hide false positive blocked/rejected firewall entries
-
I understand there will be Log Entries for Legitimate Connection Packets.
I understand these cannot be filtered out by a FW rule.
Is it possible to filter them out from the log viewer?
I have a blanket deny rule and I'm trying to get a better understanding of what is being rejected so I can create very targeted/specific pass rules.
-
I don’t get the following statement:-
I have a blanket deny rule and I'm trying to get a better understanding of what is being rejected so I can create very targeted/specific pass rules.
By default everything is blocked inbound on the wan interface and anything from the lan interface is allowed out.
Just allow what is needed on your wan interface, you may not need anything as pfSense will allow inbound from the wan if the originating packet came from the lan.
-
Can you post up what your seeing - as example of what your wanting to filter out.
That link is about out of state stuff being denied and log - its normally a sign of an issue.. Be it asymmetrical, or a loss of states, etc.
-
@nogbadthebad said in hide false positive blocked/rejected firewall entries:
By default everything is blocked inbound on the wan interface and anything from the lan interface is allowed out.
Just allow what is needed on your wan interface, you may not need anything as pfSense will allow inbound from the wan if the originating packet came from the lan.
My FW rules are very prescriptive. My last FW rule rejects everything that a previous rule doesn't allow.
@johnpoz said in hide false positive blocked/rejected firewall entries:
Can you post up what your seeing - as example of what your wanting to filter out.
Here are two pictures: one of my relevant FW rules and one for the log entries matching the tracker ID for the last one.
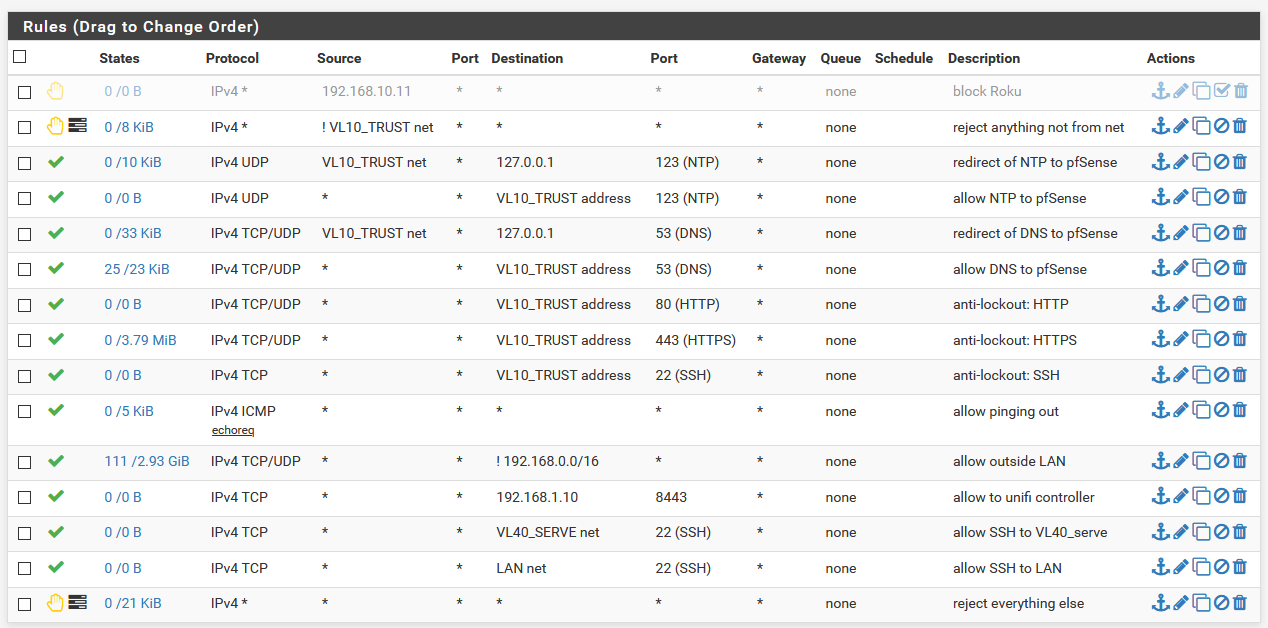
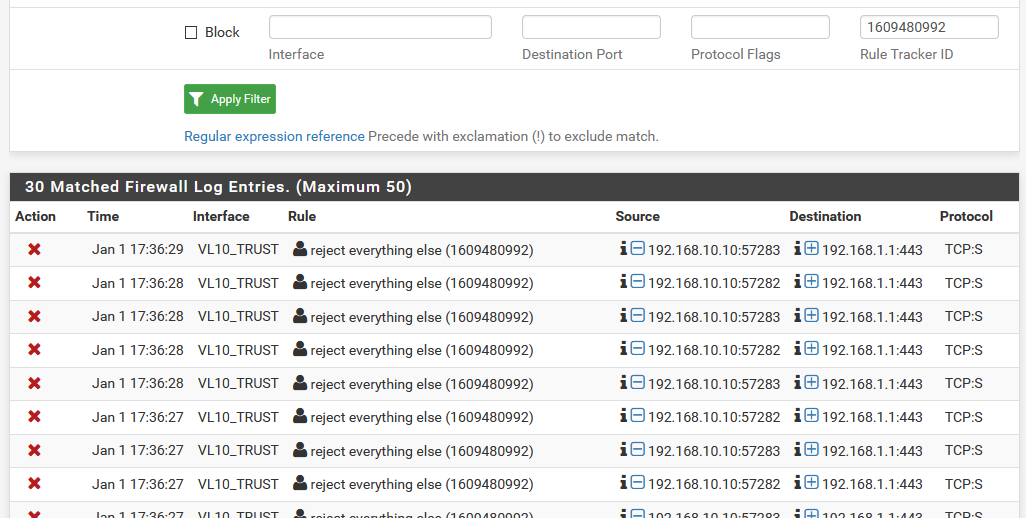
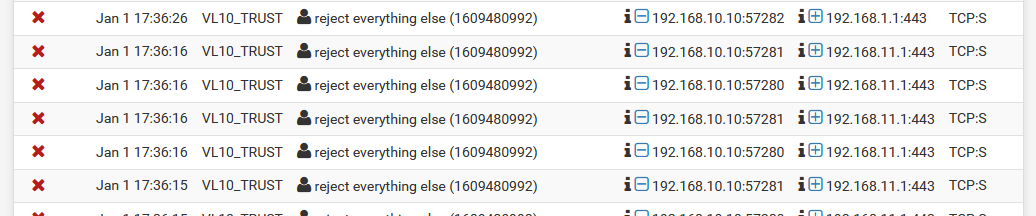
In those last two, source is my main machine, and destination is TCP:S on various other devices.
-
Well if you don't want those to log, then set the rule not to log.
Or if you just don't want to log that 192.168.10.10 machine - then add a rule above that last rule and set that rule not to log..
-
I want to see valid rejections. My understanding is that those above are "left over" ones that can't be exuded from logging.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html
-
Why would you think they are extra?
Those are a SYN block, they are not out of state rules.
You have a specific rule there that states block, that traffic matches and you have it set to log.. Why would you think it wouldn't log that?
-
@johnpoz Doh! I pasted the wrong ones. Sorry. Will get right ones when I get a chance.
-
@imthenachoman said in hide false positive blocked/rejected firewall entries:
My FW rules are very prescriptive. My last FW rule rejects everything that a previous rule doesn't allow.
I was talking about your WAN rules, your screenshot is the LAN or one of the LAN interfaces isn't it as you're doing DNS redirects to the firewall.
If you really want to understand whats hitting the firewall send the logs to a syslog server, then look at the data, I send mine to my Synology NAS and can export out if needed to Excel.