IPSec IKEv2 + 2fa (Google Authenticator)
-
Hi. Configured the IKEv2 + FreeRADIUS bundle, it works without problems. But now you need two-factor authentication.
In Diagnostics - Authentification, authentication is correct (I enter the username and PIN + code from the authenticator).
VPN doesn't work. What could have done wrong? -
Unfortunately that isn't likely to work with IKEv2.
The problem is that mOTP needs to see the plaintext of the password to read the PIN/password and OTP code separately, but IKEv2 needs EAP and expects passwords to be encrypted end-to-end and not directly readable.
-
-
Yes, Google Authenticator and mOTP work essentially the same way.
-
@jimp said in IPSec IKEv2 + 2fa (Google Authenticator):
Yes, Google Authenticator and mOTP work essentially the same way.
So are there any other 2fa methods which can work with IPSEC?
-
I'm not 100% sure but something out-of-band like Duo may be possible since it wouldn't get directly involved in a way that would break EAP.
-
I followed this guide to get OpenVPN working with DUO.
https://www.reddit.com/r/PFSENSE/comments/4y81qi/openvpn_and_duo_security_how_to/When i set this up for IPSEC, my request is hitting the NPS server but giving me this response
Authentication Type: EAP
EAP Type: -
Account Session Identifier: -
Logging Results: Accounting information was written to the local log file.
Reason Code: 66
Reason: The user attempted to use an authentication method that is not enabled on the matching network policy.Now i've set MSCHAP v2 on the authentication server in pfsense and in the NPS client policy but its not working. My knowledge of EAP and the protocols is extremly limited so any help would be appreciated
Note: When i do the simple authentication through the pfsense diagnostic tab. It works fine. I can see MS-CHAPv2 instead of EAP.
Authentication Details:
Connection Request Policy Name: Use Windows authentication for all users
Network Policy Name: Allow pfSense
Authentication Provider: Windows
Authentication Server:
Authentication Type: MS-CHAPv2
EAP Type: -Here is the NPS Settings
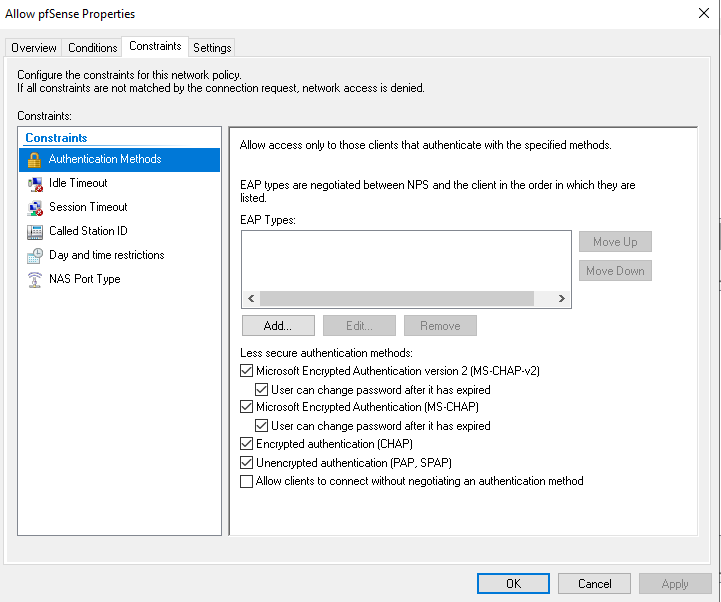
-
Update : This was fixed by adding the EAP type ms chap v2
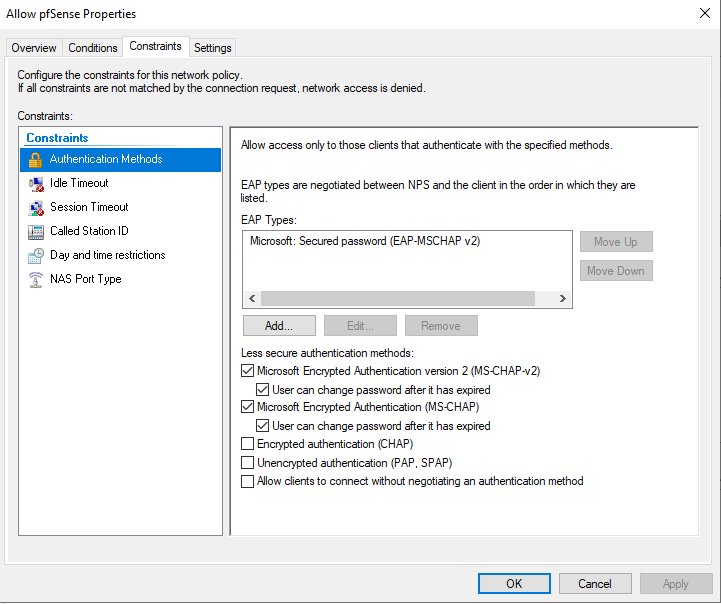
The only issue i have now is that if the duo prompt is accepted late, the VPN doesnt connected as it has already timed out. How can i increase this timeout value?
**Dec 23 13:42:26 charon 64472 15[CFG] <con-mobile|4> RADIUS Access-Request timed out after 4 attempts Dec 23 13:42:20 charon 64472 15[CFG] <con-mobile|4> retransmit 3 of RADIUS Access-Request (timeout: 5.5s) Dec 23 13:42:18 charon 64472 06[MGR] ignoring request with ID 4, already processing Dec 23 13:42:16 charon 64472 15[CFG] <con-mobile|4> retransmit 2 of RADIUS Access-Request (timeout: 3.9s) Dec 23 13:42:14 charon 64472 06[MGR] ignoring request with ID 4, already processing Dec 23 13:42:13 charon 64472 15[CFG] <con-mobile|4> retransmit 1 of RADIUS Access-Request (timeout: 2.8s)** -
@blackops786187 found a solution?
-
Nope. I suspect it’s something within the strongswan config files which I have no idea to navigate. Right now I’m using OpenVPN with duo and it’s fine for my use case
-
https://forum.netgate.com/topic/144614/mobile-clients-with-otp
Last post.