Isolating vlans
-
This post is deleted! -
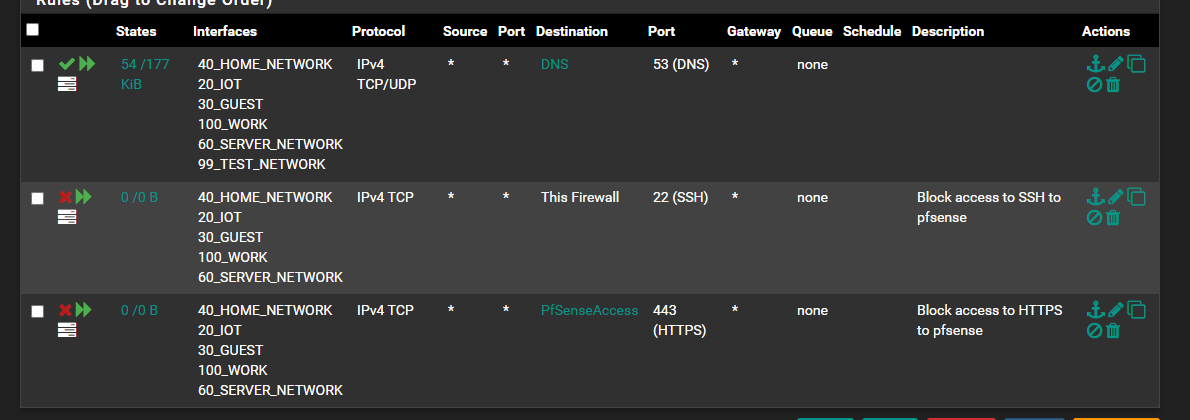
There are a few ways to approach this problem; my favorite is to create an alias called RFC_1918 and put all the non routable IP subnets in it (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16); you might also want to also add some of the illegal/special use (RFC 6890) subnets that shouldn't appear on the Internet.
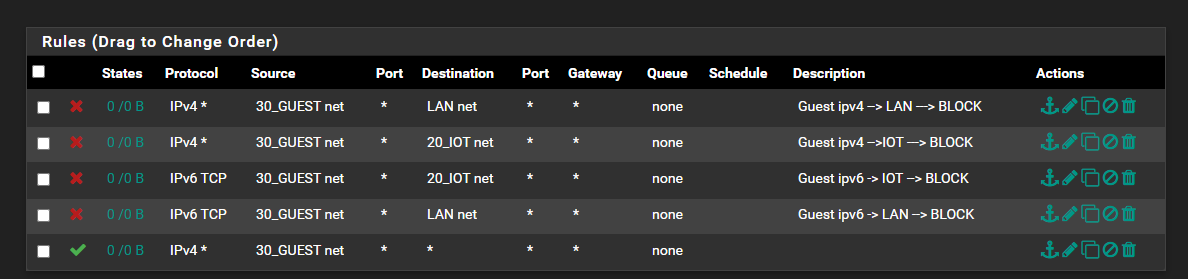
Then, in each vlan ruleset, a single before-last rule that says block from this-net to RFC_1918. Any explicit access can be granted prior to this rule, and the last rule is the allow this-net to any rule to get out to the Internet.
Unless you are using non-private IPs internally, this will work fine, and will catch any future expansion.Similarly, you could create an alias called internal_vlans and put all your internal vlans in it, and using the same rule structure, you will prevent vlans from talking to each other unless explicitly allowed. This doesn't scale quite as well, as you need to add any new vlans to the internal_vlans alias, but it does allow you to use other subnets than the standard non-routable ones.