Pfsense with pihole correct configuration?
-
Hi currently i have all my traffic goes directly tru pihole like this:
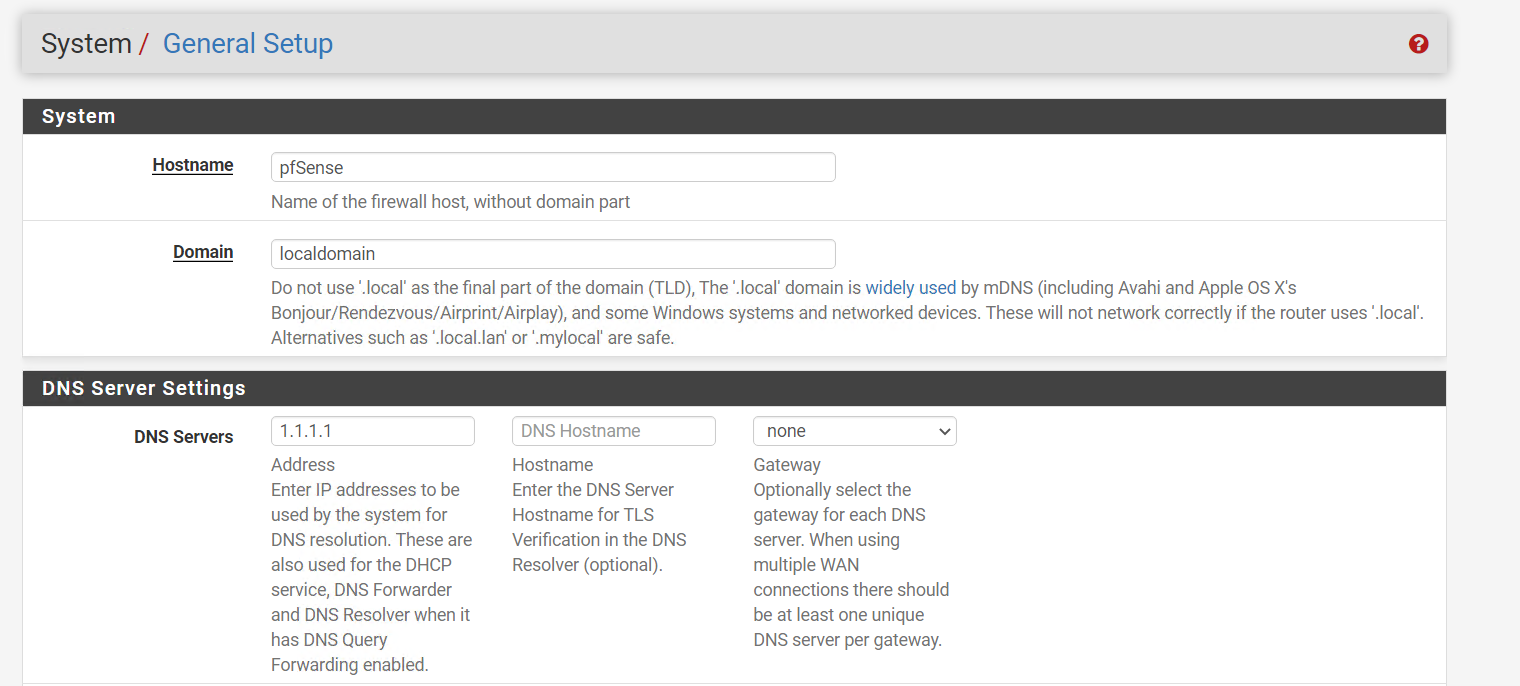
general settings:
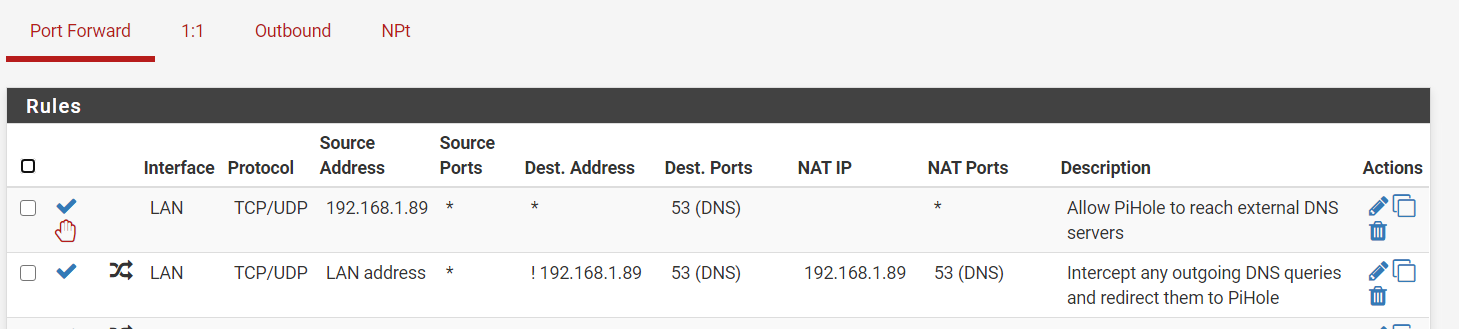
nat redir:
i have DNS resolver and Forwarder disabled on pfsense
and in my pihole i have this:
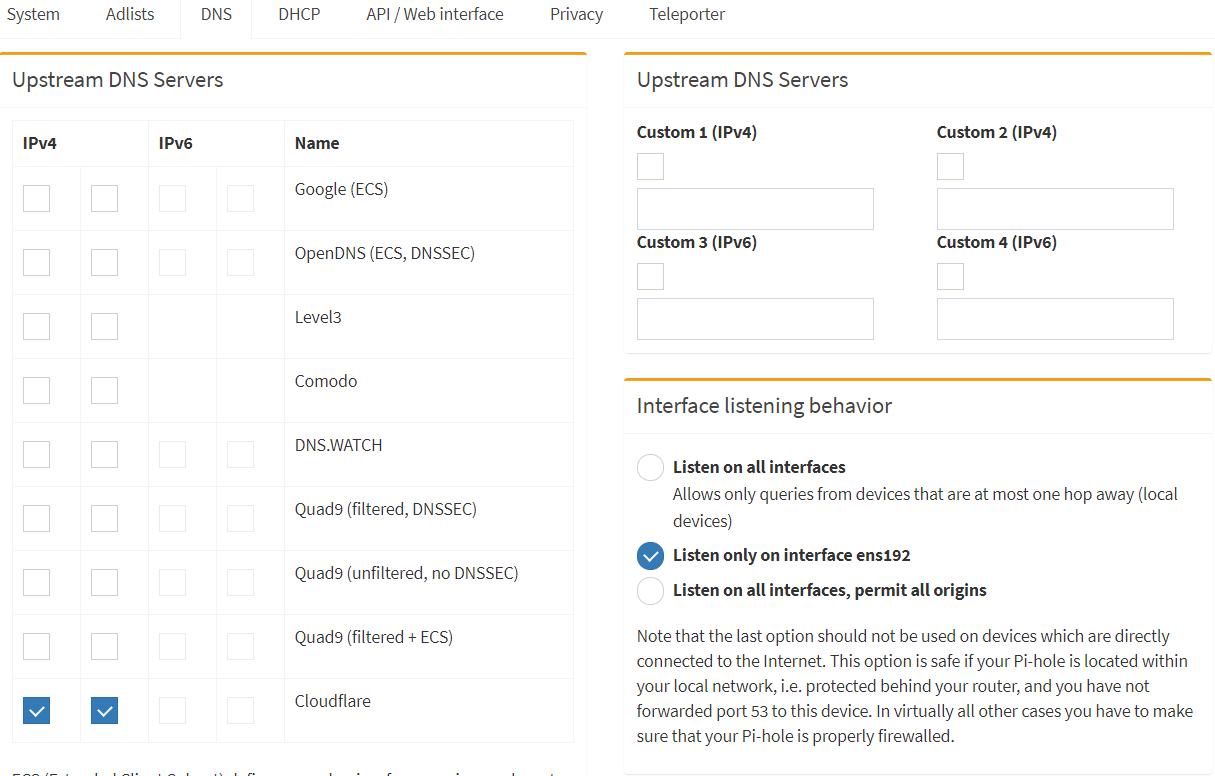
is that the best way to use pihole ? to block ads etc? or should i have my clients connect first to my pfsense? im open to any tips
thank you
-
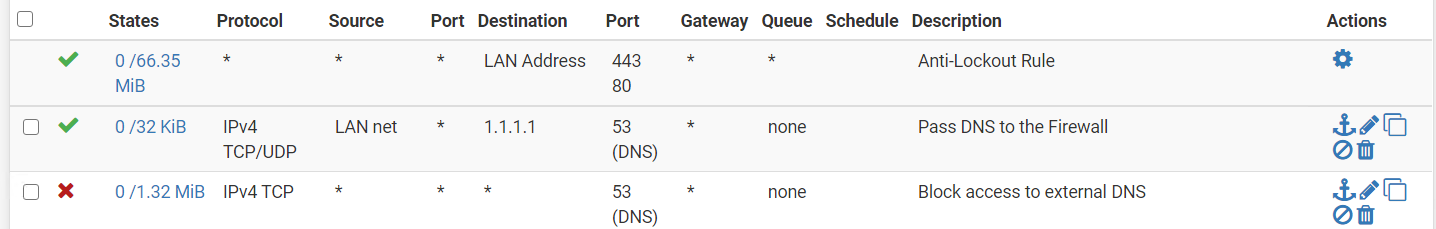
Your rules are wrong.. How exactly would you ever query pfsense for dns when above your allow you have a block to any on 53.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
You need to allow 53 to pfsense address, then below that block all others.
Your rules would even block pihole from talking to clouldflare dns.. Unless you have some floating rules allowing dns - there is no way those rules would allow anything on your lan to do any sort of dns.. Unless your doing dot or doh and you have some rule that allows 853 or just normal 443 traffic below those block 53 rules.
-
@johnpoz hi thank you for the answer, but i have a question, with my settings i suppouse to have all my clients connect directly to pihole right? im new on this sorry for asking many questions
-
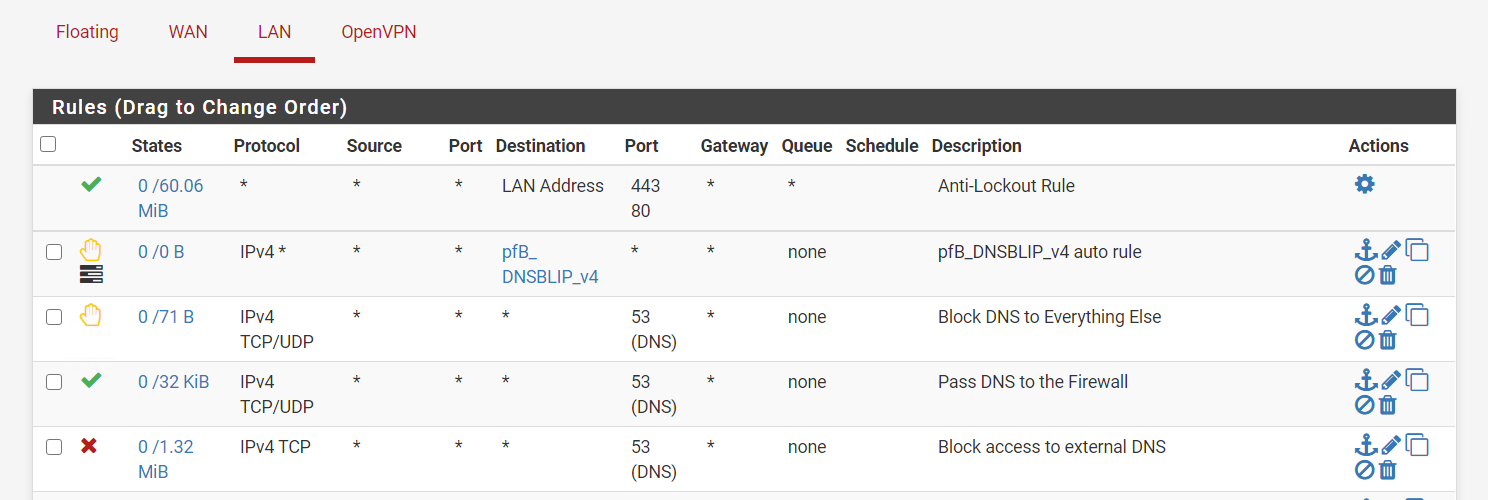
@johnpoz i just changed the order of my rules
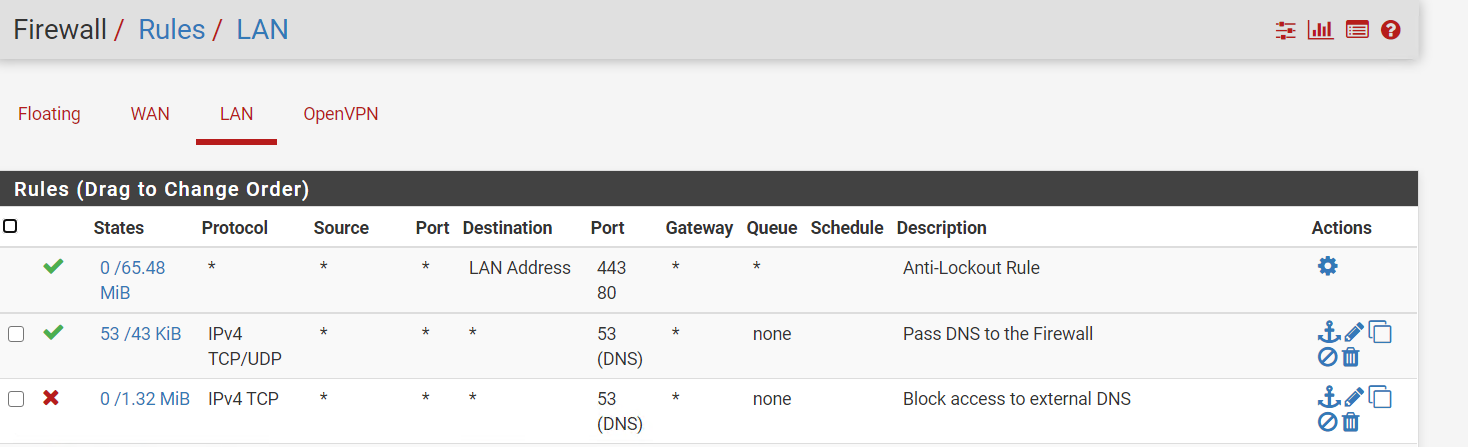
-
That rule allows a client to talk to anything on 53.. If you only want pihole to talk to clouldflare then set the specific rules..
If you want to block access to external, then you need to change your allow rule to dest for where you want to allow, lan address, clouldflare IP, etc.
The way you have your rules doesn't block any dns - because you have a rule that is any any for dns..
edit: Your port forwards are mess as well.. When would source address ever be lan address?
What did you do to your rule to get this?
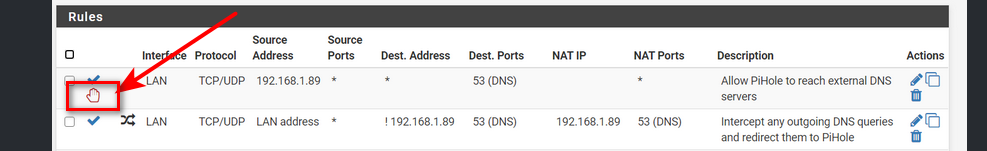
-
-
that rule allows anything to talk to 1.1.1.1 not just pihole.
-
This post is deleted! -
@johnpoz got it
so on nat
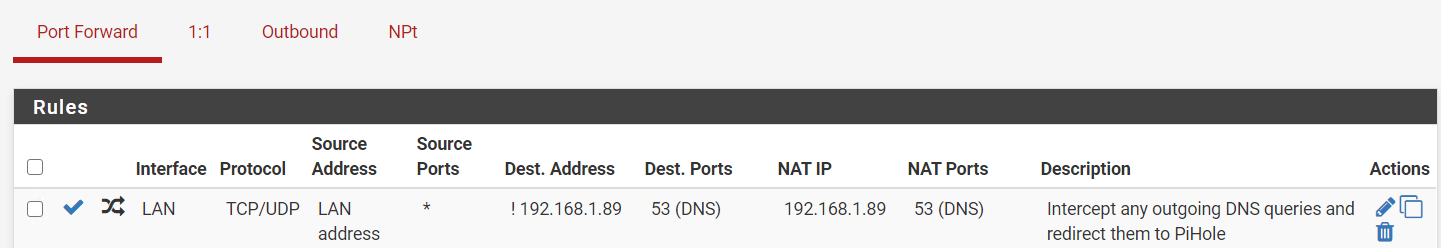
what im confused is the lan rule not sure how exactly should be
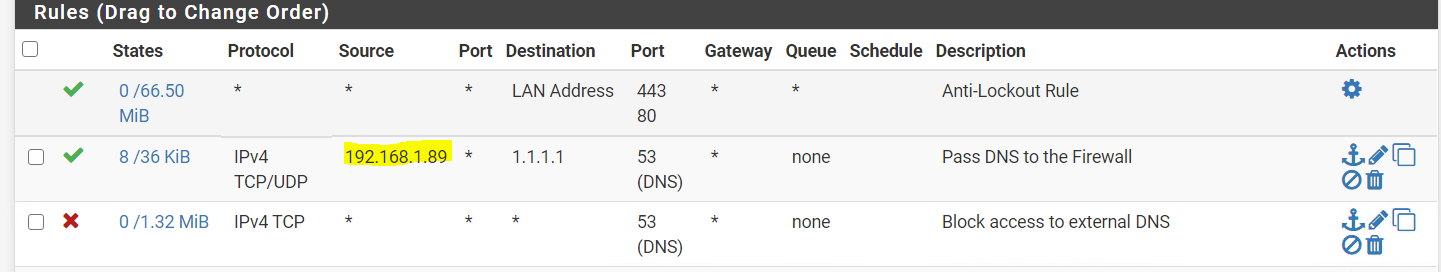
that 192.168.1.89 is my pihole
-
No not really... The redirect is suppose to be to loopback 127.0.0.1
Which then you setup to ask pihole. Pihole then asks clouldflare.
Such a setup runs into asymmetrical flow.. I have gone over this multiple multiple times. if you want to do such a redirect then you would need to do a source nat on the traffic..
The only way such a redirect works if if pihole is on a different vlan then your clients your redirecting.
-
@johnpoz you recommend me erase that rule correct? so just leave this lan rules?
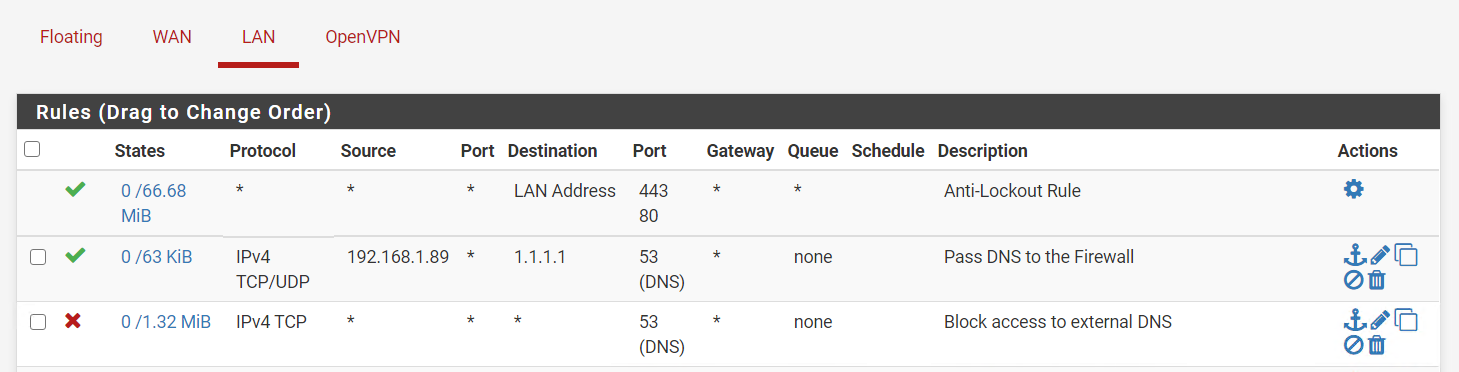
or like this
Allow all port 53 (DNS) traffic from your LAN to pi-hole server
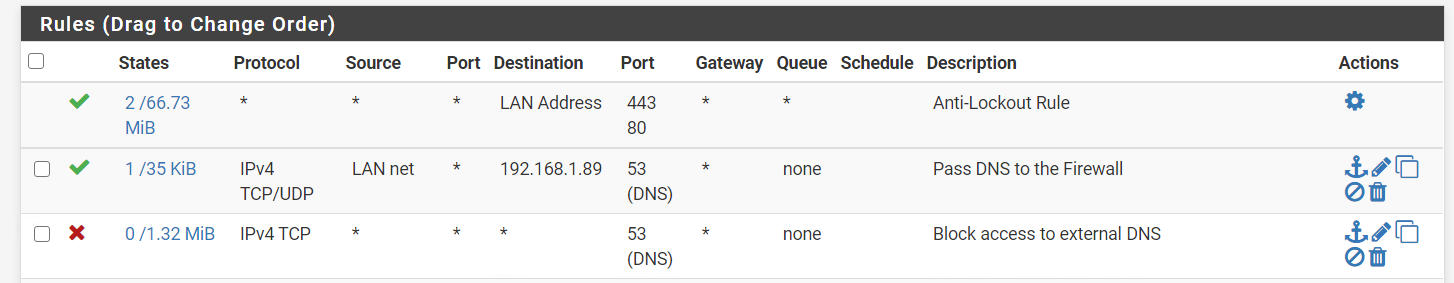
-
May I ask why you run Pihole and not pfBlockerNG ?
-Rico
-
If your going to do a port forward.. Then you need a rule to talk to where your port forwarding.
It should be loopback if your doing the redirection. If you want to forward to pihole directly then you need to make sure you setup outbound nat for such a reflection.

Or you end up with this
dig @1.1.1.1 www.google.com ;; reply from unexpected source: 192.168.3.10#53, expected 1.1.1.1#53When you do something like this.
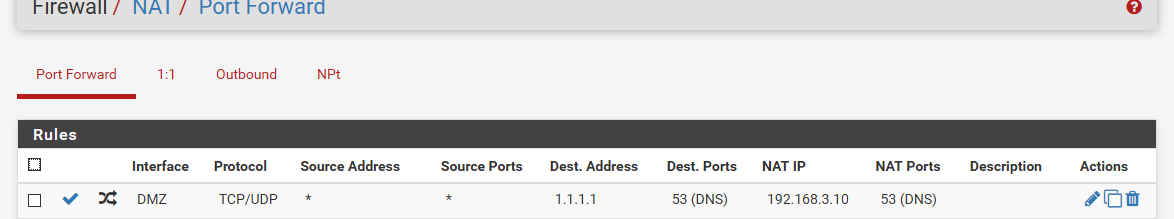
edit: I am not a fan of redirection.. If you want devices to use pihole, then hand them pihole via dhcp.. And just block all other dns.
Then just have pihole ask pfsense directly for stuff.. This allows you to resolve your own local stuff, and for pihole to see who asked.
If you don't want devices to use any thing else - then just block them from doing that. Users hate when their ISP does interception of dns.. But seems ok to do on your own network? Then why are you so mad when the ISP does it ;) It is their network after all that your connected too.
-
@johnpoz got it, now im clear, its better to have a diff segment for my pihole instead of using the same network on pfsense i should use vlan
-
@agaitan026 Putting you pi-hole on a network dedicated to such things is a good plan. I'm not prepared (no time) at the moment to lay out my setup but I'll say this:
Get your network working with unbound as a resolver.
Setup your DHCP and Unbound to register leases and static mappings in unbound. Set hosts names along with your static mappings in dhcp.
Add the pi-hole on a vlan/network of it's own or with other like devices.
Tell your devices (not the ones on the vlan with the pi-hole or the pi-hole) to use the pi-hole for dns with dhcp.
Use NAT to redirect (to the pi-hole) those who don't listen to dhcp, if you want.
Your devices would then use pi-hole which would then forward to pfsense (unbound).
Setup pi-hole to do 'conditional forwarding' (It's in pi-hole dns settings) so that the logs show the hostname dot local domain name.Sounds more complicated than it is. When time permits I'll post up all the settings in pfsense and pi-hole that are relevant.
-
@jwj sounds good, if its possible for you please share your settings :) thank you
-
@agaitan026 Will do. Might not be today, however. Sorry if the language above is not precise, it will make more sense when you see the settings.
I should add that I like pfblockerng. I use it for some light geo blocking and some other ip lists. I do prefer pi-hole for the GUI and the flexibility to create groups and manage blocklists, blacklisted domains and whitelisted domains on a client by client basis or a group of clients. For example a couple of apps on my Apple TVs will not work unless some domains are whitelisted. I don't want to whitelist them for every client (google ad network stuff), just the apple TV's. With pi-hole you can do that easily directly in the GUI.
-
@jwj correct thats what i like from pihole
-
This post is deleted! -
what i saw with my current setup, if i stop pihole, all my conectivity goes down, any chance to have pfsense as backup dns resolver?