Passing public /29 through one pfSense firewall to another
-
In a bit of a strange situation where I'm having to use two pfSense firewalls - one 'main' one that does everything you'd expect it to, and then another which has a L2TP tunnel as an interface and acts as a gateway for it. I'm unable to use L2TP on my main firewall as it instantly takes the WAN down and webconfig just hangs. Tried differnet hardware etc, to no avail. Interestingly, no such behaviour on a virtual machine. No matter -
The 2nd firewall (L2TP firewall) has a /32 assigned to the L2TP interface, with a /30 and /29 routed to it. The /30 is assigned to the LAN interface and outbound NAT is disabled so I can connect it to my main pfSense router. Main pfSense router has an OPT interface with DHCP giving it an IP from the /30 as its public IP.
However, I have no idea how to get the /29 to pass through from the L2TP firewall to my main firewall.
I believe it's a static route setting but having looked around, don't actually know how to configure it. I can assign /29 IPs on the L2TP firewall, but they aren't passed through to the main one...
What static routes do I need to set, and where to get the /29 to route to my main pfSense firewall?!
-
You would need to assign the /29 on the main firewall.
And add a static route to the other pfSense device for the /29 subnet via the main firewall.
I would not use DHCP there for the transport subnet. Just assign each ens statically from the /30.
That doesn't need to be a public IP either. Since you are using it only to route the /29 it could be any private IP.Steve
-
@stephenw10 Thanks Steve - I may be being completely thick/stupid here - so based off your instructions, I've
a) Assigned the /29 as VIPs on the main firewall as they'll be used as 1:1 NAT;
b) Set a static route from the main firewall that goes to the gateway of the L2TP-only firewall.However this hasn't worked. I might've worded my setup in a confusing way, so I've attached a diagram to show what's going on which might help explain things better and what I'm trying to achieve. The L2TP duty pfSense instance connects to the L2TP service and has the IPs routed to it. I am trying to pass these to my main firewall.
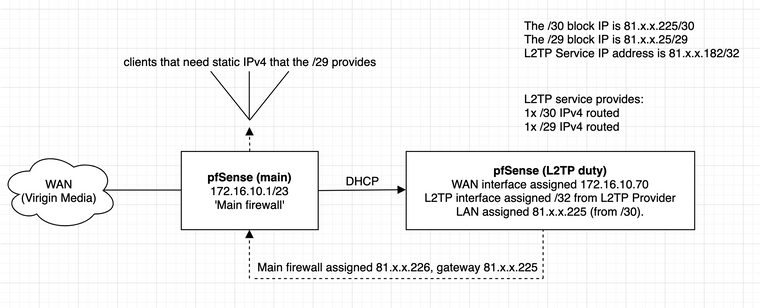
Note your point re the /30 - however, I have it for use so might as well use it for something - but will likely change it to a private IP once I can get things working and return it back to the L2TP provider!
-
How are you testing? Do you see anything blocked in the firewall logs?
Can connect from somewhere external to either end of the /30?
You will need an interface with a gateway on it in order to get reply-to tags on states opened through it. DHCP will do that automatically though.
Ping should work anyway even with an asymmetric route.Steve
-
For testing, I've got a VM (172.16.11.126) that I try to 1:1 NAT to 81.x.x.27 (one of the IPs from the /29) to replicate what I'd be doing with it in lab 'production'
Setting the gateway for 172.16.11.126 to the auto-DHCP-created gateway via a rule allows me to access the internet with the IP assigned to the interface (81.x.x.226) just fine. When I set 1:1 NAT from an address out the /29, I get nothing on the test VM. No connection incoming or outgoing, plus nothing in the firewall logs...
-
If you ping into something in the /29 from an external IP do you see those pings actually arriving anywhere? Maybe that /29 is not being routed to you correctly?
Steve
-
I thought it wasn't being routed correctly too, however if I try assign it to a device (eg if I connect a test VM onto an OPT interface) to the L2TP pfSense instance, I can assign any /29 IP there just fine via just 1:1 mapping it... leads me to believe I'm missing something in the way its being routed from the L2TP pfSense to my main one.
Really really appreciate your help so far. I'm also trying to see if there's something obvious that's been missed or if it's some sort of issue elsewhere but can't think of what it could be.
-
What does your static route look like for that?
Even if that was missing entirely you should still traffic arriving for those IPs at the L2TP pfSense if it's routed to you.
Steve
-
This is the static route on the main pfSense instance. Gateway created automatically by DHCP.
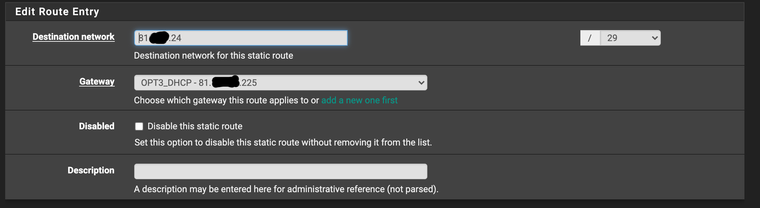
Can't ping (and I've made sure there's an IMCP rule present to pass) - so still confused.
I think another option would be to assign the /29 to the LAN interface of the L2TP pfSense, then address the main one with an IP from that /29. I'd burn 3 addresses instead of 1, which is a lot considering it's only a /29 but it would at least get me somewhere.
The aim has been to get the L2TP pfSense to route the /29 as-is, without having to waste any addresses, using the /30 as the transport network. Fast appreciating that my day job isn't in IT/network admin based on the frustration this is causing!
-
That static route appears to be on the wrong firewall, it needs to be on the L2TP pfSense to route traffic to main firewall.
Steve
-
Added a static route from the /29 to 81.x.x.225 (created the gateway on the L2TP instance for the interface address) and still nothing. Even tried creating a gateway for 81.x.x.226 (the IP given to the main firewall) to go via that and still nothing.
Have also attempted various combos of having/not having a static route on the main firewall routing traffic via the receiving interface to no avail. Nothing in the firewall logs that's showing issues either. The /29 works fine if allocated to an interface so know it's being routed down the tunnel fine.
-
The static route needs to be on the L2TP firewall and it needs to be for the /29 subnet via the .226 address on the main firewall.
Any static route on the main firewall needs to be removed of you will have a routing loop.
The hosts inside that /29 do not need a static route. The only outbound routing should be policy based on the firewall rules passing traffic from that interface.
Steve
-
I'm losing the plot here I think. Right - static route has been added to the L2TP instance which looks like the below:
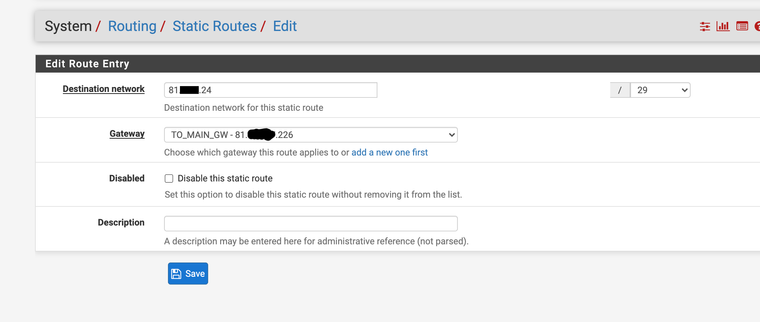
No static routes or anything are added to the main firewall. Still no luck in getting it to route - adding a 1:1 NAT to the test machine or even standing up a test interface with the /29 assigned on the main firewall results in... nothing.
Its configured like the following:
a) L2TP instance takes L2TP tunnel, auths, establishes connection
b) /30 is assigned to LAN on L2TP instance
c) Main firewall picks up .226 of that /30
d) Static route is configured like the above cap
e) /29 is assigned to an interface on the main firewall.
f) Client connected picks up a public IPv4 but usesAn allow-all rule is present on the interface which has got the /29 assigned with the gateway being the one provided on the L2TP instance.
Where do you think on the above steps I could be screwing up?
PS: I owe you a drink or three. Thank you so much for helping.
-
Send some pings to some IP in the /29 from an external address.
Check the state table in each pfSense, you should see states for that ping traffic coming in over the L2TP interface and out towards the main firewall. And states allowing it into the main firewall and out to wherever the target is, on the assigned interface for example.
If any state is missing check the firewall log for blocked traffic.Ultimately run packet captures to determine if those packets are actually arriving at all.
Steve
-
Assigning an IP from the /29 to an interface means I can ping that IP from an external address. That shows, at least, the block is being routed to the main firewall. Couldn't get any internet access, 1:1 NAT etc working though. Have now run out of time trying to diagnose, but ISP has swapped my /29 for a /28, which is more than enough for what I need for now even considering the 4 lost addresses (3+1 interface) - so have just put it on an interface on the L2TP instance and gone the easy way.
Thanks so much for your help though - absolute legend!