IPSEC allow trafic only from particular AS networks
-
I have a question regarding different IPSEC interfaces and capturing ESP traffic on the PfSense WAN interfaces in a routed IPSEC configuration .
Currently the following topology is working quite well with in routed IPSec configuration + BGP (FFR and biderectional authentication )
The topology consist out of 3 Pfsense Boxes all running version 2.4.5-RELEASE-p1 :
Client 1 -------------------- SERVER ----------------------- Client 2
IPv4 NAT-T ------------------ static IPv4 -----------------------IPv4 NAT-TThis has been working for a month so far without any problems. Until Suricata reported some external IP addresses are trying to connect to ports UDP 500 and 4500 on the WAN interface.
What i want to do right now is to allow connection to the Server only from particular BGP AS numbers. Since the source network of Client 1 and Client2 is known all i want to do is the have an alias the represent those two source IP addresses that the clients are allowed to authenticate from. I would like to bind then this alias to a rule in the WAN.
In order to implement this. I have first disable the autogenerated rules for IpSec. i.e.
System > Advanced on the Firewall/NAT tab → "Disable Auto-added VPN rules"
To my surprise the IPSEC was still working. Please note that during that time I did not had any ports matching UDP on 500 and 4500 at that time. I even rebooted the Server PfSense box and then the IPSEC connectivity from bought clients was still possible although i have „"Disable Auto-added VPN rules".
Then i decided to add to the WAN interface the following two additional rules
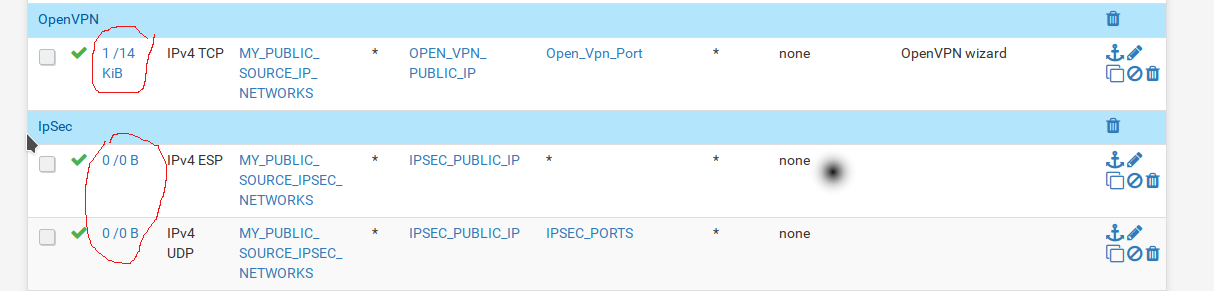
where the alias IPSEC_PORTS here is matching UDP on Port 500 and 4500.
Again the IPSEC is working and all is well and dandy although it in my opinion the IPSEC should not work in this case.
But i asked myself, why when i connect to openvpn then the states counter is changing in this case 1/14 KB and when the 2 Ipsec clients are connecting the states counter is always zero. See the picture. Basically that means that the rules are not matching. I have checked those rules several times and they need to match but for some reason unknown to me they don’t.
Under the Interfaces drop down menu in PfSense I have 2 other interfaces that are result of configuring the Ipsec VTI interfaces I named them IpSec1000 and IpSec2000 those represent the two clients. It is not possible to configure those since they are marked as “not support manual address configuration”
“
IPv4/IPv6 Configuration
This interface type does not support manual address configuration on this page.
“I have tired to do a packet capture in promiscuous mode under those interfaces as well as under WAN but I do not see any ESP packets . I was expecting to set either ISAKMP, or OAKLEY or SKEME protocol under WAN or here there but nothing.
Under Firewall → Rules there is another separate tab called “Ipsec: interface which does allow to filter which network should be allowed to pass the IPSEC tunnel. As described here
What I do not understand is why even after enabling the checkmark “"Disable Auto-added VPN rules" ” without any other rules to select the traffic coming on port 500 and 4500 the IPSEC tunnels are still working as if the checkmark was not selected.
I would like to have fully static IPSEC configuration, thus the next step was to look in
/tmp/rules.debug
and search for the "# VPN Rules" section as mentioned in other post.
pass in quick on $WAN inet proto tcp from $MY_PUBLIC_SOURCE_IP_NETWORKS to $OPEN_VPN_PUBLIC_IP port $Open_Vpn_Port tracker 1563905023 flags S/SA keep state label "USER_RULE: OpenVPN wizard" pass in quick on $WAN inet proto esp from $MY_PUBLIC_SOURCE_IPSEC_NETWORKS to $IPSEC_PUBLIC_IP tracker 1610642677 keep state label "USER_RULE" pass in quick on $WAN inet proto udp from $MY_PUBLIC_SOURCE_IPSEC_NETWORKS to $IPSEC_PUBLIC_IP port $IPSEC_PORTS tracker 1610642793 keep state label "USER_RULE"pass in quick on $IPsec inet proto udp from any to any port $IPSEC_PORTS tracker 1610701683 keep state label "USER_RULE" pass in quick on $IPsec inet proto esp from any to any tracker 1610701625 keep state label "USER_RULE" pass in quick on $IPsec inet from $HNetworks to any tracker 1610637410 keep state label "USER_RULE" pass in quick on $IPsec inet from $ONetworks to any tracker 1610637426 keep state label "USER_RULE" pass in quick on $IPsec inet proto icmp from 10.200.136.2 to 10.200.136.1 icmp-type echoreq tracker 1606076207 keep state label "USER_RULE: Easy Rule: Passed from Firewall Log View" pass in quick on $IPsec inet proto icmp from 10.200.137.2 to 10.200.137.1 icmp-type echoreq tracker 1608222268 keep state label "USER_RULE: Easy Rule: Passed from Firewall Log View" pass in quick on $OpenVPN inet proto icmp from any to any tracker 1564637974 keep state label "USER_RULE"I was not able to find anything that tells me why the IPSEC is still working. But more immortally why the rules that i pleased under WAN are not matching.
I would like to restrict who can reach the ports 500 and 4500 on the WAN interface at all but I do not understand is on which interface I should place the rule in order to match those rules if not WAN then where?
-
I did mistake when i was doing the packet capture and i realized that too late, anyway when i capture more the 100 packets (default) i see ISAKMP and ESP under WAN. Now the only question is why the rule for matching IPSEC is not working on the WAN, or precisely why it is not matching UDP 500 or UDP 4500 or ESP. Is there anything that could prevent that?