(IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP
-
There is no 'correct' workaround here. This might work for you, it appears to have worked for others. It might break at upgrade etc, it's not something we test as NAT on VTI is expected to fail.
By moving the filtering from enc to if_ipsec it should mean traffic is passed outbound on ipsecX and replies are also passed there. No states on enc0.
Using OpenVPN here is the only thing expected to work.
Steve
-
@stephenw10 said in (IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP:
There is no 'correct' workaround here. This might work for you, it appears to have worked for others. It might break at upgrade etc, it's not something we test as NAT on VTI is expected to fail.
By moving the filtering from enc to if_ipsec it should mean traffic is passed outbound on ipsecX and replies are also passed there. No states on enc0.
Using OpenVPN here is the only thing expected to work.
Steve
Since Wireguard is now available in pfsense 2.5, will it solve my issue with NAT over VPN?
-
Yes, if you can use WireGuard you can happily route, NAT or whatever across it.

-
If you only have VTI IPsec (no tunnel mode P2 entries) you can also try the patch on https://redmine.pfsense.org/issues/11395 and switch the new option over to filter only on VTI interfaces. Then you can use NAT and rules on assigned VTI interfaces.
-
@stephenw10 said in (IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP:
Yes, if you can use WireGuard you can happily route, NAT or whatever across it.

@jimp said in (IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP:
If you only have VTI IPsec (no tunnel mode P2 entries) you can also try the patch on https://redmine.pfsense.org/issues/11395 and switch the new option over to filter only on VTI interfaces. Then you can use NAT and rules on assigned VTI interfaces.
This is great! WireGuard as a solution and a patch with IPsec!
Is WireGuard a lot better than IPsec though? Is it recommended to switch over if I'll just need to use it for a single S2S connection?
-
Wireguard is perhaps slightly more flexible that IPSec if both sides support it. That's big if!
IPSec is pretty much universally supported.
You probably won't see much difference in speed. IPSec can be at least as fast.I would probably use Wireguard here because to use IPSec you will need to use that patch and doing so will prevent you using other IPSec tunnel mode connections. If you know you will never need to do that then either should be OK.
Steve
-
@stephenw10 said in (IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP:
Wireguard is perhaps slightly more flexible that IPSec if both sides support it. That's big if!
IPSec is pretty much universally supported.
You probably won't see much difference in speed. IPSec can be at least as fast.I would probably use Wireguard here because to use IPSec you will need to use that patch and doing so will prevent you using other IPSec tunnel mode connections. If you know you will never need to do that then either should be OK.
Steve
I agree. Ok, time to try WireGuard. This is the first tutorial that's been published by a Youtuber since the release of 2.5. He admits that he is not a WireGuard expert and is open to corrections of his mistakes (if there are any).
I hope you guys can have an official documentation about WireGuard very soon.
-
Yeah, that looks good. I see nothing obviously wrong with that walk-through.

Steve
-
@stephenw10 said in (IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP:
Yeah, that looks good. I see nothing obviously wrong with that walk-through.

Steve
Great! I have a few concerns though:
-
In the Peer setup, shouldn't the "Peer WireGuard Address" be just a single IP (tunnel interface of the far side peer), instead of the IP in CIDR notation that he did on the video?
-
When he created the WAN rule for 51820, he noted that he made a mistake about putting 52180 but it still works. Any idea why? Also, why is this WAN rule not automatically defined (but hidden) just like in IPSec? I know in OpenVPN, the explicit WAN rule is also required.
-
In my use case where I have one side with a static public IP (Main Site) and another side that is behind a CGNAT (so a private IP is assigned on my WAN interace; Remote Site), would it make sense to keep the "Endpoint Address" BLANK on the Main Site peer settings so that it will accept any remote IP AND will not initiate the connection?
-
-
The peer IP address is not actually required for WireGuard it routes internally using the allowed IPs vs the peer public keys.
Adding that there adds routes in pfSense automatically. It's a single IP address inside that subnet, I would not expect that to make any difference.You only actually need a firewall rule on one end to establish the tunnel. The reply traffic then uses that state so traffic goes both ways. It's better to have the rule correct at both ends though so the tunnels can establish from either end.
There are no hidden auto-rules like there are for IPSec. It's like OpenVPN in that regard. It would be better (IMO!) to have IPSec like that too but it would be a POLA violation to change that now.Yes, with one end behind NAT you can only establish outbound from there and the public IP address may change so I would leave it blank on the opposite end.
Steve
-
Ok, so are you saying that if I put the far end tunnel interface address in the Peer IP Address field but not in the Allowed IP's list (like how it was done it that video), it won't add a route for that tunnel interface address? If so, what is the use the case of the Peer IP Address field if it won't be used anyway?
-
If you add the peer IP address pfSense will add it as a gateway and you can use it for policy routing or static routes etc. You can do that manually but the scripts try to make it easier. More like OpenVPN behaves.
Steve
-
Ok, that makes sense. Then I would need that for my use case because I definitely will use the tunnel interface as gateways for routing.
Is it mandatory to put the the tunnel interface address in the allowed IP's though?
-
I figured it out. My observations are:
- Remote end tunnel interface IP in "Peer IP Address" field only (tunnel transit network not in "Allowed IP's" field)
Result: Tunnel works, route to far end subnets AND to transit network are automatically created, gateway automatically created, BUT gateway monitoring to remote tunnel interface IP does not work (it doesn't respond to ping).
- Remote end tunnel interface IP in "Peer IP Address" field AND tunnel transet network in "Allowed IP's" field
Result: Everything works!
The most important thing for me that solved my return traffic issue is to create a rule in the WireGuard interface tab and NOT on the WireGuard group tab (I left this empty) for reply-to to work. This is documented in the Netgate documentation pages.
My remaining concern now is why do I get these failures in my WireGuard "Client":
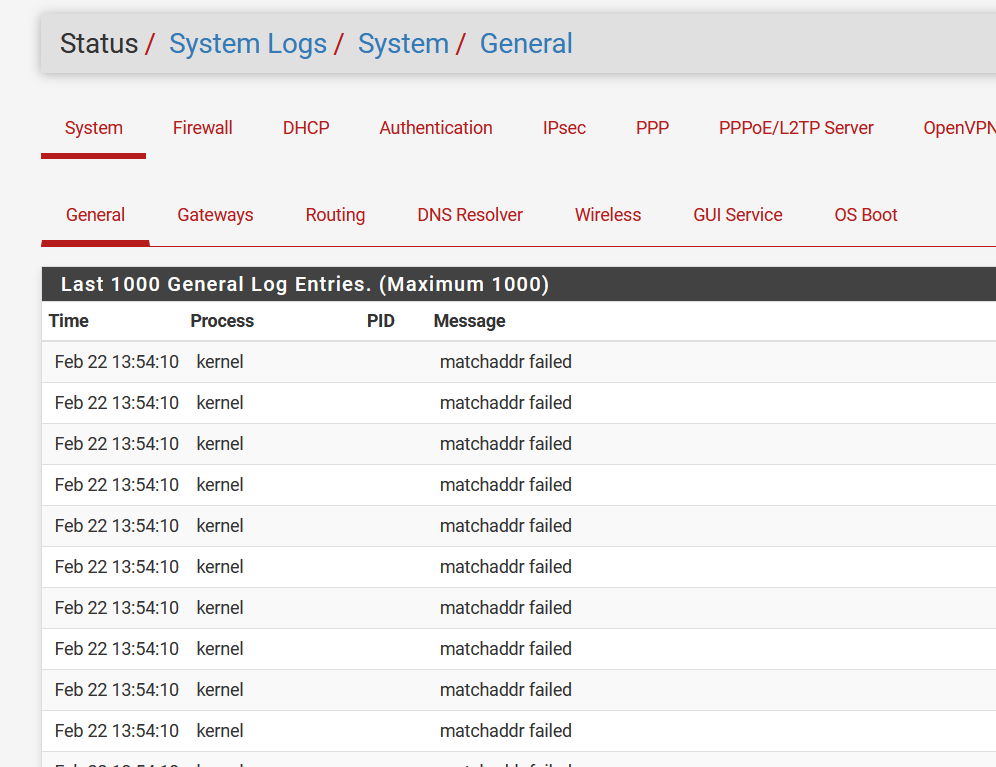
They were also in the server side while I'm trying to figure out everything but now they stopped. They continued to show in the client side even though everything seems to be working. Any ideas?
-
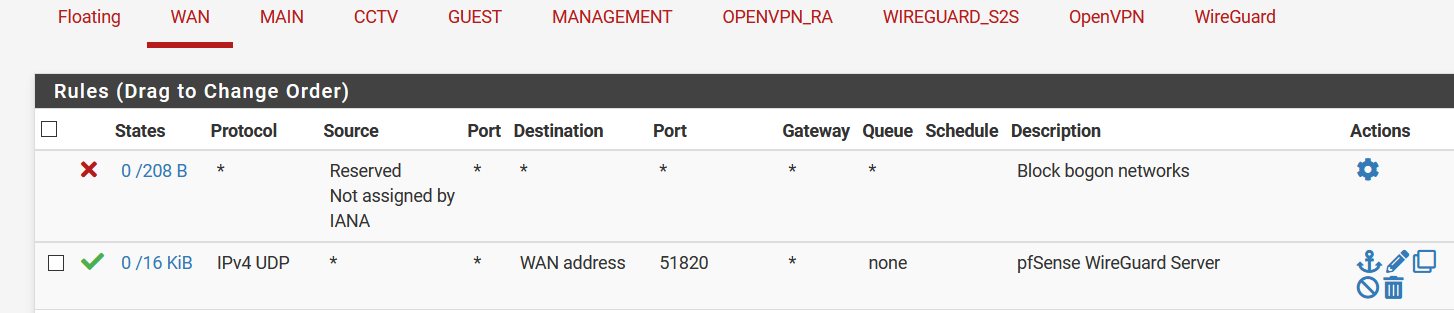
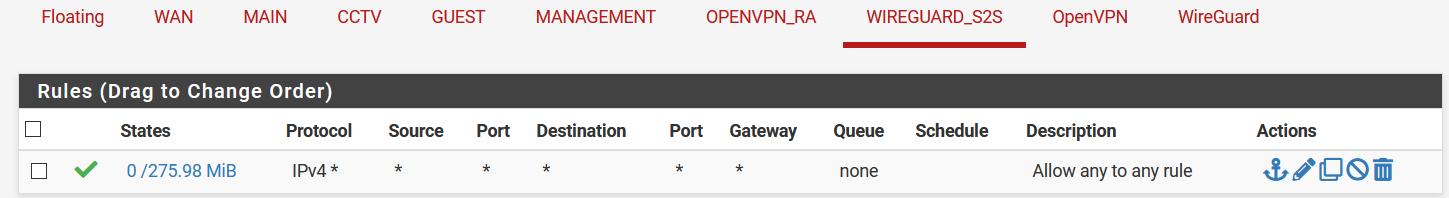
Also, I noticed that even though I get significant amount of hits in the WireGuard interface tabs on both sides, I only see 16KB for my 51820 allow rule on the server's WAN interface tab:
Server:
Client:
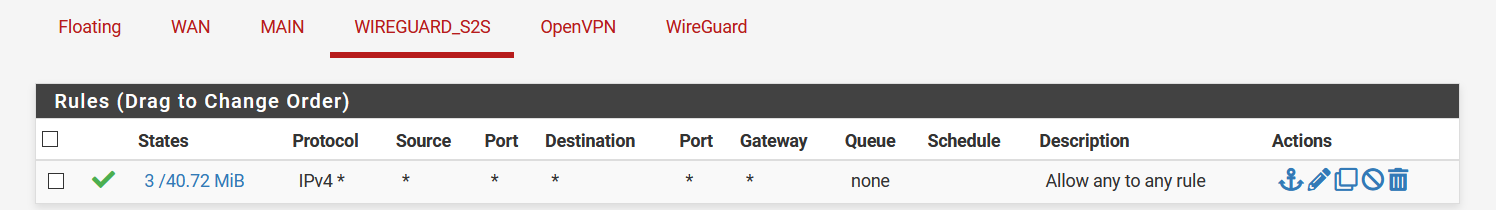
Shouldn't the WAN rule show approximately the same amount of traffic?
-
If the initial connection to the other side was outbound on that peer (there is no server/client in wg) then return traffic there will use the open state. That firewall rule would not be used to create a state that would that show traffic on it.
Steve
-
@stephenw10 said in (IPsec outbound NAT to interface address) Reply traffic destination IP not being translated back to original source IP:
If the initial connection to the other side was outbound on that peer (there is no server/client in wg) then return traffic there will use the open state. That firewall rule would not be used to create a state that would that show traffic on it.
Steve
Yup, I'm aware that there is no server/client in WG but in my use case one side is "acting" like a server and the other side is acting like a client by initiating the outbound connection. No, the initial connection was outbound from the client side (the one behind an ISP NAT, naturally) so the WAN rule I'm showing is for inbound traffic (forward traffic, not return).
-
Hmm, well I would certainly expect to see traffic on that rule then.
Check the state table for a state open on WAN with that traffic on it.
Something else must be opening it. -
I do see an open state:
client dynamic public IP:random port -> server static public IP:51820
I then disabled the WAN rule and surprisingly the tunnel still worked. This is consistent with the behavior in the Youtube video above wherein he accidentally specified a wrong destination port in the WAN rule but it still worked. Although, the only difference in this case is the open state goes like the other way around:
server static public IP:51820 -> client dynamic public IP:random port
Why did the open state reverse?
I don't have any other rules for dst_port=51820. Here are all my WAN rules:
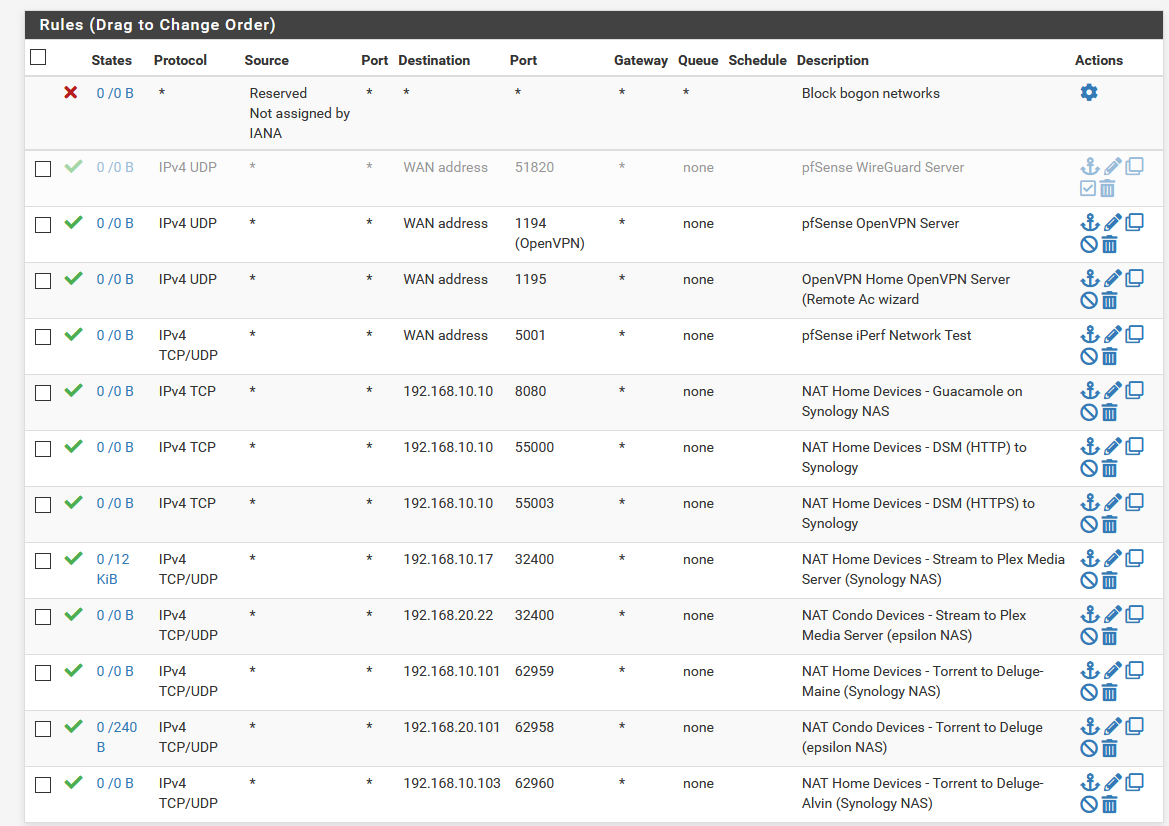
-
Run:
pfctl -ss -vvvvFind the state(s) open with port 51820. Note the rule number that opened them.
Now run:
pfctl -sr -vvvvCheck what rule opened the state.
Steve