How to setup aliases to stop networks talking to each other
-
Hi guys!
I am still trying to get my feet wet with pfSense and how to use firewall rules and aliases...
I have built my own pfSense firewall from old components a customer left me....
I have my WAN connected to the inbuilt network card for the motherboard...
I have the Intel Pro-1000 VT Quad Port 1GbE Gigabit Ethernet Network Card for my network...
Port 1 LAN (Private)
Port 2 LAN (Company)
Port 3 WIFI (Private) connected to a TP-Link 245 access point
Port 4 WIFI (Company) connected to a TP-Link 245 access point
What I would like to do is stop the LAN (Company) and WIFI (Company) talking to each other...
Not sure what is the best approach for restricting them...
Can someone give me a little help in setting this up, so I can learn a bit more about firewall rules and aliases...
Thanks!
Sorry....should have said that all ports are on different subnets...bookie56
-
What I would like to do is stop the LAN (Company) and WIFI (Company) talking to each other...
PfSense processes packets by "first hit" , and filters default on "inbound" data.
So you want to filter the packets on the "receiving interface".
And you want to Block IP's before Pass IP'sMake some IP aliases
LAN_COMPANY xxxx.xxxx.xxxx.xxxx/aa
WIFI_COMPANY yyyy.yyy.yyyy.yyyy/bbOn Lan Company interface:
Block ipv4 proto=any src=any dest (sigle host or alias) = WIFI_COMPANY
Permit ??? whatever is allowedOn Lan WiFi interface:
Block ipv4 proto=any src=any dest (sigle host or alias) = LAN_COMPANY
Permit ??? whatever is allowed/Bingo
-
You can match by inversion so allow traffic to all destinations that are NOT (some alias).
However there have been bugs in the past where the expansion of an inverted alias resulted in traffic passing as it always matches something like !A or !B for an alias of (A, B).
So best practice is to block then pass rules so:Create an alias of all your local subnets, LOCAL_SUBNETS. That can be the exact values or it could be just 192.168.0.0/16 for example if that contains them.
Then create rules like:Pass from Interface Subnet to Interface IP local services ports. NTP, DNS etc if required.
Block from Interface Subnet to LOCAL_SUBNETS
Block from Interface Subnet to this firewall. Includes any public IPs that would otherwise still be accessible.
Pass from Interface Subnet to anywhere. Allows traffic to all external destinations.Steve
-
@stephenw10 thank you for your kind input...will have a look at that tomorrow..
bookie56
-
@bingo600 Thank you for your information..
Will be looking at this in more detail tomorrow.
Live in Sweden and have just come home from eating Julbord (Christmas Buffet) bit stuffed at the moment
-
@bookie56 said in [How to setup aliases to stop networks talking to each other]
Live in Sweden and have just come home from eating Julbord (Christmas Buffet) bit stuffed at the moment

With your (Swedens) current CV19 situation , and the nearly 100% occupancy on the hospitals. Is Buffet a smart choice ?
We have a Torp near Laholm , and hear some scary stories when we're there.
/Bingo
-
@bingo600 Not such a problem. It is not the restaurants that is the problem...it is the peoples behaviour...
We were a family group of four people sitting in an almost deserted restaurant....because of the new restrictions the restaurant has lost over 3000 customers over night...
The precautions for the Christmas Buffet were very good and being as there were hardly any customers we didn't feel at risk...bookie56
-
@bookie56 Ok....after all that I made a bobo....
I should have said that I don't want the Company LAN and Company WIFI talking to the Private LAN and Private WIFI...
I want to keep my Company away from the Private... and as stated each WIFI is going to a TP-Link 245 access point...
Each of the network ports has its own subnet....bookie56
-
But allow connections the other way? From Private to Company?
And presumably you want to allow Company LAN to Company wifi?
It's all just a matter of adding the right rules in the right order.
Steve
-
@stephenw10 Thanks for your reply...
That is what I am finding confusing...
I think for my setup I just want to keep them separate...
Why would I need Company LAN to connect to Company WIFI? LAN is the cable connections and WIFI is the wireless....
If you have a scenario where they could need to talk to each other please say....
I would really like to hide my Private networks from the Company ones....just don't know if that is possible?
I am open to suggestions...
With the setup I have each port has its own subnet and I thought having it that way would give me more options....of course I have a cable connection from each wifi port to the access points...
I run my business from home and just thought it would be a good idea to separate the two for security reasons....bookie56
-
You don't need to have Company LAN and Company WIFI allowed to talk. Just most deployments would have some requirement for that such as accessing some hardwired resource (printer, file server) from a wireless device. But you can open much more specific rules to allow that.
You can block or allow traffic between subnets as you wish. pfSense just sees them as 4 separate interfaces.
If you put rules on all 4 as I outlined above clients on all the interfaces would only be able to access external public sites. You would have to add additional pass rules to allow traffic between any of the subnets, if you needed it.Steve
-
@stephenw10 Thank you Steve!
bookie56
-
@stephenw10 said in How to setup aliases to stop networks talking to each other:
However there have been bugs in the past where the expansion of an inverted alias resulted in traffic passing as it always matches something like !A or !B for an alias of (A, B).
Ouch, I've never seen this and it would be really really bad.
I have a lot of Invert match rules for almost all my pfSense Installations...
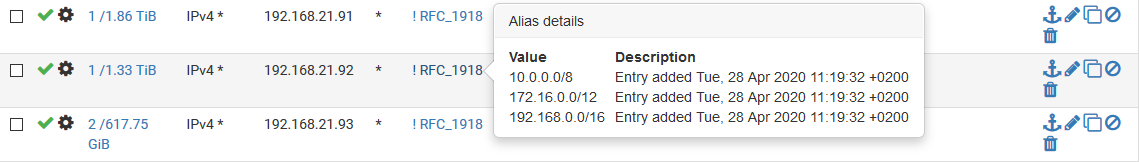
-Rico
-
There have not been for a while and I use invert rules myself. I try to use them only for single subnet aliases though.
Can't find a bug report for that now but I know I have hit it in the past.Steve