I think this is a simple question?
-
My primary goal is to have WIFI1 have full access to internal LAN and internet
and to have WIFI2 have no access to internal LAN but full access to the internetI am having no luck at all with my secondary goal to redirect dns requests from everywhere inside to port 853 so DoT will be used regardless of what the client dns configurations are.
I use DoT and would also like to have all port 53 requests from all devices no matter whether they are on LAN or LAN2 to redirect to port 853
-- not sure if that is another post to get help with or if someone could give me a rule for that? My efforts so far have resulted in LAN2 having zero access to anythingI have 1 pfsense firewall device
2 - 8 port unmanaged switches
2 - consumer grade routers with all functions turned off except WIFI (AP)
LAN connected to SW1
LAN2 connected to SW2
WIFI1 is connected to (LAN) switch1 = has complete and full access to LAN
WIFI2 is connected to (LAN2) switch2 = has no access to LAN except for ports 853/53 and all internet trafficor at least I believe it works this way based on my firewall rules
Here is a screenshot of the firewall rules
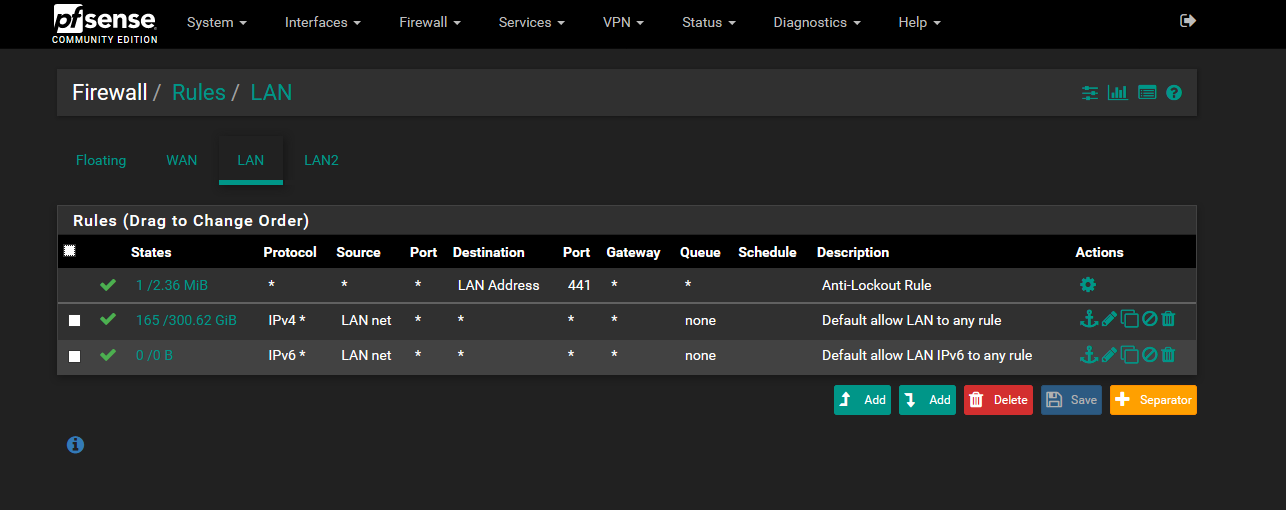
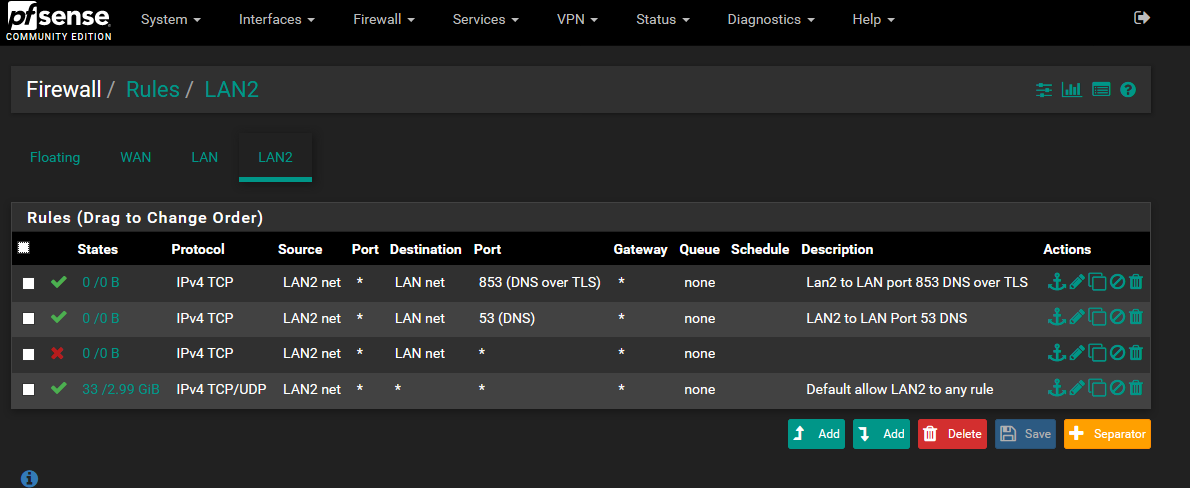
I would love it if someone could tell what I did was working but give any advice on a way to do it better or just leave it as is.
Thanks everyone for any and all suggestions about this!
-
@1of1000quadrillion said in I think this is a simple question?:
53 requests from all devices no matter whether they are on LAN or LAN2 to redirect to port 853
Where did you get the idea that would ever work?? A client asking for normal dns over 53 is not going to be answered by something running dot.. Clients rarely ever use 53 over tcp anyway. While sure it can be used - its not all that common. And your not redirecting normal udp dns And a again a normal 53 dns query even if over tcp is not going to be answered by something doing dot..
Doing dot over your own local network is pretty freaking pointless.. Who would be sniffing this traffic? If they are sniffing on your local network - you hiding dns is pretty minor concern that is for sure.
-
LOL-Right you are, both my sons are programmers and one is experimenting with hacking right now, so I guess he COULD be sniffing out traffic on my internal network, but I trust him and don't need to hide anything from my own son.
I feel a bit ridiculous and thank you for the reminder that there is such a thing as to much (and in my case useless)security.
I just deleted to two DNS rules and left the one blocking traffic from LAN2 to LAN and allowed LAN2 to everything else, meaning the internet.
I think I am good.
Cheers