offloading OpenVPN using external gateway
-
Your pfSense is the main router , and has to make the decision, what "traffic" to forward to the RasPI , you have to "set that up" in the pfSense (routing or policy routing).
What is nets are "behind" the OpenVPN ?
-
@bingo600 Currently I am using a "per IP" policy so only specific clients and specific traffic is going thru VPN.
I am using only firewall rules by indicating specific outgoing gateway (WAN or VPN). -
@chrispazz said in offloading OpenVPN using external gateway:
@bingo600 Currently I am using a "per IP" policy so only specific clients and specific traffic is going thru VPN.
I am using only firewall rules by indicating specific outgoing gateway (WAN or VPN).Then i suppose you have to make policy routing.
Make an IP host alias Ie. OVPN_FORWARDS , and put your IP's in that one.
Then make a policy route rule , AF IPv4 , Proto any , matching Source IP = OVPN_FORWARDS , dest any.
Click advanced options
Set the Raspi Gateway as Gateway
Pray that you have enabled forwarding in Raspbian Linux

Remember that pfSense matches on inbound traffic , meaning the rule has to be applied on all interfaces where matching ip's could "enter" (Ingress traffic).
/Bingo
-
@bingo600 here we are! this is exactly what I did before writing here! ahahahah
Yes I enabled forwarding in Raspbian but I cannot understand why it is going outside without using VPN
I am sure it is using the new rule because of some tests I did....
I am starting to suppose that the problem could be on the RPI side....strange since it is working from SSH....
-
@chrispazz said in offloading OpenVPN using external gateway:
Yes I enabled forwarding in Raspbian but I cannot understand why it is going outside without using VPN

Does the package reach the RasPI (using the gateway you set) ?
Or does the pfSense never send it to the Raspi ? -
@bingo600 I do not know how to check this on the RPI side....

I followed this guide:
https://www.instructables.com/Raspberry-Pi-VPN-Gateway/
-
@chrispazz said in offloading OpenVPN using external gateway:
@bingo600 I do not know how to check this on the RPI side....

Quick hack
Enable temporary logging on the Policy Rule , look for log entries to confirm your rule matches "interesting traffic".Real Packet capture (on pfSense).
Diagnostic --> Packet CaptureI suppose your pfSense Wan Interface is the one connecting to the "ISP Router LAN" ?
Packet Capture on pfSense
If you have a screen + kbd on the RasPi , you could install wireshark on that one , to do the packet capture.If only SSH , install tcpdump on the RasPI
How about NAT ?
Are you natting on your pfSense WAN IF ?/Bingo
-
You say your pfSense is 192.168.99.1 , but the drawing shows 99.250
Is the 99.1 interface a pfSense "inside Lan" ip ?
How does the 192.168.99.x interface relate on the drawing ?
I expect your pfSense to have a WAN ip on the ISP router LAN , meaning the 192.168.5.x range.
Since you say you can ping and prob SSH to the Raspi , i assume that is correct or ??
-
@bingo600 NAS is 99.250.
Inside NAS (Synology) I run a VM with pfsense (99.1).I tried enabling logging on the rule and I can confirm it is using it.
Yes, my pfsense WAN interface is the one connecting to the ISP router.
And yes, I am using NAT on the pfsense WAN if.... -
Just for completeness
What is your pfSense WAN IP ? -
@bingo600 it is 192.168.5.254
-
-
@chrispazz said in offloading OpenVPN using external gateway:
I tried enabling logging on the rule and I can confirm it is using it.
Ok
Now try to do a packet trace on the pfSense WAN
Set host address to the Raspi IP
And generate some traffic destined for VPN
-
@bingo600 oops....sorry. Inside IP of router is 192.168.5.254.
Pf sense has 192.168.5.1 on the WAN side...
-
Activated packet capture on host 192.168.5.9 and opened a webpage with www.google.it:
16:58:57.410983 IP 192.168.5.1 > 192.168.5.9: ICMP echo request, id 43267, seq 8815, length 9
16:58:57.920985 IP 192.168.5.1 > 192.168.5.9: ICMP echo request, id 43267, seq 8816, length 9 -
@chrispazz said in offloading OpenVPN using external gateway:
Activated packet capture on host 192.168.5.9 and opened a webpage with www.google.it:
16:58:57.410983 IP 192.168.5.1 > 192.168.5.9: ICMP echo request, id 43267, seq 8815, length 9
16:58:57.920985 IP 192.168.5.1 > 192.168.5.9: ICMP echo request, id 43267, seq 8816, length 9Where did 192.168.5.9 come from ??
did you mean 5.99 -
@bingo600 yes is 5.99 :) don't hate me eheheh
-
So we have confirmed that the ICMP (ping) packages are actually being "policy routed" from 5.1 (pfSense) to 5.99 (RasPI)
We don't see any Echo reply ... The issue is probably on the RasPI
-
On the Raspi (as root)
What does a : sudo iptables -L show ?
And this one ?
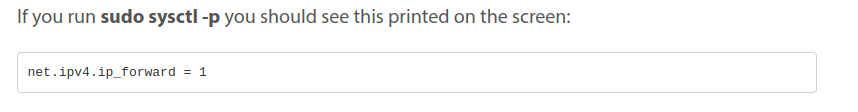
-
This post is deleted!