Selective routing with Surfshark VPN issues.
-
A few days ago I have a post on here asking about a routing problem I had with a free VPN service that would cause NAT reflection it act up or id loose internet. That was solved by selecting not to pull routes. Awesome! So I decided to sub to surfshark since they had a great deal for students. I'm actually having a lot more trouble with them than I did with the ProtonVPN that I tried. I followed the instructions on their site but surfshark had steps to add extra dns addresses and enable dns resolve which I didn't have to do with the other. Pfsense Surfshark Guide Im assuming all these tutorials these providers have are to have your entire networking piped through the VPN, which is not what I want.
Instead of having my entire network piped through the vpn, I want to be able to set a LAN rule for a specific host/alias and select the vpn gateway. At first when setting it up, I did select "dont pull routes" even though the tutorial had it unselected. The vpn is up and running. I have my LAN allow all rule untouched and NAT outbound rule through the VPN. Back in LAN rules, I created a single ip rule and used the VPN as its gateway. I was able to get internet and access local machine with local ip but like a few days ago no access to anything with my domain. I then made the LAN allow all rule and slected the WAN gateway for it but then I lost internet.
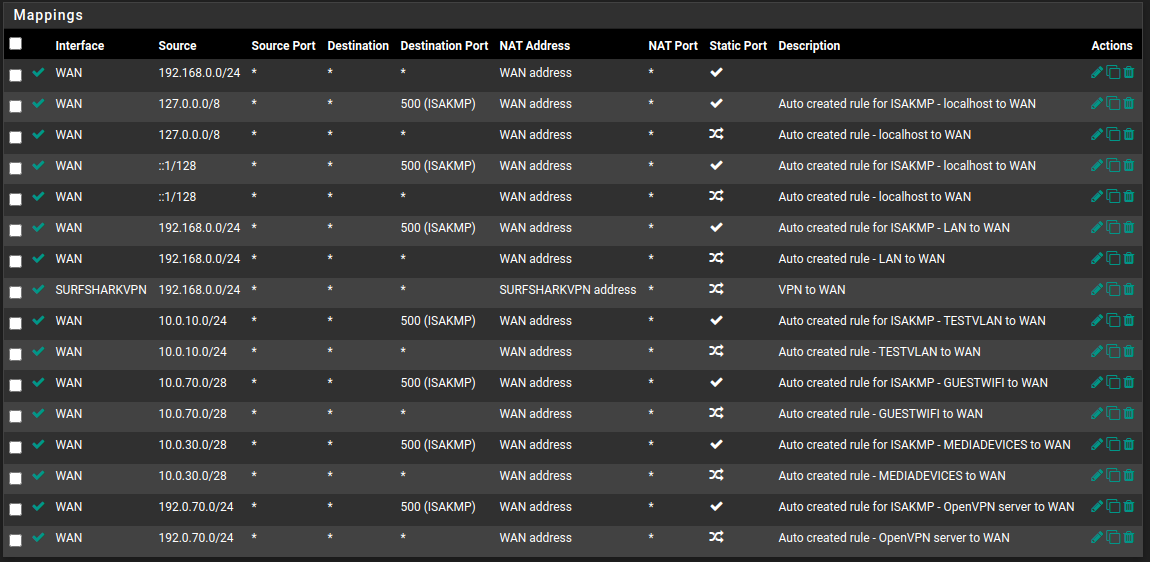
So im stuck at the moment figuring out the best route to take on this. Hoping someone out there catches this thread that has been through it that can give me some tips. Here are pics of my rules and stuff. Nevermind the VLAN stuff, was just testing for a future setup.

-
If your going to policy route stuff out a gateway, and you want said devices your policy routing to also access stuff on other vlans, then you need to create rule(s) above the policy route that allows them to get to your other vlans on whatever ports you want, etc.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
So some IP on your lan that is in your mediaplayer1 alias, first rule - use vpn.. Your vpn sure can not get to your vlans - so how would it ever get to your vlans? put a rule above that that allows says hey want to go to vlanX, ok allowed - no gateway set.
see the bypass policy routing section
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html -
@johnpoz Nothing is on a vlan. It's all on LAN at the moment.(192.168.0.0) I showed a bad example. I wanted to make sure it works on one network before getting to splitting up networks.
-
well what does this mean?
ago no access to anything with my domain
Devices on lan don't use pfsense to talk to other stuff on the lan? But you have not rules to allow those to talk to dns on lan..
Not sure what guide you followed.. But clearly you have more than one network, ie vlans even if they are not tagged since you clearly have more than 1 network there listed in the outbound nats.
There is ZERO reason to do manual outbound, just setup a hybrid for your vpn connection.
And you clearly have rules there in your picture showing access to other vlans - testvlan net, etc..
If your connection is not working through the vpn.. What about connections not through the vpn?
BTW - what is 192.0.70/24 - that is not a rfc1918 address... Why would you be using that??
-
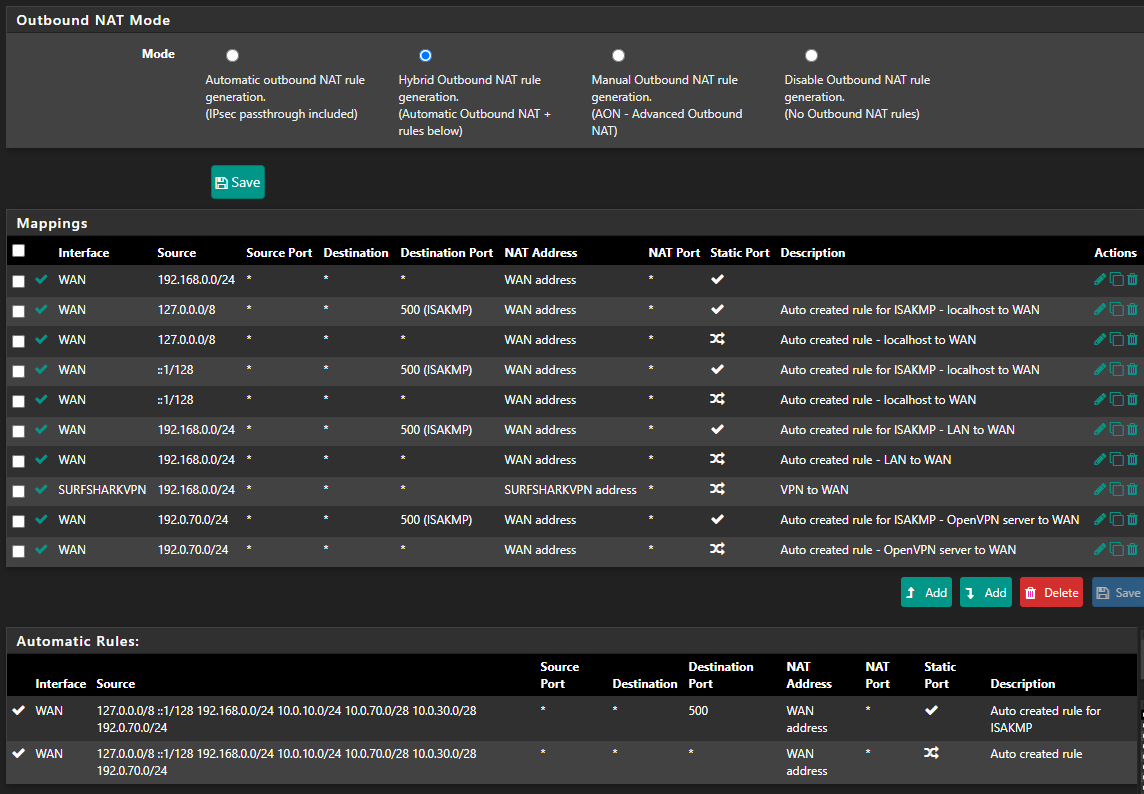
@johnpoz Alright I switched it back to hybrid and removed the extras that do not need to be there. Regarding my domain, I have a number of hosted services behind a reverse proxy. So when I can get the vpn routing to work, I seem to lose access to my services internally using my domain. Its a nat reflection issue as I have access with it outside of my network.
Just to make sure, I can get rid of the rest of this minus the vpn nat rule?
-
Your nat reflection would be broken by vpn sure, if your forcing traffic out a vpn to try and get to your wan IP.
Nat reflection is always bad idea.. its sometimes a work around for shitty app, or not using local dns. What you should do for local resources is just resolve whatever fqdn to the local IP, when you local vs the public IP. This is a split dns setup.
You can get rid of everything in the hybrid nat you just need the vpn one..
-
@johnpoz Yeah I guess I figured with having the LAN Allow all rule as is and then just change the gateway on the ones I want going through the vpn would work fine. Thats actually the way I had it when trying protonVPN.