Is it possible to query domain name using outside DNS if using split DNS with Unbound?
-
I'm using pfSense's unbound resolver.
I'm also using a split DNS setup with Host Overrides that associate certain Domain Names with LAN address. I'm using Cloudflare as a registrar and have the local domain name listed as a CNAME.So just to illustrate an example with base domain name known as domain.com and a subdomain as pfsense.domain.com
At cloudflare I have entries:
A domain.com ----> WAN IP address
CNAME pfsense.domain.com -----> domain.comWithin pfsense DNS Resolver
Host Override
pfsense.domain.com----->10.0.1.1From within a LAN located behind pfSense I'd like to perform a DNS lookup that bypasses the DNS resolver. I thought this could be done by specifying a specific DNS server such as:
nslookup pfsense.domain.com 1.1.1.1
---OR----
dig @8.8.8.8 pfsense.domain.comI would have expected in the two lines above, pfsense.domain.com would have resolved to the WAN IP address, however it seems in every case it resolves to the LAN IP address. Is there a way with a firewall rule or other other method to query an outside resolver rather than pfSense's resolver in this case?
-
Are you intercepting dns.. a query direct to 8.8.8.8 would query public dns..
-
Honestly I'm not trying to intercept dns, I'm honestly trying to get soa records for a specific domain from cloudflare needed for the traefik reverse proxy. traefik needs to query the soa records similar to a command such as:
nslookup -type=soa domain.com 1.1.1.1
As you're probably aware 1.1.1.1 is intended to query a specific name server.
If I have the following situation
pfsense.domain.com --> Listed as Host Override within pfsensenslookup -type=soa pfsense.domain.com 1.1.1.1 I'll get the following: #nslookup -type=soa pfsense.domain.com. 1.1.1.1 Server: 1.1.1.1 Address: 1.1.1.1#53 *** Can't find pfsense.domain.com.: No answerTo further elaborate if I have another subdomain pfsense2.domain.com which is also listed at Cloudflare as a CNAME for domain.com and DOES NOT have a Host Override, then the nslookup will succeed. The soa lookup will proceed with either:
#nslookup -type=soa pfsense2.domain.com. 1.1.1.1
or
#nslookup -type=soa pfsense2.domain.com.I'm labeling success in this situation like the following:
nslookup -type=soa pfsense2.domain.com 9.9.9.9 Server: 9.9.9.9 Address: 9.9.9.9#53 Non-authoritative answer: *** Can't find pfsense2.domain.com: No answer Authoritative answers can be found from: domain.com origin = connie.ns.cloudflare.com mail addr = dns.cloudflare.com serial = 2035664926 refresh = 10000 retry = 2400 expire = 604800 minimum = 3600Specifying the specific DNS server doesn't seem to make a difference either with nslookup or dig.
What I would like to occur is if nameserver such as 1.1.1.1 is specified the query goes to the named nameserver, however with no nameserver the query is handled by Unbound. I don't believe the current implementation with the Host Override functions like this unfortunately after I've spent time looking at the log files. Perhaps however this behavior could be altered with firewall rules??? Not sure.
-
More is going on with your DNS..
Because
is a locally defined host domain name, unbound knows about it.
It's also normal that the upstream 1.1.1.1 doesn't know what pfsense.domain.com is. But it should know about the SOA of domain.com, that is, if you use a public registered domain name for your local network.unbound, the resolver, can resolve something like 'pfsense.domain.com' to a A or AAAA but it has no SOA record, most probably because you didin't define one locally. It's not really playing the role of a authoritative DNS server.
If your "domain.com" is a registered domain name - using a registrar, a SOA would exist.
A nslookup (run on a PC on LAN ) asking for the domain SOA (not subdomain !) :
C:\Users\Gauche>nslookup -type=soa brit-hotel-fumel.net 1.1.1.1 Serveur : one.one.one.one Address: 1.1.1.1 Réponse ne faisant pas autorité : brit-hotel-fumel.net primary name server = ns1.brit-hotel-fumel.net responsible mail addr = postmaster.brit-hotel-fumel.net serial = 2020050319 refresh = 14400 (4 hours) retry = 3600 (1 hour) expire = 1209600 (14 days) default TTL = 10800 (3 hours)A dig (on pfSense) gives me an identical, more cryptic :
dig @1.1.1.1my-registred-local.net SOA +short gives me ns1.my-registred-local.net. postmaster.my-registred-local.net. 2020050319 14400 3600 1209600 10800which is also correct, as "my-registred-local.net" is a domain name I own (rent).
Also, your 'nslookup' (from PC on LAN) returns :
Server: 1.1.1.1 Address: 1.1.1.1#53mine returns :
Server: one.one.one.one Address: 1.1.1.1#53so you can't 'reverse ptr'.
Reset your DNS settings to default ?!
edit DNS resolver and SOA records : same question ?
Btw : Forwarding is useless, something from the past, blows a hole in your 'privacy'.
Except if you have to communicate your DNS request to an upstream DNS company.The Internet is based on a pile of RFC papers. These papers tell you what (DNS) to use so everything works well. pfSense is setup up by default respecting thses RFC's. No where it's stated that you should use some "Fortne 500" company's DNS to make your connection work. That is, you'll be needing an ISP, as being your own ISP probably financially a show-stopper.
-
@kevdog said in Is it possible to query domain name using outside DNS if using split DNS with Unbound?:
Honestly I'm not trying to intercept dns
My point was - the only way you would not be able to directly query the dns is, you can not talk them - ie blocked either at pfsense or your isp. Or your intercepting traffic either at pfsense or isp.
If your saying your getting your host override returned - than that says your intercepting it at pfsense.. Or you have your public dns misconfigured with the wrong IP?
As you're probably aware 1.1.1.1 is intended to query a specific name server.
Ok ;) hehehehe dude I am well aware of exactly how dns functions ;)
How about you PM the fqdn your trying to query, if you don't want to post it here - so I can see exactly what public dns says about it.
-
Ok got your PM.. with your domain.. And don't show anything wrong with it on the public side. Other than cloudflare likes to use invalid serial numbers for their SOA ;)
Maybe your not understanding me.. Pfsense has nothing to do with you talking to some IP out on the public, be it dns, be it http/https, ssh, sftp, ntp, whatever..
Unless you blocked it - any client on your network would be able to talk directly to any dns server on the planet.
If your not able to do a query for your domain for any sort of record directly to say goggle or quad9.. Then either you blocked it in pfsense, or its blocked upstream, or your intercepting traffic dns and sending it local? Which would explain how your getting your local records when your suppose to be asking some external NS.
Your dig @8.8.8.8 would be direct to that IP and whatever you query you query..
Here I setup a host override for www.cnn.com to point to 10.11.12.13
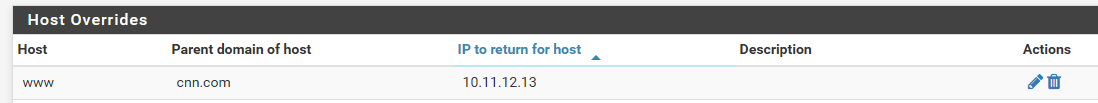
If I query that locally - that is what I get.
C:\>dig www.cnn.com ; <<>> DiG 9.16.8 <<>> www.cnn.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7685 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.cnn.com. IN A ;; ANSWER SECTION: www.cnn.com. 3600 IN A 10.11.12.13 ;; Query time: 6 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Tue Nov 10 07:14:49 Central Standard Time 2020 ;; MSG SIZE rcvd: 56If I query say 8.8.8.8 I get the public..
C:\>dig @8.8.8.8 www.cnn.com ; <<>> DiG 9.16.8 <<>> @8.8.8.8 www.cnn.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14646 ;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;www.cnn.com. IN A ;; ANSWER SECTION: www.cnn.com. 147 IN CNAME turner-tls.map.fastly.net. turner-tls.map.fastly.net. 29 IN A 151.101.1.67 turner-tls.map.fastly.net. 29 IN A 151.101.65.67 turner-tls.map.fastly.net. 29 IN A 151.101.129.67 turner-tls.map.fastly.net. 29 IN A 151.101.193.67 ;; Query time: 32 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Tue Nov 10 07:15:50 Central Standard Time 2020 ;; MSG SIZE rcvd: 143If your trying to so something that would query unbound.. ie pfsense for that - then yeah you would be back your local host override. If your domain is set as pfsense domain, and you have your zone set as static then looking for something that you don't have a local record for would not look up from public. But the default setting is transparent.. And even if you had a local record for a, but not for soa.. you would be able to look that up as well as long as the domain is not your local zone.
example - here I can query cnn.com for their soa.
C:\>dig cnn.com soa ; <<>> DiG 9.16.8 <<>> cnn.com soa ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7664 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;cnn.com. IN SOA ;; ANSWER SECTION: cnn.com. 3600 IN SOA ns-47.awsdns-05.com. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 ;; Query time: 53 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Tue Nov 10 07:19:11 Central Standard Time 2020 ;; MSG SIZE rcvd: 113 -
I tried replying to your thread but my post was flagged as spam... what give??
-
No idea what you were trying to post?
-
Ok basically I had everything typed out and formatted but that was flagged as spam.
I created the experiment you had above with the cnn override.
***Due to spam filter on these forums I can't type the actual www address below so to bypass spam filter --- c/n/n=cnn -- sorry about confusion.
In both cases of query (dig www.c/n/n.com and dig @8.8.8.8 www.c/n/n.com) it resolved to the local IP address assigned in the override.
I've tested this from multiple servers running in different VM's on the LAN and its the same for all.
You stated something about dns interception however this has to be at the pfsense level since anything upstream to this would not resolve to the host override. Is there anywhere else in pfsense where the dns would be getting intercepted? I don't have any firewall rules for port 53 in any of the rulesets. I'm really confused.
I've also ran the same queries above directly within pfsense -- the queries actually resolve correctly as per your example.
-
@kevdog said in Is it possible to query domain name using outside DNS if using split DNS with Unbound?:
I tried replying to your thread but my post was flagged as spam... what give??
Could that be reputation < 5 ?
/Bingo
-
pfsense does not do dns redirection unless you specifically set it up.
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html
What do you have in front of pfsense? Some soho router doing redirection pointing to pfsense for dns? Are you connected wireless to some wifi router behind pfsense, doing redirection?
Or wired to some soho router doing it?
This isn't rocket since - pfsense run a dns server. Unbound out of the box.. If you create a record locally for www.domain.tld that pints to 192.168.1.100 or something - nothing else would resolve that unless pfsense is asked for that.. If your resolving local IP, then someone you asked pfsense.. How you have your network setup I do not know..
-
Hey thanks for at least pointing things out to me -- I really appreciate it since it really made me examine my setup a lot closer.
To answer your question directly I have a comcast model that plugs directly into self-built "protectli-type" box. pfsense is virtualized within xcp-ng which works pretty well for home setup.
I think however I found the problem after scratching my head for a really long long time. Within pfsense System->Advanced->Firewall & NAT -> Network Address Translation
NAT reflection mode for port fowards was set to Pure NAT. After disabling this setting, the queries would resolved appropriately. Strange I didn't think about this before.
-
Nat reflection has nothing to do with dns..
Nat reflection would be if you hit your wan IP on port X, and you had a port forward setup to forward port X to ip 192.168.1.100
That has zero to do with how dns would respond if you ask pfsense or not.. Again if you were doing a directed query to 8.8.8.8, pfsense would have zero to do with that conversation, nor would nat reflection.
Unless you had some port forward setup for dns (tcp/upd 53)??
Did you setup port forwarding for dns? Or redirection of dns?
-
-
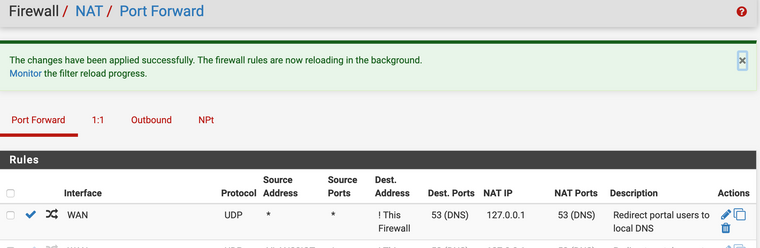
Why would you setup a rule like that - makes zero sense.. For starter why would anything be hitting your wan but not to any of your firewall IPs?
For the life of me - can not figure out what that rule would do.. There should be nothing hitting your wan on 53, but not directed to your wan IP.. What are you wan firewall rules?
But yes if some traffic came into your wan interface for say 8.8.8.8 (not a firewall IP) it would be forwarded to loopback.. If your wan firewall rules allowed it, or some floating rule did. And then yes that would return whatever host override you had setup. etc..
-
Yea - I get it. They don't make much sense -- I've definitely had to either drop some of the NAT and Firewall rules for not making sense. Bottom line was the NAT rules was redirecting all port 53 requests to pfsense which was intercepting all the outgoing traffic.
Thanks a lot for your help on this issue.