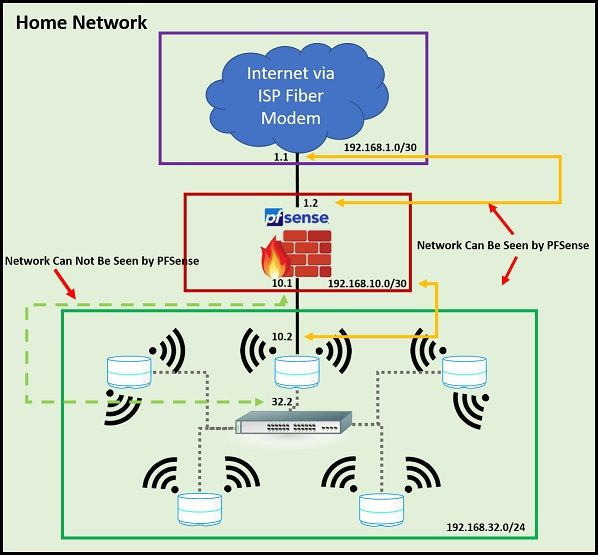
Getting PFSense to See Internal Network
-
I assumed that was just depicting the wifi mesh there, not a real switch?
-
@stephenw10 said in Getting PFSense to See Internal Network:
I assumed that was just depicting the wifi mesh there, not a real switch?
Ahh could be

-
@stephenw10 Google Wifi's allow you to directly connect them via Ethernet to improve performance of the mesh. You get way better speeds if they are meshed by Ethernet too. So yes they are all interconnected through a switch. The pucks just see it as that is a faster path to devices vise using wireless if they are near one of the other pucks. It is sort of like they are mini routers using RIP or OSPF to get to a part of the network.
-
@bingo600 Yeah I thought of that too but it would bypass the security needs and defeat the purpose of having the firewall. The limitation is that you can't static route through the Google Wifi pucks.
-
@greg-dreelin
This link does not have to be insecure.
You can add rules to that interface , that deny's anything you don't want to transport.In fact it could be as secure as the link you suggest (going to the top google wifi).
Assumption :
1:
192.168.32.0/24 has def-gw on the google inside (32.1?)2:
All packets going to the internet will have (be natted to) the google device outside IF.That would mean that you see all internet bound traffic (on the pfSense) via the google outside ip (192.168.10.2)
TLDR Brainstorming in public - See Summary
On the top (10.1) interface , you could :
Block src any dest 192.168.32.0/24 ports any (I'd set dest to RFC1918)
Permit src any dest any ports anyOr (i suppose the google thingy nats all to (10.2)
Instead of src any you could use src 192.168.10.2 (google wifi outside)That would effectively block anything comming in from that IF , to the "inside"
But you should never see any packets destined for 192.168.32.0/24 , on the google outside , as it shuold be kept on the inside IF.
You could manage the pfSense vial the "new switch pfSense IF"
Then you wouldn't even have to open pfSense management from the google device.The only thing (i see right now), is to watch out for would be assymetric routing , when going (outbound) to the internet.
But if you keep (use) def-gw as the google inside ip , all internet traffic would go that way , and be seen in the pfSense as comming from 192.168.10.2
And pfSense will route return packets that way.Summary
Basically i think you don't need to do anything wrt. rules on the pfSense-Google IF, the routing would handle that (keep 192.168.32.0/24 packets inside).Since you say that the requests to the 192.168.32.0/24 devices will be initiated from the pfSense.
The new pfSense-Switch IF , could be made even with "no rules" on it, so that it effectively blocks anything (inbound to pfSense) initiated from the 192.168.32.0/24 Net , aka. the pfSense can initiate to "inside devices" , and "inside devices can ansver" , No "inside devices" can initiate via that IF.I'd might allow pfSense mgmt via the "new IF"
Well brainstorming is a bit messy , so many possibilities.
I hope you get the idea.Edit:
Since your def-gw is on the google , you might have to add a specific return route on the devices that must be reached from (via) the pfSense (if packets originate from another pfsense network) than the .32.0 network/Bingo
PS:
Are the devices you need to reach behind wifi or in the switch ?
Can you create multi lans on the google inside interface ?PPS: Idea
Can you disable DHCP on the Google ??
That would open up for (DHCP) using the pfSense DHCP / DNS / NTP etc ....
And maybe prevent a bit of "Big brother..."PPPS: Idea (hack)
Can you do static routes on the google ?
If yes , you might be able to set the google def-gw to the new pfSense IF.
And if you're lucky , disconnect the google outside IF , and it'll keep using the static def-gw.
And effectively make it an AP.
But knowing google , they prob want to "own/track" all your outbound traffic, and prevent that "hack" -
Again, what are you actually trying to connect to on the inside subnet?
You could have a separate interface in pfSense that connects to the switch directly and only carries inbound traffic. You would have to outbound NAT it in pfSense to prevent asymmetry.
Steve
-
@stephenw10 said in Getting PFSense to See Internal Network:
Again, what are you actually trying to connect to on the inside subnet?
You could have a separate interface in pfSense that connects to the switch directly and only carries inbound traffic. You would have to outbound NAT it in pfSense to prevent asymmetry.
Steve
Well I have a Plex Server I want to allow access to someone in my family. I have put in port forwarding from the device through the Google Wifi, through the PFSense, and the ISP's gateway. When the person tries to access it I can see the request come in on the PFSense but for the internal IP and it denies it. I am assuming since it cannot see the 192.168.32.0 net it dumps it. I have tried a rule to allow but it keeps denying it. I am at a loss right now on getting it through.
-
If you are seeing traffic with a destination in the 192.168.32.x subnet hitting something on a pfSense interface then you have one of those port forwards setup wrong. Probably the one in pfSense since it's actually arriving there.
Adding a port forward will normally automatically add a firewall rule on WAN to pass that so I assume you either changed that or chose not to have it added.
Port forwards happen before the firewall so if your port forward is configured to use the 192.168.30.x destination and you have removed (or just added) the rule you will see that blocked on WAN.
However that's wrong anyway because the pfSense forward should be to the Google WIFI node IP, 10.2. The forward in Google WIFI should be to the 192.168.32.X IP.Can we see a screenshot of the forward and WAN rules?
What are you running Plex on? You can probably tunnel to pfSense from there and get past the WIFI as I initially suggested.
Steve
-
@stephenw10 I am running the Plex on a 14Tb UnRAID rack mount system. It is a docker on the UnRAID platform. This issue is getting connection to in from the outside. Dynamic DNS is a bit hokey at best.
-
@greg-dreelin
Why don't you split the WiFi Lan and "Switch Lan" into two lans, each with a pfSense interface.
Make (keep) a Lan/Vlan just having the WiFi stuff (192.168.32.0/24)
Make a new one 192.168.33.0/24 , where you put all your non wifi attached stuff.
You could be quite permissive on the pfSense wifi interface , as it is also a trusted zone.
Allow ip src 192.168.10.2 dest 192.168.33.0/24Traffic from Wifi to "Switch" should not be an issue (well it would be natted to the google outside) , prob. but not a problem.
Traffic initiated from "Switch" to Wifi would be troublesome (portforward needed) , but do you really have any need for that ?
If done like that , then you'll get kind of two separate segments in your house.
But at least one of them will be "normal"./Bingo
-
Well I'm pretty sure you could setup a tunnel from Unraid to pfSense. Even if that's a, probably unnecessary, VPN tunnel. Then have Plex listen on the tunnel subnet too. You could then port forward to it in pfSense as though it's directly connected.
But if you can port forward in Google WFI you just need to get all three port forwards setup correctly.
Or, yes, move the Unraid box to a different interface on pfSense dircetly.
Steve
-
Thank you all for some great ideas. Unfortunately I can't VLAN with Google Wifi networks (yep it blows), the switch can but the wifis can't figure it out. I theory it should work with port forwarding and punching through the PFSense but I am missing something that is not allowing the push from the firewall to the local network behind the first Google Wifi. I am interested in the second line idea and may try that. I appreciate all the advice and help.
-
Your google wifi is also doing nat.. If you want something from outside to get to something on the google network, you would have to do 2 port forwards.
1 at edge, and then again at your downstream nat router.
Here is the thing - if you want to run a big boy network.. Your not going to do it with soho stuff designed for home users.
Get APs that support vlans. Get switch(es) that do vlans if you want.. Your only going to cause yourself grief trying to do enterprise grade networking with home user stuff..
-
It's ugly (triple NAT!) but you can port-forward in Google WIFI: https://support.google.com/wifi/answer/6274503?hl=en-GB
This will work if you have all three port forwards setup correctly.
The fact you were seeing blocked traffic in pfSense shows at least one port forward is wrong. See my comments above.
Steve
-
This post is deleted!