Replace Cisco Router's IPsec tunnel with pfSense Router's
-
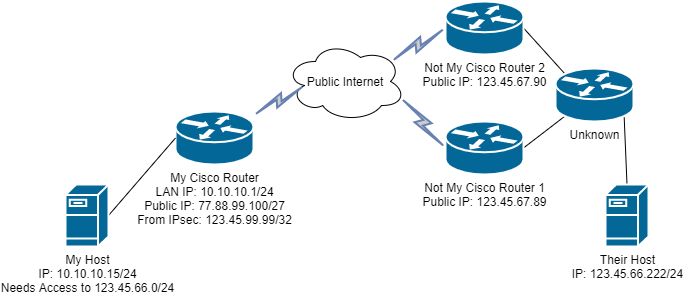
I am replacing "My Cisco Router" with a pfSense Router.
However "My Host" accesses "Their Host" via an IPsec tunnel.
The relevant sections of the configuration of "My Cisco Router" looks like this:
crypto isakmp policy 1 encr aes 256 authentication pre-share group 2 lifetime 3600 crypto isakmp key SomeSecretKey! address 123.45.67.89 crypto isakmp key SomeSecretKey! address 123.45.89.90 crypto isakmp invalid-spi-recovery crypto isakmp keepalive 10 periodic ! ! crypto ipsec transform-set AES256 esp-aes 256 esp-sha-hmac ! crypto map THEVPNMAP 1 ipsec-isakmp description The VPN Tunnel to OtherPlace set peer 123.45.67.89 set peer 123.45.89.90 set transform-set AES256 set pfs group2 match address VPNTUNNELACL reverse-route ! archive log config hidekeys ! ! ip ssh time-out 60 ip ssh authentication-retries 2 ! ! interface FastEthernet4 description THE_WAN ip address 77.88.99.100 255.255.255.224 ip access-group FIREWALLACL in ip verify unicast reverse-path no ip redirects no ip unreachables no ip proxy-arp ip flow ingress ip nat outside ip virtual-reassembly duplex auto speed auto snmp trap ip verify drop-rate crypto map THEVPNMAP hold-queue 32 in ! interface Vlan1 description Internal LAN Gateway ip address 10.10.10.1 255.255.255.0 no ip redirects no ip unreachables no ip proxy-arp ip nat inside ip virtual-reassembly ip tcp adjust-mss 1452 hold-queue 32 in ! no ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 77.88.99.97 ip http server ip http access-class 23 ip http authentication local ip http secure-server ip http timeout-policy idle 60 life 86400 requests 10000 ! ip nat inside source static 10.10.10.15 123.45.99.99 ! ip access-list extended FIREWALLACL permit icmp any any permit tcp any any eq 22 permit tcp any any eq telnet permit esp host 78.90.123.45 host 77.88.99.100 permit udp host 78.90.123.45 host 77.88.99.100 eq isakmp permit udp host 78.90.123.45 host 77.88.99.100 eq non500-isakmp permit icmp 78.90.123.0 0.0.0.127 host 77.88.99.100 echo permit esp 123.45.0.0 0.0.255.255 host 77.88.99.100 permit udp 123.45.0.0 0.0.255.255 host 77.88.99.100 eq isakmp permit udp 123.45.0.0 0.0.255.255 host 77.88.99.100 eq non500-isakmp permit icmp 123.45.0.0 0.0.255.255 host 77.88.99.100 echo permit icmp any host 77.88.99.100 echo-reply permit icmp any host 77.88.99.100 time-exceeded permit icmp any host 77.88.99.100 unreachable deny ip 10.0.0.0 0.255.255.255 any deny ip 172.16.0.0 0.15.255.255 any deny ip 192.168.0.0 0.0.255.255 any deny ip 127.0.0.0 0.255.255.255 any deny ip host 255.255.255.255 any deny ip host 0.0.0.0 any deny ip any any ip access-list extended VPNTUNNELACL permit ip host 123.45.99.99 123.45.66.0 0.0.0.255 ! access-list 23 permit 0.0.0.0 access-list 23 permit any no cdp run ! endI have been working on replacing "My Cisco Router" with "My pfSense Router" and I was actually able to create the Phase 1 and Phase 2 components. Status -> IPsec shows ESTABLISHED in green as well as a child entry.
To get the Phase 2 (child entry) working I had to use the following:
Local Network of 10.10.10.1/32
NAT/BINAT translation: 123.45.99.99/32
Remote Network: 123.45.66.0/24I had to use the translation option with 123.45.99.99, as I have no control over the remote site and this is what they expect.
*Note at this point all I have been trying to do is see if I can successfully ping "Their Host" (123.45.66.222) from the pfSense router (10.10.10.1). Eventually I will need to able to ping from 10.10.10.15
However all my attempts to ping or trace route to 123.45.66.222 from a shell terminal do not seem to work.
I am confused as to what the appropriate configuration on the pfSense router should be to replicate the functionality of "My Cisco Router". Do I need to something else, NAT things, Rules, Virtual IPs, etc. ? Routing over through the tunnel does not seem to work.
Any help would be very much appreciated.
Kindest Regards,
Adan -
@acestrider1
Local network ( phase 2) 10.10.10.0/24
Or
10.10.10.15/32 -
Thanks for the reply.
Yes, for the time being I am trying to ping from the pfSense router itself. Also, as I am given a single IP Address to use (123.45.99.99) I am assuming it is being translated to 10.10.10.1. This way I can perform test pings from the router's shell.
-
*Minor Update to the diagram
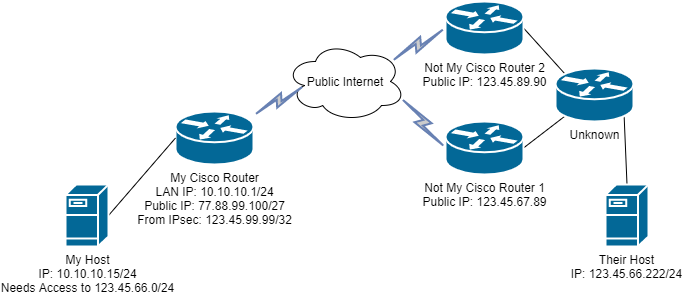
"Not My Cisco Router 2" had IP Address 123.45.67.90 instead of IP Address 123.45.89.90 on the original post's diagram. I do not think that this changes my questions.
The original diagram represent what is actually working using Cisco hardware.
The following diagram is what I presently I am presently doing:
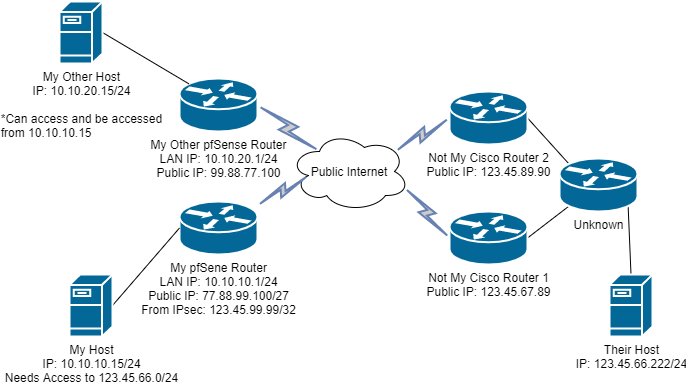
I am basically trying to replace the "My Cisco Router"
I have a working IPsec tunnel between LANS: 10.10.10.0/24 and 10.10.20.0/24. I did this to test if an IPsec VPN between two pfSense routers would work as expected and second check the configuration on "My pfSense Router". I can report that at least the tunnel between my pfSense routers works.