Question regarding rules if add IPv6
-
I have been using IPv4 exclusively on my system. I am looking at adding IPv6 and trying to learn more about it before I try it out. One question I am not sure about is with regard to the firewall rules. Obviously, right now, the rules on my WAN and various local interfaces are all set to IPv4 only. If I move to IPv4 and IPv6 on the firewall, is it sufficient to simply edit each rule to use the "IPv4 +IPv6" dropdown in the rule and re-save? Or do I need to duplicate each rule and use IPv6 only in the new rule?
Also, do each of my aliases need to be edited to include the corresponding IPv6 address? For example, I use pfSense as an NTP server, and there is an alias for "local NTP" which contains the local addresses for each of the NTP servers on my local interfaces. Do I need to add IPv6 addresses for each of these so that IPv6-connected clients can access the local NTP server on their interface? Or will they still be able to access the server via IPv4?
Thanks in advance for any assistance.
-
As to your rules.. Depends for example if you have a rule for icmp this is different than icmpv6. So in such a case you might need to create different rule for icmpv6.
But in general most rules should work for both ipv4 and ipv6.
As to your aliases - yeah you would need to add any IPv6 addresses/networks to aliases you created if you want to include IPv6 in those. If your talking built in aliases like lan net, or optX net, or lan address, or "this firewall" those would include IPv6 address if that net or address is ipv4 and ipv6, etc.
But if all you do is hand out or set IPv4 for say ntp - your client would still be able to talk to it via IPv4.. Its pretty much impossible to setup a client that is just pure IPv6.. That is if you want to actually access most of the internet..
Your clients would really need to be dual stack for the foreseeable future..
-
@johnpoz Well that makes things much easier I guess. Just a matter of ticking a different box in each rule and resaving, for the most part. My aliases also include some local addresses that are blocked from internet access. If I want to ensure that those same addresses/clients are blocked even if they pick up an IPV6 address, do I have to assign them a static V6 address and then add those addresses to the "block" alias group? (i.e. can they use V6 to get around V4 rules if I don't specify?)
-
If you don't have any allow rules for IPv6, then default is block.. But sure if you had a rule that allowed any IPv6, then they could use that rule.
Keep in mind that many clients will use random IPv6, and they will change all the time.. So yeah if you want to get specific with rules to allow or deny specific clients based on IPv6 then you need to make sure that client only uses specific IPv6 address.
You will need to turn off the clients use of privacy/temporary IPv6 addresses if your trying to control access based upon specific IPs used.
Once a client has an IPv6 - they will try and use that first, before they use IPv4.. Out of the box most if not all OSes prefer IPv6 over IPv4.. And only when IPv6 is not available will they use IPv4.. If your trying to go to something.domain.tld and there is no AAAA entry for it - then they would just use IPv4, but if there is AAAA for it - they would attempt to use IPv6 first.
So yes you will have to create your rules with this in mind.. While it might seem like IPv6 is just a longer IP.. There are many changes to keep in mind when wanting to use IPv6 on a network, especially if your doing any sort of specific segmentation and firewalling to control access.
-
@johnpoz
Hmm. This is more complicated than I hoped. I will have to continue my planning/reading process. Thanks for the help. -
@johnpoz So given what you said, how does one block only certain IPV6 clients from internet access if the clients use random addresses?
-
@pfguy2018 thank you lida
-
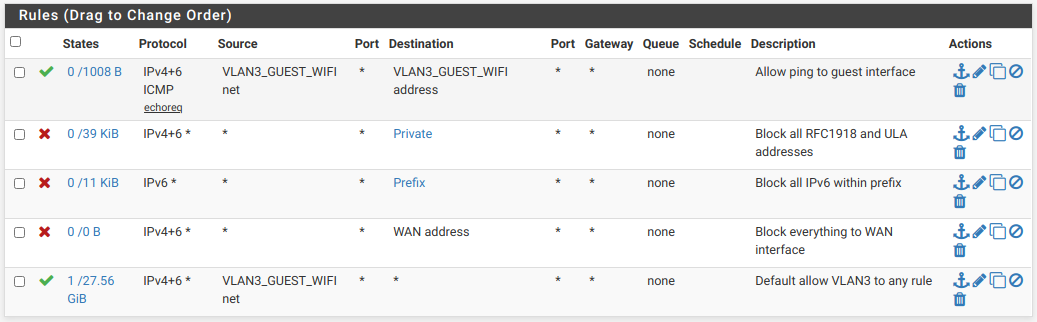
I recently changed the rules for my guest WiFi VLAN to IPv6. in some cases it was only necessary to change from IPv4 to IPv4 & IPv6. I have only one rule that is IPv6 specific and none that are IPv4 specific. That IPv6 one is to block anything within my prefix.
Here are my rules: