Mysterious block: Can’t connect to LAN ssh host from WAN
-
I set up a NAT rule like so:

It has a corresponding Firewall rule:

When I am on the LAN I can telnet into that host (on Port 22) like so:
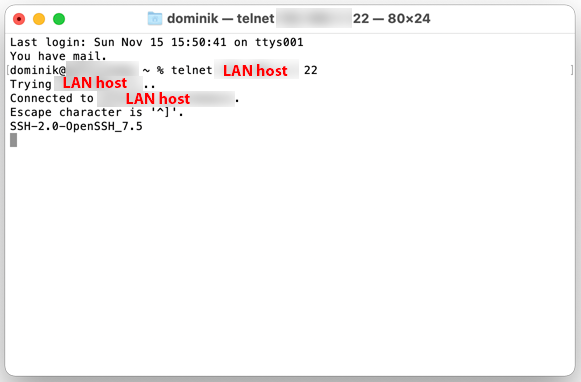
However, when I am outside of my home, I cannot get in:
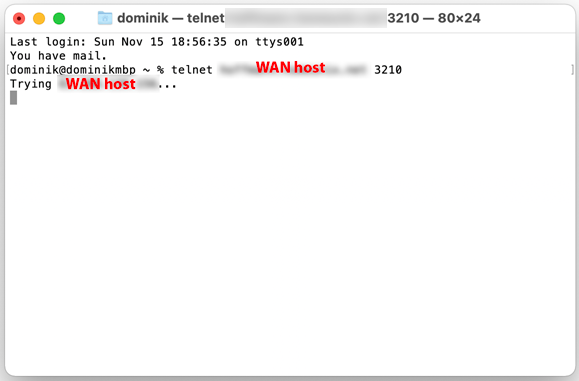
Crickets!
Where else might there be a block? My ISP is not blocking anything, which I verified today.
-
Hi,
Your mentionned a ssh acces, but are using telnet.
What happens when you use 'ssh' ?Why do you hide LAN IP addresses ?
Your firewall rule is on WAN ?
Then this :
says a lot : nothing comes into the pfSense WAN port.
This means : traffic is blocked up stream. Most typically your upstream ISP router. That one has to be natted to.edit : the pfSense manual contains a complete run down on how to look for NAT and port forward issues.
-
state is 0/0 so that rule never match
check the order of your rules on WAN interface, maybe you have a block before the NAT ruleRulesets on the Interface tabs are evaluated on a first match basis by pfSense. This means that reading the ruleset for an interface from top to bottom, the first rule that matches will be the one used by the firewall. Evaluation stops after reaching this match and then the firewall takes the action specified by that rule.
-
These are the only preceding firewall rules:
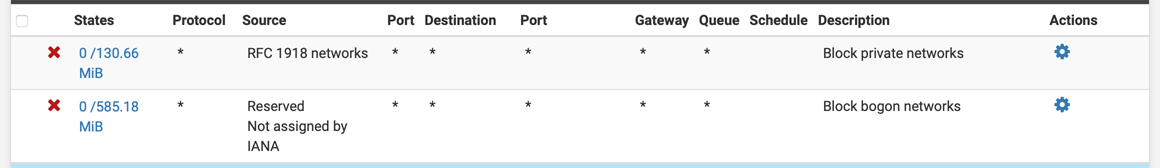
I will get back in touch with my ISP. My ISP doesn’t provide its own router. Their hand-off is the Ethernet port of their ONT (optical network terminal).
-
And those rules are seeing quite a few hits.. 585MB to bogon??? WTF??
I am also curious why your using telnet client to test ssh access ;)
But in general just like when testing any port forwarding. I don't care what the isp says they don't block or do or whatever. Validate the traffic your trying to forward actually hits your wan..
Simple 10 second sniff on your wan interface will give you proof if the traffic got there or not.
Now sniff on the lan side interface - do you see pfsense send the traffic on?
Its quite possible your client your sshing to locally has a firewall that does not allow access from source other than its local network. Does this ssh host your trying to hit even use pfsense as its gateway? etc..
https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat.html
-
I was at the headquarters of my ISP today. They have a Gigabit guest WiFi network at their facility. One of their tech people confirmed for me that there is no outbound port blocking there. Still I could not ssh into my home server.
-
And did you do the 10 second test of just sniffing on your wan while your trying to connect? Who says your isp is blocking, could be blocked from where you trying to test from - or anywhere between, etc. etc..
You can not troubleshoot port forwarding until you actually verify pfsense even sees the traffic.. It can not forward what it never sees.
that there is no outbound port blocking there.
What about inbound? Which what your trying to do right.. Not outbound..
-
@johnpoz: How do I do that? I haven’t, actually. What tool would I use? Should I do a Diagnostics→Packet Capture?
I did. Nothing shows up on the WAN interface that would have the port number 3210 or the WAN IP address of my router or the WAN IP of the network from where I made the ssh attempt. The LAN packet capture successfully showed the connections that were made from the LAN on Port 22.
-
@johnpoz I meant to say that I tested trying to connect to my home server from a network that I know has no outbound port blocking of its own. I had to have their tech verify that on their network outbound traffic on Port 3210 was permitted.
-
So back to this one :
Between your pfSense, the pfSense WAN NIC, and your ISP, are some other 'boxes'. One of them is probably your ISP-box at your place.
Is this a modem ? A router ?
If it's a router, you natted port TCP 3210 from it's 'WAN' to it's LAN, to the WAN IP, port 3210 of your pfSense ?
Your WAN IP is RF 1918 = 10/8, 172.16/12, 192.168/16 ?
What happens if you take pfSense out of the netork, and hook up your home server directly ?
@Gertjan said in Mysterious block: Can’t connect to LAN ssh host from WAN:Most typically your upstream ISP router. That one has to be natted to.
-
@DominikHoffmann said in Mysterious block: Can’t connect to LAN ssh host from WAN:
The LAN packet capture successfully showed the connections that were made from the LAN on Port 22.
And how was that? You connected from pfsense to this server? 2 devices on your lan, talking to each other would not show up on pfsense lan packet capture.
Per what @Gertjan is saying.. Is there something in front of pfsense? Another router, an isp device? Does pfsense have a public IP on its wan or a rfc1918 address? Ie the address ranges given above.
-
I just spoke with the CTO of my ISP. The support people I have talked to may not have been aware of this, but he zeroed in on the issue right away. My ISP uses NAT to dole out IPs to customers’ routers. So, my LAN address space was essentially double-NATted, and connections to my network originating from the WAN were not routed to my router, because I have no control over that part of the ISP’s infrastructure.
-
Which you wouldn't had to have asked anyone - just looked on your router what your wan address was.
And if you would of been very obvious when you sniffed as well that no packets were getting to your wan..
-
@johnpoz: I guess, I was not familiar with did not fully understand exactly what everything on the pfSense dashboard meant.
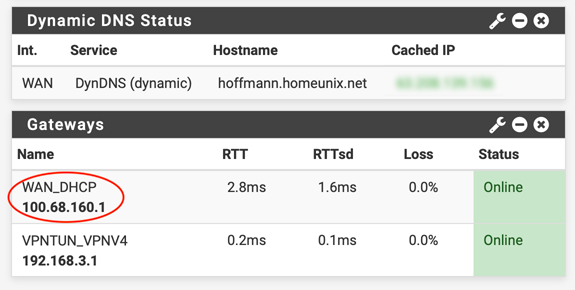
If I had understood, I would have noticed that the IP on the Internet (obscured, green) was not identical to the WAN_DHCP address (circled in red).
My ISP has given me a static IP address, and everything works now, including my OpenVPN setup about which I had posted earlier. I am still trying to ascertain, why it worked in the first place.
Thanks very much for all of you who helped shed light on the issue.
-
Or just that 100.68 is a Carrier grade nat IP.. 10.64/10
Well how it worked in the first place, is when it was working you were not on a CGNat IP..