? what?
[2.4.5-RELEASE][admin@pfSense.localdomain]/root: ping 192.168.0.2 PING 192.168.0.2 (192.168.0.2): 56 data bytes ^C --- 192.168.0.2 ping statistics --- 20 packets transmitted, 0 packets received, 100.0% packet lossLAN ICMP packet capture during this ping:
18:15:54.396315 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 38250, length 40 18:15:54.396355 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 38250, length 40 18:15:54.398692 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 38251, length 40 18:15:54.398705 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 38251, length 40 18:15:54.400630 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 38252, length 40 18:15:54.400643 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 38252, length 40 18:15:54.402520 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 38253, length 40 18:15:54.402533 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 38253, length 40 18:15:54.404441 IP 192.168.0.43 > 192.168.0.1: ICMP echo request, id 16724, seq 38254, length 40 18:15:54.404454 IP 192.168.0.1 > 192.168.0.43: ICMP echo reply, id 16724, seq 38254, length 40 18:15:56.750487 IP 192.168.0.27 > 192.168.0.1: ICMP echo request, id 0, seq 0, length 64 18:15:56.750545 IP 192.168.0.1 > 192.168.0.27: ICMP echo reply, id 0, seq 0, length 64 18:15:58.248093 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.248131 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.284755 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.284769 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.286302 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.286315 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.288076 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.288088 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.291733 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.291746 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.295890 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.295903 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.312926 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.312940 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.314371 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.314384 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.318436 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.318448 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:15:58.319794 IP 192.168.0.57 > 192.168.0.1: ICMP echo request, id 570, seq 26888, length 64 18:15:58.319807 IP 192.168.0.1 > 192.168.0.57: ICMP echo reply, id 570, seq 26888, length 64 18:16:01.641597 IP 192.168.0.116 > 54.186.148.131: ICMP echo request, id 44477, seq 59729, length 64 18:16:01.685131 IP 54.186.148.131 > 192.168.0.116: ICMP echo reply, id 44477, seq 59729, length 64(no traces of 192.168.0.2)
You don't have any bridges setup in pfsense?
No bridges.
Lets see the route table? You don't have some specific route setup for this 192.168.0.2?
This is the route table:
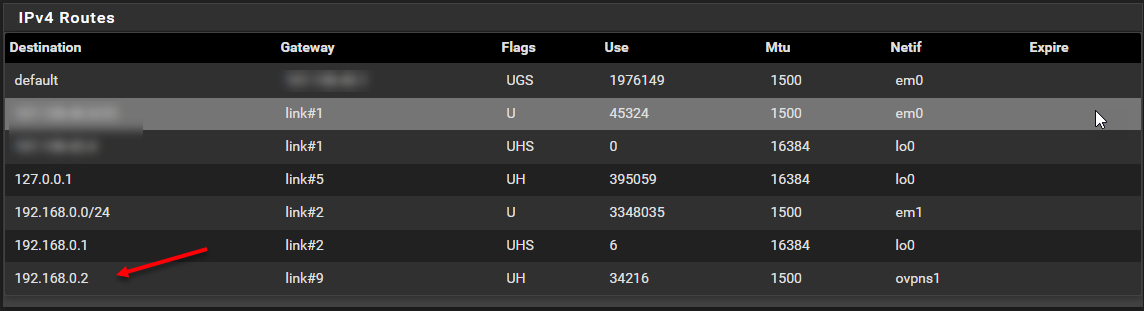
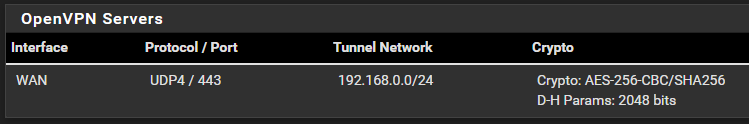
I see an entry there for 192.168.0.2 - is this somehow related? I cannot find where it is set up.I do have OpenVPN set up, but it's not bound to any particular IP address, as far as I understand:
-
I changed OpenVPN tunnel nework to another subnet, and this resolved the issue.
Thank you for the help!