Conditional Outbound NAT
-
I want migrade rules from iptables to pfSense. I can't find how to configure source/outbound NAT (see POSTROUTING lines) on pfSense. I can't find how to make translation dependent on destination IP from source packed like on iptables.
iptables -t nat -A PREROUTING -i WAN --dst 192.168.0.5 -p udp --dport 5252 -j DNAT --to 172.16.0.200:5252 iptables -t nat -A PREROUTING -i WAN --dst 192.168.0.6 -p udp --dport 5252 -j DNAT --to 172.16.0.200:5252 iptables -t nat -A POSTROUTING -o LAN -m conntrack --ctstate DNAT --ctorigdst 192.168.0.5 -j SNAT --to 10.254.0.5 iptables -t nat -A POSTROUTING -o LAN -m conntrack --ctstate DNAT --ctorigdst 192.168.0.6 -j SNAT --to 10.254.0.6 -
@rsrb
You can try it here: Firewall > NAT > OutboundSwitch into the hybride mode so that manually added rules are applied.
-
Yes I understand but how do I combine both outbound NAT and port forward for the same packet ?
The outbound NAT rules for interface LAN has condition- line: translate source IP to 10.254.0.5 only when original packet destination IP is 192.168.0.5
- line: translate source IP to 10.254.0.6 only when original packet destination IP is 192.168.0.6
But in Outbount NAT form I can specify only Destination IP after Port Forward NAT (translated) which is same (172.16.0.200) for both original packets how I nead.
I nead two different translation depended on original destination IP:
src:any/* dst:192.168.0.5:5252 -translate->src:10.254.0.5/* dst:172.16.0.200:5252
src:any/* dst:192.168.0.6:5252 -translate->src:10.254.0.6/* dst:172.16.0.200:5252 -
@viragomann Thank you for your response. I specified more details. Do you have any idea how to configure on pfSense?
-
@rsrb
I'm afraid, outbound NAT depending on the origianal destination address isn't doable on pfSense. -
I am having a hard time understanding what your trying to accomplish exactly... Can you provide example use case of what is happening where you would want/need to do whatever it is your trying to do.
You can for sure do conditional outbound nat, and pick what interface it nats too, etc.
this is doable in a sense.. But why would device try to go to 192.168.0.5 vs 172.16.0.200?
src:any/* dst:192.168.0.5:5252 -translate->src:10.254.0.5/* dst:172.16.0.200:5252 src:any/* dst:192.168.0.6:5252 -translate->src:10.254.0.6/* dst:172.16.0.200:5252Where that source is either a specific interface or a vip on an interface. But not understanding why you would want or need to do such a thing.. As you have that stated I do not think you could do such a thing? You want to forward traffic that is dest for 192.168.0.5 to 172.16.0.200, but source nat the traffic based upon the client that tried to go there?
You could just do a port forward where the source would be natted to something.
If I have a outbound nat rules that says when talking to 172.16.0.200, and the source is 192.168.0.5, source nat it to 10.254.0.5..
But still not understanding why your source would not just directly talk to 172.16.0.200?? And you would nat it to the interface on pfsense to talk to that IP..
More than happy to help, but need to understand what your actually trying to accomplish - because I'm not getting the use case..
edit: Also your networks are all rfc1918, why are you doing any natting if they want to talk to each other?
-
I tried to simplify the assignment as much as possible. The IPs on the WAN interface are IPs for various groups of IoT devices (for many of them it is not even possible to set the destination port :(). IoT device types are mixed in same subnets. Here is not possibility to identify device type by source IP. The LAN interface is actually a VPN tunnel to cloud provider with a silly application. But its provider is willing to publish it on only one IP address and port. And on top of this application requires for each IoT device type one separate source IP (only). Routing of packets outside NAT box is done now and work OK.
+----NAT BOX----------------+ | | IoT clients | eth0 tun0 | IoT portal ORIGINAL PACKET | 192.168.0.1/24 172.16.0.1 | TRANSLATED PACKET src:* dst:192.168.0.5+-> 192.168.0.5 |-->src:10.254.0.5 dst:172.16.0.200:5252/udp src:* dst:192.168.0.6+-> 192.168.0.6 |-->src:10.254.0.6 dst:172.16.0.200:5252/udp | | +---------------------------+I tried describe this simply and exactly by my actuall NAT configuration:
iptables -t nat -A PREROUTING -i WAN --dst 192.168.0.5 -p udp --dport 5252 -j DNAT --to 172.16.0.200:5252 iptables -t nat -A PREROUTING -i WAN --dst 192.168.0.6 -p udp --dport 5252 -j DNAT --to 172.16.0.200:5252 iptables -t nat -A POSTROUTING -o LAN -m conntrack --ctstate DNAT --ctorigdst 192.168.0.5 -j SNAT --to 10.254.0.5 iptables -t nat -A POSTROUTING -o LAN -m conntrack --ctstate DNAT --ctorigdst 192.168.0.6 -j SNAT --to 10.254.0.6Us I wrote at begging: "I want migrade rules from iptables to pfSense. "
-
@johnpoz Is possible to do NAT on pfSense like on Linux? I tried to describe in more detail.
-
Still trying to wrap my head around what your trying to accomplish.. If the connection is a vpn tunnel - why do you need to nat? Seems like a cluster to me.. If you have something you need to talk to at some site via a vpn.. Then route the appropriate networks.. This sure seems like a some sort of MacGyver setup with bubblegum and toothpicks and rubberbands..
-
@johnpoz
Yes it is true. The world of IoT is like this :(.
I can improve this solution by replacing the Linux server with a more secure pfSense. Not more. But I can't find a solution to replace box 1: 1 with the functionality of the existing Linux.
But back on track. Is it possible to configure the same NAT behavior on pfSense as on current Linux, as I described above? If that's not possible, the pfSense is not the way for me :(. -
So I am clear.. You have some IOT device
192.168.0.X
And he tries to talk to 192.168.0.5, which you want to send that to 172.168.0.200, but make the source 10.254.0.5..
For starters you would have to have a 192.168.0.5 vip on pfsense. And then to translate it to 10.254.0.5 you would need another vip..
edit: ok did a simple test of this.. I create a port forward on my lan interface, you could create a vip for your IP.. That said hey if you go to 192.168.9.253 on port 5353 send it to 172.16.200.2
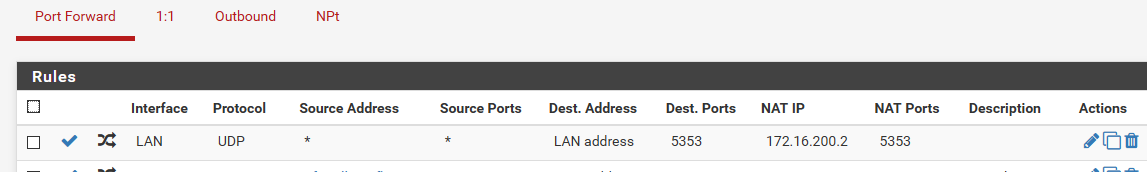
I then created an outbound nat that said hey if your sending to 172.16.200.2 - use the vip IP 192.168.100.2 (I already had this for talking to my modem)..

I then generated simple dns query on port 5353, easiest way to just generate some traffic to specific port on specific IP..
Sniffing on wan, since that is where it would go trying to get to some unknown IP on my network.. But with yours you would have a vpn to send it down, etc.
So you can see the traffic was sent to 172.16.200.2 from my 192.168.100.2 address..
12:58:32.127354 IP 192.168.100.2.16046 > 172.16.200.2.5353: UDP, length 49 12:58:37.139187 IP 192.168.100.2.16046 > 172.16.200.2.5353: UDP, length 49 12:58:42.150230 IP 192.168.100.2.16046 > 172.16.200.2.5353: UDP, length 49So yes I would think what your wanting to do is possible just in the gui - but you would have to create different vips for both your inside 192.168.0.x addresses and your 10.200 addresses